Unix Programmer's Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Practice Test Version 1.8 LPI 117-101: Practice Exam QUESTION NO: 1 CORRECT TEXT
LPI 117-101 117-101 LPI 101 General Linux, Part I Practice Test Version 1.8 LPI 117-101: Practice Exam QUESTION NO: 1 CORRECT TEXT You suspect that a new ethernet card might be conflicting with another device. Which file should you check within the /proc tree to learn which IRQs are being used by which kernel drives? Answer: interrupts QUESTION NO: 2 How many SCSI ids for peripherals can SCSI-1 support? A. 5 B. 6 C. 7 D. 8 Answer: C Explanation: SCSI-1 support total 7 peripherals. There are several different types of SCSI devices. The original SCSI specification is commonly referred to as SCSI-1. The newer specification, SCSI-2, offers increased speed and performance, as well as new commands. Fast SCSI increases throughput to more than 10MB per second. Fast-Wide SCSI provides a wider data path and throughput of up to 40MB per second and up to 15 devices. There there are Ultra-SCSI and Ultra-Wide-SCSI QUESTION NO: 3 You need to install a fax server. Which type of fax/modem should you install to insure Linux compatibility? Test-King.com A. External Serial Fax/modem B. External USB Fax/modem C. Internal ISA Fax/modem D. Internal PCI Fax/modem Answer: A QUESTION NO: 4 You are running Linux 2.0.36 and you need to add a USB mouse to your system. Which of the following statements is true? "Welcome to Certification's Main Event" - www.test-king.com 2 LPI 117-101: Practice Exam A. You need to rebuild the kernel. -

UNIX Version 7 Volume 1
UNIXTM TIME-SHARING SYSTEM: UNIX PROGRAMMER'S MANUAL Seventh Edition, Volume 1 January, 1979 Bell Telephone Laboratories, Incorporated Murray Hill, New Jersey PREFACE Although this Seventh Edition no longer bears their byline, Ken Thompson and Dennis Ritchie remain the fathers and preceptors of the UNIX² time-sharing system. Many of the improvements here described bear their mark. Among many, many other people who have contributed to the further ¯owering of UNIX, we wish especially to acknowledge the contributions of A. V. Aho, S. R. Bourne, L. L. Cherry, G. L. Chesson, S. I. Feldman, C. B. Haley, R. C. Haight, S. C. Johnson, M. E. Lesk, T. L. Lyon, L. E. McMahon, R. Morris, R. Muha, D. A. Nowitz, L. Wehr, and P. J. Weinberger. We appreciate also the effective advice and criticism of T. A. Dolotta, A. G. Fraser, J. F. Maranzano, and J. R. Mashey; and we remember the important work of the late Joseph F. Ossanna. B. W. Kernighan M. D. McIlroy __________________ ²UNIX is a Trademark of Bell Laboratories. INTRODUCTION TO VOLUME 1 This volume gives descriptions of the publicly available features of the UNIX² system. It does not attempt to provide perspective or tutorial information upon the UNIX operating system, its facilities, or its implementation. Various documents on those topics are contained in Volume 2. In particular, for an overview see `The UNIX Time-Sharing System' by Ritchie and Thompson; for a tutorial see `UNIX for Beginners' by Kernighan. Within the area it surveys, this volume attempts to be timely, complete and concise. Where the latter two objectives con¯ict, the obvious is often left unsaid in favor of brevity. -

Control of Protein Orientation on Gold Nanoparticles † ∥ † § † ∥ ⊥ Wayne Lin, Thomas Insley, Marcus D
Article pubs.acs.org/JPCC Control of Protein Orientation on Gold Nanoparticles † ∥ † § † ∥ ⊥ Wayne Lin, Thomas Insley, Marcus D. Tuttle, Lingyang Zhu, Deborah A. Berthold, Petr Kral,́, † ‡ # † Chad M. Rienstra,*, , , and Catherine J. Murphy*, † ‡ Department of Chemistry and Department of Biochemistry, University of Illinois at Urbana−Champaign, 600 South Matthews Avenue, Urbana, Illinois 61801, United States § School of Chemical Sciences, University of Illinois at Urbana−Champaign, 505 South Matthews Avenue, Urbana, Illinois 61801, United States ∥ ⊥ Department of Chemistry and Department of Physics, University of Illinois at Chicago, 845 West Taylor Street, Chicago, Illinois 60607, United States # Center for Biophysics and Computational Biology, University of Illinois at Urbana−Champaign, 607 South Matthews Avenue, Urbana, Illinois 61801, United States *S Supporting Information ABSTRACT: Gold nanoparticles (Au NPs) have attracted much attention due to their potential applications in nanomedicine. While numerous studies have quantified biomolecular adsorption to Au NPs in terms of equilibrium binding constants, far less is known about biomolecular orientation on nanoparticle surfaces. In this study, the binding of the protein α-synuclein to citrate and (16- mercaptohexadecyl)trimethylammonium bromide (MTAB)-coated 12 nm Au NPs is examined by heteronuclear single quantum coherence NMR spectroscopy to provide site-specific measurements of protein−nanoparticle binding. Molecular dynamics simulations support the orientation assignments, which -

