RED HAT ENTERPRISE LINUX FEATURE BRIEF Application-Optimized Infrastructure with Containers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

IEEE Std 1003.1-2008
This preview is downloaded from www.sis.se. Buy the entire standard via https://www.sis.se/std-911530 INTERNATIONAL ISO/IEC/ STANDARD IEEE 9945 First edition 2009-09-15 Information technology — Portable Operating System Interface (POSIX®) Base Specifications, Issue 7 Technologies de l'information — Spécifications de base de l'interface pour la portabilité des systèmes (POSIX ®), Issue 7 Reference number ISO/IEC/IEEE 9945:2009(E) Copyright © 2001-2008, IEEE and The Open Group. All rights reserved This preview is downloaded from www.sis.se. Buy the entire standard via https://www.sis.se/std-911530 ISO/IEC/IEEE 9945:2009(E) PDF disclaimer This PDF file may contain embedded typefaces. In accordance with Adobe's licensing policy, this file may be printed or viewed but shall not be edited unless the typefaces which are embedded are licensed to and installed on the computer performing the editing. In downloading this file, parties accept therein the responsibility of not infringing Adobe's licensing policy. Neither the ISO Central Secretariat nor IEEE accepts any liability in this area. Adobe is a trademark of Adobe Systems Incorporated. Details of the software products used to create this PDF file can be found in the General Info relative to the file; the PDF-creation parameters were optimized for printing. Every care has been taken to ensure that the file is suitable for use by ISO member bodies and IEEE members. In the unlikely event that a problem relating to it is found, please inform the ISO Central Secretariat or IEEE at the address given below. -

Operating Systems Processes
Operating Systems Processes Eno Thereska [email protected] http://www.imperial.ac.uk/computing/current-students/courses/211/ Partly based on slides from Julie McCann and Cristian Cadar Administrativia • Lecturer: Dr Eno Thereska § Email: [email protected] § Office: Huxley 450 • Class website http://www.imperial.ac.uk/computing/current- students/courses/211/ 2 Tutorials • No separate tutorial slots § Tutorials embedded in lectures • Tutorial exercises, with solutions, distributed on the course website § You are responsible for studying on your own the ones that we don’t cover during the lectures § Let me know if you have any questions or would like to discuss any others in class 3 Tutorial question & warmup • List the most important resources that must be managed by an operating system in the following settings: § Supercomputer § Smartphone § ”Her” A lonely writer develops an unlikely relationship with an operating system designed to meet his every need. Copyright IMDB.com 4 Introduction to Processes •One of the oldest abstractions in computing § An instance of a program being executed, a running program •Allows a single processor to run multiple programs “simultaneously” § Processes turn a single CPU into multiple virtual CPUs § Each process runs on a virtual CPU 5 Why Have Processes? •Provide (the illusion of) concurrency § Real vs. apparent concurrency •Provide isolation § Each process has its own address space •Simplicity of programming § Firefox doesn’t need to worry about gcc •Allow better utilisation of machine resources § Different processes require different resources at a certain time 6 Concurrency Apparent Concurrency (pseudo-concurrency): A single hardware processor which is switched between processes by interleaving. -

Openextensions POSIX Conformance Document
z/VM Version 7 Release 1 OpenExtensions POSIX Conformance Document IBM GC24-6298-00 Note: Before you use this information and the product it supports, read the information in “Notices” on page 73. This edition applies to version 7, release 1, modification 0 of IBM z/VM (product number 5741-A09) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2018-09-12 © Copyright International Business Machines Corporation 1993, 2018. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents List of Tables........................................................................................................ ix About This Document............................................................................................xi Intended Audience......................................................................................................................................xi Conventions Used in This Document.......................................................................................................... xi Where to Find More Information.................................................................................................................xi Links to Other Documents and Websites.............................................................................................. xi How to Send Your Comments to IBM....................................................................xiii Summary of Changes for z/VM -

System Calls & Signals
CS345 OPERATING SYSTEMS System calls & Signals Panagiotis Papadopoulos [email protected] 1 SYSTEM CALL When a program invokes a system call, it is interrupted and the system switches to Kernel space. The Kernel then saves the process execution context (so that it can resume the program later) and determines what is being requested. The Kernel carefully checks that the request is valid and that the process invoking the system call has enough privilege. For instance some system calls can only be called by a user with superuser privilege (often referred to as root). If everything is good, the Kernel processes the request in Kernel Mode and can access the device drivers in charge of controlling the hardware (e.g. reading a character inputted from the keyboard). The Kernel can read and modify the data of the calling process as it has access to memory in User Space (e.g. it can copy the keyboard character into a buffer that the calling process has access to) When the Kernel is done processing the request, it restores the process execution context that was saved when the system call was invoked, and control returns to the calling program which continues executing. 2 SYSTEM CALLS FORK() 3 THE FORK() SYSTEM CALL (1/2) • A process calling fork()spawns a child process. • The child is almost an identical clone of the parent: • Program Text (segment .text) • Stack (ss) • PCB (eg. registers) • Data (segment .data) #include <sys/types.h> #include <unistd.h> pid_t fork(void); 4 THE FORK() SYSTEM CALL (2/2) • The fork()is one of the those system calls, which is called once, but returns twice! Consider a piece of program • After fork()both the parent and the child are .. -

