Google Cloud Platform Roles and Permissions Avi Networks — Technical Reference (18.1)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

A Visualization on What's Changing Google Accounts Help
Google Accounts Help About the conversion: A visualization on what's changing Google offers different types of accounts to different types of users. Until recently, we offered two primary types of accounts that were completely separate services: Google Accounts Provide access to all Google products and services, such as Gmail, Blogger, Orkut, and Web History. Can be created with any email address, such as the email address you have with your organization, or with any webmail address (@yahoo.com, @hotmail.com, etc.). Signing up for Gmail automatically creates a Google Account with that address. Google Apps Accounts Issued and managed by and used with your @my-domain.com organization. Provide access to only Gmail, Calendar, Docs, Sites, Groups, and Video. Before the transition Google Accounts Google Apps accounts Example accounts: [email protected] Example accounts: [email protected] [email protected] [email protected] [email protected] Sample of products on Google Accounts: Only 6 products on Google Apps accounts: However, we recently transitioned Google Apps accounts so you can use your @my-domain.com address to access the same Google products and services that Google Accounts holders can. Your Google Apps Account is now a Google Account. Conflicting accounts If you've used other Google products outside of the ones you can access with your Google Apps account such as Picasa, Reader, or AdWords, you've already created a conflicting Google Account. If you used your Google Apps email address to sign up for and use those other Google services, you now have two Google Accounts, with the same address. -
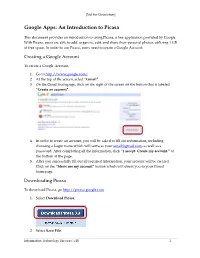
Google Apps: an Introduction to Picasa
[Not for Circulation] Google Apps: An Introduction to Picasa This document provides an introduction to using Picasa, a free application provided by Google. With Picasa, users are able to add, organize, edit, and share their personal photos, utilizing 1 GB of free space. In order to use Picasa, users need to create a Google Account. Creating a Google Account To create a Google Account, 1. Go to http://www.google.com/. 2. At the top of the screen, select “Gmail”. 3. On the Gmail homepage, click on the right of the screen on the button that is labeled “Create an account”. 4. In order to create an account, you will be asked to fill out information, including choosing a Login name which will serve as your [email protected], as well as a password. After completing all the information, click “I accept. Create my account.” at the bottom of the page. 5. After you successfully fill out all required information, your account will be created. Click on the “Show me my account” button which will direct you to your Gmail homepage. Downloading Picasa To download Picasa, go http://picasa.google.com. 1. Select Download Picasa. 2. Select Save File. Information Technology Services, UIS 1 [Not for Circulation] 3. Click on the downloaded file, and select Run. 4. Follow the installation procedures to complete the installation of Picasa on your computer. When finished, you will be directed to a new screen. Click Get Started with Picasa Web Albums. Importing Pictures Photos can be uploaded into Picasa a variety of ways, all of them very simple to use. -

Getting Started with Google Cloud Platform
Harvard AP275 Computational Design of Materials Spring 2018 Boris Kozinsky Getting started with Google Cloud Platform A virtual machine image containing Python3 and compiled LAMMPS and Quantum Espresso codes are available for our course on the Google Cloud Platform (GCP). Below are instructions on how to get access and start using these resources. Request a coupon code: Google has generously granted a number of free credits for using GCP Compute Engines. Here is the URL you will need to access in order to request a Google Cloud Platform coupon. You will be asked to provide your school email address and name. An email will be sent to you to confirm these details before a coupon code is sent to you. Student Coupon Retrieval Link • You will be asked for a name and email address, which needs to match the domain (@harvard.edu or @mit.edu). A confirmation email will be sent to you with a coupon code. • You can only request ONE code per unique email address. If you run out of computational resources, Google will grant more coupons! If you don’t have a Gmail account, please get one. Harvard is a subscriber to G Suite, so access should work with your @g.harvard.edu email and these were added already to the GCP project. If you prefer to use your personal Gmail login, send it to me. Once you have your google account, you can log in and go to the website below to redeem the coupon. This will allow you to set up your GCP billing account. -

