Hierarchical Brokering with Feedback Control Framework in Mobile Device-Centric Clouds
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Factory Model Device Model
Factory Model Device Model Acer A1-713 acer_aprilia Acer A1-811 mango Acer A1-830 ducati Acer A3-A10 G1EA3 Acer A3-A10 mtk6589_e_lca Acer A3-A10 zara Acer A3-A20 acer_harley Acer A3-A20FHD acer_harleyfhd Acer Acer E320-orange C6 Acer Aspire A3 V7 Acer AT390 T2 Acer B1-723 oban Acer B1-730 EverFancy D40 Acer B1-730 vespatn Acer CloudMobile S500 a9 Acer DA220HQL lenovo72_we_jb3 Acer DA222HQL N451 Acer DA222HQLA A66 Acer DA222HQLA Flare S3 Power Acer DA226HQ tianyu72_w_hz_kk Acer E330 C7 Acer E330 GT-N7105T Acer E330 STUDIO XL Acer E350 C8n Acer E350 wiko Acer G100W maya Acer G1-715 A510s Acer G1-715 e1808_v75_hjy1_5640_maxwest Acer Icona One 7 vespa Acer Iconia One 7 AT1G* Acer Iconia One 7 G1-725 Acer Iconia One 7 m72_emmc_s6_pcb22_1024_8g1g_fuyin Acer Iconia One 7 vespa2 Acer Iconia One 8 vespa8 Acer Iconia Tab 7 acer_apriliahd Acer Iconia Tab 8 ducati2fhd Acer Iconia Tab 8 ducati2hd Acer Iconia Tab 8 ducati2hd3g Acer Iconia Tab 8 Modelo II - Professor Acer Iconia Tab A100 (VanGogh) vangogh Acer Iconia Tab A200 s7503 Acer Iconia Tab A200 SM-N9006 Acer Iconia Tab A501 ELUGA_Mark Acer Iconia Tab A501 picasso Acer Iconia Tab A510 myPhone Acer Iconia Tab A510 picasso_m Acer Iconia Tab A510 ZUUM_M50 Acer Iconia Tab A701 picasso_mf Acer Iconia Tab A701 Revo_HD2 Acer Iconia TalkTab 7 acer_a1_724 Acer Iconia TalkTab 7 AG CHROME ULTRA Acer Liquid a1 Acer Liquid C1 I1 Acer Liquid C1 l3365 Acer Liquid E1 C10 Acer Liquid E2 C11 Acer Liquid E3 acer_e3 Acer Liquid E3 acer_e3n Acer Liquid E3 LS900 Acer Liquid E3 Quasar Acer Liquid E600 e600 Acer Liquid -

Compatibility Sheet
COMPATIBILITY SHEET SanDisk Ultra Dual USB Drive Transfer Files Easily from Your Smartphone or Tablet Using the SanDisk Ultra Dual USB Drive, you can easily move files from your Android™ smartphone or tablet1 to your computer, freeing up space for music, photos, or HD videos2 Please check for your phone/tablet or mobile device compatiblity below. If your device is not listed, please check with your device manufacturer for OTG compatibility. Acer Acer A3-A10 Acer EE6 Acer W510 tab Alcatel Alcatel_7049D Flash 2 Pop4S(5095K) Archos Diamond S ASUS ASUS FonePad Note 6 ASUS FonePad 7 LTE ASUS Infinity 2 ASUS MeMo Pad (ME172V) * ASUS MeMo Pad 8 ASUS MeMo Pad 10 ASUS ZenFone 2 ASUS ZenFone 3 Laser ASUS ZenFone 5 (LTE/A500KL) ASUS ZenFone 6 BlackBerry Passport Prevro Z30 Blu Vivo 5R Celkon Celkon Q455 Celkon Q500 Celkon Millenia Epic Q550 CoolPad (酷派) CoolPad 8730 * CoolPad 9190L * CoolPad Note 5 CoolPad X7 大神 * Datawind Ubislate 7Ci Dell Venue 8 Venue 10 Pro Gionee (金立) Gionee E7 * Gionee Elife S5.5 Gionee Elife S7 Gionee Elife E8 Gionee Marathon M3 Gionee S5.5 * Gionee P7 Max HTC HTC Butterfly HTC Butterfly 3 HTC Butterfly S HTC Droid DNA (6435LVW) HTC Droid (htc 6435luw) HTC Desire 10 Pro HTC Desire 500 Dual HTC Desire 601 HTC Desire 620h HTC Desire 700 Dual HTC Desire 816 HTC Desire 816W HTC Desire 828 Dual HTC Desire X * HTC J Butterfly (HTL23) HTC J Butterfly (HTV31) HTC Nexus 9 Tab HTC One (6500LVW) HTC One A9 HTC One E8 HTC One M8 HTC One M9 HTC One M9 Plus HTC One M9 (0PJA1) -

Smartphone Price List
SMARTPHONE PRICE LIST Brand Part Number Description Status Colour Normal Price Oh Yes Price MF352MYA / MF353MYA Apple iPhone 5S 16GB Space Gray / Silver RM 1,699 RM 1,699 MGC472MYA / MGD482MYA / MGE492MYA iPhone 6 16GB Space Gray / Silver / Gold RM 2,699 RM2,699 MGF4F2MYA /MGG4H2MYA /MGH4J2MYA iPhone 6 64GB Space Gray / Silver / Gold RM 3,199 RM3,199 MGI4A2MYA / MGJ4C2MYA / MGK4E2MYA iPhone 6 128GB Space Gray / Silver / Gold RM 3,550 RM3,550 MGLA82MYA / MGMA92MYA / MGNAA2MYA iPhone 6 Plus 16GB Space Gray / Silver / Gold RM 3,199 RM3,199 MGOAH2MYA / MGPAJ2MYA / MGQAK2MYA iPhone 6 Plus 64GB Space Gray / Silver / Gold RM 3,699 RM3,699 MGRAC2MYA / MGSAE2MYA / MGTAF2MYA iPhone 6 Plus 128GB Space Gray / Silver / Gold RM 3,974 RM3,974 MKU12MY/A , MKQK2MY/A , MKU32MY/A , MKQM2MY/A iPhone 6s 16GB Space Gray / Silver / Gold / Rose Gold RM 3,199 RM 3,199 MKQN2MY/A , MKQP2MY/A , MKQQ2MY/A , MKQR2MY/A iPhone 6s 64GB Space Gray / Silver / Gold / Rose Gold RM 3,699 RM 3,699 MKQT2MY/A , MKQU2MY/A , MKQV2MY/A , MKQW2MY/A iPhone 6s 128GB Space Gray / Silver / Gold / Rose Gold RM 4,199 RM 4199 MKU12MY/A , MKU22MY/A , MKU32MY/A , MKU52MY/A iPhone 6s Plus 16GB Space Gray / Silver / Gold / Rose Gold RM 3,699 RM 3,699 MKU62MY/A , MKU72MY/A , MKU82MY/A , MKU92MY/A iPhone 6s Plus 64GB Space Gray / Silver / Gold / Rose Gold RM 4,199 RM 4,199 MKUD2MY/A , MKUE2MY/A, MKUF2MY/A , MKUG2MY/A iPhone 6s Plus 128GB Space Gray / Silver / Gold / Rose Gold RM 4,699 RM 4,699 E1200Y Keystone 2 Black / White RM 89 RM 89 G318HZ Galaxy V Plus Black / White RM 299 RM 299 J110G/DS -

Electronic 3D Models Catalogue (On July 26, 2019)
Electronic 3D models Catalogue (on July 26, 2019) Acer 001 Acer Iconia Tab A510 002 Acer Liquid Z5 003 Acer Liquid S2 Red 004 Acer Liquid S2 Black 005 Acer Iconia Tab A3 White 006 Acer Iconia Tab A1-810 White 007 Acer Iconia W4 008 Acer Liquid E3 Black 009 Acer Liquid E3 Silver 010 Acer Iconia B1-720 Iron Gray 011 Acer Iconia B1-720 Red 012 Acer Iconia B1-720 White 013 Acer Liquid Z3 Rock Black 014 Acer Liquid Z3 Classic White 015 Acer Iconia One 7 B1-730 Black 016 Acer Iconia One 7 B1-730 Red 017 Acer Iconia One 7 B1-730 Yellow 018 Acer Iconia One 7 B1-730 Green 019 Acer Iconia One 7 B1-730 Pink 020 Acer Iconia One 7 B1-730 Orange 021 Acer Iconia One 7 B1-730 Purple 022 Acer Iconia One 7 B1-730 White 023 Acer Iconia One 7 B1-730 Blue 024 