Process Relationships (Chapter 9 )
Process Relationships (Chapter 9 ) Terminal Logins & Network Logins Process Groups and Sessions Job Control Relationships explained with examples Amy Lin, UAH 6/25/2019 Terminal Login Procedure init getty login shell “init” • At old time, the sysadmin would create a text file called /etc/ttys, each line would specify the device name and other parameters passed to getty • On Linux, the information is in /etc/inittab, a typical line in inittab is - 5:2345:respawn:/sbin/mingetty tty5 (man 5 inittab) - mingetty is almost the same as getty except it’s not suitable for serial line connections , you might consider to use (m)getty if dialup connection is needed. • On system startup, init reads inittab to get terminal information and fork/exec a “getty” process for each terminal “getty” • Calls open for the terminal device (read and write) • Opens descriptors 0, 1, and 2 to the device and outputs “login:” • Waits for someone to enter a user name Amy Lin, UAH 6/25/2019 The “login” After user enters a user name, login invokes exec function execle(“/bin/login”, “login”, “-p”, username, (char*)0, envp); • login calls “getpwnam” to fetch the password file entry • login reads the entered password, call crypt (3) to encrypt the password then compare to the encrypted password file entry • If log incorrectly, login exits with “1”, init then respawns getty to start over In successful login, login performs the following - Change to user’s home directory - Change permissions of terminal device so we can read from and write to it - Set group IDs - Initialize environment variables, such as PATH, HOME, SHELL, USER, LOGNAME Amy Lin, UAH 6/25/2019 The “shell” At the end of login process, a login shell is invoked with fork/exec execl(“/bin/sh”,“-sh”,(char*)0) - The prefix “-” before argv[0] is a flag to all the shells that they are being invoked as a login shell. -

C-Balancer: a System for Container Profiling and Scheduling
1 C-Balancer: A System for Container Profiling and Scheduling Akshay Dhumal∗, Dharanipragada Janakiramy Department of Computer Science, Indian Institute of Technology Madras Email: ∗[email protected], [email protected] Abstract—Linux containers have gained high popularity in that can be grouped under namespaces are process PID, file recent times. This popularity is significantly due to various advan- system mount points, interprocess communication, network, tages of containers over Virtual Machines (VM). The containers etc. The resource management for a container is done by are lightweight, occupy lesser storage, have fast boot up time, easy to deploy and have faster auto-scaling. The key reason control groups (cgroups) [5], that limits the resource usage behind the popularity of containers is that they leverage the per process group. Using cgroups, it is possible to bound the mechanism of micro-service style software development, where resources (CPU, memory, I/O) of a container. The OS based applications are designed as independently deployable services. container virtualization significantly gained mass attention and There are various container orchestration tools for deploying and adoption with the release of Docker, which is a container managing the containers in the cluster. The prominent among them are Docker Swarm, and Kubernetes. However, they do orchestration and management tool designed to simplify the not address the effects of resource contention when multiple creation and deployment of containers on a single host. With containers are deployed on a node. Moreover, they do not provide the growing usage and popularity, the containers were seen as support for container migration in the event of an attack or a replacement for VM in public and private cloud operations. -

