Risk Scenario Development Template
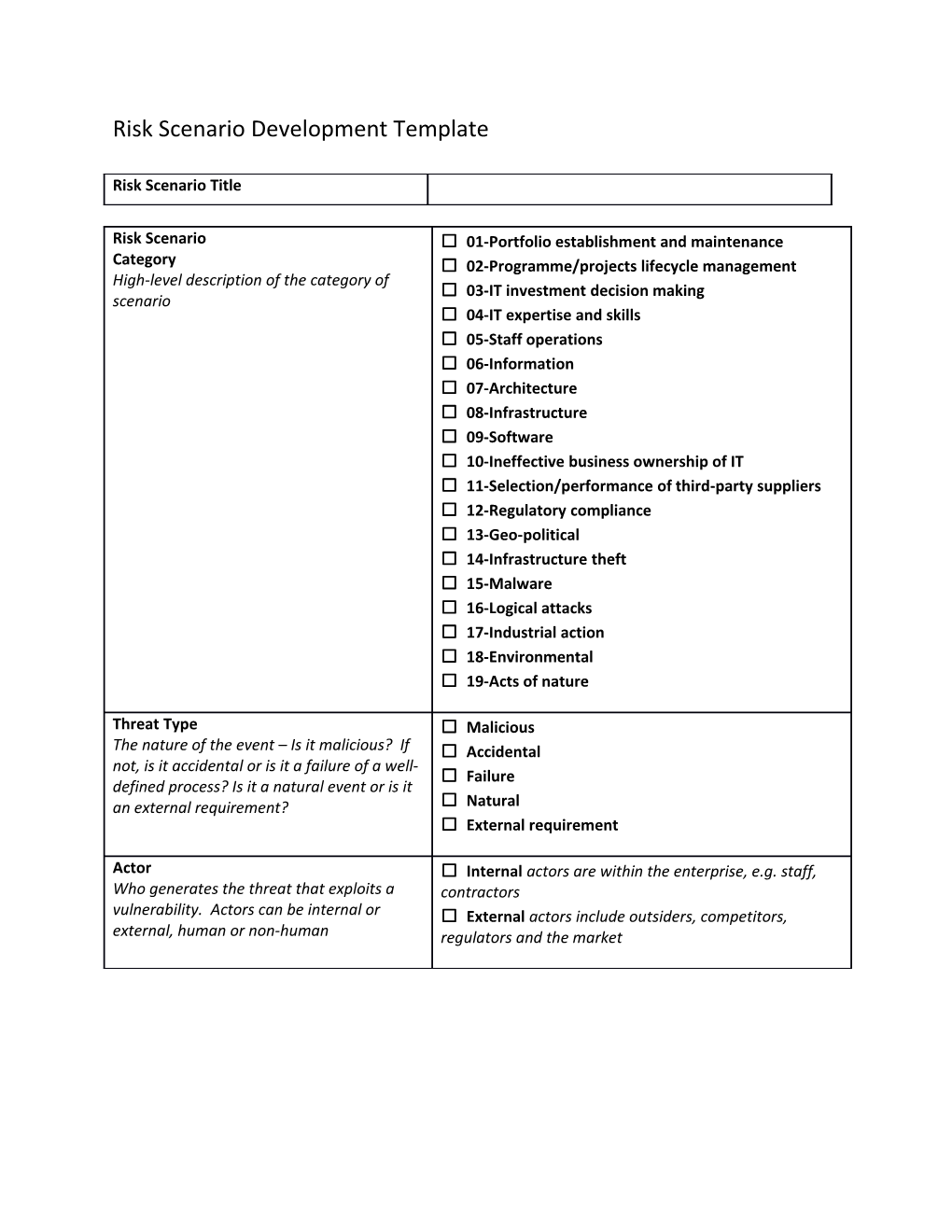
Risk Scenario Title
Risk Scenario ☐ 01-Portfolio establishment and maintenance Category ☐ 02-Programme/projects lifecycle management High-level description of the category of ☐ 03-IT investment decision making scenario ☐ 04-IT expertise and skills ☐ 05-Staff operations ☐ 06-Information ☐ 07-Architecture ☐ 08-Infrastructure ☐ 09-Software ☐ 10-Ineffective business ownership of IT ☐ 11-Selection/performance of third-party suppliers ☐ 12-Regulatory compliance ☐ 13-Geo-political ☐ 14-Infrastructure theft ☐ 15-Malware ☐ 16-Logical attacks ☐ 17-Industrial action ☐ 18-Environmental ☐ 19-Acts of nature
Threat Type ☐ Malicious The nature of the event – Is it malicious? If ☐ Accidental not, is it accidental or is it a failure of a well- ☐ Failure defined process? Is it a natural event or is it ☐ an external requirement? Natural ☐ External requirement
Actor ☐ Internal actors are within the enterprise, e.g. staff, Who generates the threat that exploits a contractors vulnerability. Actors can be internal or ☐ External actors include outsiders, competitors, external, human or non-human regulators and the market Event ☐ Disclosure Is it disclosure (of confidential information), ☐ Interruption interruption (of a system, of a project), theft ☐ Modification or destruction? Action also includes ☐ ineffective design (of systems, processes, Theft etc.), inappropriate use, changes in rules ☐ Destruction and regulation (that will materially impact a ☐ Ineffective design system) or ineffective execution of processes ☐ Ineffective execution (e.g. change management procedures, ☐ Rules and regulations acquisition procedures, project prioritisation ☐ Inappropriate use processes) Asset 1. Process, e.g. modelled as COBIT 5 processes, or An asset is any item of value to the business Processes enterprise that can be affected and lead to 2. People and organisation business impact (Assets and resources can 3. Physical Infrastructure (facilities, equipment etc.) be identical, e.g. IT hardware is an 4. IT Infrastructure (including computing hardware, important resource because all IT networks, middleware) applications use it, and at the same time, it 5. Information is an asset because it has a certain value to 6. Applications the enterprise). Resource 1. Process, e.g. modelled as COBIT 5 processes, or A resource is anything that helps to achieve business Processes goal (Assets and resources can be identical, 2. People and organisation e.g. IT hardware is an important resource 3. Physical Infrastructure (facilities, equipment etc.) because all IT applications use it, and at the 4. IT Infrastructure (including computing hardware, same time, it is an asset because it has a networks, middleware) certain value to the enterprise). 