File System, Files, and *Tab /Etc/Fstab
File system, files, and *tab File system files directories volumes, file systems mounting points local versus networked file systems 1 /etc/fstab Specifies what is to be mounted where and how fs_spec: describes block special device for remote filesystem to be mounted fs_file: describes the mount point fs_vfstype: describes the type of file system fs_mntops: describes the mount options associated with the filesystem 2 /etc/fstab cont. fs_freq: used by the dump command fs_passno: used by fsck to determine the order in which checks are done at boot time. Root file systems should be specified as 1, others should be 2. Value 0 means that file system does not need to be checked 3 /etc/fstab 4 from blocks to mounting points metadata inodes directories superblocks 5 mounting file systems mounting e.g., mount -a unmounting manually or during shutdown umount 6 /etc/mtab see what is mounted 7 Network File System Access file system (FS) over a network looks like a local file system to user e.g. mount user FS rather than duplicating it (which would be a disaster) Developed by Sun Microsystems (mid 80s) history for NFS: NFS, NFSv2, NFSv3, NFSv4 RFC 3530 (from 2003) take a look to see what these RFCs are like!) 8 Network File System How does this actually work? server needs to export the system client needs to mount the system server: /etc/exports file client: /etc/fstab file 9 Network File System Security concerns UID GID What problems could arise? 10 Network File System example from our raid system (what is a RAID again?) Example of exports file from -

Rve P.Vp:Corelventura
® M-8400RVe Thermal Transfer Printer Operator and Technical Reference Manual PN 9001075A SATO America, Inc. 10350-A Nations Ford Rd. Charlotte, NC 28273 Main Phone: (704) 644-1650 Fax: (704) 644-1661 Technical Support Hotline: (704) 644-1660 E-Mail:[email protected] © Copyright 2000 SATO America, Inc. Warning: This equipment complies with the requirements in Part 15 of FCC rules for a Class A computing device. Operation of this equipment in a residential area may cause unacceptable interference to radio and TV reception requiring the operator to take whatever steps are necessary to correct the interference. All rights reserved. No part of this document may be reproduced or issued to third parties in any form whatsoever without the express permission of SATO America, Inc. The materials in this document is provided for general information and is subject to change without notice. SATO America, Inc. assumes no responibilities for any errors that may appear. SATOM8400RVe PREFACE M-8400RVe PRINTER OPERATOR’S MANUAL The M-8400RVe Printer Operator’s Manual contains basic information about the printer such as setup, installation, cleaning and maintenance. It also contains complete instructions on how to use the operator panel to configure the printer. The following is a brief description of each section in this manual. SECTION 1. PRINTER OVERVIEW This section contains a discussion of the printer specifications and optional features. SECTION 2. INSTALLATION This section contains instructions on how to unpack and set up the printer, load the labels and ribbon. SECTION 3. CONFIGURATION This section contains instructions on how to configure the printer using the DIP switches and the LCD/Menu/Control panel. -

Filesystem Hierarchy Standard
Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Version 3.0 Publication date March 19, 2015 Copyright © 2015 The Linux Foundation Copyright © 1994-2004 Daniel Quinlan Copyright © 2001-2004 Paul 'Rusty' Russell Copyright © 2003-2004 Christopher Yeoh Abstract This standard consists of a set of requirements and guidelines for file and directory placement under UNIX-like operating systems. The guidelines are intended to support interoperability of applications, system administration tools, development tools, and scripts as well as greater uniformity of documentation for these systems. All trademarks and copyrights are owned by their owners, unless specifically noted otherwise. Use of a term in this document should not be regarded as affecting the validity of any trademark or service mark. Permission is granted to make and distribute verbatim copies of this standard provided the copyright and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this standard under the conditions for verbatim copying, provided also that the title page is labeled as modified including a reference to the original standard, provided that information on retrieving the original standard is included, and provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this standard into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the copyright holder. Dedication This release is dedicated to the memory of Christopher Yeoh, a long-time friend and colleague, and one of the original editors of the FHS. -

