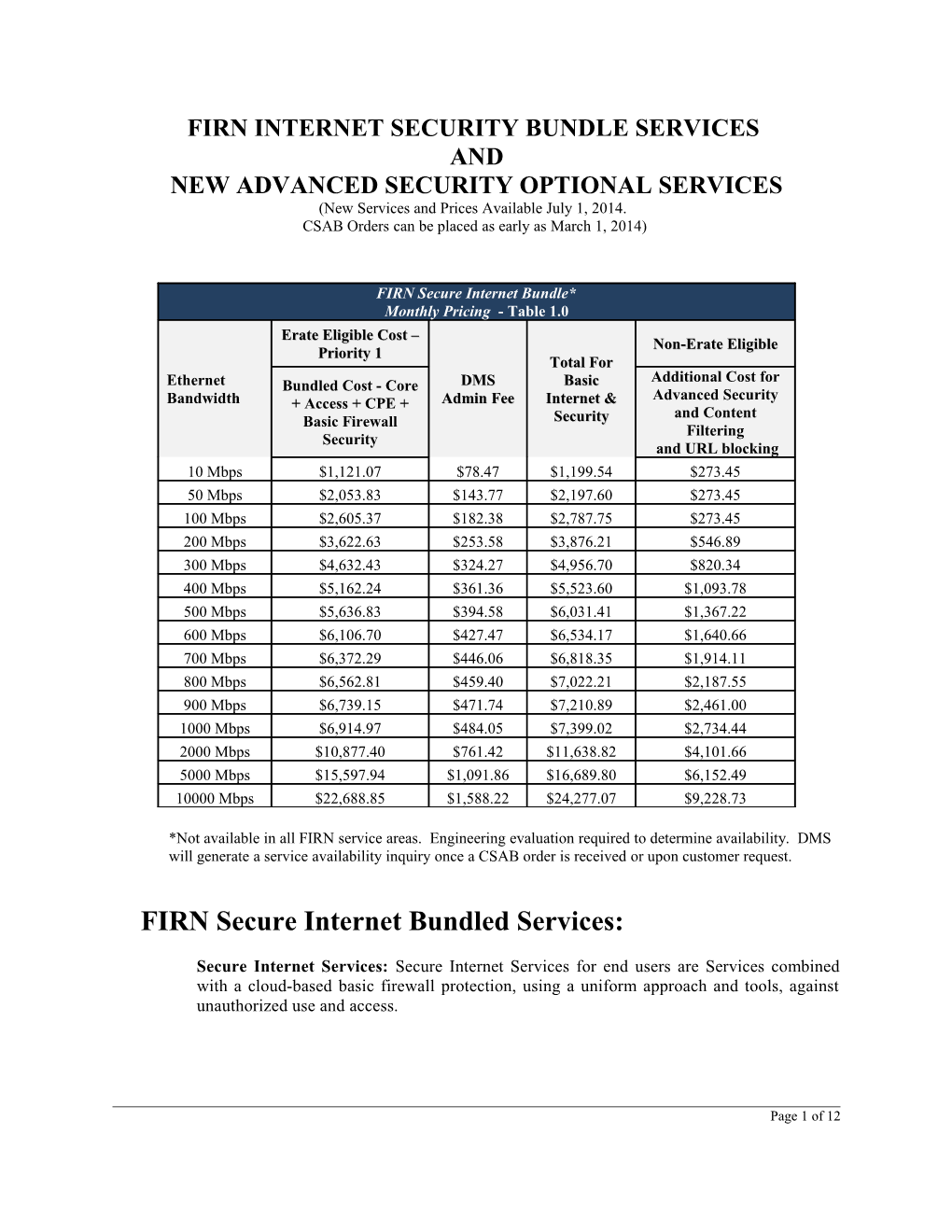
FIRN INTERNET SECURITY BUNDLE SERVICES AND NEW ADVANCED SECURITY OPTIONAL SERVICES (New Services and Prices Available July 1, 2014. CSAB Orders can be placed as early as March 1, 2014)
FIRN Secure Internet Bundle* Monthly Pricing - Table 1.0 Erate Eligible Cost – Non-Erate Eligible Priority 1 Total For Additional Cost for Ethernet Bundled Cost - Core DMS Basic Advanced Security Bandwidth + Access + CPE + Admin Fee Internet & and Content Basic Firewall Security Filtering Security and URL blocking 10 Mbps $1,121.07 $78.47 $1,199.54 $273.45 50 Mbps $2,053.83 $143.77 $2,197.60 $273.45 100 Mbps $2,605.37 $182.38 $2,787.75 $273.45 200 Mbps $3,622.63 $253.58 $3,876.21 $546.89 300 Mbps $4,632.43 $324.27 $4,956.70 $820.34 400 Mbps $5,162.24 $361.36 $5,523.60 $1,093.78 500 Mbps $5,636.83 $394.58 $6,031.41 $1,367.22 600 Mbps $6,106.70 $427.47 $6,534.17 $1,640.66 700 Mbps $6,372.29 $446.06 $6,818.35 $1,914.11 800 Mbps $6,562.81 $459.40 $7,022.21 $2,187.55 900 Mbps $6,739.15 $471.74 $7,210.89 $2,461.00 1000 Mbps $6,914.97 $484.05 $7,399.02 $2,734.44 2000 Mbps $10,877.40 $761.42 $11,638.82 $4,101.66 5000 Mbps $15,597.94 $1,091.86 $16,689.80 $6,152.49 10000 Mbps $22,688.85 $1,588.22 $24,277.07 $9,228.73
*Not available in all FIRN service areas. Engineering evaluation required to determine availability. DMS will generate a service availability inquiry once a CSAB order is received or upon customer request.
FIRN Secure Internet Bundled Services:
Secure Internet Services: Secure Internet Services for end users are Services combined with a cloud-based basic firewall protection, using a uniform approach and tools, against unauthorized use and access.
Page 1 of 12 FIRN Secure Internet includes:
a) Internet Access b) Local Transport Facilities c) Premise Router d) Cloud Based Basic Firewall Service
The cloud-based basic firewall provides the following security functions for all virt ual contexts:
a) The Sandbox Analyzer to identify and analyze targeted and unknown files for mal icious behaviors. It shall generate and automatically deliver protection for newly di scovered malware via signature updates. Signature update delivery shall include int egrated logging/reporting. b) Geo Blocking to prevent network based access to internal resources by blocking ba sed on geographic location. c) Application Blocking to identify and block unwanted applications without regard t o the port they are using for communication. d) Security Information and Event Management (SIEM): Secure Internet Services will include detailed information provided by