Language Technology for Cultural Heritage Data (Latech 2007), Pages 41–48, Prague, Czech Republic, June
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Introduction to Computer System
Chapter 1 INTRODUCTION TO COMPUTER SYSTEM 1.0 Objectives 1.1 Introduction –Computer? 1.2 Evolution of Computers 1.3 Classification of Computers 1.4 Applications of Computers 1.5 Advantages and Disadvantages of Computers 1.6 Similarities Difference between computer and Human 1.7 A Computer System 1.8 Components of a Computer System 1.9 Summary 1.10 Check your Progress - Answers 1.11 Questions for Self – Study 1.12 Suggested Readings 1.0 OBJECTIVES After studying this chapter you will be able to: Learn the concept of a system in general and the computer system in specific. Learn and understand how the computers have evolved dramatically within a very short span, from very huge machines of the past, to very compact designs of the present with tremendous advances in technology. Understand the general classifications of computers. Study computer applications. Understand the typical characteristics of computers which are speed, accuracy, efficiency, storage capacity, versatility. Understand limitations of the computer. Discuss the similarities and differences between the human and the computer. Understand the Component of the computer. 1.1 INTRODUCTION- Computer Today, almost all of us in the world make use of computers in one way or the other. It finds applications in various fields of engineering, medicine, commercial, research and others. Not only in these sophisticated areas, but also in our daily lives, computers have become indispensable. They are present everywhere, in all the dev ices that we use daily like cars, games, washing machines, microwaves etc. and in day to day computations like banking, reservations, electronic mails, internet and many more. -

The Strange Birth and Long Life of Unix - IEEE Spectrum Page 1 of 6
The Strange Birth and Long Life of Unix - IEEE Spectrum Page 1 of 6 COMPUTING / SOFTWARE FEATURE The Strange Birth and Long Life of Unix The classic operating system turns 40, and its progeny abound By WARREN TOOMEY / DECEMBER 2011 They say that when one door closes on you, another opens. People generally offer this bit of wisdom just to lend some solace after a misfortune. But sometimes it's actually true. It certainly was for Ken Thompson and the late Dennis Ritchie, two of the greats of 20th-century information technology, when they created the Unix operating system, now considered one of the most inspiring and influential pieces of software ever written. A door had slammed shut for Thompson and Ritchie in March of 1969, when their employer, the American Telephone & Telegraph Co., withdrew from a collaborative project with the Photo: Alcatel-Lucent Massachusetts Institute of KEY FIGURES: Ken Thompson [seated] types as Dennis Ritchie looks on in 1972, shortly Technology and General Electric after they and their Bell Labs colleagues invented Unix. to create an interactive time- sharing system called Multics, which stood for "Multiplexed Information and Computing Service." Time-sharing, a technique that lets multiple people use a single computer simultaneously, had been invented only a decade earlier. Multics was to combine time-sharing with other technological advances of the era, allowing users to phone a computer from remote terminals and then read e -mail, edit documents, run calculations, and so forth. It was to be a great leap forward from the way computers were mostly being used, with people tediously preparing and submitting batch jobs on punch cards to be run one by one. -

The Strange Birth and Long Life of Unix - IEEE Spectrum
The Strange Birth and Long Life of Unix - IEEE Spectrum http://spectrum.ieee.org/computing/software/the-strange-birth-and-long-li... COMPUTING / SOFTWARE FEATURE The Strange Birth and Long Life of Unix The classic operating system turns 40, and its progeny abound By WARREN TOOMEY / DECEMBER 2011 They say that when one door closes on you, another opens. People generally offer this bit of wisdom just to lend some solace after a misfortune. But sometimes it's actually true. It certainly was for Ken Thompson and the late Dennis Ritchie, two of the greats of 20th-century information technology, when they created the Unix operating system, now considered one of the most inspiring and influential pieces of software ever written. A door had slammed shut for Thompson and Ritchie in March of 1969, when their employer, the American Telephone & Telegraph Co., withdrew from a collaborative project with the Photo: Alcatel-Lucent Massachusetts Institute of KEY FIGURES: Ken Thompson [seated] types as Dennis Ritchie looks on in 1972, shortly Technology and General Electric after they and their Bell Labs colleagues invented Unix. to create an interactive time-sharing system called Multics, which stood for "Multiplexed Information and Computing Service." Time-sharing, a technique that lets multiple people use a single computer simultaneously, had been invented only a decade earlier. Multics was to combine time-sharing with other technological advances of the era, allowing users to phone a computer from remote terminals and then read e-mail, edit documents, run calculations, and so forth. It was to be a great leap forward from the way computers were mostly being used, with people tediously preparing and submitting batch jobs on punch cards to be run one by one. -