Acer Iconia One 7 B1-730 Cyan 025 Acer Aspire Switch 10 026 Acer Iconia Tab A1-810 Red 027 Acer Iconia Tab A1-810 Black 028 Acer Iconia A1-830 White 029 Acer Liquid Z4 White 030 Acer Liquid Z4 Black 031 Acer Liquid Z200 Essential White 032 Acer Liquid Z200 Titanium Black 033 Acer Liquid Z200 Fragrant Pink 034 Acer Liquid Z200 Sky Blue 035 Acer Liquid Z200 Sunshine Yellow 036 Acer Liquid Jade Black 037 Acer Liquid Jade Green 038 Acer Liquid Jade White 039 Acer Liquid Z500 Sandy Silver 040 Acer Liquid Z500 Aquamarine Green 041 Acer Liquid Z500 Titanium Black 042 Acer Iconia Tab 7 (A1-713) 043 Acer Iconia Tab 7 (A1-713HD) 044 Acer Liquid E700 Burgundy Red 045 Acer Liquid E700 Titan Black 046 Acer Iconia Tab 8 047 Acer Liquid X1 Graphite Black 048 Acer Liquid X1 Wine Red 049 Acer Iconia Tab 8 W 050 Acer -

ASUS Fonepad Series ASUS Fonepad 7 (FE171CG) | 22 ASUS Fonepad 8 (FE380CG) | 24
ASUS PRODUCT See what others can’t see With the ZenFone 2, you’ll discover a new universe of possibilities. GUIDE FOR SMARTPHONE & TABLET May - June 2015 with 400% better color contrast & brightness Fast speed with 4GB RAM, 2.3GHz Super Quad Core Intel® Atom™ Processor 5.5’’ Full HD IPS Panel with 72% screen-to-body ratio for best entertainment See What Others Can’t See www.asus.com/my | Image by Robert Jahns ZE551ML Design Story ASUS ZenFone 2 with Intel Inside® Design Story Zen Spirit The Ultimate Beautifully and The perfect balance of Beauty and Strength Beauty & Precisely Crafted Zen means a balance of beauty and strength. It is also an introduction to new values that enhance the user experience in an entirely new way, custom-built for a dawning Strength From the 3.9mm Ultra-Thin Edge to era of more active where lifestyle, technology, and thought are one and the same. Zen the delicate 0.4mm Laser Drilled Speaker is also an attitude, a different way of living that brings happiness in every moment. ASUS ZenFone 2 is a Pure Power ASUS ZenFone™ 2 has an incredibly slim profi le, it is just 3.9mm at the thinnest edge. This is more than an impressive engineering feat: the thin design Zen can be trendy and the spirit of ASUS ZenFone™ is empowering luxury for every- encased in Sheer Beauty is so comfortable to hold, and makes using ASUS ZenFone™ 2 easier. This also allows ASUS ZenFone™ 2 to eliminate the visual and physical obstacle on one. -

Liste Des Appareils Compatibles Table Des Matières