Digital Media Asset Management and Sharing
Digital Media Asset Management and Sharing Introduction Digital media is one of the fastest growing areas on the internet. According to a market study by Informa Telecoms & Media conducted in 2012, the global 1. online video market only, will reach $37 billion in 2017¹. Other common media OTT Video Revenue Forecasts, types include images, music, and digital documents. One driving force for this 2011-2017, by Informa Telecoms phenomena growth is the popularity of feature rich mobile devices2, equipped & Media, with higher resolution cameras, bigger screens, and faster data connections. November 2012. This has led to a massive increase in media content production and con- sumption. Another driving force is the trend among many social networks to 2. incorporate media sharing as a core feature in their systems². Meanwhile, Key trends and Takeaways in Digital numerous startup companies are trying to build their own niche areas in Media Market, this market. by Abhay Paliwal, March 2012. This paper will use an example scenario to provide a technical deep-dive on how to use Google Cloud Platform to build a digital media asset management and sharing system. Example Scenario - Photofeed Photofeed, a fictitious start-up company, is interested in building a photo sharing application that allows users to upload and share photos with each other. This application also includes a social aspect and allows people to post comments about photos. Photofeed’s product team believes that in order for them to be competitive in this space, users must be able to upload, view, and edit photos quickly, securely and with great user experiences. -

Jon Leibowitz, Chairman J. Thomas Rosch Edith Ramirez Julie Brill
102 3136 UNITED STATES OF AMERICA FEDERAL TRADE COMMISSION COMMISSIONERS: Jon Leibowitz, Chairman J. Thomas Rosch Edith Ramirez Julie Brill ____________________________________ ) In the Matter of ) ) GOOGLE INC., ) a corporation. ) DOCKET NO. C-4336 ____________________________________) COMPLAINT The Federal Trade Commission, having reason to believe that Google Inc. (“Google” or “respondent”), a corporation, has violated the Federal Trade Commission Act (“FTC Act”), and it appearing to the Commission that this proceeding is in the public interest, alleges: 1. Respondent Google is a Delaware corporation with its principal office or place of business at 1600 Amphitheatre Parkway, Mountain View, CA 94043. 2. The acts and practices of respondent as alleged in this complaint have been in or affecting commerce, as “commerce” is defined in Section 4 of the FTC Act. RESPONDENT’S BUSINESS PRACTICES 3. Google is a technology company best known for its web-based search engine, which provides free search results to consumers. Google also provides various free web products to consumers, including its widely used web-based email service, Gmail, which has been available since April 2004. Among other things, Gmail allows consumers to send and receive emails, chat with other users through Google’s instant messaging service, Google Chat, and store email messages, contact lists, and other information on Google’s servers. 4. Google’s free web products for consumers also include: Google Reader, which allows users to subscribe to, read, and share content online; Picasa, which allows users to edit, post, and share digital photos; and Blogger, Google’s weblog publishing tool that allows users to share text, photos, and video. -
Moto G User Guide.Pdf
Moto G pick a topic, get what you need At a glance Start Home screen & apps Control & customize Calls Contacts Messages Email Type Socialize Browse Photos & videos Music Books Games Locate & navigate Work Connect & transfer PPtrotect Want more? Troubleshoot Safety Hot topics Search topics At a glance a quick look At a glance First look Tips & tricks First look •Start: Back cover off, SIM in, charge up, and sign in. Top topics Your new Moto G has pretty much everything— camera, Internet, email, and more. You can even change the back cover See “Start”. for a new look with optional covers. •Top topics: Just want a quick list of what your phone can Note: Your phone may look a little different. do? See “Top topics”. • Help: All your questions about your new phone answered right on your phone. Touch Apps > Moto Care. Want even more? See “Get help”. Note: Certain apps and features may not be available in all countries. This product meets the applicable national or international RF exposure guidance (SAR guideline) 3.5mm when used normally against your head or, when worn Headset Jack Front Camera or carried, at a distance of 1.5 cm from the body. The SAR 4:00 Back Camera guideline includes a considerable safety margin designed to micro SIM (on back) assure the safety of all persons, regardless of age and health. (under back cover) Power Key 4:00 Press = Screen WED, DECEMBER 18 On/Off Hold = Phone On/Off Back Volume Keys Home Recent GoogleGoogle Play Store Apps Menu More Micro USB/ Microphone Charger Back Next At a glance At a glance Top topics Tips & tricks First look •Intuitive: To get started quickly, touch Apps > Top topics Check out what your phone can do. -

