Rusty Russell
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Filesystem Hierarchy Standard
Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Version 3.0 Publication date March 19, 2015 Copyright © 2015 The Linux Foundation Copyright © 1994-2004 Daniel Quinlan Copyright © 2001-2004 Paul 'Rusty' Russell Copyright © 2003-2004 Christopher Yeoh Abstract This standard consists of a set of requirements and guidelines for file and directory placement under UNIX-like operating systems. The guidelines are intended to support interoperability of applications, system administration tools, development tools, and scripts as well as greater uniformity of documentation for these systems. All trademarks and copyrights are owned by their owners, unless specifically noted otherwise. Use of a term in this document should not be regarded as affecting the validity of any trademark or service mark. Permission is granted to make and distribute verbatim copies of this standard provided the copyright and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this standard under the conditions for verbatim copying, provided also that the title page is labeled as modified including a reference to the original standard, provided that information on retrieving the original standard is included, and provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this standard into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the copyright holder. Dedication This release is dedicated to the memory of Christopher Yeoh, a long-time friend and colleague, and one of the original editors of the FHS. -

Communicating Between the Kernel and User-Space in Linux Using Netlink Sockets
SOFTWARE—PRACTICE AND EXPERIENCE Softw. Pract. Exper. 2010; 00:1–7 Prepared using speauth.cls [Version: 2002/09/23 v2.2] Communicating between the kernel and user-space in Linux using Netlink sockets Pablo Neira Ayuso∗,∗1, Rafael M. Gasca1 and Laurent Lefevre2 1 QUIVIR Research Group, Departament of Computer Languages and Systems, University of Seville, Spain. 2 RESO/LIP team, INRIA, University of Lyon, France. SUMMARY When developing Linux kernel features, it is a good practise to expose the necessary details to user-space to enable extensibility. This allows the development of new features and sophisticated configurations from user-space. Commonly, software developers have to face the task of looking for a good way to communicate between kernel and user-space in Linux. This tutorial introduces you to Netlink sockets, a flexible and extensible messaging system that provides communication between kernel and user-space. In this tutorial, we provide fundamental guidelines for practitioners who wish to develop Netlink-based interfaces. key words: kernel interfaces, netlink, linux 1. INTRODUCTION Portable open-source operating systems like Linux [1] provide a good environment to develop applications for the real-world since they can be used in very different platforms: from very small embedded devices, like smartphones and PDAs, to standalone computers and large scale clusters. Moreover, the availability of the source code also allows its study and modification, this renders Linux useful for both the industry and the academia. The core of Linux, like many modern operating systems, follows a monolithic † design for performance reasons. The main bricks that compose the operating system are implemented ∗Correspondence to: Pablo Neira Ayuso, ETS Ingenieria Informatica, Department of Computer Languages and Systems. -

Linux Kernel and Driver Development Training Slides
Linux Kernel and Driver Development Training Linux Kernel and Driver Development Training © Copyright 2004-2021, Bootlin. Creative Commons BY-SA 3.0 license. Latest update: October 9, 2021. Document updates and sources: https://bootlin.com/doc/training/linux-kernel Corrections, suggestions, contributions and translations are welcome! embedded Linux and kernel engineering Send them to [email protected] - Kernel, drivers and embedded Linux - Development, consulting, training and support - https://bootlin.com 1/470 Rights to copy © Copyright 2004-2021, Bootlin License: Creative Commons Attribution - Share Alike 3.0 https://creativecommons.org/licenses/by-sa/3.0/legalcode You are free: I to copy, distribute, display, and perform the work I to make derivative works I to make commercial use of the work Under the following conditions: I Attribution. You must give the original author credit. I Share Alike. If you alter, transform, or build upon this work, you may distribute the resulting work only under a license identical to this one. I For any reuse or distribution, you must make clear to others the license terms of this work. I Any of these conditions can be waived if you get permission from the copyright holder. Your fair use and other rights are in no way affected by the above. Document sources: https://github.com/bootlin/training-materials/ - Kernel, drivers and embedded Linux - Development, consulting, training and support - https://bootlin.com 2/470 Hyperlinks in the document There are many hyperlinks in the document I Regular hyperlinks: https://kernel.org/ I Kernel documentation links: dev-tools/kasan I Links to kernel source files and directories: drivers/input/ include/linux/fb.h I Links to the declarations, definitions and instances of kernel symbols (functions, types, data, structures): platform_get_irq() GFP_KERNEL struct file_operations - Kernel, drivers and embedded Linux - Development, consulting, training and support - https://bootlin.com 3/470 Company at a glance I Engineering company created in 2004, named ”Free Electrons” until Feb. -

