Key Infection: Smart Trust for Smart Dust
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Shared Sensor Networks Fundamentals, Challenges, Opportunities, Virtualization Techniques, Comparative Analysis, Novel Architecture and Taxonomy
Journal of Sensor and Actuator Networks Review Shared Sensor Networks Fundamentals, Challenges, Opportunities, Virtualization Techniques, Comparative Analysis, Novel Architecture and Taxonomy Nahla S. Abdel Azeem 1, Ibrahim Tarrad 2, Anar Abdel Hady 3,4, M. I. Youssef 2 and Sherine M. Abd El-kader 3,* 1 Information Technology Center, Electronics Research Institute (ERI), El Tahrir st, El Dokki, Giza 12622, Egypt; [email protected] 2 Electrical Engineering Department, Al-Azhar University, Naser City, Cairo 11651, Egypt; [email protected] (I.T.); [email protected] (M.I.Y.) 3 Computers & Systems Department, Electronics Research Institute (ERI), El Tahrir st, El Dokki, Giza 12622, Egypt; [email protected] 4 Department of Computer Science & Engineering, School of Engineering and Applied Science, Washington University in St. Louis, St. Louis, MO 63130, 1045, USA; [email protected] * Correspondence: [email protected] Received: 19 March 2019; Accepted: 7 May 2019; Published: 15 May 2019 Abstract: The rabid growth of today’s technological world has led us to connecting every electronic device worldwide together, which guides us towards the Internet of Things (IoT). Gathering the produced information based on a very tiny sensing devices under the umbrella of Wireless Sensor Networks (WSNs). The nature of these networks suffers from missing sharing among them in both hardware and software, which causes redundancy and more budget to be used. Thus, the appearance of Shared Sensor Networks (SSNs) provides a real modern revolution in it. Where it targets making a real change in its nature from domain specific networks to concurrent running domain networks. That happens by merging it with the technology of virtualization that enables the sharing feature over different levels of its hardware and software to provide the optimal utilization of the deployed infrastructure with a reduced cost. -

Concepts General Concepts Wireless Sensor Networks (WSN)
Wireless Sensor Networks – Concepts General Concepts Wireless Sensor Networks (WSN) are built based on a combination of multiple sensors placed in diverse locations, wireless communication network infrastructure and software data processing to monitor and record multiple parameters. Commonly monitored parameters are temperature, atmospheric pressure, humidity, vibration, illuminance, sound level, power consumption, chemical concentration, body health signals and many others, dependant on the selected available sensors. The WSN are used in multiple fields, ranging from remote environment monitoring, medical health, to home surveillance and industrial machines monitoring. In some cases, WSN can also be additionally used for control functions, apart from monitoring functions. Typically a WSN is made of sensor nodes that are wirelessly connected to a gateway that is then connected to a main computer (Fig. 1). In some WSN the sensor nodes can also be connected to each other, so that is possible to implement multi-hop wireless mesh networks. The gateway connects to the main computer through a cabled or wireless connection. Figure 1 – Wireless sensor network The wireless communications used in WSN depend on the application requirements, taking into consideration the needs in terms of transmission distance, sensor data bandwidth, energy source and power consumption. Common communications include standard protocols such as 2.4 GHz radio based on either IEEE802.15.4 (ZigBee, ISA 100, WirelessHart, MiWi) or IEEE802.11 (WiFi) standards. Each sensor node typically includes an embedded microcontroller system with adequate electronic interface with a sensor (or set of sensors), a radio transceiver with antenna (internal or external) and an energy source, usually a battery, or in some cases an energy harvesting circuit. -