Unlimited Free Calling with Google Voice
Unlimited Free Calling with Google Voice 1. Unlimited Free Calling with Google Voice ............................................ 0 1. Introduction ................................................................................... 1 2. Free Calling from a Landline ............................................................. 1 3. Free Calling from a Cellphone (using the Voice plan) ........................... 2 4. Free Calling with Voice Over IP (VOIP) - Introduction........................... 6 5. The Gizmo5 Project - Background ..................................................... 6 6. Google Voice Integration with Gizmo5 ............................................... 7 7. Gizmo5 Integration with SIP Sorcery ................................................. 7 8. SIP Sorcery Integration with sipgate ................................................. 8 9. SIP Sorcery Scripting ...................................................................... 9 10. Unified Dial Plan ........................................................................... 9 11. Customizing the SIP Sorcery Unified Dialplan ...................................15 12. Connecting other SIP Clients and Devices........................................16 13. Configuring and Testing your SIP Calling Chain ................................21 14. Additional setup screenshots .........................................................28 15. Revision History...........................................................................29 1. Introduction Google Voice is a free service -

Moto G7 Power User Guide
User Guide Drive Contents Music, movies, TV & YouTube Check it out Check it out Clock When you’re up and running, explore what your phone can do. Get Started Connect, share & sync First look Connect with Wi-Fi Topic Location Insert the SIM and microSD cards Connect with Bluetooth wireless Charge up & power on Share files with your computer Find these fast: Wi-Fi, airplane mode, Quick settings Sign in Share your data connection flashlight, and more. Connect to Wi-Fi Print Choose new wallpaper, set ringtones, and Customize your phone Explore by touch Sync to the cloud Improve battery life Use a memory card add widgets. Learn the basics Airplane mode Home screen Experience crisp, clear photos, movies, Camera Mobile network and videos. Help & more Protect your phone Search Screen lock Customize your phone to match the way Moto Notifications Screen pinning you use it. App notifications Backup & restore Status icons Encrypt your phone Browse, shop, and download apps. Apps Volume Your privacy Keep your info safe. Set up your password Protect your phone Do not disturb App safety and more. Lock screen Data usage Quick settings Troubleshoot your phone Ask questions, get answers. Speak Speak Restart or remove an app Direct Share Restart your phone Share your Internet connection. Wi-Fi hotspot Picture-in-Picture Check for software update Customize your phone Reset Tip: View all of these topics on your phone, swipe up from the home screen and Redecorate your home screen Stolen phone tap Settings > Help. For FAQs, and other phone support, visit www.motorola.com/ Choose apps & widgets Accessibility support. -

Platform Competition in an Age of Machine Learning
DISRUPTIVE INCUMBENTS: PLATFORM COMPETITION IN AN AGE OF MACHINE LEARNING C. Scott Hemphill * Recent advances in machine learning have reinforced the competi- tive position of leading online platforms. This Essay identifies two im- portant sources of platform rivalry and proposes ways to maximize their competitive potential under existing antitrust law. A nascent competitor is a threatening new entrant that, in time, might become a full-fledged platform rival. A platform’s acquisition of a nascent competitor should be prohibited as an unlawful acquisition or maintenance of monopoly. A disruptive incumbent is an established firm—often another plat- form—that introduces fresh competition in an adjacent market. Anti- trust enforcers should take a more cautious approach, on the margin, when evaluating actions taken by a disruptive incumbent to compete with an entrenched platform. INTRODUCTION The leading online platforms—Google in search, Facebook in social network services, and Amazon in e-commerce—benefit from economies of scale and access to user data that are difficult for rivals to replicate. These barriers are reinforced by advances in machine learning, a set of artificial intelligence (AI) techniques1 that use models to “learn” desired behavior from “examples rather than instructions.”2 This Essay considers how competition might be enhanced, notwithstanding these advantages, under existing antitrust law.3 * Moses H. Grossman Professor of Law, New York University School of Law. I thank John Asker, Adam Cox, Harry First, Jacob Gersen, Jeannie Gersen, Bert Huang, Avery Katz, Benedict Kingsbury, Bhaven Sampat, Tim Wu, and audiences at Columbia, ETH Zurich, and NYU, for helpful comments. Tim Keegan, Ryan Knox, Ina Kosova, Alison Perry, and David Stein provided outstanding research assistance. -