Liste des appareils compatibles Table des matières Acer 3 TELEEPOCH 17 Apple 3 VERTU 17 Archos 3 VESTEL 17 Asus 3 Wind River 17 CJSC Explay 3 XIAOMI 17 Cellon 3 ZTE 17 Compal 3 Autre 18 Coolpad 4 Dell 4 Digi-in 4 DORO 4 Fly 4 Foxconn international holdings limited 4 Fujitsu 4 Gigabyte 5 Google 5 HP 5 HTC 5 Hisense 6 Huawei 6 KYOCERA CORPORATION 7 LGE 7 LENOVO mobile 8 Mediatek 9 Micromax 9 Mobiwire 9 MOTOROLA 10 NVidia 10 OPPO 10 PANASONIC CORPORATION 10 PANTECH 10 PEGATRON 10 POSITIVO 10 SHARP 11 SK TELESYS 11 SAMSUNG 11 SONY 14 SONY ERICSSON 14 SYMPHONY TELECA 15 TCT MOBILE LIMITED (ALCATEL) 15 2 Acer Fonepad 7(FE375CXG)– K019_2 Liquid X1– s3 Fonepad 7 LTE– K01Q Liquid Jade– acer_S55 PadFone mini– ASUS-T00C Liquid Z500– acer_Z500 ZenFone 6– ASUS_Z002 Liquid Z4– acer_Z6 Fonepad 7 (FE375CXG)– K019_4 Liquid Z205– acer_z205p ASUS Fonepad 8– K016_2 Liquid Jade S– acer_S56 PadFone Infinity– ASUS-A80 E380– acer_e3n Padfone X– ASUS-T00D Iconia Tab 7– acer_apriliahd ZenFone 4– ASUS_T00Q Liquid E600– e600 Fonepad 7– K012 Liquid S1– a10 ASUS Fonepad 7 LTE– K00Y Liquid Z410– acer_z410 PadFone 2– A68 Liquid Z205– acer_z205 ZenFone 5 LTE– ASUS_T00P Iconia TalkTab 7– acer_a1_724 Fonepad 7– K00Z Liquid E3– acer_e3 ZenFone 5– ASUS_T00F Iconia Tab 7– acer_aprilia Padfone mini– ASUS-T00S Liquid Z200– acer_z200 Liquid E700– acer_e39 CJSC Explay Craft– Craft Apple Prime– Prime Iphone 4s ou plus récent Gravity– T4728 IPad 2 ou plus récent – Incompatible avec Pulsar– Pulsar MyCompanion Tornado– Tornado Hit– Hit Archos ATV– ATV Archos 70 Copper– ac70cv Shine– -

Fonepad Is Calling a Tablet, Smartphone, and 8-Megapixel Camera in the Palm of Your Hand Crystal-Clear Photos Palmed Portability Multi-Core Performance
ASUS PRODUCT GUIDE FOR SMARTPHONE & TABLET March - April 2015 FE171CG Fonepad is Calling A tablet, smartphone, and 8-Megapixel camera in the palm of your hand Crystal-Clear Photos Palmed Portability Multi-Core Performance Intel, the Intel logo, Intel Atom, Intel Inside, the Intel Inside logo are trademarks of Intel Corporation in the U.S. and/or other countries. *Other names and brands may be claimed as the property of others PROMOTION ASUS Fonepad™ 7 with Intel Inside® ASUS Fonepad™ 7 with Intel Inside® Fonepad is Calling The perfect combination of tablet and smartphone in one hand SPECIFICATIONS MODEL: FE170CG • Intel® Atom™ Processor Z2520 (1.2GHz) • Android™ 4.4 KitKat Bundle with • 7" LED Backlight WSVGA (1024x600) Persona • 1GB Memory Cover • 8GB Storage + Free 16GB ASUS WebStorage for 1 Year (Worth RM89) • 3G, Bluetooth 4.0, Wi-Fi, 802.11 b/g/n • 0.3 MP Front Camera, 2 MP Rear Camera • Up to 10* Hours of Battery Life • GPS A-GPS & Glonass,G-Sensor, E-compass, Proximity, Ambient Light Sensor • Talk Time - 30 hours (3G) RM • Dimension - 192 x 110 x 10.7mm | 290gr • Color - Black, White, Blue & Red • 1 Year Local Warranty 429 ASUS FONEPAD 7 : FONEPAD IS CALLING 03 ABOUT ASUS ASUS Fonepad™ 7 with Intel Inside® ASUS Fonepad™ 7 with Intel Inside® CONTENT ASUS Awards No.2 in Finland ANDROID No.3 in Norway ASUS Awards & Review | 06 TABLET No.3 in Sweden TOP No.1 in Rusia ASUS ZenUI No.2 in Netherlands BRAND No.2 in Belgium 10 | ZenUI Vision 2 No.3 in Denmark Worldwide in unit shipment 11 | What’s Next, Do It Later IDC (Q2, 2013) No.1 in -

