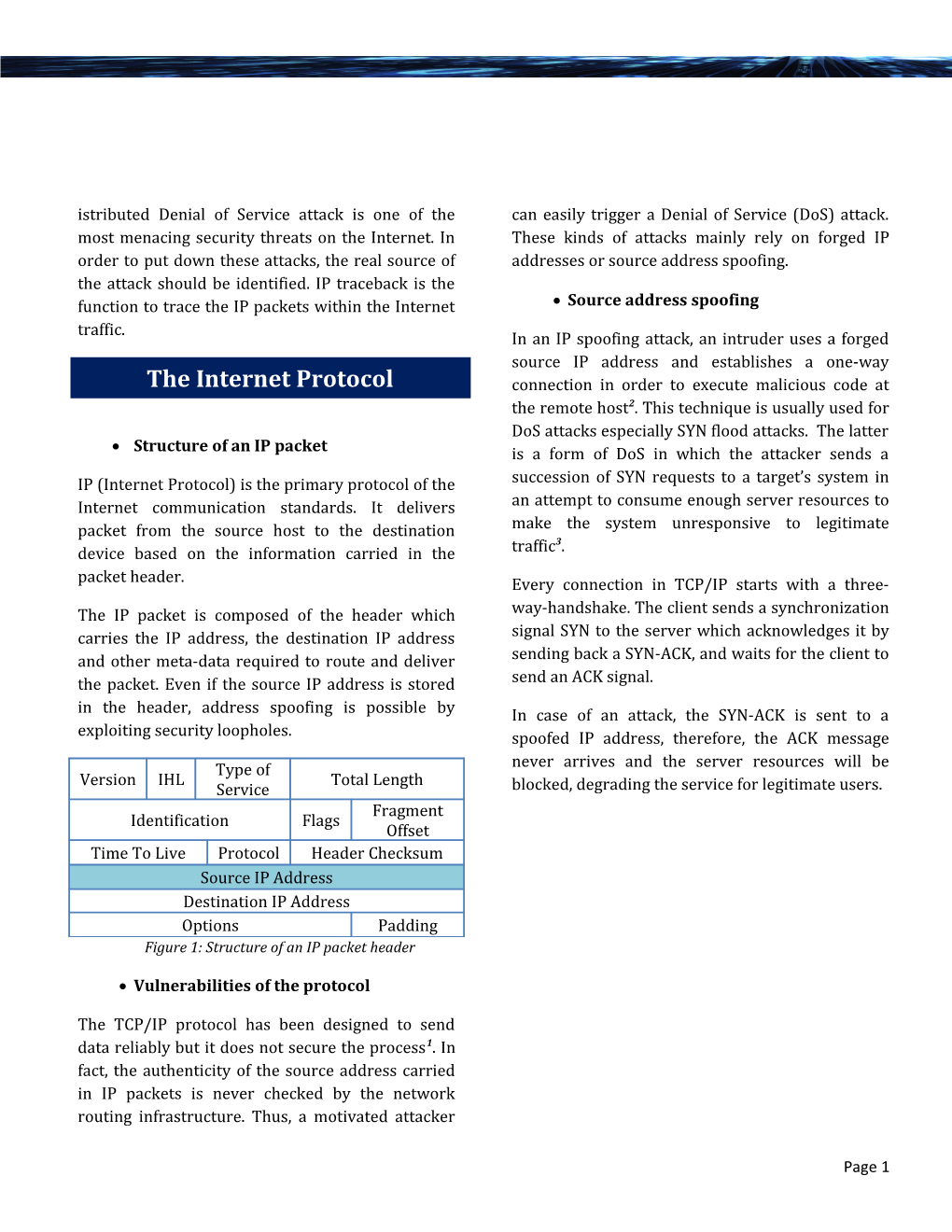
istributed Denial of Service attack is one of the can easily trigger a Denial of Service (DoS) attack. most menacing security threats on the Internet. In These kinds of attacks mainly rely on forged IP order to put down these attacks, the real source of addresses or source address spoofing. the attack should be identified. IP traceback is the function to trace the IP packets within the Internet Source address spoofing traffic. In an IP spoofing attack, an intruder uses a forged source IP address and establishes a one-way The Internet Protocol connection in order to execute malicious code at the remote host2. This technique is usually used for DoS attacks especially SYN flood attacks. The latter Structure of an IP packet is a form of DoS in which the attacker sends a IP (Internet Protocol) is the primary protocol of the succession of SYN requests to a target’s system in Internet communication standards. It delivers an attempt to consume enough server resources to packet from the source host to the destination make the system unresponsive to legitimate 3 device based on the information carried in the traffic . packet header. Every connection in TCP/IP starts with a three- The IP packet is composed of the header which way-handshake. The client sends a synchronization carries the IP address, the destination IP address signal SYN to the server which acknowledges it by and other meta-data required to route and deliver sending back a SYN-ACK, and waits for the client to the packet. Even if the source IP address is stored send an ACK signal. in the header, address spoofing is possible by In case of an attack, the SYN-ACK is sent to a exploiting security loopholes. spoofed IP address, therefore, the ACK message Type of never arrives and the server resources will be Version IHL Total Length Service blocked, degrading the service for legitimate users. Fragment Identification Flags Offset Time To Live Protocol Header Checksum Source IP Address Destination IP Address Options Padding Figure 1: Structure of an IP packet header
Vulnerabilities of the protocol
The TCP/IP protocol has been designed to send data reliably but it does not secure the process1. In fact, the authenticity of the source address carried in IP packets is never checked by the network routing infrastructure. Thus, a motivated attacker
Page 1 (Distributed) Denial of Service the origin of the malicious packets. This attacks will localise the next upstream router. The major drawback of this simple method is DoS disables network services for that it requires a strong interoperability legitimate users. An attack starts when between routers, and the attack must still computers are infected with malware and be in progress while the tracing of turned into botnets. These machines malicious packet takes place. become the compromised hosts. There are two kinds of compromised hosts: Comparison of Existing IP The Zombies: They launch the SYN Traceback Techniques flooding attack through uncompromised machines that communicate with the victim’s machine through the three-way- IP traceback techniques can be classified handshake protocol. These as pro-active or reactive. uncompromised machines are called A pro-active