Dongle Brochure Final File.Qxd
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
13 Cool Things You Can Do with Google Chromecast Chromecast
13 Cool Things You Can Do With Google Chromecast We bet you don't even know half of these Google Chromecast is a popular streaming dongle that makes for an easy and affordable way of throwing content from your smartphone, tablet, or computer to your television wirelessly. There’s so much you can do with it than just streaming Netflix, Hulu, Spotify, HBO and more from your mobile device and computer, to your TV. Our guide on How Does Google Chromecast Work explains more about what the device can do. The seemingly simple, ultraportable plug and play device has a few tricks up its sleeve that aren’t immediately apparent. Here’s a roundup of some of the hidden Chromecast tips and tricks you may not know that can make casting more magical. Chromecast Tips and Tricks You Didn’t Know 1. Enable Guest Mode 2. Make presentations 3. Play plenty of games 4. Cast videos using your voice 5. Stream live feeds from security cameras on your TV 6. Watch Amazon Prime Video on your TV 7. Create a casting queue 8. Cast Plex 9. Plug in your headphones 10. Share VR headset view with others 11. Cast on the go 12. Power on your TV 13. Get free movies and other perks Enable Guest Mode If you have guests over at your home, whether you’re hosting a family reunion, or have a party, you can let them cast their favorite music or TV shows onto your TV, without giving out your WiFi password. To do this, go to the Chromecast settings and enable Guest Mode. -

1322X USB Dongle Reference Manual
1322x USB Dongle Reference Manual Document Number: 1322xUSBRM Rev. 1.5 11/2010 How to Reach Us: Information in this document is provided solely to enable system and software implementers to use Freescale Semiconductor products. There are no express or implied copyright licenses granted Home Page: hereunder to design or fabricate any integrated circuits or integrated circuits based on the information www.freescale.com in this document. E-mail: Freescale Semiconductor reserves the right to make changes without further notice to any products [email protected] herein. Freescale Semiconductor makes no warranty, representation or guarantee regarding the suitability of its products for any particular purpose, nor does Freescale Semiconductor assume any USA/Europe or Locations Not Listed: Freescale Semiconductor liability arising out of the application or use of any product or circuit, and specifically disclaims any Technical Information Center, CH370 and all liability, including without limitation consequential or incidental damages. “Typical” parameters 1300 N. Alma School Road that may be provided in Freescale Semiconductor data sheets and/or specifications can and do vary Chandler, Arizona 85224 +1-800-521-6274 or +1-480-768-2130 in different applications and actual performance may vary over time. All operating parameters, [email protected] including “Typicals”, must be validated for each customer application by customer’s technical experts. Freescale Semiconductor does not convey any license under its patent rights nor the rights Europe, Middle East, and Africa: of others. Freescale Semiconductor products are not designed, intended, or authorized for use as Freescale Halbleiter Deutschland GmbH Technical Information Center components in systems intended for surgical implant into the body, or other applications intended to Schatzbogen 7 support or sustain life, or for any other application in which the failure of the Freescale Semiconductor 81829 Muenchen, Germany product could create a situation where personal injury or death may occur. -
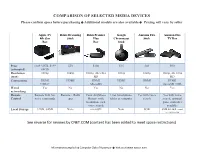
Comparison of Selected Media Devices
COMPARISON OF SELECTED MEDIA DEVICES Please confirm specs before purchasing Additional models are also available Pricing will vary by seller Apple TV Roku Streaming Roku Premier Google Amazon Fire Amazon Fire 4th Gen Stick Plus Chromecast Stick TV Box Box Box Stick Price $149 32GB, $199 $50 $100 $35 $40 $90 (estimated) 64GB Resolution 1080p 1080p 1080p, 4K Ultra 1080p 1080p 1080p, 4K Ultra (max) HD HD Connections HDMI HDMI HDMI HDMI HDMI HDMI USB-C MicroSD microSD USB Wired Yes No Yes No No Yes networking Remote Remote with Siri Remote + Roku Point Anywhere Uses Smartphone, Yes with voice Yes with voice Control voice commands app Remote with tablet or computer search search; optional headphone jack game controller voice search available Local Storage 32GB, 64GB None microSD None 8GB 8GB internal expand to 128GB w/SD See reverse for reviews by CNET.COM (content has been edited to meet space restrictions) Information compiled by Computer Club of Rossmoor Visit us at www.caccor.com Reviews by CNET.COM (content has been edited to meet space restrictions) Apple TV Roku Streaming Roku Premier Plus Google Amazon Fire Amazon Fire 4th Gen Box Stick Box Chromecast Stick Stick TV Box Good Apple TV lets you The Roku Streaming The Roku Premiere+ Chromecast is a cheap Fire Stick can access Fire TV can access stream all the video Stick is a lightning fast, can access more TV wireless video dongle thousands of streaming thousands of streaming content in the iTunes inexpensive device to shows and movies in that streams content to apps. -

