PRO:MAN End-User Documentation [System Administration] [Utility]
[System Administration] Section III
Security
This section covers how to set up security on your system. This is primarily PRO:MAN security and not necessarily server security. Your server should have security and firewall protection as any other server on your network.
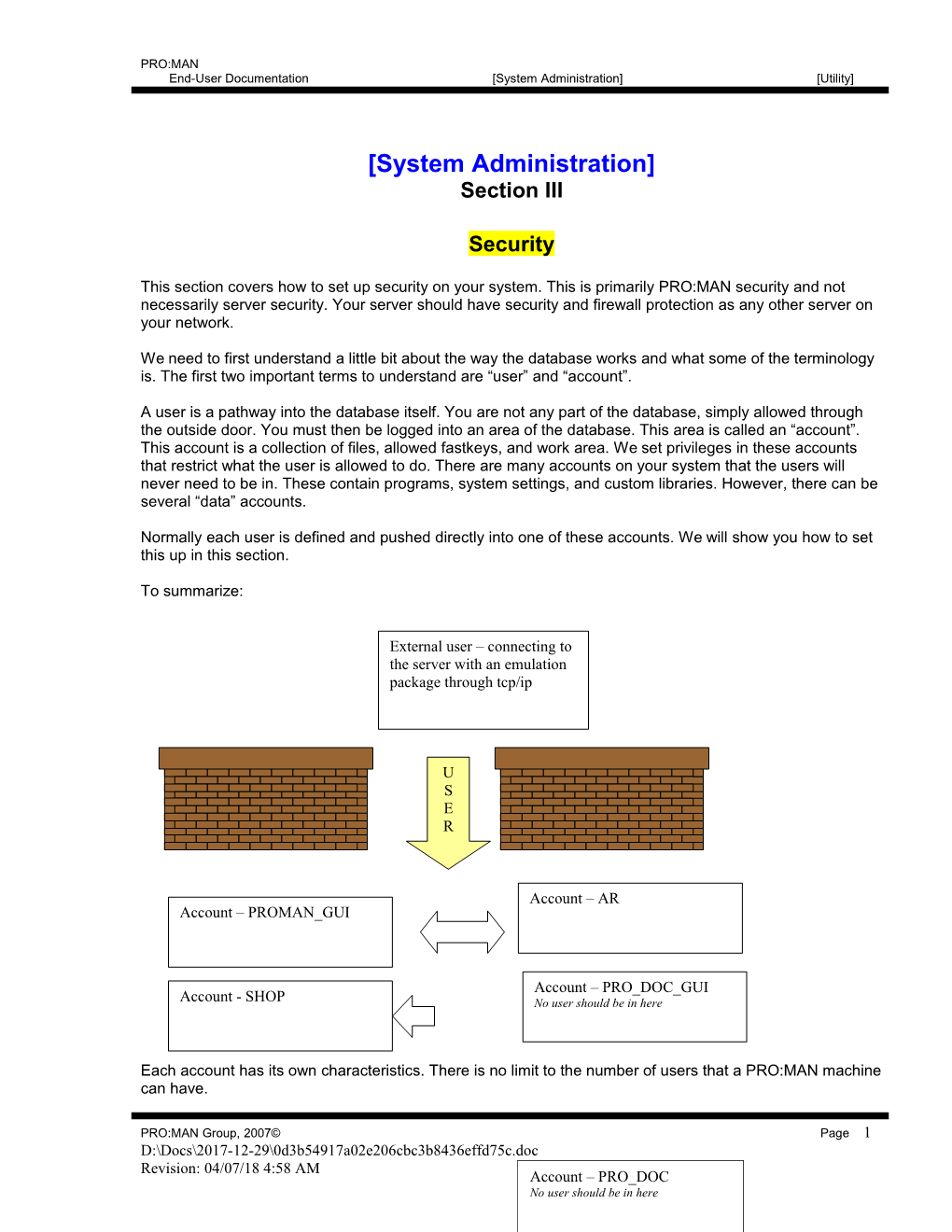
We need to first understand a little bit about the way the database works and what some of the terminology is. The first two important terms to understand are “user” and “account”.
A user is a pathway into the database itself. You are not any part of the database, simply allowed through the outside door. You must then be logged into an area of the database. This area is called an “account”. This account is a collection of files, allowed fastkeys, and work area. We set privileges in these accounts that restrict what the user is allowed to do. There are many accounts on your system that the users will never need to be in. These contain programs, system settings, and custom libraries. However, there can be several “data” accounts.