approach locates the source “reflectors”. after the attack by looking at the records The Stepping Stones: They act as files and logs of the network. intermediate nodes between the attacker A reactive approach locates the attacker and the zombies to make it harder to on the flight when the attack is detected discover the attacker. by a specialised hardware. IP Traceback The comparison of traceback techniques will focus on three illustrative methods which belong to different classes of IP DDoS attack is a growing concern as it traceback techniques. These techniques targets a broad range of industries, from remain at the stage of research and are e-commerce to financial institutions, it can not yet released in the market. The Source lead to a significant loss of money because Path Isolation Engine (or hash-based) of unavailability of service. Preventive algorithm is an in-band pro-active measures against these attacks are techniques. The iCaddie ICMP is the available, but the identification of the evolution of the ICMP out-of-band source of attack and prevention of any traceback technique. The third one is the recurrences are also crucial to a good reactive IDIP mechanism. practice of cyber security. Source Path Isolation Engine One of the ways to achieve IP traceback is (SPIE) hop-by-hop link testing. When an attack is launched, the network administrator will SPIE, or Hashed-based IP traceback is log into the closest router to the victim used to trace the origin of a single packet. and analyse the packet flow to determine This system was proposed by Snoeren et
Page 2 al5. It is a packet logging technique which limited duration of time because of space means that it involves storing packet constraint. digests at some crucial routers. The main issue is that the storage of saved packet Packet digests are created by Data data requires a lot of memory. SPIE is of Generation Agent (DGA) at each router. high storage efficiency and thus reduces Before a traceback begins, an attack the memory requirement (0.5% of the link packet must be detected. To determine it, capacity per unit time in storage). In fact, an intrusion detection system (IDS) is instead of storing the packets, it uses used. IDS provides a packet, the last hop auditing techniques. It computes and router, the time of attack, to the SPIE stores 32-bit packet digest. Moreover, an Traceback Manager (STM) which will efficient data structure to store packet verify its authenticity and integrity. Upon digest is mandatory. SPIE uses Bloom successful verification, STM will send the filter structure. signature information to the SPIE Collection and Reducing Agent (SCAR) Another important issue of packet logs is responsible for the victim’s network area. the risk of eavesdropping. Storing only If any match is found, the SCAR returns a packet digests and not the entire packet partial attack graph of the involving prevents SPIE from being misused by routers. Then STM will then send new attackers. Therefore, the network is queries to another SCAR region. This protected from eavesdropping which is process continues until the attack path is one of the criteria of an effective IP constructed. Finally, the STM sends the traceback system. result back to the IDS.