Linux 2.5 Kernel Developers Summit
conference reports This issue’s reports are on the Linux 2.5 Linux 2.5 Kernel Developers Linux development, but I certainly Kernel Developers Summit Summit thought that, in all of this time, someone would have brought this group together OUR THANKS TO THE SUMMARIZER: SAN JOSE, CALIFORNIA before. Rik Farrow, with thanks to La Monte MARCH 30-31, 2001 Yarroll and Chris Mason for sharing their Summarized by Rik Farrow Another difference appeared when the notes. first session started on Friday morning. The purpose of this workshop was to The conference room was set up with cir- provide a forum for discussion of cular tables, each with power strips for changes to be made in the 2.5 release of For additional information on the Linux laptops, and only a few attendees were Linux (a trademark of Linus Torvalds). I not using a laptop. USENIX had pro- 2.5 Kernel Developers Summit, see the assume that many people reading this vided Aeronet wireless setup via the following sites: will be familiar with Linux, and I will hotel’s T1 link, and people were busy <http://lwn.net/2001/features/KernelSummit/> attempt to explain things that might be typing and compiling. Chris Mason of unfamiliar to others. That said, the odd- <http://cgi.zdnet.com/slink?91362:12284618> OSDN noticed that Dave Miller had numbered releases, like 2.3 and now 2.5, <http://www.osdn.com/conferences/kernel/> written a utility to modulate the speed of are development releases where the the CPU fans based upon the tempera- intent is to try out new features or make ture reading from his motherboard. -

Linux Kernel 8.1 Introduction
Page 1 of 6 Linux Kernel 8.1 Introduction: The Linux kernel is a Unix-like operating system kernel used by a variety of operating systems based on it, which are usually in the form of Linux distributions. The Linux kernel is a prominent example of free and open source software. The Linux kernel is released under the GNU General Public License version 2 (GPLv2) (plus some firmware images with various non-free licenses), and is developed by contributors worldwide. Day-to-day development discussions take place on the Linux kernel mailing list. The Linux kernel was initially conceived and created in 1991 by Finnish computer science student Linus Torvalds. Linux rapidly accumulated developers and users who adapted code from other free software projects for use with the new operating system. The Linux kernel has received contributions from thousands of programmers. 8.2 History: History In April 1991, Linus Torvalds, a 21-year-old student at the University of Helsinki, Finland started working on some simple ideas for an operating system. He started with a task switcher in Intel 80386 assembly language and a terminal driver. On 25 August 1991, Torvalds posted the following to comp.os.minix, a newsgroup on Usenet: I'm doing a (free) operating system (just a hobby, won't be big and professional like gnu) for 386(486) AT clones. This has been brewing since April, and is starting to get ready. I'd like any feedback on things people like/dislike in minix, as my OS resembles it somewhat (same physical layout of the file-system (due to practical reasons) among other things). -