GTW 270 Series Frequently Asked Questions
GTW 270 Series Frequently Asked Questions How do I pair my GTW 270 Hybrid with my gaming platform via the dongle? Upon arrival the dongle is already paired with the earbuds. To pair your GTW 270 Hybrid with your gaming platform, please follow the instructions below. 1. Open lid to power on earbuds 2. Plug the dongle and power on your gaming platform. Please use the accessory extension cable for PC or PS4. 3. The dongle will light purple when it automatically connects to your earbuds In case you reset your paired device list, please follow the instructions below. 1. Have both earbuds in the closed charge case, then open the lid. 2. Press and hold the charge case button to initiate pairing. The LEDs pulse red and blue. 3. Plug the dongle into the USB port of your gaming platform of choice. Use the extension cable to connect it to a USB-A port for PC. Press and hold the dongle button to initiate pairing. Why doesn’t the microphone work on my GTW 270 Hybrid when I am using the aptX low latency connection via dongle? aptX low latency only supports the playback channel, which is why the GTW 270 Hybrid is not suited for competitive/online multiplayer games such as Fortnite or CS:GO. For the GTW 270 Hybrid, we strived to have full immersion in experiential games. This is something that will only be possible through the aptX codec which has higher bandwidth, resulting in supporting only the single audio channel without having the microphone functionality. -

Service Manual: (D480/D479), Color Controller Type E-3100, Color
Color Controller: E-3100/5100 (Machine Codes: D480/D479) SERVICE MANUAL October 2008 Subject to change Safety Information When using this machine, the following safety precautions should always be followed. Safety During Operation In this manual, the following important symbols are used: Indicates a potentially hazardous situation which, if instructions are not followed, could result in death or serious injury. Indicates a potentially hazardous situation which, if instructions are not followed, may result in minor or moderate injury or damage to property. • Connect the power cord directly into a wall outlet and never use an extension cord. • Disconnect the power plug (by pulling the plug, not the cable) if the power cable or plug becomes frayed or otherwise damaged. • To avoid hazardous electric shock, do not remove any covers or screws other than those specified in this manual. • Turn off the power and disconnect the power plug (by pulling the plug, not the cable) if any of the following occurs: • 1) You spill something into the machine. • 2) You suspect that your machine needs service or repair. • 3) The external housing of your machine has been damaged. • Protect the machine from dampness or wet weather, such as rain and snow. • Unplug the power cord from the wall outlet before you move the machine. While moving the machine, you should take care that the power cord will not be damaged under the machine. • When you disconnect the plug from the wall outlet, always pull the plug (not the cable). • Risk of explosion if battery is replaced by an incorrect type. • Dispose of used batteries according to the instructions. -

Smart TV Connection Options for FORMED
Smart TV Connection Options for FORMED FORMED does not currently have a TV App, although this is something we hope to offer in the future. Additionally, users may encounter issues streaming the videos available on FORMED directly on their SmartTV using the pre-loaded browser on the TV. This is likely because the browser is incompatible with our video player. FORMED’s supported browsers are: • Google Chrome • Firefox • Safari • Edge If you would like to access FORMED on your SmartTV we recommend the below options: Direct Connection (HDMI) You may use an HDMI cord/cable to connect your HDMI-enabled computer to your SmartTV (all of which have at least one HDMI input). Select the HDMI input option and after you have connected the cord to both devices your computer screen should be mirrored on your SmartTV. * If your computer screen is not mirrored on your TV display you may need to navigate to your computer's projector/projector settings and ensure that either "Duplicate" or "Second Screen Only" is selected. The latter choice will cause the video to only appear on the TV. Chromecast If you use Google Chrome as your web browser you can stream videos or movies from FORMED to a SmartTV using a Chromecast device. This device plugs in to your TV’s HDMI input will allow you to stream FORMED from your computer, tablet or smart-phone to your SmartTV. The Chromecast is $25 - $35 *We've found the easiest way to cast FORMED is by using a computer with the chrome browser, rather than casting from a phone or tablet. -
Wifi Display Miracast Dongle TV Dongle Airplay Adapter Amazon
WiFi Display Miracast Dongle TV Dongle Airplay Adapter Amazon 【Compact Pocket Size】Lightweight design 0.5oz. 【Good for Eyes】Cast to large screen, Free to eyes 【Support Devices】Support Miracast/DLNA/Airplay to cast contents (Video, Game, Picture) from Smartphone/Tablet/MAC to HDTV/Projector 【Fast Setup】No need driver and app installation. Only 3 steps Plug -> Connect -> Play Click 【Add to Cart】below. Buy it NOW http://amzn.to/2svxnCy • ✅【SATISFACTION GUARANTEE】Miracast Dongle is backed by manufacturer 30-day money back guarantee with a 1-year warranty and dedicate technical support team that can help you to get perfect shopping experience. Click 【 Add to Cart 】NOW, Get Delivery in Two-day for Amazon Prime Customer Copyright © 2018 iFlashJump.com • ✅【COMPACT POCKET SIZE】Extremely mini and lightweight design, easy to carry. With 0.5oz, the portable mini size enables business conference, multimedia campus education, home theater entertainment takes place anywhere anytime which outputs from your smart phone, tablet or MacBook laptop. You can put it in any place even in your small pocket when travelling or working • ✅【BENEFICIAL FOR EYES】Stare at the little screen long time definitely will cause eyes uncomfortable, so that easily leads to short-sighted. But casted to large screen, stay clear away from the screen, will be more free to eyes Copyright © 2018 iFlashJump.com • ✅【FAST SETUP and OPERATION】No need driver and app installation. Only 3 steps to start amazing visual journey. Plug it into HDMI jack on TV or monitor, then connect USB to -