the MyFloridaNet QRadar tool. DMS and each Secure Internet Services end user will receive two QRadar login accounts allowing them accurate, correlating information regarding network flows (500:1 sa mpling), session data, packet captures, reputation white/black listing and endpoint s ystem vulnerability results providing the maximum amount of detail to traffic trave rsing their network connection. This access shall give Secure Internet Services end users visibility into their Internet connection activity, virtual activity, user activity a nd application activity, giving them intelligence into their FIRN Secure Internet co nnection.
The cloud-based firewall will provide the following optional more advanced securi ty functions for all virtual contexts subscribing to the Advanced Security and Content Filtering service at the pricing listed in the second column of Table 1.0.
a) NextGeneration IPS & IDS: By proactively applying deep packet and application inspection of network activity at the border of the FIRN and the internally protected zones, service will provide better analysis and overall security for each FIRN Orga nization. Automated correlation and Intrusion Analysis by this service will provide notifications of suspected unauthorized network activity and has the ability to preve nt the activity from ever reaching the end user’s internal network. This feature is pa rt of the advanced cloud-based firewall deployment. b) Malware & Anti-Virus detection: This service feature provides real time anti-viru s and anti-malware protection. End users will have the ability to automatically take action on malicious files currently in transport across the network. This feature wil l block unwanted malware and viruses at our edge devices before they consume Int ernet bandwidth or threaten the local network and ultimately desktop endpoint syste ms users depend on to access the Internet. This feature is part of the advanced clou d-based firewall deployment. c) Next Generation Content Filtering/URL Blocking is enabled upon request. This service helps End users enforce their protection policies and block inappropriate, ill egal, and dangerous web content. It will have the ability to block multiple categori
Page 2 of 12 es of objectionable web content, providing the necessary combination of control an d flexibility to protect important resources. The service will deliver sophisticated r eporting and visually descriptive monitoring through dashboards, graphs, charts, an d data search functionality. This feature is part of the advanced cloud-based firewa ll deployment.