Advanced Bash-Scripting Guide
Advanced Bash−Scripting Guide An in−depth exploration of the art of shell scripting Mendel Cooper <[email protected]> 2.2 31 October 2003 Revision History Revision 0.1 14 June 2000 Revised by: mc Initial release. Revision 0.2 30 October 2000 Revised by: mc Bugs fixed, plus much additional material and more example scripts. Revision 0.3 12 February 2001 Revised by: mc Another major update. Revision 0.4 08 July 2001 Revised by: mc More bugfixes, much more material, more scripts − a complete revision and expansion of the book. Revision 0.5 03 September 2001 Revised by: mc Major update. Bugfixes, material added, chapters and sections reorganized. Revision 1.0 14 October 2001 Revised by: mc Bugfixes, reorganization, material added. Stable release. Revision 1.1 06 January 2002 Revised by: mc Bugfixes, material and scripts added. Revision 1.2 31 March 2002 Revised by: mc Bugfixes, material and scripts added. Revision 1.3 02 June 2002 Revised by: mc 'TANGERINE' release: A few bugfixes, much more material and scripts added. Revision 1.4 16 June 2002 Revised by: mc 'MANGO' release: Quite a number of typos fixed, more material and scripts added. Revision 1.5 13 July 2002 Revised by: mc 'PAPAYA' release: A few bugfixes, much more material and scripts added. Revision 1.6 29 September 2002 Revised by: mc 'POMEGRANATE' release: some bugfixes, more material, one more script added. Revision 1.7 05 January 2003 Revised by: mc 'COCONUT' release: a couple of bugfixes, more material, one more script. Revision 1.8 10 May 2003 Revised by: mc 'BREADFRUIT' release: a number of bugfixes, more scripts and material. -
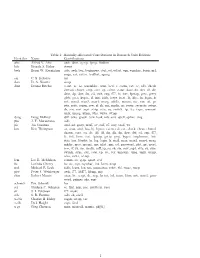
Manually-Allocated Contributions in Research Unix Editions Identifier Name Contributions Aho Alfred V
Table 1: Manually-Allocated Contributions in Research Unix Editions Identifier Name Contributions aho Alfred V. Aho awk, dbm, egrep, fgrep, libdbm bsb Brenda S. Baker struct bwk Brian W. Kernighan adv, awk, beg, beginners, ctut, ed, edtut, eqn, eqnchar, learn, m4, neqn, rat, ratfor, trofftut, uprog csr C. S. Roberts tss dan D. A. Nowitz uucp dmr Dennis Ritchie a.out, ar, as, assembler, atan, bcd, c, cacm, cat, cc, cdb, check, chmod, chown, cmp, core, cp, ctime, ctour, date, db, dev, df, dir, dmr, dp, dsw, du, ed, exit, exp, f77, fc, fort, fptrap, getc, getty, glob, goto, hypot, if, init, iolib, iosys, istat, ld, libc, ln, login, ls, m4, man2, man3, man4, mesg, mkdir, mount, mv, nm, od, pr, ptx, putc, regen, rew, rf, rk, rm, rmdir, rp, secur, security, setup, sh, sin, sort, sqrt, strip, stty, su, switch, tp, tty, type, umount, unix, uprog, utmp, who, write, wtmp doug Doug McIlroy diff, echo, graph, join, look, m6, sort, spell, spline, tmg jfm J. F. Maranzano adb jfo Joe Ossanna azel, ed, getty, nroff, ov, roff, s7, stty, troff, wc ken Ken Thompson ar, atan, atof, bas, bj, bproc, cacm, cal, cat, check, chess, chmod, chown, core, cp, dc, dd, df, dir, dli, dp, dsw, dtf, ed, exp, f77, fc, fed, form, fort, fptrap, getty, grep, hypot, implement, init, itoa, ken, libplot, ln, log, login, ls, mail, man, man2, man4, mesg, mkdir, moo, mount, mv, nlist, nm, od, password, plot, pr, qsort, rew, rf, rk, rm, rmdir, roff, rp, sa, sh, sin, sort, sqrt, stty, su, sum, switch, sync, sys, tabs, tp, ttt, tty, umount, uniq, unix, utmp, who, write, wtmp lem Lee E. -