Project Shell 2 Due: November 6, 2019 at 11:59Pm
CSCI0330 Intro Computer Systems Doeppner Project Shell 2 Due: November 6, 2019 at 11:59pm 1 Introduction 2 Before you write any code, read this handout in its entirety. 2 2 Assignment 2 2.1 Stencil 2 2.2 Jobs vs. Processes 3 2.3 Foreground vs. Background 3 2.4 Specifications 3 3 Signals 5 3.0 Sending Signals 6 3.1 Ignoring Signals 6 3.2 Signal Handling in the Child Process 6 3.3 Process Groups 6 4 Multiple Jobs 7 4.1 Process State 8 5 Reaping 8 5.1 Reaping a Child Process 9 6 fg and bg 10 7 Support Code 10 8 Library Functions 12 9 Testing Your Shell 12 9.1 Format of the Tracefiles 13 9.2 Test Executables 13 9.3 Demo 13 9.4 Error Checking 13 9.5 Shell Clean Up 13 10 GDB Tips for Shell 2 14 10.1 handle signal 14 10.2 catch signal 14 11 Grading 14 1 CSCI0330 Project Shell 2 October 31, 2018 12 Handing In 14 1 Introduction Tom was drifting through the water with his new chum the magic conch. Suddenly, an enormous tentacle emerged from the depths of the ocean and speared into the heart of his friend, splitting the shell evenly in two. Tom was otterly overwhelmed with emocean and blinked mildly, looking at his friends, shell_1 and shell_2. Shell_2 was trying to communicate, but Tom couldn’t quite catch the signals. Kelp Tom reestablish connection with his shelly friends. CTRL-\. Now, your shell can run only one program at a time since it runs programs in the foreground, occupying the entire shell. -

RAIK 284H, Spring 2010 Writing Your Own Unix Shell Assigned: Apr. 1, Due: Thur., Apr
RAIK 284H, Spring 2010 Writing Your Own Unix Shell Assigned: Apr. 1, Due: Thur., Apr. 15, 9:00PM Dylan Douglas ([email protected]) is the lead person for this assignment. Introduction The purpose of this assignment is to become more familiar with the concepts of process control and sig- nalling. You’ll do this by writing a simple Unix shell program that supports job control. Logistics You may work in a group of up to two people in solving the problems for this assignment. The only “hand- in” will be electronic. Any clarifications and revisions to the assignment will be posted on the course Web page. Hand Out Instructions Start by copying the file shlab-handout.tar to the protected directory (the lab directory) in which you plan to do your work. Then do the following: • Type the command tar xvf shlab-handout.tar to expand the tarfile. • Type the command make to compile and link some test routines. • Type your team member names and CSE/cree login names in the header comment at the top of tsh.c. Looking at the tsh.c (tiny shell) file, you will see that it contains a functional skeleton of a simple Unix shell. To help you get started, we have already implemented the less interesting functions. Your assignment is to complete the remaining empty functions listed below. As a sanity check for you, we’ve listed the approximate number of lines of code for each of these functions in our reference solution (which includes lots of comments). 1 • eval: Main routine that parses and interprets the command line. -

Signals Kernel Software This Lecture Non‐Local Jumps Application Code Carnegie Mellon Today
Carnegie Mellon Introduction to Computer Systems 15‐213/18‐243, Fall 2009 12th Lecture Instructors: Greg Ganger and Roger Dannenberg Carnegie Mellon Announcements Final exam day/time announced (by CMU) 5:30‐8:30pm on Monday, December 14 Cheating… please, please don’t Writing code together counts as “sharing code” – forbidden “Pair programming”, even w/o looking at other’s code – forbidden describing code line by line counts the same as sharing code Opening up code and then leaving it for someone to enjoy – forbidden in fact, please remember to use protected directories and screen locking Talking through a problem can include pictures (not code) –ok The automated tools for discovering cheating are incredibly good …please don’t test them Everyone has been warned multiple times cheating on the remaining labs will receive no mercy Carnegie Mellon ECF Exists at All Levels of a System Exceptions Hardware and operating system kernel Previous Lecture software Signals Kernel software This Lecture Non‐local jumps Application code Carnegie Mellon Today Multitasking, shells Signals Long jumps Carnegie Mellon The World of Multitasking System runs many processes concurrently Process: executing program State includes memory image + register values + program counter Regularly switches from one process to another Suspend process when it needs I/O resource or timer event occurs Resume process when I/O available or given scheduling priority Appears to user(s) as if all processes executing simultaneously Even though most systems -

Inter-Process Communication Mechanisms (IPC)
Inter-Process Communication Mechanisms (IPC) Signals Pipes Message Queues Semaphores Shared Memory Signals v Signal: a mechanism to notify process of system events ™ Asynchronous notification ™ Synchronous errors or exceptions v Invoke signals ™ Processes may send each other signals by kill system call, ™ Kernel may send signals to a process. v A process may react to a signal by ™ Ignore the signal ™ handle signals itself v Asynchronously execute a specified procedure (the signal handler) Signals (Cont.) v A set of defined signals ™ 1)SIGHUP 2) SIGINT 3) SIGQUIT ™ 4) SIGILL 5) SIGTRAP 6) SIGIOT ™ 7) SIGBUS 8) SIGFPE 9) SIGKILL ™ 10) SIGUSR1 11) SIGSEGV 12) SIGUSR2 ™ 13) SIGPIPE 14) SIGALR 15)SIGTERM ™ 17) SIGCHLD 18) SIGCONT 19) SIGSTOP ™ 20) SIGTSTP 21) SIGTTIN 22) SIGTTOU ™ 23) SIGURG 24) SIGXCPU 25) SIGXFSZ ™ 26) SIGVTALRM 27) SIGPROF 28) SIGWINCH ™ 29) SIGIO 30) SIGPWR Signals (Cont.) v Kernel handles signals using default actions. ™ Terminate the process ™ Core dump and terminate the process v E.g., SIGFPE(floatingpoint exception) : core dump and exit ™ Ignore the signal ™ Suspend the process ™ Resume the process’s execution, if it was stopped v Signal related fields in task_struct data structure ™ signal (32 bits):pending signals ™ blocked: a mask of blocked signal ™ sigaction array: address of handling routine or a flag to let kernel handle the signal Linux Signals v Normal process can only send signals to processes with the same uid and gid or to the processes in the same process group Note: Process Group v Unix introduces the -