FIRN Help Desk
a) FIRN Secure Internet includes access to our standard FIRN helpdesk to provide ass istance directly to FIRN end users to answer questions related to all FIRN Secure I nternet service tools and services. b) The helpdesk will work directly with the end user to provide advice on remediation methods and industry best practices as they relate to services FIRN provides as part of our Secure Internet offering. c) The helpdesk will be staffed live and/or offer immediate call back within thirty (3 0) minutes 24x7x365. d) The Secure Internet Service staff will perform daily “eyes on glass” real-time monit oring and analysis of security events. Monitoring and analysis shall span multiple s ources including but not limited to events from the security tools (SIEM), MFN net work tools, NetFlow logs, firewall logs, and router logs.
New Secure Internet and Advanced Security & Content Filtering
Secure Internet services shall be offered based on the rates provided in Table 1.0 below. All current FIRN Internet Services shall remain with the exception of the following changes:
1) Pricing for Secure Internet Services is flat rate (included in Table 1.0) in the AT&T, CenturyLink and Verizon LATA areas. This new pricing shall be an addition to the flat rate and mileage band pricing originally available under the FIRN contract. The new flat rates in Table 1 may not apply outside of these areas. Any connections outside of the AT&T, Century Link, and Verizon LATAs shall be priced as an individual case basis (ICB). ICB pricing shall never be more than the original flat rate pricing available under the original FIRN contract.
2) A FIRN managed CPE router is included in the standard service. However, the FIRN end-user may choose to manage the FIRN CPE router or provide and manage their owned CPE router as long as it is certified by the FIRN Service Provider. The option to manage the CPE router is at no additional cost to the end user.
3) The FIRN Secure Internet service bundle introduces performance measures via Service Level Agreements for Install, Moves, Adds, Changes and Outages with the following Table 2.0
Page 3 of 12 Service Performance Measures Table 2.0 SLA Performance Target Liquidated Measurement Damages Install, Moves, Adds, 64kbps to T1 = 60 days 10% MRC of Measured and calculated Changes (“IMAC”) Service* if per incident based on the >T1 to 45Mbps = 80 performance is not operational tools provided. business days met. FIRN will not be liable where facilities do not >45Mbps = 180 exist for access types business days (excluding Ethernet) greater than 12 Mbps. Site Outage & Service Within twenty-four 5% MRC of the Measured using the Troubles – Restore (24) hours Monday – entire service if trouble ticketing system. Friday. outage > 24 hours SLA clock will start when the trouble has been reported in the ticketing system. The SLA clock will stop when the site has been restored and verified with the end user. For all service troubles, FIRN must open trouble tickets pro-actively and immediately when the outage has been discovered. The time between the actual outage and the opened trouble ticket was opened will be counted towards SLA restoral time. For example: if an outage occurred at 1:00PM and the trouble ticket was opened at 1:30PM, 30 minutes of this time will be counted towards the SLA restoral time. *MRC of Service = MRC of (Core Port + CPE + Access) for each site
Note: Secure Internet service shall be available and pricing effective July 1st, 2014.
FIRN Advanced Security Offerings (ASO):
A. ASO can be purchased by end users as an Advanced Security Bundle (ASB) (see B.). Some of these ASB as well as other Advanced Security Offerings may also be purchased separately (See I-J.). B. Advanced Security Bundle (ASB): ASB includes, for each end user selected location (distr ict headquarters):
Page 4 of 12 1) Fully Managed Device for On-site Intrusion Prevention System (IPS) Device and Servic e.
2) Fully Managed Device for On-site Premise Firewall Event Logging Management, Analys is and Notification of end user District Area Network (DAN) Firewall.
3) Fully Managed Device for On-site end user Device Event Logging Management and Ana lysis for up to 15 devices per end user location.