Factory Model Device Model
Factory Model Device Model Acer A1-713 acer_aprilia Acer A1-830 Avvio_753 Acer A1-830 X958E Acer A3-A20 8675 Acer Acer E320-orange C6 Acer Acer E320-orange Oysters T72MR 3G Acer AT390 QMobile i10 Acer AT390 T2 Acer AT390 Xiaomi Acer B1-723 oban Acer B1-730 a29 Acer B1-820 i-mobile2.8 Acer CloudMobile S500 a9 Acer DA220HQL gilda_p8081 Acer DA226HQ sm618_w_ztc_72lca Acer E120 K2 Acer E310 lava75_cu_jb Acer E330 A37 Acer E330 C7 Acer E330 G910 Acer E330 msm8x25q_d5 Acer E330 Z50_Nova Acer E350 C8n Acer G100W F13 Acer Iconia Tab 7 acer_apriliahd Acer Iconia Tab A211 g12refM805 Acer Iconia Tab A211 MYPHONE_AGUA_OCEAN_MINI Acer Iconia Tab A501 E353I Acer Iconia Tab A510 K235 Acer Iconia TalkTab 7 acer_a1_724 Acer Iconia TalkTab 7 d3268_ctp_q_mobile Acer Liquid a1 Acer Liquid C1 I1 Acer Liquid C1 s620_f_h1_trx_j401_ec Acer Liquid E1 C10 Acer Liquid E2 C11 Acer Liquid E3 acer_e3 Acer Liquid E3 acer_e3n Acer Liquid E3 D7.2 3G Acer Liquid E3 hedy89_we_jb2 Acer Liquid E3 SOLO Acer Liquid E600 e600 Acer Liquid E600 S5J Acer Liquid E600 z3368 Acer Liquid E700 acer_e39 Acer Liquid Gallant E350 C8 Acer Liquid Jade acer_S55 Acer Liquid Jade S acer_S56 Acer Liquid Jade Z ABCD Acer Liquid Jade Z acer_S57 Acer Liquid Jade Z k002_gfen Acer Liquid Jade Z mobiistar BUDDY Acer Liquid Mini Bmobile.AX800 Acer Liquid Mini C4R Acer Liquid S1 a10 Acer Liquid S2 a12 Acer Liquid S2 B706 Acer Liquid S3 FIREFLY_S10DUAL Acer Liquid S3 s3 Acer Liquid X2 acer_S59 Acer Liquid X2 g517_d1e_less26 Acer Liquid Z200 A1000s Acer Liquid Z200 acer_z200 Acer Liquid Z200 s9201b Acer -

Fnac Reprise
FNAC REPRISE Liste des smartphones éligibles au programme de reprise au 19/08/2016 ACER LIQUID Z4 APPLE IPHONE 5 BLACK 64GB ACER INCORPORATED LIQUID Z530S APPLE IPHONE 5 WHITE 16GB ACER INCORPORATED LIQUID Z630S APPLE IPHONE 5 WHITE 32GB ALBA ALBA 4.5INCH 5MP 4G 8GB APPLE IPHONE 5 WHITE 64GB ALBA DUAL SIM APPLE IPHONE 5C ALCATEL IDOL 3 8GB APPLE IPHONE 5C BLUE 16GB ALCATEL ONE TOUCH 228 APPLE IPHONE 5C BLUE 32GB ALCATEL ONE TOUCH 903 APPLE IPHONE 5C BLUE 8GB ALCATEL ONE TOUCH 903X APPLE IPHONE 5C GREEN 16GB ALCATEL ONE TOUCH IDOL 2 MINI S APPLE IPHONE 5C GREEN 32GB ALCATEL ONE TOUCH TPOP APPLE IPHONE 5C GREEN 8GB ALCATEL ONETOUCH POP C3 APPLE IPHONE 5C PINK 16GB AMAZON FIRE PHONE APPLE IPHONE 5C PINK 32GB APPLE APPLE WATCH EDITION 42MM APPLE IPHONE 5C PINK 8GB APPLE IPHONE 3G APPLE IPHONE 5C WHITE 16GB APPLE IPHONE 3G BLACK 16GB APPLE IPHONE 5C WHITE 32GB APPLE IPHONE 3G BLACK 8GB APPLE IPHONE 5C WHITE 8GB APPLE IPHONE 3G WHITE 16GB APPLE IPHONE 5C YELLOW 16GB APPLE IPHONE 3GS APPLE IPHONE 5C YELLOW 32GB APPLE IPHONE 3GS 8GB APPLE IPHONE 5C YELLOW 8GB APPLE IPHONE 3GS BLACK 16GB APPLE IPHONE 5S APPLE IPHONE 3GS BLACK 32GB APPLE IPHONE 5S BLACK 16GB APPLE IPHONE 3GS WHITE 16GB APPLE IPHONE 5S BLACK 32GB APPLE IPHONE 3GS WHITE 32GB APPLE IPHONE 5S BLACK 64GB APPLE IPHONE 4 APPLE IPHONE 5S GOLD 16GB APPLE IPHONE 4 BLACK 16GB APPLE IPHONE 5S GOLD 32GB APPLE IPHONE 4 BLACK 32GB APPLE IPHONE 5S GOLD 64GB APPLE IPHONE 4 BLACK 8GB APPLE IPHONE 5S WHITE 16GB APPLE IPHONE 4 WHITE 16GB APPLE IPHONE 5S WHITE 32GB APPLE IPHONE 4 WHITE 32GB APPLE IPHONE -