Normally each user is defined and pushed directly into one of these accounts. We will show you how to set this up in this section.
To summarize:
External user – connecting to the server with an emulation package through tcp/ip
U S E R
Account – AR Account – PROMAN_GUI
Account – PRO_DOC_GUI Account - SHOP No user should be in here
Each account has its own characteristics. There is no limit to the number of users that a PRO:MAN machine can have.
PRO:MAN Group, 2007© Page 1 D:\Docs\2017-12-29\0d3b54917a02e206cbc3b8436effd75c.doc Revision: 04/07/18 4:58 AM Account – PRO_DOC No user should be in here PRO:MAN End-User Documentation [System Administration] [Utility]
PASSWORD
There are two levels of passwords in D3, the database that PRO:MAN runs on. This section will show how to change users passwords. There is an optional security setting that can be set on SECURITY_MAINT. This is a sets of additional parameters and how passwords are entered. You can see that section below. The process is essentially the same, just what a password must look like and how long it is valid for.
Regardless of those settings, the way that a user changes their password remains the same. Below is an explanation of setting up a password for a user along with changing a users password.
The program will attempt a login using the User ID entered. If the User ID is invalid, the script will re-prompt for the User ID until a valid User ID has been entered or the cancel button is clicked. A valid User ID is one that is recognized by the ProMan system. This is one of the two levels of security provided by ProMan.
Once a suitable ProMan User ID has been enter and OK is clicked the following screen will appear:
The User ID field will auto fill from the name field entered in PROFILES_MAINT, and the user is prompted to enter a valid Password to proceed or click Close to end the session.
PRO:MAN Group, 2007© Page 2 D:\Docs\2017-12-29\0d3b54917a02e206cbc3b8436effd75c.doc Revision: 04/07/18 4:58 AM PRO:MAN End-User Documentation [System Administration] [Utility]
The password is validated against the users profiles set in PROFILE_MAINT. The number of attempts the user has to enter a valid password depend on the defaults set in SECUIRTY_MAINT. If the user exceeds the default number of times to enter a password a popup window will appear advising that “Your account has been locked. Contact your system administrator”
The user password will also have an expiry date based on the number of days since the last change, again this is set in SECURITY_MAINT. The number of days for a password to expire should be determined by the system administrator. After expiration of the password, the change password portion of the login screen will automatically be shown after a valid password has been entered. A new password must be entered before the system will allow the user to access the system. The “close” option may be used to exit without accessing the system. The next login attempt will again force a new password in the same way.
To change the existing password, a valid password must have been entered first. The “New Password” is validated against the optional criteria established by the system administrator:
1. Maximum password Length 2. Reuse option. Determines if the same password is allowed to be reused. 3. Alpha. Determines if an alpha character is required as part of the password. 4. Numeric. Determines if a numeric character is required as part of the password.
In addition, the number of days before the password must be changed and the option to encrypt the password when stored on the users profile is set by the administrator.
The “Confirm” value is matched against the “New Password” to insure the accuracy of the “New Password”.
Enter your new password. Note your CAPS lock key. Remember case is important. You will be prompted to re-enter it to confirm your password.
We covered how to make a user in Section II. This user is a name that identifies that person and the user should have a password on it. The level of the password security is dependant on your environment. It can be fairly light (a user can keep their password the same forever) or fairly tight (a user must change the password every so many days, and cannot reuse a password). These levels are set up in SECURITY_MAINT listed below. Only administrators should have access to this fastkey.
PRO:MAN Group, 2007© Page 3 D:\Docs\2017-12-29\0d3b54917a02e206cbc3b8436effd75c.doc Revision: 04/07/18 4:58 AM PRO:MAN End-User Documentation [System Administration] [Utility]
This screen is used to set the different security options that are available in ProMan when dealing with users passwords. If you are looking for a tighter security you may want to use all the option available, if you are look for a more low end security on your system you may only want to set a few defaults. This should be determined by the system administrator.
Check Password – Determines if the logic for password security is being used.
Password Minimum Length – sets the minimum length of a password.
Need at least one numbers – sets a flag that says all passwords that are entered must have at least one numeric character.
Need at least one alpha – sets a flag that says all passwords that are entered must have at least one alpha character.