Fuss, Futexes and Furwocks: Fast Userlevel Locking in Linux
Fuss, Futexes and Furwocks: Fast Userlevel Locking in Linux Hubertus Franke Rusty Russell IBM Thomas J. Watson Research Center IBM Linux Technology Center [email protected] [email protected] Matthew Kirkwood [email protected] Abstract makes it now feasible to deploy even more de- manding enterprise applications such as high Fast userlevel locking is an alternative locking end databases, business intelligence software mechanism to the typically heavy weight ker- and application servers. As a result, whole en- nel approaches such as fcntl locking and Sys- terprise business suites and middleware such 2 tem V semaphores. Here, multiple processes as SAP™, Websphere™, Oracle, DB2™ , etc., communicate locking state through shared are now available for Linux. memory regions and atomic operations. Ker- For these enterprise applications to run effi- nel involvement is only necessary when there ciently on Linux, or on any other operating is contention on a lock, in order to perform system for that matter, the OS must provide queueing and scheduling functions. In this pa- the proper abstractions and services. Enter- per we discuss the issues related to user level prise applications and applications suites are locking by following the history of ideas and increasingly built as multi process / multi- the code to the current day. We present the ef- threaded applications. Multi-threaded appli- ficacy of "futexes" through benchmarks, both cations can take better advantage of SMP synthetic and through adaptations to existing hardware, while multiple processes allows for databases. We conclude by presenting the po- higher degrees of fault tolerance, i.e., a single tential future directions of the "futex" inter- process abort does not necessarily bring the en- face. -

Community Notebook Kernel News Zack’S Kernel News
Community Notebook Kernel News Zack’s Kernel News Chronicler Zack Licensing Confusion performing source distribution, a complete An interesting little licensing escapade occurred machine-readable copy of the corresponding Brown reports on recently. Matthew Garrett noticed that CloudLi- source code, to be distributed under the the latest news, nux corporation had released their lve kernel terms of Sections 1 and 2 above on a medium driver under a new, proprietary license, whereas customarily used for software interchange.” views, dilemmas, before, it had been released under the GPL. So apparently, a written offer would be good Technically, nothing too fishy is going on here enough, and the three-week delay might be and developments because the original author of GPL’d code is still legally acceptable. within the Linux free to release that code under other licenses. But Matthew noticed that, in this particular Kernel Development kernel community. case, the driver still pretended to the kernel to Overflow be a GPL’d driver and still used kernel symbols Thomas Gleixner posed an interesting ques- By Zack Brown that were restricted to GPL-only code. tion – all the more interesting in that it was That’s a big no-no, and Matthew submitted taken so seriously. He pointed out that inter- a patch to make the kernel automatically treat est in the kernel was continuing to grow and the lve module as non-GPL, whether it said it that the number of patch submissions from was or not. But that wasn’t the end of the story individuals and corporations was growing as because licensing is a very touchy legal sub- well. -
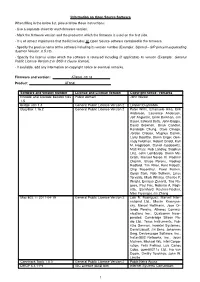
Information on Open Source Software When Filling in The
Information on Open Source Software When filling in the below list, please follow these instructions: - Use a separate sheet for each firmware version. - Mark the firmware version and the product in which the firmware is used on the first side. - It is of utmost importance that the list includes all Open Source software contained in the firmware. - Specify the precise name of the software including its version number (Example: Siproxd – SIP proxy/masquerading daemon Version: 0.5.10). - Specify the license under which the software is released including (if applicable) its version (Example: General Public License Version 2 or BSD-3 clause license). - If available, add any information on copyright notice or eventual remarks. Firmware and version: AT904L-03.18 Product: AT904L Software and version number License and License Version Copyright notice / remarks Encode and Decode base64 files Public domain John Walker 1.5 bridge-utils 1.4 General Public License Version 2 Lennert Buytenhek BusyBox 1.16.2 General Public License Version 2 Peter Willis, Emanuele Aina, Erik Andersen, Laurence Anderson, Jeff Angielski, Enrik Berkhan, Jim Bauer, Edward Betts, John Beppu, David Brownell, Brian Candler, Randolph Chung, Dave Cinege, Jordan Crouse, Magnus Damm, Larry Doolittle, Glenn Engel, Gen- nady Feldman, Robert Griebl, Karl M. Hegbloom, Daniel Jacobowitz, Matt Kraai, Rob Landley, Stephan Linz, John Lombardo, Glenn Mc- Grath, Manuel Novoa III, Vladimir Oleynik, Bruce Perens, Rodney Radford, Tim Riker, Kent Robotti, Chip Rosenthal, Pavel Roskin, Gyepi Sam, Rob Sullivan, Linus Torvalds, Mark Whitley, Charles P. Wright, Enrique Zanardi, Tito Ra- gusa, Paul Fox, Roberto A. Fogli- etta, Bernhard Reutner-Fischer, Mike Frysinger, Jie Zhang Mac 802.11 2011-04-19 General Public License Version 2 Luis R. -