There are two options to determine the route of a packet flow. The first one is to audit the flow while it passes through the network and the second is to attempt to infer the route based on its impact on the state of the network. The difficulty of using them increases as the size of the packet flow decreases. Especially, the second one becomes impossible because small flows have no detectable impacts on the network. Thus, an audit option is used in SPIE.
SPIE is also called hash-based IP traceback because a hash of the invariant fields in the IP header is stored in each router as a 32-bit digest. It remains stored only for a
Page 3 iCaddie ICMP iii. The computational overhead of the attack path construction process In out-of-band pro-active schemes, the tracing mechanism is conducted with the help of separate iv. The storage capacity to collect and store packets generated at the routers when the information for path construction malicious packet traverses through them. Like iTrace, the Caddie message is an extra ICMP The most used technique is the ICMP Traceback message generated by a router or an application, (iTrace). As a packet traverses through the called a Caddie initiator. Attached to it is the entire network, an ICMP (Internet Control Message packet history of one randomly selected packet, Protocol)7 packet is generated by the router every called a Ball packet, which is forwarded by the 20,000 packets that pass through it. ICMP router. In fact, while a router is forwarding messages are contained within standard IP packets, it randomly selects one of the packets as a packets, thus the header structure is the same as ball packet. The Caddie message will collect the the IP one. The iTrace payload contains useful path information about the sequence of the routers information about the router visited by IP packets (called Caddie propagators) identity along the way such as router’s ID, information about the adjacent toward the ball packet’s destination. routers, timestamp, MAC address pair of the link traverse, etc. Thus, the victim is able to infer the true source of the IP packet from the information available. As most of the DoS attacks are flooding attacks, a sufficient amount of trace packets is likely to be generated. This technique does not require any modification of the existing infrastructure. However, it consumes considerable bandwidth and requires a large number of packets to traceback an attacker. It also has a poor handling of DDoS. In recent years, there has been an improvement in tackling the issues of the 8 original scheme . Figure 4: The scheme of iCaddie
One of the variants of the classic ICMP traceback is However, while iTrace generates ICMP traceback iCaddie9. It has been designed by taking into message every 20,000 packets, iCaddie works account various properties: differently. In order to reduce the number of traceback messages produced, each router i. The cost and time required for upgrading maintains a timer that indicates how long it has not network equipment received a traceback message. If the amount ii. The extra traffic load due to out-of-band IP exceeds a specified threshold the router will start traceback techniques to act as Caddie initiator.