Flexis—A Flexible Sensor Node Platform for the Internet of Things
sensors Article FlexiS—A Flexible Sensor Node Platform for the Internet of Things Duc Minh Pham and Syed Mahfuzul Aziz * UniSA STEM, University of South Australia, Mawson Lakes, SA 5095, Australia; [email protected] * Correspondence: [email protected]; Tel.: +61-08-8302-3643 Abstract: In recent years, significant research and development efforts have been made to transform the Internet of Things (IoT) from a futuristic vision to reality. The IoT is expected to deliver huge economic benefits through improved infrastructure and productivity in almost all sectors. At the core of the IoT are the distributed sensing devices or sensor nodes that collect and communicate information about physical entities in the environment. These sensing platforms have traditionally been developed around off-the-shelf microcontrollers. Field-Programmable Gate Arrays (FPGA) have been used in some of the recent sensor nodes due to their inherent flexibility and high processing capability. FPGAs can be exploited to huge advantage because the sensor nodes can be configured to adapt their functionality and performance to changing requirements. In this paper, FlexiS, a high performance and flexible sensor node platform based on FPGA, is presented. Test results show that FlexiS is suitable for data and computation intensive applications in wireless sensor networks because it offers high performance with low energy profile, easy integration of multiple types of sensors, and flexibility. This type of sensing platforms will therefore be suitable for the distributed data analysis and decision-making capabilities the emerging IoT applications require. Keywords: Internet of Things (IoT); wireless sensor networks (WSN); sensor node; field-programmable Citation: Pham, D.M.; Aziz, S.M. -

A Zigbee-Based Wireless Biomedical Sensor Network
A ZIG BEE -BASED WIRELESS BIOMEDICAL SENSOR NETWORK AS A PRECURSOR TO AN IN-SUIT SYSTEM FOR MONITORING ASTRONAUT STATE OF HEALTH by XIONGJIE DONG B.S., Kansas State University, 2011 A THESIS submitted in partial fulfillment of the requirements for the degree MASTER OF SCIENCE Department of Electrical & Computer Engineering College of Engineering Kansas State University Manhattan, Kansas 2014 Approved by Major Professor Steve Warren ABSTRACT Networks of low-power, in-suit, wired and wireless health sensors offer the potential to track and predict the health of astronauts engaged in extra-vehicular and in-station activities in zero- or reduced- gravity environments. Fundamental research questions exist regarding (a) types and form factors of biomedical sensors best suited for these applications, (b) optimal ways to render wired/wireless on-body networks with the objective to draw little-to-no power, and (c) means to address the wireless transmission challenges offered by a spacesuit constructed from layers of aluminized mylar. This thesis addresses elements of these research questions through the implementation of a collection of ZigBee-based wireless health monitoring devices that can potentially be integrated into a spacesuit, thereby providing continuous information regarding astronaut fatigue and state of health. Wearable biomedical devices investigated for this effort include electrocardiographs, electromyographs, pulse oximeters, inductive plethysmographs, and accelerometers/gyrometers. These ZigBee-enabled sensors will form the nodes of an in-suit ZigBee Pro network that will be used to (1) establish throughput requirements for a functional in-suit network and (2) serve as a performance baseline for future devices that employ ultra-low-power field-programmable gate arrays and micro-transceivers. -

A Comparative Study Between Operating Systems (Os) for the Internet of Things (Iot)
VOLUME 5 NO 4, 2017 A Comparative Study Between Operating Systems (Os) for the Internet of Things (IoT) Aberbach Hicham, Adil Jeghal, Abdelouahed Sabrim, Hamid Tairi LIIAN, Department of Mathematic & Computer Sciences, Sciences School, Sidi Mohammed Ben Abdellah University, [email protected], [email protected], [email protected], [email protected] ABSTRACT Abstract : We describe The Internet of Things (IoT) as a network of physical objects or "things" embedded with electronics, software, sensors, and network connectivity, which enables these objects to collect and exchange data in real time with the outside world. It therefore assumes an operating system (OS) which is considered as an unavoidable point for good communication between all devices “objects”. For this purpose, this paper presents a comparative study between the popular known operating systems for internet of things . In a first step we will define in detail the advantages and disadvantages of each one , then another part of Interpretation is developed, in order to analyze the specific requirements that an OS should satisfy to be used and determine the most appropriate .This work will solve the problem of choice of operating system suitable for the Internet of things in order to incorporate it within our research team. Keywords: Internet of things , network, physical object ,sensors,operating system. 1 Introduction The Internet of Things (IoT) is the vision of interconnecting objects, users and entities “objects”. Much, if not most, of the billions of intelligent devices on the Internet will be embedded systems equipped with an Operating Systems (OS) which is a system programs that manage computer resources whether tangible resources (like memory, storage, network, input/output etc.) or intangible resources (like running other computer programs as processes, providing logical ports for different network connections etc.), So it is the most important program that runs on a computer[1]. -