Oracle® Linux 7 Managing File Systems
Oracle® Linux 7 Managing File Systems F32760-07 August 2021 Oracle Legal Notices Copyright © 2020, 2021, Oracle and/or its affiliates. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" or "commercial computer software documentation" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, reproduction, duplication, release, display, disclosure, modification, preparation of derivative works, and/or adaptation of i) Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs), ii) Oracle computer documentation and/or iii) other Oracle data, is subject to the rights and limitations specified in the license contained in the applicable contract. -

Www . Electricalpartmanuals . Com' Com .·�
. -� GEH-764AB SupiJf'sedes GEH-764AA com . Polyphase Switc.hboard ) :., ltatt... our Meters -.:-.. / ii' . _/ •, TYPES DS-19, DSW-19, DSM�19, DS-20, DSW-20 DSM-20, DS-341 DSW-341. DSM-341 DS-35 c DSW-351 DSM-35, DS-381 DSW-381 DSM-38 DS-39 I . DSW·-39:· DSM-39 I DS-40 I DSM-40 DSW-4 W-41, DSM-411 DS-43 DSW-441 DSM-44 ElectricalPartManuals . GENERAL . ELECTRIC www . ElectricalPartManuals . com' com .·� . TYPES COVERED • TWO-ELEMENT CONSTRUCTION THREE-ELEMENT CONSTRUCTION DS-19, DSW-19, DSM-19 (Surface Mount DS-20, DSW-20, DSM-20 (Surface Mount ing) ing) DS-34, DSW-34, DSM-34 (Semiflush Mount DS-35, DSW-35, DSM-35 (Semiflush Mount ing) ing) DS-38, DSW-38, DSM-38 (Drawout, Semi DS-39, DSW-39, DSM-39 (Drawout, Semi flush Mounting) flush Mounting) DS-40, DSW-40, DSM-40 (Drawout, Surface DS-41, DSW-41, DSM-41 (Drawout, Surface Mounting) Mounting) DS-43, DSW-43, DSM-43 (Drawout, Semi DS-44, DSW-44, DSM-44 (Drawout, Semi flush or Surface Mounting) flush or Surface Mounting) ElectricalPartManuals . These instructions do not purport to cover all details or variations in equipment nor to provide for every possible contingency to be met in connection with installation, operation or maintenance. Should further information be desired or should particular problems arise which are not covered sufficiently for the purchaser's purposes, the matter should be referred to the General Electric Company. 0 2 www . ElectricalPartManuals . com c POLYPHASE com SWITCHBOARD WATTHOUR METERS . The Types DS-19, DS-34, DS-38, DS-40, and DS-43 next inserted completing the electric circuits through meters are back-connected, switchboard, two-stator, the meter and locking the latch on the cradle. -

Name Synopsis Description Options
UMOUNT(8) System Administration UMOUNT(8) NAME umount − unmount file systems SYNOPSIS umount −a [−dflnrv][−t fstype][−O option...] umount [−dflnrv]{directory|device}... umount −h|−V DESCRIPTION The umount command detaches the mentioned file system(s) from the file hierarchy. A file system is spec- ified by giving the directory where it has been mounted. Giving the special device on which the file system livesmay also work, but is obsolete, mainly because it will fail in case this device was mounted on more than one directory. Note that a file system cannot be unmounted when it is ’busy’ - for example, when there are open files on it, or when some process has its working directory there, or when a swap file on it is in use. The offending process could evenbe umount itself - it opens libc, and libc in its turn may open for example locale files. Alazy unmount avoids this problem, but it may introduce another issues. See −−lazy description below. OPTIONS −a, −−all All of the filesystems described in /proc/self/mountinfo (or in deprecated /etc/mtab) are un- mounted, except the proc, devfs, devpts, sysfs, rpc_pipefs and nfsd filesystems. This list of the filesystems may be replaced by −−types umount option. −A, −−all−targets Unmount all mountpoints in the current namespace for the specified filesystem. The filesystem can be specified by one of the mountpoints or the device name (or UUID, etc.). When this option is used together with −−recursive,then all nested mounts within the filesystem are recursively un- mounted. This option is only supported on systems where /etc/mtab is a symlink to /proc/mounts. -

Managing Network File Systems in Oracle® Solaris 11.4
Managing Network File Systems in ® Oracle Solaris 11.4 Part No: E61004 August 2021 Managing Network File Systems in Oracle Solaris 11.4 Part No: E61004 Copyright © 2002, 2021, Oracle and/or its affiliates. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" or "commercial computer software documentation" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, reproduction, duplication, release, display, disclosure, modification, preparation of derivative works, and/or adaptation of i) Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs), ii) Oracle computer documentation and/or iii) other Oracle data, is subject to the rights and limitations specified in the license contained in the applicable contract.