Page 4 Then, as routers act as Caddie propagators, they (IDIP) is handled by the network. Therefore, it uses append their IP address to the Router List (RL) less resources. along with the incoming interface and next hop information. This list is encrypted with a Message- IDIP is used to trace the real-time path and source 12 Authentication Hash function (HMAC) in order to of intrusion . IDIP systems are separated in IDIP prevent the RL elements from being modified. This communities. Each community contains its own function runs with the Time-Released Key Chain system of intrusion detection and the response is (TRKC)10. To generate a sequence of secret keys, managed by the Discovery Coordinator. Each each router successively applies the HMAC community is divided in neighbourhoods in such a function to a randomly selected seed, and then way that only one IDIP component belongs to each each router reveals the key after a delay at the end neighbourhood. This architecture allows the of each time interval. The destination of a Caddie collection of intrusion-related information at a message can retrieve the newest key, and then central site which enables the exchange of compute all the secret keys for previous time intrusion reports to have a better understanding of intervals to finally compute and verify the HMACs the situation. In each neighbourhood, a local IDS for every RL element in the Caddie message. agent watches and sends its report to a boundary controller. The benefit of this approach is that the number of trace packets produced is fewer. It is independent of the attack path and is solely dependent on the number of attack sources. The scheme produces fewer attack sources and false positives as the chances of two packets digest forwarded within a short gap of time is much smaller. More generally, the ICMP traceback scheme is really interesting as it can handle DDoS very well with fast recognition and requires low interoperability between ISPs as Caddie propagators transmit the Caddie packet like any other packet. However, it still requires more Figure 5: IDIP Community bandwidth than an in-band technique and the deployment cost is non-negligible. When an attack occurs, the detector node sends an attack report to its neighbours, which will help Reactive IDIP trace the attack path and also send the attack report along the attack path. But before sending it, Intrusion Detection System (IDS) can also be used they will decide how to respond to the attack by reactive attack defence methods. It will alert the (disabling the user account, installing filtering system in case of attack and this one will respond rules, etc.), depending on the type of attack and the with a traceback. The defence can be handled by response of other IDIP nodes. Then all the attack the network or by the host11. For instance, the reports are sent back to the Discovery Coordinator. Intrusion Detection and Identification Protocol This allows it to have an overview of the situation
Page 5 and modify local node decision if necessary. This The reactive IDS assisted approach: It requires a technique stops the diffusion of the attack and at significant amount of cooperation between ISP to the same time rebuild the attack path. perform the traceback. The reliability of this scheme is only up to the extent to which a router is The efficiency of IDIP is linked to the effectiveness secured to an attacker. of intrusion identification at different boundary controllers. Each controller needs to have the same SPIE intrusion detection capability as the IDS. The automated response allows the system to react iCaddie quickly. IDIP One of the main advantages of this technique is its Number of packets for tracing minimal dependence on the system infrastructure. This method can trace the connection that spoofed Many the source addresses. In fact, the IDIP protocol is based on what the components have recorded Many rather than network routing tables. The drawbacks are that it requires high ISP cooperation especially Few with the controller boundary and that it depends Incremental deployment on the reliability of the router. IDIP can successfully trace back the source unless it Yes encounters stepping stones – a sequence of intermediate hosts that help attacker remains Yes anonymous. Yes Comparative study DDoS handling Three main approaches have been studied: No The pro-active in-band technique: The traceback information is carried within the packet header. Yes Logging scheme like SPIE, can only trace packets Yes that have been delivered in the recent past as the packet digests are made to expire after a certain Scalability period of time. Bad The pro-active out-of-band technique: The trace information is sent within a separate packet. This High technique requires more network bandwidth in High delivering the trace information. Time required for traceback
Page 6 A few minutes Bandwidth usage
Quick Low
In real-time High
Number of false positives Low
Few Table 1 - Comparative tables of three IP traceback techniques Very few Conclusion Very few The objective of IP traceback is to determine the Memory requirements true source of DoS/DDoS attacks. IP traceback and attack detection form an efficient collaborative High defence against DoS attacks across the Internet. Depending on the company’s resources, there also High exist various pro-active techniques that all have Low evolved from basic scheme, such as IP marking, IP logging, ICMP-based traceback, overcoming the Misuse by the attacker shortcomings that the researchers had focused on. Some are more prone to one aspect of the network No attack than other. Hence network administrators No should take into consideration their business requirement and objective to implement the best No suited approach. However, it has been done at the lab scale but hasn't yet moved out into the field. Tracking until
Source
Source
Stepping stones
Computational overhead
High
Low
Low
Page 7 Page 8