Scantraffic: Smart Camera Network for Traffic Information Collection
ScanTraffic: Smart Camera Network for Traffic Information Collection Daniele Alessandrelli1, Andrea Azzar`a1, Matteo Petracca2, Christian Nastasi1, and Paolo Pagano2 1 Real-Time Systems Laboratory, Scuola Superiore Sant'Anna, Pisa, Italy fd.alessandrelli, a.azzara, [email protected] 2 National Laboratory of Photonic Networks, CNIT, Pisa, Italy fmatteo.petracca, [email protected] Abstract. Intelligent Transport Systems (ITSs) are gaining growing in- terest from governments and research communities because of the eco- nomic, social and environmental benefits they can provide. An open issue in this domain is the need for pervasive technologies to collect traffic- related data. In this paper we discuss the use of visual Wireless Sensor Networks (WSNs), i.e., networks of tiny smart cameras, to address this problem. We believe that smart cameras have many advantages over classic sensor motes. Nevertheless, we argue that a specific software in- frastructure is needed to fully exploit them. We identify the three main services such software must provide, i.e., monitoring, remote configura- tion, and remote code-update, and we propose a modular architecture for them. We discuss our implementation of such architecture, called ScanTraffic, and we test its effectiveness within an ITS prototype we deployed at the Pisa International Airport. We show how ScanTraffic greatly simplifies the deployment and management of smart cameras col- lecting information about traffic flow and parking lot occupancy. Keywords: intelligent transport systems, visual wireless sensor net- works, smart cameras 1 Introduction Intelligent Transport Systems (ITSs) are nowadays at the focus of public au- thorities and research communities aiming at providing effective solutions for improving citizens lifestyle and safety. -
LNCS 3222, Pp
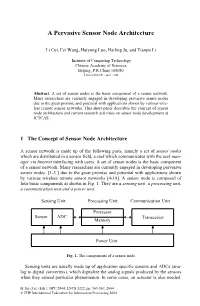
A Pervasive Sensor Node Architecture Li Cui, Fei Wang, Haiyong Luo, Hailing Ju, and Tianpu Li Institute of Computing Technology Chinese Academy of Sciences Beijing, P.R.China 100080 [email protected] Abstract. A set of sensor nodes is the basic component of a sensor network. Many researchers are currently engaged in developing pervasive sensor nodes due to the great promise and potential with applications shown by various wire- less remote sensor networks. This short paper describes the concept of sensor node architecture and current research activities on sensor node development at ICTCAS. 1 The Concept of Sensor Node Architecture A sensor network is made up of the following parts, namely a set of sensor nodes which are distributed in a sensor field, a sink which communicates with the task man- ager via Internet interfacing with users. A set of sensor nodes is the basic component of a sensor network. Many researchers are currently engaged in developing pervasive sensor nodes [1-3 ] due to the great promise and potential with applications shown by various wireless remote sensor networks [4-10]. A sensor node is composed of four basic components as shown in Fig. 1. They are a sensing unit, a processing unit, a communication unit and a power unit. Sensing Unit Processing Unit Communication Unit Processor Sensor ADC Transceiver Memory Power Unit Fig. 1. The components of a sensor node Sensing units are usually made up of application specific sensors and ADCs (ana- log to digital converters), which digitalize the analog signals produced by the sensors when they sensed particular phenomenon. -