4) Fully Managed Counter Threat Appliance (CTA) to assimilate logging information from all end user selected sources passing on significant events for further analysis.
5) Fully Managed Cloud Based Security Information and Event Management (SIEM) Correl ation via forwarded information from the CTA.
6) End User Portal for detailed information regarding their Security incidents and security p osture.
C. Intrusion Prevention System (IPS): IPS helps eliminate malicious inbound and outbound traffic 24x7x365, without device or signature management, and without increasing in-house headcount. IPS service lets the end user comply with data loss regulations to protect against threats to sensitive data by centralizing the analysis of all devices including firewall logs and provides comprehensive reporting via the FIRN’s end user portal to demonstrate the effectiveness of the end user’s security controls. The IPS device can be attached to the End User network to provide Intrusion Detection with the onus then on the end user to implement appropriate corrective action. Alternatively, the IPS can be placed in-line of Internet traffic, in which case the FIRN service provider shall implement recommended security response to the intrusion. IPS includes:
1) Configuration and implementation.
2) Administration and tuning.
3) 24x7x365 Real-time security event and device health monitoring.
4) Upgrade, change, and patch management.
5) Thousands of unique countermeasures.
6) Daily audits of existing rules.
7) Advanced analysis and blocking techniques, including advanced statistical analysis, suspicious activity correlation and expert security analysis of patterns.
8) Twice weekly countermeasure updates.
9) Intelligence-enhanced threat protection.
10) On-demand security and compliance reporting.
D. Firewall Event Logging: Monitoring of any supported end user premise firewall listed below and support for next generation and HA Firewall pairs at no additional charge. Log information shall be incorporated into the provided SIEM and any SIEM indications of a
Page 5 of 12 problem are analyzed by security professionals in near real time and end user are notified of any significant firewall events complete with recommended firewall configuration changes. End users desiring a full proactively managed firewall solution can combine this offering with existing FIRN contract firewall management options. Supported firewall devices are:
1) Cisco
2) Juniper Networks
3) Palo Alto Networks
4) Dell SonicWALL
5) Check Point
6) Fortinet
E. End User Device Event Logging: The 15 devices can be any mixture of any supported devices (servers, routers, etc.) capable of sending log information to the provided logging device. The logging information shall be fed into the SIEM similar to the Firewall log information and proactively responded to the same way, resulting in notification of the end user of any suspicious activity complete with recommended actions.
F. Counter Threat Appliance (CTA): The CTA resides on the end user’s network and shall be responsible for maintaining connections to all sources an end user needs monitored and managed. The CTA shall collect logs from these sources and handles parsing, normalization, de-duplication and filtering of collected events. Security events of interest are sent from the CTA to the FIRN’s Security Operations Centers (SOC) via a secured connection, where they are prioritized and, if needed, reviewed by the FIRN’s service provider certified Security Analysts to determine if any malicious or suspicious activity is occurring. Additionally, the CTA is a secure point from which FIRN’s Security Analysts can provide device management. Through the secured connection, the CTA shall have the capability to enable communications and administrative activities for vendor managed devices.
G. End User Portal and Reports: The End User Portal shall provide the intelligence and analytics needed to easily understand the risks, demonstrate compliance and make better security decisions. The Portal shall give end users full visibility into their security and compliance posture with advanced reporting functionality integrated across all proffered Advanced Security Offerings. The End User Portal shall include a mobile application ensuring security data is always at the end user’s fingertips.
H. Advanced Security Bundled Pricing
Page 6 of 12 ASB Monthly Pricing Table 2.0 Bandwidth Monthly Recurring 10 Mbps $3,651.91 50 Mbps $3,651.91 100 Mbps $3,651.91 200 Mbps $3,977.19 300 Mbps $4,428.73 400 Mbps $4,428.73 500 Mbps $4,428.73 600 Mbps $4,712.28 700 Mbps $4,712.28 800 Mbps $4,712.28 900 Mbps $4,712.28 1,000 Mbps $4,712.28 2,000Mbps* $9,424.56 5,000Mbps* $23,561.40 10,000Mbps* $47,122.80
*Where available
Standalone Advanced Security Options.