Montana Kaimin, April 28, 1993 Associated Students of the University of Montana
University of Montana ScholarWorks at University of Montana Associated Students of the University of Montana Montana Kaimin, 1898-present (ASUM) 4-28-1993 Montana Kaimin, April 28, 1993 Associated Students of the University of Montana Let us know how access to this document benefits ouy . Follow this and additional works at: https://scholarworks.umt.edu/studentnewspaper Recommended Citation Associated Students of the University of Montana, "Montana Kaimin, April 28, 1993" (1993). Montana Kaimin, 1898-present. 8585. https://scholarworks.umt.edu/studentnewspaper/8585 This Newspaper is brought to you for free and open access by the Associated Students of the University of Montana (ASUM) at ScholarWorks at University of Montana. It has been accepted for inclusion in Montana Kaimin, 1898-present by an authorized administrator of ScholarWorks at University of Montana. For more information, please contact [email protected]. Students petition Baucus to keep professor at UM By Shaun Tatarka Staff Writer A UM student has sent a petition signed by 35 UM Russian department students to U.S. Sen. Max Baucus, D-Mont., in an attempt to keep a visiting professor from having to return to the former Soviet Union. Judith Dotson, a senior in Russian and history, said she sent the petition in hopes that Baucus could help find money to keep visiting professor Dr. Ludmila Pavlina at UM. Pavlina has spent the last three years at UM teaching first-year Russian language students. “She is an excellent teacher and the only native-speaking Russian professor we have,” Dotson said. “It would be a tragedy to lose her.” Dotson said she chose Baucus because of the national government's recent concerns over Soviet-U.S. -

Squinting at Power Series
Squinting at Power Series M. Douglas McIlroy AT&T Bell Laboratories Murray Hill, New Jersey 07974 ABSTRACT Data streams are an ideal vehicle for handling power series. Stream implementations can be read off directly from simple recursive equations that de®ne operations such as multiplication, substitution, exponentiation, and reversion of series. The bookkeeping that bedevils these algorithms when they are expressed in traditional languages is completely hidden when they are expressed in stream terms. Communicating processes are the key to the simplicity of the algorithms. Working versions are presented in newsqueak, the language of Pike's ``squint'' system; their effectiveness depends critically on the stream protocol. Series and streams Power series are natural objects for stream processing. Pertinent computations are neatly describable by recursive equations. CSP (communicating sequential process) languages1, 2 are good vehicles for implementation. This paper develops the algorithmic ideas and reduces them to practice in a working CSP language,3 not coincidentally illustrating the utility of concurrent programming notions in untangling the logic of some intricate computations on sequences. This elegant approach to power series computation, ®rst demonstrated but never published by Kahn and MacQueen as an application of their data stream system, is still little known.4 Power series are represented as streams of coef®cients, the exponents being given implicitly by ordinal position. (This is an in®nite analogue of the familiar representation of a polynomial as an array of coef®cients.) Thus the power series for the exponential function ∞ 1 1 1 e x = Σ x n / n! = 1 + x + __ x 2 + __ x 3 + ___ x 4 + . -