Wireless Sensor Network for Monitoring Applications
Wireless Sensor Network for Monitoring Applications A Major Qualifying Project Report Submitted to the University of WORCESTER POLYTECHNIC INSTITUTE In partial fulfillment of the requirements for the Degree of Bachelor of Science By: __________________________ __________________________ Jonathan Isaac Chanin Andrew R. Halloran __________________________ __________________________ Advisor, Professor Emmanuel Agu, CS Advisor, Professor Wenjing Lou, ECE Table of Contents Table of Figures ............................................................................................................................................. 4 Abstract ......................................................................................................................................................... 5 1. Introduction ........................................................................................................................................... 6 1.1 What are Wireless Sensor Networks? ........................................................................................... 6 1.2 Why Sensor Networks? ................................................................................................................. 6 1.3 Application Examples .................................................................................................................... 7 1.4 Project Goal ................................................................................................................................... 8 2. Background ........................................................................................................................................... -

Sensor Validation and Fusion with Distributed Smart Dust Motes For
From: AAAI Technical Report SS-02-03. Compilation copyright © 2002, AAAI (www.aaai.org). All rights reserved. SENSOR VALIDATION AND FUSION WITH DISTRIBUTED ‘SMART DUST’ MOTES FOR MONITORING AND ENABLING EFFICIENT ENERGY USE Alice M. Agogino Jessica Granderson Department of Mechanical Engineering University of California, Berkeley, CA 94720 {aagogino, jgrander}@me.berkeley.edu Shijun Qiu Dept of Mechanical and Electrical Engineering Xiamen University, China (Visiting Scholar, UC Berkeley) [email protected] Abstract 1. Distributed MEMS Sensors – Smart Dust MEMS (microelectronic mechanical systems) sensors make a rich design space of distributed networked sensors viable. The goal of the Smart Dust project is to build a self- They can be deeply embedded in the physical world and contained, millimeter-scale sensing and communication spread throughout our environment like “smart dust”. platform for a massively distributed sensor network Today, networked sensors called Smart Dust motes can be [16,24]. These devices will ultimately be around the size of constructed using commercial components on the scale of a a grain of sand and will contain sensors, computational square inch in size and a fraction of a watt in power. High- density distributed networked sensors have recently been ability, bi-directional wireless communications, and a targeted for use in research devoted to the efficient use of power supply, while being inexpensive enough to deploy energy. Such networks require a large number of sensors by the hundreds. for control at different levels. However, in reality, sensor information is always corrupted to some degree by noise There exist endless possibilities for the applications of and degradation, which vary with operating conditions, these devices. -

Basics of Contiki-OS and Using It for Wireless Sensor Network Applications
Basics of Contiki-OS and using it for Wireless Sensor Network Applications Shantanoo Desai prepared for: Prof. Dr. Anna Förster Sustainable Communication Networks University of Bremen 20th November 2015 1 Outline CONTIKI-OS Contiki in a nutshell Requirements Getting Started Initial Steps File Structure in Contiki Terminal Basics First Program in Contiki: Hello-World Programming using Terminal Hello-World files Getting Output Understanding codes in Contiki Programming a Sensor Node TelosB Sensor Node Connecting the TelosB to Contiki-OS Hello-World program on TelosB Cooja Simulator in Contiki-OS Hello-World Simulation with Cooja Adding Sensor Nodes to Cooja Mote Output in Cooja References 2 Contents of this section CONTIKI-OS Contiki in a nutshell Requirements 3 What is Contiki? CONTIKI-OS in a nutshell: • Complete environment for programming Sensor Nodes • Has everything for getting started in making Applications • In-built simulator called COOJA • Large pool of sensor compatibility e.g. TelosB, Zolertia Z1 4 Requirements Requirements before we begin: • VMware Virtual Player • VMware Workstation 12 Player (recent) • Instant Contiki • Instant Contiki version 2.7/3.0 LOST??? - refer to this : www.contiki-os.org/start.html and follow the steps. 5 Contents of this section Getting Started Initial Steps File Structure in Contiki Terminal Basics 6 Getting Started • Open VMWare player and click on ‘Open a Virtual Machine’ (Don’t Worry ! if it looks different for Windows or MAC-OS! this is for Ubuntu.) 7 Getting Started (contd.) • Navigate to your Instant Contiki 2.7 folder and select the “.vmx” file • After booting of the virtual machine, Login with password: user Figure: First look of Contiki-OS 8 File Structure in Contiki • Click on ‘Places’ and then ‘Home’ folder (top left corner) • target folders: contiki & contiki-2.7 (choose any one and see the folders) Figure: File Structure in Contiki 9 Folders in Contiki and their Usage • apps: applications like webbrowser, telnet etc. -