5. Information 6. Applications Time 7. Timing of occurrence (critical, non-critical – Does the event occur at a critical moment?) 8. Duration (extended – The duration of the event – e.g. extended outage of a service or data centre) 9. Detection (slow ,moderate, instant) 10. Time Lag (immediate, delayed – Lag between the event and the consequence – Is there an immediate consequence, e.g. Network failure, immediate downtime, or delayed consequence), e.g. wrong IT architecture with accumulated high costs, over a time span of several years?)
Risk scenario Describe the risk/opportunity scenario, including a discussion of the negative and positive impact of the scenario. The description will clarify the threat/vulnerability type and include the actors, events, assets, and time issues. Risk Type Describe the risk type, include whether the risk type is primary or secondary, i.e., a higher or lower degree of fit. Risk Types: IT Benefit/Value Enablement: Associated with [missed] opportunities to use technology to improve efficiency or effectiveness of business processes, or as an enabler for new business initiatives o Technology enabler for new business initiatives o Technology enabler for efficient operations IT Programme and Project Delivery: Associated with the contribution of IT to new or improved business solutions, usually in the form of projects and programmes as part of investment portfolios. o Project quality o Project relevance o Project overrun IT Operations and Service Delivery: Associated with all aspects of the business as usual performance of IT systems and services, which can bring destruction or reduction of value to the enterprise. o IT service interruptions o Security problems o Compliance issues
Risk Response
Describe how the enterprise will respond to the risk. The purpose of defining a risk response is to bring risk in line with the defined risk tolerance for the enterprise: Risk Acceptance Risk Sharing/Transfer Risk Mitigation Risk Avoidance
Risk Mitigation using COBIT 5 Enablers (see Appendix 4 – page 219 in Final Dev Draft C5 for Risk) Describe how the enterprise will work to avoid the risk from materializing. For Risk Mitigation possibilities use COBIT 5 Management Practices (Enablers). Please provide the following information: Reference, title and description of one or more concrete enablers that can help to mitigate the risk The estimated effect that implementing this enabler will have on the frequency and impact of the risk. Use either Low, Medium or High. Based on the two parameters frequency and impact give an indication whether this enabler is ‘essential’ (Key management practice to mitigate the risk) or not. An enabler is considered essential if it has a high effect on reducing either impact or frequency of the scenario.
Process Title Management Effect Effect Essential Referenc Practice On On e Frequency Impac t