Q8:BËJ B<IE<C E<NJ
GIF>I8DD@E> Kernel News Q8:BËJB<IE<CE<NJ KiXZb`e^B\ie\c ;lZb8e[:fm\i ?Xi[nXi\:fdgXk`Y`c`kp :feki`Ylk`fej Matt Mackall was a bit shaken to discover Adam Osuchowski was poking around in Wang Chen created a web page for kernel a kernel error message that began “Trea- the deep dark places of the kernel and contribution stats. The page breaks down son uncloaked!” The message went on to came upon some hard-coded assembly information by person and employer, as say that the TCP code had detected a bro- that used the xadd instruction. Because well as by change sets and number of ken peer. Matt thought the message was the 386 CPU didn’t implement an xadd lines of code affected. Also, it's possible alarming, so he posted a patch to change instruction, Adam asked whether Linux to search for a given person or employer it. Herbert Xu’s reply was, “What’s next, still supported the 386. The xadd in- and see a graph of only their contribu- you’re going to remove ‘printer on fire’ as struction turned out to be just a bug, but tions. According to Wang’s stats, for ex- well? This message has been there for the incident sparked a discussion about ample, Yahoo employees have contri- eons and is part of Linux lore.” But Alan which older systems were and were not buted much more to version 2.6.25 than Cox said, “It was changed. The printer on supported under Linux. -

Fall 2020 Vol
;login FALL 2020 VOL. 45, NO. 3 : & Guide to the Performance of Optane DRAM Jian Yang, Juno Kim, Morteza Hoseinzadeh, Joseph Izraelevitz, and Steven Swanson & Understanding Linux Superpages Weixi Zhu, Alan L. Cox, and Scott Rixner & Interview with Ion Stoica about Serverless Computing Rik Farrow & Measuring the Health of Open Source Projects Georg J.P. Link & Using OpenTrace to Track DB Performance Problems Anatoly Mikhaylov Columns SRE and Justice Laura Nolan Socially Distant Projects Cory Lueninghoener Communicating with BPF Dave Josephsen Hand-Over-Hand Locking for Highly Concurrent Collections Terence Kelly Everything Is a Punch Card Simson L. Garfinkel Thanks to our USENIX Supporters! USENIX appreciates the financial assistance our Supporters provide to subsidize our day-to-day operations and to continue our non-profit mission. Our supporters help ensure: • Free and open access to technical information • Student Grants and Diversity Grants to participate in USENIX conferences • The nexus between academic research and industry practice • Diversity and representation in the technical workplace We need you now more than ever! Contact us at [email protected]. USENIX PATRONS USENIX BENEFACTORS We offer our heartfelt appreciation to the following sponsors and champions of conference diversity, open access, and our SREcon communities via their sponsorship of multiple conferences: Ethyca Dropbox Microsoft Azure Packet Datadog Goldman Sachs LinkedIn Salesforce More information at www.usenix.org/supporters FALL 2020 VOL. 45, NO. 3 EDITOR EDITORIAL Rik Farrow 2 Musings Rik Farrow MANAGING EDITOR Michele Nelson SYSTEMS COPY EDITORS 6 An Empirical Guide to the Behavior and Use of Scalable Steve Gilmartin Persistent Memory Jian Yang, Juno Kim, Morteza Hoseinzadeh, Amber Ankerholz Joseph Izraelevitz, and Steven Swanson PRODUCTION 12 How to Not Copy Files Yang Zhan, Alex Conway, Nirjhar Mukherjee, Arnold Gatilao Ian Groombridge, Martín Farach-Colton, Rob Johnson, Yizheng Jiao, Ann Heron Michael A. -