Number of Days Password is good for – sets the number of days that a password is good for. The next time a users logs on, after their password has expired, will be prompted to enter a new password.
Can user Re-use Passwords – sets a flag to tell the system if a password can be reused
Encrypt Password in Log File – tells the system to encrypt the passwords in the password file. This means that administrators can not edit or list the file and see passwords and help users who have forgotten passwords. On the other hand, prying eyes can see other people's password.
Number of Attempts Allowed – number of attempts the user is allowed to enter their password incorrectly until there user ID is locked.
PRO:MAN Group, 2007© Page 4 D:\Docs\2017-12-29\0d3b54917a02e206cbc3b8436effd75c.doc Revision: 04/07/18 4:58 AM PRO:MAN End-User Documentation [System Administration] [Utility]
Fastkey Lists
Each time a fastkey is run, it is logged into a file. There are no system flags to turn this on or off, it is automatically done. Actually, the system tracks the last 200 times the fastkey was run, regardless of dates. The logging takes place no matter how they executed the fastkey, either from their menu or by typing the fastkey name in.
There are a couple of reports available to review these logs. They essentially show who ran what and when. You CANNOT tell what they typed as far as options when they ran the fastkey. You can see only the port, date, time, and user ID. Here is a list of these fastkeys:
Fastkey Description LIST_FASTKEY_LOG Provides either a summary of the number of times each fastkey was run, or prints full details of each time the fastkey was run. This can be a long report as it lists all fastkeys that have ever been run. There could be, hypothetically, 200 lines for each fastkey ever run. LIST_FASTKEY_LOG_DT Essentially the same as the previous report, except that it is date driven. The user can input a start and ending date. LIST_FASTKEY_LOG_IND This report only shows the results for one fastkey. It is either a summary or a detail version. This is typically used to see who ran “fastkey” today. LIST_FASTKEY_LOG_USR This report shows the log information for a single user (not a user account, but a user ID).
These reports can be useful when trying to determine what processes are being run and when.
Transaction Log
There are times when certain data is being changed and we need to know who is doing it. The system could not track every transaction ever put in by a user. It can, however, track information of interest. We provide a “field” level flag to tell the system to start tracking any change to this data. This only works from data entry screens and the field must be on a screen. It does not track items that are “behind the scenes” transactional data. To turn the tracking on, you need to know the file name and the file attribute. This information is fairly easy to obtain.
On any data entry screen, you can press the F1 key for help. This will force the system into a help screen. One such example:
PRO:MAN Group, 2007© Page 5 D:\Docs\2017-12-29\0d3b54917a02e206cbc3b8436effd75c.doc Revision: 04/07/18 4:58 AM PRO:MAN End-User Documentation [System Administration] [Utility]
When your curse is in the field you would like to obtain information on press F1, you will see a help screen for this field. The information that we want to know is shown on the right-hand side.
In our example above, we can see the file name is CM and the attribute is “96”. With this information, use the fastkey called FS_UPDATE. This screen will prompt you for the File Name and Amc Nbr.
PRO:MAN Group, 2007© Page 6 D:\Docs\2017-12-29\0d3b54917a02e206cbc3b8436effd75c.doc Revision: 04/07/18 4:58 AM PRO:MAN End-User Documentation [System Administration] [Utility]
The field that tells the system to audit any changes is Audit. The default is no checkmark for the entire system. You need to place a checkmark in this field.
The next time that a user updates this data (either on the CUSTOMERS screen or any other data entry screen that allows the update of the same information) it will be tracked in a log file with the old information and the new information. Note: If the user is currently in the screen when the change to FS_UPDATE was done, it will not take effect until they get out of the screen and get back into the fastkey.
There is a report to show information that has been logged into our “transactional logger”. This fastkey is called TRX_LOG_RPT. It allows several options.
This report is date driven. The user has the option to print the report, view the report in spool, display grid, notepad, excel, PDF, and as a HTML file. The example below shows the report being viewed in a display grid.
PRO:MAN Group, 2007© Page 7 D:\Docs\2017-12-29\0d3b54917a02e206cbc3b8436effd75c.doc Revision: 04/07/18 4:58 AM PRO:MAN End-User Documentation [System Administration] [Utility]
PRO:MAN Group, 2007© Page 8 D:\Docs\2017-12-29\0d3b54917a02e206cbc3b8436effd75c.doc Revision: 04/07/18 4:58 AM