End user may purchase any of the products and services described below.
1) IPS Monitoring is as described in C. 3) above. Pricing for those wishing to buy as a standalone product is as follows:
IPS Monitoring Monthly Pricing - Table 3.0 Internet Bandwidth Monthly Recurring 0 Mbps to 100 Mbps $936.25 101 Mbps to 1000 Mbps $1,471.25 1001 Mbps to 2000 Mbps $1,658.50
2) IPS Management was included and described in the bundled offering. Pricing for those wishing to buy as a standalone product is as follows:
Page 7 of 12 IPS Management Monthly Pricing - Table 4.0 Internet Bandwidth Monthly Recurring 0 Mbps to 100 Mbps $1,671.34 101 Mbps to 500 Mbps $2,228.81 501 Mbps to 1000 Mbps $3,477.50 1001 Mbps to 2000 Mbps $4,796.81 2001 Mbps to 4000 Mbps $6,464.94 4001 Mbps to 10000 Mbps $9,674.94
3) End User Device Event Monitoring was included and described in for up to 15 devices in the bundled offering. For those wishing to buy monitoring for additional devices or as a standalone offering pricing is as follows:
Device Monitoring Monthly Pricing - Table 5.0 Device Count Monthly Recurring 1 $133.75 15 $1,605.00 200 $12,216.19 500 $23,451.19
4) Vulnerability Management service identifies exposures and weak spots in end user environments by performing highly accurate external scanning and internal scanning across the network. Vulnerability Management shall enable vulnerability scanning without the hardware, software and maintenance requirements of scanning products. Vulnerability results shall be integrated into FIRN’s other Managed Security Services, allowing threats against vulnerable and non-vulnerable systems to be assessed and prioritized accordingly.
The Vulnerability Management technology shall be fully managed and maintained by the FIRN’s dedicated vulnerability management team, eliminating administration and maintenance burdens so end users can better focus on protecting assets and reducing risks. Vulnerability Management includes:
a) Highly accurate internal and external vulnerability scanning.
b) Support for physical, cloud and virtual infrastructure.
c) Dedicated vulnerability management team to provide expert guidance and support.
d) Flexible reporting and remediation workflow tools via on-demand portal.
e) 24x7x365 expert support by certified security analysts. Page 8 of 12 Vulnerability Management service Monthly Pricing - Table 6.0 Network or Monthly Recurring Server Device Count 128 $642.00 512 $1,337.50 1024 $12,751.19 Application Count Monthly Recurring 10 $820.69 25 $1,337.50 160 $3,477.50
5) Log Retention Services shall be a fully-managed service that provides support for a wide range of sources, allowing capture and aggregation of the millions of logs generated every day by critical information assets such as servers, routers, firewalls, databases, applications and other systems. The Log Retention Services shall support hundreds of devices per appliance. Log Retention Services Include:
a) Log Retention device with 13TB of compressed storage (3.8TB uncompressed).
b) Capturing and storing end user-specified system logs from the IT devices, systems and other network assets to the Log Retention Appliance.
c) Implementing software upgrades and security patches to Log Retention Appliance Monitor the information security, system health and performance of Log Retention Appliances 24x7x365.
d) Provide end user client access to the Logs.
e) Configure any Log Retention Appliance native alerting functionality to provide aler ting to notify end user of any such end user Devices no longer transmitting Logs to the Log Retention Appliances.
f) Act as the initial point of contact for end user support.
Log Retention Services Monthly Pricing - Table 7.0 (13TB Compressed Capacity) End User Device Count Monthly Recurring 25 $2,380.75 100 $2,688.91 500 $3,298.81 Page 9 of 12 Additional 13/3 8TB Capacity $1,337.50
Security Incident Response and Consulting:
1) The Incident Response and Digital Forensics practice shall help provide rapid containment and eradication of threats, minimizing the duration and impact of a security breach. Leveraging elite cyber threat intelligence and global visibility, FIRN shall help end users prepare for, respond to and recover from even the most complex and large- scale security incidents. The rate is based upon a response tailored to the particular event and is on a per-end user basis.