Samsung Dongle Leak Suggests the Smartphone Maker Is Killing the Headphone Jack 5 August 2019, by Dalvin Brown
Samsung dongle leak suggests the smartphone maker is killing the headphone jack 5 August 2019, by Dalvin Brown While the latest development isn't groundbreaking for most, it may be disheartening if you're a Samsung user who still relies on a 3.5mm headphone jack to plug in earbuds. The Korean giant was one of the last major holdouts, so users who swear by wired headphones are increasingly running out of new smartphone options. If you aren't ready to ditch the cord and use wireless earbuds, you can buy headphones that connect via Lightning cable. Lightning headphones plug directly into the charging port of your device, however, the major downside is you can't listen to music and charge your smartphone at the same time. Credit: CC0 Public Domain ©2019 USA Today Distributed by Tribune Content Agency, LLC. Headphone jacks on new smartphones are a dying breed—first, Apple's got rid of the 3.5mm portals on iPhones and other flagship phone makers like Google, Sony, Motorola and Huawei followed suit, with the exception of a few models. Now, a leaked photo of a dongle appears to show that Samsung is heading in the same direction. Images of Samsung's upcoming 3.5mm to USC-B dongle have popped up online ahead of the South Korean smartphone maker's Galaxy Note 10 unveiling, which is set to happen in New York on August 7. A website for Samsung fans called SamMobile released the set of photos on Thursday, reporting that the adapter will most likely come packaged with the Galaxy Note 10 and Galaxy Note 10+. -

Neomediacast HDMI Dongle – NTV300D Data Sheet - Preliminary NTV300D the NETGEAR Difference
NTV300D Data Sheet NeoMediacast HDMI Dongle – NTV300D Data Sheet - Preliminary NTV300D The NETGEAR Difference • Small form-factor for easy installation • Best-in-class wireless connectivity for enhanced user experience • Seamless integration with NETGEAR home connectivity devices Benefits Android 4.2+ • Instantaneously turn any TV into a Smart TV with the latest Android applications • Easy portability of existing Android apps • Customizable platform for curated content and applications 802.11ac WiFi • Best-in-class wireless for best quality viewing experience even with HD quality video 1080p/60 full HD Video • No compromise in accessing the best content available Full-featured Android Set-top box Miracast-enabled • Wireless, intuitive sharing of content from mobile screen to big screen TV in your pocket Integrated Bluetooth® 4.0 • Bluetooth-enabled remote devices for easy access to content As service providers continue to develop and Integrated Digital Rights Management deploy multi-screen video initiatives, the need • Access to premium content for a platform that supports the quickest time- to-market for these initiatives is critical. The Whole Home System NETGEAR® NTV300D NeoMediacast® HDMI Dongle provides just that platform. Packing the features of a high-end set-top box, the NTV300D allows service providers to develop Broadcast and operate a curated content store leveraging the integrated Android SDK technology. By allowing for seamless portability of existing MSO Cloud/ Android applications, or cost-effectively IP Cloud developing new applications, the NTV300D Open IP Cloud ensures a complete media streaming solution for HMG7000 NTV300D plugged accessing both premium and free Over-the-Top in to an HDTV (OTT) content. -