Uma Introdução À Computação: História E Ciência Editora Ixtlan - São Paulo – 2016
São Paulo – 2016 Copyright © Autores diversos Projeto gráfico: Editora Ixtlan Revisão: Eduardo Telmo Fonseca Santos Milena Montenegro Pereira Diagramação: Márcia Todeschini Capa: Gabriel Polizello Uma introdução à computação: história e ciência Editora Ixtlan - São Paulo – 2016 ISBN: 978-85-8197-510-8 1.Ciência da computação 2.história CDD 000 Editora Ixtlan - CNPJ 11.042.574/0001-49 - I.E. 456166992117 [email protected] – www.editoraixtlan.com DIREITOS PRESERVADOS – É proibida a reprodução total ou parcial, de qualquer forma ou por qualquer meio. A violação dos direitos de autor (Lei Federal 9.610/1998) é crime previsto no art. 184 do Código Penal. Sumário 1. Início da computação - 3 2. Software - 19 3. Representação da Informação - 27 4. Ciência da Computação é Ciência? - 35 5. Rede de Computadores - 37 6. Exercícios Complementares - 49 7. Bibliografia - 53 Cap´ıtulo 1 Início da computação Para entender os fundamentos da computação atual é preciso olhar para o passado e ver como essa disciplina/área foi fundada e como vem se desenvolvendo até a atualidade [5]. Uma das bases da computação é a Matemática. Desde os primórdios o ser humano percebeu a necessidade de desenvolver algo para auxiliá-lo nas mais diversas operações. Essa necessidade é a responsável pelo surgimento desde as máquinas de calcular até as mais diversas máquinas utilizadas no mundo todo. Em torno de 2600 anos a.C., surgiu um dos primeiros instrumentos manuais voltados para ajudar o homem a calcular quantias numéricas. Esse instrumento usado para representação dos números era o ábaco chinês, que apesar do tempo em que surgiu, ainda é comumente utilizado em certas localidades. -

Universidad Nacional Autónoma De México, Por Permitirme El Honor De Formar Parte De Ella
Universidad Nacional Autónoma de México FACULTAD DE INGENIERÍA “SISTEMA DE MONITOREO DE SERVIDORES UNIX” T E S I S Que para obtener el Título de: INGENIERO EN COMPUTACIÓN P r e s e n t a: EDGAR CRISTÓBAL RAMÍREZ MIRANDA Director de Tesis: Ing. Noé Cruz Marín Agradecimientos Más que gracias, mi eterno amor a mi padre, mi madre y a mis hermanos a los cuales les debo lo que soy. Papá te admiro y respeto profundamente por la rectitud y honradez con la que te conduces a cada paso de tu vida, por el apoyo y dirección que siempre de ti he recibido, por todas las enseñanzas que desde chico recibí de ti y espero seguir recibiendo. Mamá te amo por todos los años de dedicación que me has dado, por los desvelos, por las lágrimas, por los cariños, por tu inmensa ternura y compasión, por que no encuentro ni encontraré jamás la forma de pagarte todo lo que me has dado, gracias. A mi hermano Emilio por ser mi amigo, por enseñarme a defenderme, por ser mi ídolo, por ensañarme a no desistir nunca hasta alcanzar las metas, porque a tu lado siempre me sentí protegido, por alentarme a ser ingeniero. A mi hermano Joaquín, por que de ti aprendí a ser más sereno a pensar antes de actuar, por siempre protegerme de todos sin importarte nada, por estar conmigo en las buenas y en las malas, por tu tolerancia, por ser mi amigo en los tiempos difíciles. Gracias por aguantarme, soportarme, cuidarme y quererme de la forma en la que lo hacen, estoy y siempre estaré orgulloso de pertenecer a la familia Ramírez Miranda. -