Incident Response Service Monthly Pricing - Table 8.0 Minimum 50 hours Hourly Rated 1 $449.40* *Includes travel and expenses, discounts may be available for additional hours needed during same on-site visit
The FIRN’s Security and Risk Consulting (SRC) group shall help customers solve security and compliance challenges. FIRN shall provide services listed below:
Regulatory and Compliance Testing and Analysis
GLBA (Gramm-Leach-Bliley Act) Gap Analysis Vulnerability HIPAA (Health Insurance Portability and Accountability Assessments Act) Gap Analysis Penetration Testing FISMA (Federal Information Security Management Web Application Act)/NIST (National Institute of Standards and Assessments Technology) Gap Analysis Network Security PCI (Payment Card Industry) Gap Analysis Assessment QSA (Qualified Security Assessor) On-Demand Physical Security ISO (International Organization for Standardization) Assessment 2700x Gap Analysis Wireless Network General Controls Audit Testing Information Security Assessment Social Engineering Security Architecture Review War Dialing Governance Review Data Discovery and Facility Clearance Readiness Review Classification E-Discovery (Electronic Discovery) Security and Compliance Attestation Reporting Third-Party Diligence and Vendor Management IT (Information Technology) Risk Assessment
Note: Page 10 of 12 The Gramm-Leach-Bliley Act (GLBA) requires financial institutions to develop, implement, and maintain a comprehensive written information security program that protects the privacy and integrity of end user records.
The Health Insurance Portability and Accountability Act of 1996 (HIPPA) includes: the HIPAA Privacy Rule, which protects the privacy of individually identifiable health information; the HIPAA Security Rule, which sets national standards for the security of electronic protected health information; the HIPAA Breach Notification Rule, which requires covered entities and business associates to provide notification following a breach of unsecured protected health information; and the confidentiality provisions of the Patient Safety Rule, which protect identifiable information being used to analyze patient safety events and improve patient safety.
Payment Card Industry (PCI) Gap Analysis are designed to combat identity theft and to better secure credit card data. Credit card associations created the Payment Card Industry (PCI) Data Security Standard (DSS) and expect organizations that process, store or transmit cardholder data to comply with these standards.
ISO (International Organization for Standardization) 2700x is a series of specifications which include Information Security Management Systems whose focus is based on evaluating process rather than content. These standards contain a Code of Practice consisting of a comprehensive set of information security control objectives and a menu of best practice security controls.
Security Risk Consulting Service Monthly Pricing - Table 8.0 Minimum 50 hours Hourly Rated 1 $385.20* * Includes travel and expenses
2) All CSAB orders shall include a statement-of-work to be reviewed and approved by DMS and end user. The statement-of-work template shall be defined in the operational and user guide. Service Level Objectives:
Security Risk Consulting Service Service Level Objectives - Table 9.0
SLO Type Description Action
Security Monitoring (applicable End user shall receive a response (according 1/30th of monthly fee to ASB and Standalone options) to the escalation procedures defined in the for Service for the End User Portal or in the manner pre- affected device selected in writing by End user, either through the help desk ticketing system,
Page 11 of 12 email, or by telephone) to security incidents within fifteen (15) minutes of the determination by the Service Provider that given malicious activity constitutes a security incident. This is measured by the difference between the time stamp on the incident ticket created by the SOC personnel or technology and the time stamp of the correspondence documenting the initial escalation. A “security incident” is defined as an incident ticket that comprises an event (log) or group of events (logs) that is deemed high severity by the SOC. The most up-to- date version can always be found in the Real-Time Events section of the End User Portal). Automatically created incident tickets (via correlation technology) and event(s) or log(s) deemed low severity will not be escalated, but will be available for reporting through the End user portal. Active Health Monitoring (for Active health checks identifying the 1/30th of monthly fee all FIRN provided devices) following conditions are subject to the for Service for the following SLAs: affected device
Device Unreachable – 30 minute response (via phone, ticket, or email) from identification of the device being unreachable. This is measured by the difference between the time stamp on the device unreachable ticket created by the SOC personnel or technology and the time stamp of the correspondence documenting the initial escalation.
Page 12 of 12