An Improved Ant Colony Algorithm in Wireless Sensor Network Routing
Paper—An Improved Ant Colony Algorithm in Wireless Sensor Network Routing An Improved Ant Colony Algorithm in Wireless Sensor Network Routing https://doi.org/10.3991/ijoe.v13i05.7060 Liping LV Jiaozuo University, Henan, China [email protected] Abstract—In order to make the energy consumption of network nodes rela- tively balanced, we apply ant colony optimization algorithm to wireless sensor network routing and improve it. In this paper, we propose a multi-path wireless sensor network routing algorithm based on energy equalization. The algorithm uses forward ants to find the path from the source node to the destination node, and uses backward ants to update the pheromone on the path. In the route selec- tion, we use the energy of the neighboring nodes as the parameter of the heuris- tic function. At the same time, we construct the fitness function, and take the path length and the node residual energy as its parameters. The simulation re- sults show that the algorithm can not only avoid the problem of local optimal solution, but also prolong the life cycle of the network effectively. Keywords—wireless sensor network, ant colony algorithm, routing 1 Introduction In recent years, with the rapid development of wireless communication technology, the sensor becomes miniaturized, networked, integrated and intelligent [4]. Compared with traditional sensors, the cost of micro sensors is very low. However, its coverage is small. Therefore, in practical applications, tens of thousands of micro-sensors are often required to work together. Based on this demand, the concept of wireless sensor networks has emerged [2]. As an important information acquisition technology, wireless sensor networks greatly expand the functionality of existing networks [1]. -

Wireless Sensor Network Implementation Using MIWI Wireless Protocol Stack Suman Chhajed Md.Sabir .M.Tech
Volume 4, No. 11, Nov-Dec 2013 ISSN No. 0976-5697 International Journal of Advanced Research in Computer Science RESEARCH PAPER Available Online at www.ijarcs.info Wireless Sensor Network Implementation using MIWI Wireless Protocol Stack Suman Chhajed Md.Sabir .M.Tech. Student, Department of ECE, GITS-Udaipur Asst. Prof., Department o fECE, GITS-Udaipur [email protected] [email protected] Abstract: This Paper is to design full functional nodes and to deploy wireless sensor network for Industrial parameter monitoring. Sensor nodes acquire the physical variable from field and wirelessly transmit to central master node for acquisition, monitoring, analysis and storage. The resulting designed product could form a reliable support for transferring data between nodes and a computer. A most important stage of this thesis work is to develop sensor nodes for collecting sensor data and acquires data on master node which has MIWI wireless protocol stack. I. INTRODUCTION Wireless Sensor Network (WSN) is a promising data mining solution of industrial wireless data network. Instrumented with wireless sensors, it will become available to monitor the plants in real time, such as air temperature, soil water content, and nutrition stress. The real time information of the fields will provide a solid base to adjust strategies at any time. WSN will revolutionize the data collection in industrial research. However, there have been few researches on the applications of WSN for industrial wireless network. This work was focused on the investigation of wireless sensor networks in industrial Figure.1. Wireless Sensor Network Model applications. The datasets were obtained from experiments. A.