Lezione 11 Processi Sistemi Operativi (9 CFU), Cdl Informatica, A
Lezione 11 Processi Sistemi Operativi (9 CFU), CdL Informatica, A. A. ! !" ! 1 Dipartimento di Scienze Fisic$e, Informatic$e e %atematic$e Universit& di %odena e Re((io )mi*ia $ttp+"",e-*a-.in(..nimo.it"peop*e"andreo*ini"didattica"sistemi/operativi 1 0.ote of t$e da1 (%editate, (ente, meditate...) “This is the UNIX philosophy: write programs that do one thing and do it well. Write programs to work together. Write programs to handle text streams, because that is a niversal inter"ace.# #o.(*as McI*ro1 (192 -) %atematico, In(e(nere, Programmatore Inventore de**e pipe e de**e utilit1 U3I4 2 SOLUZIONI DEGLI ESERCIZI 3 Esercizio 1 (1 min.) 0.al 5 il PID del processo init (il (estore dei servizi U3I4)6 4 Identi7cazione esatta con pidof Il PID del processo init p.8 essere individ.ato a partire dal s.o nome esatto con i* comando pidof+ pidof init Si dovre--e ottenere il PID 1. 5 Esercizio 2 (2 min.) I processi del des9top :;3OM)< iniziano con la strin(a :(nome<. Come si possono individ.are i processi del des9top in esec.zione6 6 Individuazione tramite pgrep I processi de**=am-iente des9top ;3OME possono essere individ.ati cercando *=espressione re(olare ^gnome.*$ con il comando pgrep+ pgrep ^gnome.*$ Per stampare anc$e i nomi dei comandi si .sa *=opzione -l+ pgrep -l ^gnome.*$ 7 Esercizio 3 (2 min.) Elencate t.tti i processi (e relativi PID) ese(.iti per conto del vostro .sername. Le((ete la pa(ina di man.ale del comando opportuno per capire come fare. -

Praktikum Iz Softverskih Alata U Elektronici
PRAKTIKUM IZ SOFTVERSKIH ALATA U ELEKTRONICI 2017/2018 Predrag Pejović 31. decembar 2017 Linkovi na primere: I OS I LATEX 1 I LATEX 2 I LATEX 3 I GNU Octave I gnuplot I Maxima I Python 1 I Python 2 I PyLab I SymPy PRAKTIKUM IZ SOFTVERSKIH ALATA U ELEKTRONICI 2017 Lica (i ostali podaci o predmetu): I Predrag Pejović, [email protected], 102 levo, http://tnt.etf.rs/~peja I Strahinja Janković I sajt: http://tnt.etf.rs/~oe4sae I cilj: savladavanje niza programa koji se koriste za svakodnevne poslove u elektronici (i ne samo elektronici . ) I svi programi koji će biti obrađivani su slobodan softver (free software), legalno možete da ih koristite (i ne samo to) gde hoćete, kako hoćete, za šta hoćete, koliko hoćete, na kom računaru hoćete . I literatura . sve sa www, legalno, besplatno! I zašto svake godine (pomalo) updated slajdovi? Prezentacije predmeta I engleski I srpski, kraća verzija I engleski, prezentacija i animacije I srpski, prezentacija i animacije A šta se tačno radi u predmetu, koji programi? 1. uvod (upravo slušate): organizacija nastave + (FS: tehnička, ekonomska i pravna pitanja, kako to uopšte postoji?) (≈ 1 w) 2. operativni sistem (GNU/Linux, Ubuntu), komandna linija (!), shell scripts, . (≈ 1 w) 3. nastavak OS, snalaženje, neki IDE kao ilustracija i vežba, jedan Python i jedan C program . (≈ 1 w) 4.L ATEX i LATEX 2" (≈ 3 w) 5. XCircuit (≈ 1 w) 6. probni kolokvijum . (= 1 w) 7. prvi kolokvijum . 8. GNU Octave (≈ 1 w) 9. gnuplot (≈ (1 + ) w) 10. wxMaxima (≈ 1 w) 11. drugi kolokvijum . 12. Python, IPython, PyLab, SymPy (≈ 3 w) 13. -

The History of Unix in the History of Software Haigh Thomas
The History of Unix in the History of Software Haigh Thomas To cite this version: Haigh Thomas. The History of Unix in the History of Software. Cahiers d’histoire du Cnam, Cnam, 2017, La recherche sur les systèmes : des pivots dans l’histoire de l’informatique – II/II, 7-8 (7-8), pp77-90. hal-03027081 HAL Id: hal-03027081 https://hal.archives-ouvertes.fr/hal-03027081 Submitted on 9 Dec 2020 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. 77 The History of Unix in the History of Software Thomas Haigh University of Wisconsin - Milwaukee & Siegen University. You might wonder what I am doing The “software crisis” and here, at an event on this history of Unix. the 1968 NATO Conference As I have not researched or written about on Software Engineering the history of Unix I had the same question myself. But I have looked at many other The topic of the “software crisis” things around the history of software and has been written about a lot by profes- this morning will be talking about how sional historians, more than anything some of those topics, including the 1968 else in the entire history of software2. -