(C) 1995 Microsoft Corporation. All Rights Reserved
(c) 1995 Microsoft Corporation. All rights reserved. Developed by ActiveWare Internet Corp., http://www.ActiveWare.com (C) 2000-2002 by the netfilter coreteam <[email protected]>: Paul 'Rusty' Russell <[email protected]> Marc Boucher <[email protected]> James Morris <[email protected]> Harald Welte <[email protected]> Jozsef Kadlecsik <[email protected]> (c) 2002-2008 Erik de Castro Lopo" ; src_get_version */ (c) 2003, 2004 Phil Blundell <[email protected]> (c) 2004 Mihnea Stoenescu, under the same license: (c) 2009-2013 Zoltan Herczeg All rights reserved. (C) 2016 Panasonic System Networks Co., Ltd. (c) allow anyone who receives a copy of the Modified Version to make the Source form of the Modified Version available to others under (c) allow anyone who receives a copy of the Modified Version to make the Source form of the Modified Version available to others under i) the Original License or ii) a license that permits the licensee to freely copy, modify and redistribute the Modified Version using the same licensing terms that apply to the copy that the licensee received, and requires that the Source form of the Modified Version, and of any works derived from it, be made freely available in that license fees are prohibited but Distributor Fees are allowed. Distribution of Compiled Forms of the Standard Version or Modified Versions without the Source (c) any litigation relating to this Agreement shall be subject to the jurisdiction of the Federal Courts of the Northern District of California, with venue lying in Santa Clara County, California, with the losing party responsible for costs, including without limitation, court costs and reasonable attorneys fees and expenses. -

Fault Injection Test Harness a Tool for Validating Driver Robustness
Fault Injection Test Harness a tool for validating driver robustness Louis Zhuang Stanley Wang Intel Corp. Intel Corp. [email protected], [email protected] [email protected] Kevin Gao Intel Corp. [email protected] Abstract 1 Introduction FITH (Fault Injection Test Harness) is a tool High-availability (HA) systems must respond for validating driver robustness. Without gracefully to fault conditions and remain oper- changing existing code, it can intercept arbi- ational during unexpected software and hard- trary MMIO/PIO access and IRQ handler in ware failures. Each layer of the software stack driver. of a HA system must be fault tolerant, produc- ing acceptable output or results when encoun- Firstly I’ll first list the requirements and design tering system, software or hardware faults, in- for Fault Injection. Next, we discuss a cou- cluding faults that theoretically should not oc- ple of new generally useful implementation in cur. An empirical study [2] shows that 60- FITH 70% of kernel space defects can be attributed to device driver software. Some defect con- 1. KMMIO - the ability to dynamically hook ditions (such as hardware failure, system re- into arbitrary MMIO operations. source shortages, and so forth) seldom hap- pen, however, it is difficult to simulate and reproduce without special assistant hardware, 2. KIRQ - the ability to hook into an arbi- such as an In-Circuit Emulator. In these situa- trary IRQ handler, tions, it is difficult to predict what would hap- pen should such a fault occur at some time in the future. Consequently, device drivers that Then I’ll demonstrate how the FITH can help are highly available or hardened are designed developers to trace and identify tricky issues to minimize the impact of failures to a system’s in their driver.