Destekleyen Telefon Listesini Görmek İçin Tıklayınız
Sayfa1 Görüntü Marka Model Ürün Ses Aktarımı Aktarımı 360 360 Hayır Hayır Acer S510 Acer Liquid S1 Evet Evet alps Q1 alps Q1 Evet Evet alps N5 Amazon alps N5 Evet Evet Amazon KFSAWI KFSAWI Hayır Evet Android ARCHOST552 101 ARCHOSHuawei T552 101 Evet Evet Archos Xenon Lite AsusXenon PadFone Lite Hayır Evet Asus PadFone T004 AsusInfinity fonepad 2 Evet Evet Asus K01Q Asus7 LTE ZenFone Evet Evet Asus Asus Asus_Z00AD 2 ZE551ML Evet Evet ZENFONEAsus ZenFone 2 Asus Asus_T00J LASERAsus5 ZenFone Evet Evet Asus Asus_T00G ZE601KL6 Evet Evet Asus Asus_Z011D AsusZ011D MeMO Evet Evet Asus Asus K01A PAD Evet Evet ZENFONE 2 Asus Asus_Z00LD LASERAsus Google Hayır Evet Asus Nexus 7 ZE601KLNexus 7 Hayır Evet Asus Asus_Z011D Z011D Hayır Evet BBK vivo Xshot vivo Xshot Evet Evet BBK vivo X5L vivo X5 Evet Evet BBK BLUvivo X710LSTUDIO BLUvivo XshotSTUDIO Hayır Evet BLU 7.0 LTE 7.0 LTE Evet Evet Foxconn BOWAY Pro InternationalBOWAY BOWAY_V95 ERENEBENV95 Evet Evet HoldingsERENEBEN EBEN M2 EBEN M2 Hayır Evet Limited InFocus M320 FUJITSUInFocus M320 Hayır Evet FUJITSU RM02 Gionee GN500arrows M02 Evet Evet GiONEE GN5001 1 Evet Evet GiONEE F103 GiONEEGionee F103 M5 Evet Evet GiONEE GN8001 GioneePlus TD-LTE Evet Evet GiONEE GN5001S GiONEE F103GN5001S Evet Evet GiONEE F103L L Hayır Evet GuangXin KINGSUN-F4 KINGSUN F4 Hayır Evet GUOMI GUOMI A9 HTCGUOMI Desire A9 Hayır Evet HTC HTCHTC_D728x One_M8 HTC728 dual ONE sim M8 Evet Evet HTC HTCdual simOne DUAL SIM Evet Evet HTC E9PLUSNexus 9 dual HTC OneNexus M9 9 Evet Evet HTC sim PLUS Evet Evet HTC HTCHTC_M10h Desire HTC -
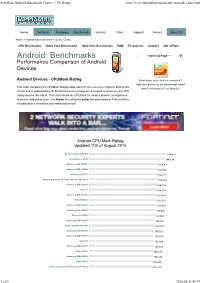
Passmark Android Benchmark Charts - CPU Rating
PassMark Android Benchmark Charts - CPU Rating http://www.androidbenchmark.net/cpumark_chart.html Home Software Hardware Benchmarks Services Store Support Forums About Us Home » Android Benchmarks » Device Charts CPU Benchmarks Video Card Benchmarks Hard Drive Benchmarks RAM PC Systems Android iOS / iPhone Android TM Benchmarks ----Select A Page ---- Performance Comparison of Android Devices Android Devices - CPUMark Rating How does your device compare? Add your device to our benchmark chart This chart compares the CPUMark Rating made using PerformanceTest Mobile benchmark with PerformanceTest Mobile ! results and is updated daily. Submitted baselines ratings are averaged to determine the CPU rating seen on