IBM Systems - Iseries
IBM Systems - iSeries i5/OS PASE APIs Version 5 Release 4 IBM Systems - iSeries i5/OS PASE APIs Version 5 Release 4 Note Before using this information and the product it supports, be sure to read the information in “Notices,” on page 85. Sixth Edition (February 2006) This edition applies to version 5, release 4, modification 0 of IBM i5/OS (product number 5722-SS1) and to all subsequent releases and modifications until otherwise indicated in new editions. This version does not run on all reduced instruction set computer (RISC) models nor does it run on CISC models. © Copyright International Business Machines Corporation 1998, 2006. All rights reserved. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents i5/OS PASE APIs . .1 Parameters . .16 APIs . .1 Authorities . .16 i5/OS PASE Callable Program APIs . .1 Return Value . .16 QP2SHELL() and QP2SHELL2()—Run an i5/OS Related Information . .16 PASE Shell Program . .2 Qp2free()—Free i5/OS PASE Heap Memory . .16 Parameters . .2 Parameters . .16 Authorities . .2 Authorities . .16 Return Value . .3 Return Value . .16 Error Messages . .3 Related Information . .16 Usage Notes . .3 Qp2jobCCSID()—Retrieve Job CCSID for i5/OS Related Information . .5 PASE . .17 QP2TERM()—Run an i5/OS PASE Terminal Session .5 Parameters . .17 Parameters . .5 Authorities . .17 Authorities . .5 Return Value . .17 Return Value . .5 Related Information . .17 Error Messages . .6 Qp2malloc()—Allocate i5/OS PASE Heap Memory 17 Usage Notes . .6 Parameters . .18 Related Information . .6 Authorities . .18 i5/OS PASE ILE Procedure APIs . .6 Return Value . -
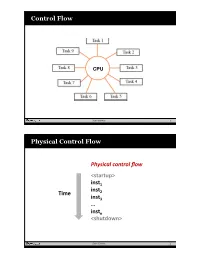
Process-Slides.Pdf
Control Flow CPU Sean Barker 1 Physical Control Flow Physical control flow <startup> inst1 inst Time 2 inst3 … instn <shutdown> Sean Barker 2 Operating System User-level Applications Operating System Hardware Resources Sean Barker 3 Processes Memory Memory Memory Stack Stack Stack Heap Heap Heap Data Data … Data Code Code Code CPU CPU CPU Registers Registers Registers Sean Barker 4 Control Flow Abstraction Process A Process B Process C Time Sean Barker 5 Control Flow Time-Sharing Process A Process B Process C Time Sean Barker 6 Context Switching Process A Process B user code kernel code context switch Time user code kernel code context switch user code 11/12/15 Sean Barker 7 Exceptions:'hardware/support/for/OS/ Interrupt'Vector stored/in/memory Exceptions special/register/holds/base/address transfer' control' to'OS'in'response' to'event What'code'should'the'OS'run'to'handle'the'event? code/for// Unique'ID'per'type'of'event exception/handler/ 0 Exception Ta bl e code/for/ ID'='index'into'exception'table' User-Process OS exception/handler/ 1 0 (a.k.a./interrupt/vector) 1 code/for exception 2 event' ... exception/handler/ 2 Handler'i is'called'each'time' exception'processing n&1 exception'i occurs by/exception'handler ... return'or'abort code/for/ exception/handler/ n<1 Exception/ numbers a/ jump/table/ for/exceptions… 9 10 Sean Barker 8 Open'a'file (trap/system/ call) Segmentation'Fault User/process/calls:/open(filename, options) int a[1000]; open executes/system/call/instruction/int void bad () { Write/to/invalid/memory/location. a[5000] = 13; 0804d070 <__li b c _o p e n>: } .