USB 3.0* Radio Frequency Interference Impact on 2.4 Ghz Wireless Devices
USB 3.0* Radio Frequency Interference Impact on 2.4 GHz Wireless Devices White Paper April 2012 Document: 327216-001 INFORMATION IN THIS DOCUMENT IS PROVIDED IN CONNECTION WITH INTEL PRODUCTS. NO LICENSE, EXPRESS OR IMPLIED, BY ESTOPPEL OR OTHERWISE, TO ANY INTELLECTUAL PROPERTY RIGHTS IS GRANTED BY THIS DOCUMENT. EXCEPT AS PROVIDED IN INTEL'S TERMS AND CONDITIONS OF SALE FOR SUCH PRODUCTS, INTEL ASSUMES NO LIABILITY WHATSOEVER AND INTEL DISCLAIMS ANY EXPRESS OR IMPLIED WARRANTY, RELATING TO SALE AND/OR USE OF INTEL PRODUCTS INCLUDING LIABILITY OR WARRANTIES RELATING TO FITNESS FOR A PARTICULAR PURPOSE, MERCHANTABILITY, OR INFRINGEMENT OF ANY PATENT, COPYRIGHT OR OTHER INTELLECTUAL PROPERTY RIGHT. A "Mission Critical Application" is any application in which failure of the Intel Product could result, directly or indirectly, in personal injury or death. SHOULD YOU PURCHASE OR USE INTEL'S PRODUCTS FOR ANY SUCH MISSION CRITICAL APPLICATION, YOU SHALL INDEMNIFY AND HOLD INTEL AND ITS SUBSIDIARIES, SUBCONTRACTORS AND AFFILIATES, AND THE DIRECTORS, OFFICERS, AND EMPLOYEES OF EACH, HARMLESS AGAINST ALL CLAIMS COSTS, DAMAGES, AND EXPENSES AND REASONABLE ATTORNEYS' FEES ARISING OUT OF, DIRECTLY OR INDIRECTLY, ANY CLAIM OF PRODUCT LIABILITY, PERSONAL INJURY, OR DEATH ARISING IN ANY WAY OUT OF SUCH MISSION CRITICAL APPLICATION, WHETHER OR NOT INTEL OR ITS SUBCONTRACTOR WAS NEGLIGENT IN THE DESIGN, MANUFACTURE, OR WARNING OF THE INTEL PRODUCT OR ANY OF ITS PARTS. Intel may make changes to specifications and product descriptions at any time, without notice. Designers must not rely on the absence or characteristics of any features or instructions marked "reserved" or "undefined". -

Bringing Programability and Connectivity Into Isolated Vehicles
1 ProCMotive: Bringing Programability and Connectivity into Isolated Vehicles ARSALAN MOSENIA, Princeton University JAD F. BECHARA, Princeton University TAO ZHANG, Cisco Systems PRATEEK MITTAL, Princeton University MUNG CHIANG, Purdue University In recent years, numerous vehicular technologies, e.g., cruise control and steering assistant, have been proposed and deployed to improve the driving experience, passenger safety, and vehicle performance. Despite the existence of several novel vehicular applications in the literature, there still exists a signicant gap between resources needed for a variety of vehicular (in particular, data-dominant, latency-sensitive, and computationally-heavy) applications and the capabilities of already-in- market vehicles. To address this gap, dierent smartphone-/Cloud-based approaches have been proposed that utilize the external computational/storage resources to enable new applications. However, their acceptance and application domain are still very limited due to programability, wireless connectivity, and performance limitations, along with several security/privacy concerns. In this paper, we present a novel reference architecture that can potentially enable rapid development of various vehicular applications while addressing shortcomings of smartphone-/Cloud-based approaches. e architecture is formed around a core component, called SmartCore, a privacy/security-friendly programmable dongle that brings general-purpose computational and storage resources to the vehicle and hosts in-vehicle applications. -

HI762(Chromecast)Guide
HI762(Chromecast)guide Product display HI762(Chromecast)is a single of a receiver, can not use the mouse to operate. Data port :One HDMI + USB 2.0 Instructions for use HI762(Chromecast)and television through the HDMI connection; or use the HDMI extension line, One end is connected with the HI762(Chromecast), the other end is connected with the television. Introduction This document helps user to understand how to use RK2928 wireless HDMI dongle and what kind of devices they need to work with the dongle. Basically, RK2928 wireless HDMI dongle have implemented three features, Miracast (WiFi Display or WFD), DLNA and Airplay which are running on separate function mode, or rather, two different WIFI working mode. Function Description(1) Mode :Miracast Use steps: Step 1: Plug one end of the Micro USB cable into USB port and the other end into power adapter. Step 2: Plug one end of the HDMI cable into the HDMI port on the TV, and the other end into Miracast Receiver. Step 3: Switch TV on and turn to HDMI channel. And then, screen of TV says “Initializing”—“Waiting for connection”. Pair Mobile/Tablet and TV by Miracast Step 4: On your mobile/tablet(Android 4.2 in need, like M2).choose “Setting”.(*Connecting Wi-Fi before pair the devices.) Step 5: Turn on“WiFi”—choose “Display”—Turn on “WiFi Display”—“search display devices”( the name of valid device is as same on TV)—connect to the valid device. Step 6: Screen displaying from “Connection in progress” to Ready to display”, mobile/tablet and TV are now paired by Miracast.