the charts. This chart shows the CPUMark for various phones, smartphones and other Android devices. The higher the rating the better the performance. Find out which Android device is best for your hand held needs! Android CPU Mark Rating Updated 11th of August 2016 Samsung SM-G930W8 189,083 Lemobile Le X520 184,124 Samsung SM-N920P 168,971 Samsung SM-G890A 167,226 Samsung SCV31 166,812 Samsung Galaxy S6 Edge (Various Models) 165,338 Samsung SM-G928V 164,894 HTC 10 164,138 Samsung SM-G930F 163,461 HTC 2PS5200 163,113 Samsung SM-N920V 163,087 Samsung SM-N920T 162,504 Oneplus A3003 159,868 Samsung SM-G935F 159,781 Samsung SM-N920W8 159,160 Samsung SM-G930T 158,021 Samsung SM-G930V 157,587 LG H820 156,995 Samsung SM-G935P 156,823 Cmdc M836 156,217 Samsung SM-G930A 155,820 Xiaomi MI 5 152,639 Samsung Galaxy S6 (Various Models) 152,343 1 -
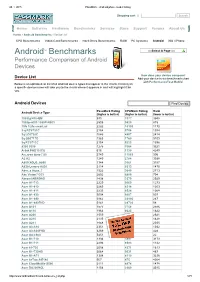
Androidtm Benchmarks
28. 1. 2015 PassMark Android phone model listing Shopping cart | Search Home Software Hardware Benchmarks Services Store Support Forums About Us Home » Android Benchmarks » Device List CPU Benchmarks Video Card Benchmarks Hard Drive Benchmarks RAM PC Systems Android iOS / iPhone TM Select A Page Android Benchmarks Performance Comparison of Android Devices How does your device compare? Device List Add your device to our benchmark chart with PerformanceTest Mobile! Below is an alphabetical list of all Android device types that appear in the charts. Clicking on a specific device name will take you to the charts where it appears in and will highlight it for you. Android Devices Find Device PassMark Rating CPUMark Rating Rank Android Device Type (higher is better) (higher is better) (lower is better) 1005tg N10QM 935 3377 3948 1080pn003 1080PN003 2505 9820 815 1life 1Life.smart.air 2282 10103 1170 3q RC9731C 2154 5756 1394 3q LC0720C 1646 4897 2414 3q QS0717D 1363 1760 3109 3q RC9712C 2154 5223 1396 9300 9300 1275 3364 3321 Alink PAD10 ICS 616 1130 4249 A.c.ryan dyno 7.85 2749 11065 596 A2 A2 1240 2784 3388 A800 XOLO_A800 1344 3661 3157 A830 Lenovo A830 2114 8313 1470 Abs_a Aqua_7 1522 3640 2713 Abc Vision7DCI 2602 6880 704 Abroad ABROAD 1438 3379 2929 Acer A1713 2229 9069 1273 Acer A1810 2265 8314 1203 Acer A1811 2233 8524 1268 Acer A1830 3004 9207 507 Acer A1840 3962 23996 267 Acer A1840FHD 5141 28720 58 Acer A101 1577 3758 2586 Acer A110 1964 8623 1822 Acer A200 1559 3822 2621 Acer A210 2135 8315 1428 Acer A211 1848 8130 2035 Acer A3A10 2351 8128 1032 Acer A3A20FHD 3269 11265 428 Acer AA3600 5451 22392 22 Acer B1710 1336 3897 3173 Acer B1711 2293 8583 1142 Acer b1720 2058 4371 1613 Acer B1730HD 3064 9031 487 Acer B1A71 1308 4119 3236 Acer beTouch E140 567 475 4264 Acer CloudMobile S500 2111 4874 1478 Acer DA220HQL 1156 2960 3545 http://www.androidbenchmark.net/device_list.php 1/71 28.