UNIX Security
UNIX Security CSE497b - Spring 2007 Introduction Computer and Network Security Professor Jaeger www.cse.psu.edu/~tjaeger/cse497b-s07/ CSE497b Introduction to Computer and Network Security - Spring 2007 - Professor Jaeger UNIX System • Originated in the late 60’s, early 70’s – Bell Labs: Ken Thompson, Dennis Ritchie, Douglas McIlroy • Multiuser Operating System – Enables protection from other users – Enables protection of system services from users • Simpler, faster approach than Multics CSE497b Introduction to Computer and Network Security - Spring 2007 - Professor Jaeger Page 2 UNIX Security • Each user owns a set of files – Simple way to express who else can access – All user processes run as that user • The system owns a set of files – Root user is defined for system principal – Root can access anything • Users can invoke system services – Need to switch to root user (setuid) • Q: Does UNIX enable configuration of “secure” systems? CSE497b Introduction to Computer and Network Security - Spring 2007 - Professor Jaeger Page 3 UNIX Challenges • More about protection than security – Implicitly assumes non-malicious user and trusted system processes • Discretionary Access Control (DAC) – User or their processes may update permission assignments • Each program has all user’s rights • Must trust their processes to be non-malicious • File permission assignments – Assignment based on what is necessary for things to work • All your processes have all your rights • System services have full access – Users invoke setuid (root) procs that have all -
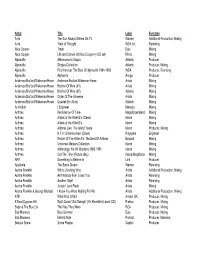
Steve Discog Long
Artist Title Label Function A-ha The Sun Always Shines On TV Warner Additional Production, Mixing A-ha Train of Thought WEA Int. Remixing Alice Cooper Trash Epic Mixing Alice Cooper Life and Crimes Of Alice Cooper (4 CD set) Rhino Mixing Alphaville Afternoons In Utopia Atlantic Producer Alphaville Singles Collection Atlantic Producer, Mixing Alphaville First Harvest: The Best Of Alphaville 1984-1992 WEA Producer, Remixing Alphaville Alphaville Amiga Producer Anderson/Bruford/Wakeman/Howe Anderson Bruford Wakeman Howe Arista Mixing Anderson/Bruford/Wakeman/Howe Brother Of Mine (#1) Arista Mixing Anderson/Bruford/Wakeman/Howe Brother Of Mine (#2) Atlantic Mixing Anderson/Bruford/Wakeman/Howe Order Of The Universe Arista Mixing Anderson/Bruford/Wakeman/Howe Quartet (I'm Alive) Atlantic Mixing Animotion I Engineer Mercury Mixing Anthrax Persistence Of Time Megaforce/Island Mixing Anthrax Attack of the Killer B's (Clean) Island Mixing Anthrax Attack of the Killer B's Island Mixing Anthrax Anthrax Live: The Island Years Island Producer, Mixing Anthrax N.F.V.:Oidivnikufesin (Clean) Polygram Engineer Anthrax Return Of The Killer A's: The Best Of Anthrax Beyond Mixing Anthrax Universal Masters Collection Island Mixing Anthrax Anthrology: No Hit Wonders 1985-1991 Island Mixing Anthrax Got The Time (Picture disc) Island/Megaforce Mixing APB Something to Believe In Link Producer Apollonia The Same Dream Warner Remixing Aretha Franklin Who's Zooming Who Arista Additional Production, Mixing Aretha Franklin Aint Nobody Ever Loved You Arista Remixing