Annual Report for 2005
In October 2005, Google piloted the Doodle 4 Google competition to help celebrate the opening of our new Googleplex offi ce in London. Students from local London schools competed, and eleven year-old Lisa Wainaina created the winning design. Lisa’s doodle was hosted on the Google UK homepage for 24 hours, seen by millions of people – including her very proud parents, classmates, and teachers. The back cover of this Annual Report displays the ten Doodle 4 Google fi nalists’ designs. SITTING HERE TODAY, I cannot believe that a year has passed since Sergey last wrote to you. Our pace of change and growth has been remarkable. All of us at Google feel fortunate to be part of a phenomenon that continues to rapidly expand throughout the world. We work hard to use this amazing expansion and attention to do good and expand our business as best we can. We remain an unconventional company. We are dedicated to serving our users with the best possible experience. And launching products early — involving users with “Labs” or “beta” versions — keeps us efficient at innovating. We manage Google with a long-term focus. We’re convinced that this is the best way to run our business. We’ve been consistent in this approach. We devote extraordinary resources to finding the smartest, most creative people we can and offering them the tools they need to change the world. Googlers know they are expected to invest time and energy on risky projects that create new opportunities to serve users and build new markets. Our mission remains central to our culture. -

Google Cheat Sheet
Google Cheat Sheet Cool web tools and services offered by (and about) Google. Compiled by James Spellos President, Meeting U. [email protected] http://www.meeting-u.com last updated: March 3, 2010 GOOGLE and related products referenced herein are trademarks of Google, Inc. and are used for identification purposes only. Their use does not represent any approval or recommendation by the trademark owner. www.meeting-u.com..... [email protected] Page 1 of 18 Table of Contents Topic Page Description Google Pages 3 Google advanced functions, accessed beyond the main search page Even Cooler 9 How to use Google search box more Tools efficiently Google 13 Services Google has purchased and re- Purchases branded Google 15 Tools to help with search engine Business optimization and enterprise-wide solutions Google Blogs 16 Official & unofficial blogs relating to Google Google Hacks 16 Services provided outside of Google & Mash-Ups that enhance Google tools Customizing 18 Step by step instructions to track and News Feed in follow Google News stories. iGoogle www.meeting-u.com..... [email protected] Page 2 of 18 Google Pages - Many of the advanced functions of Google are accessible through their main page, others aren‟t. Here is a list of Google functionality, along with a brief description, as well as the URL that will enable you to find those pages. A number of these URL‟s are redirects (bringing you to the proper page, but using an alternate URL). The URL‟s used here are the most common & easiest to enter. Service URL Details Google Alerts™ http://www.google.com/alerts By entering keywords, the user can be alerted when there are new Google search results using those terms. -
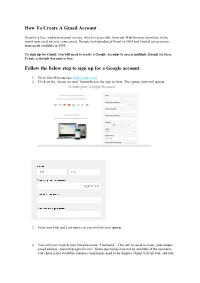
How-To-Create-A-Gmail-Account.Pdf
How To Create A Gmail Account Gmail is a free, web-based email service, which is accessible from any Web browser anywhere in the world (just need internet connection). Google first introduced Gmail in 2004 and limited test accounts were made available in 2005. To sign up for Gmail, you will need to create a Google Account to access multiple Google services. Create a Google Account is free. Follow the below step to sign up for a Google account. 1. Go to Gmail homepage: mail.google.com. 2. Click on the “create account” button below the sign in form. The signup form will appear. 3. Enter you First and Last names as you wish them to appear 4. You will have to pick your Gmail account “Username”. This will be used to create your unique email address “[email protected]”. Some usernames may not be available if the username you chose is not available anymore (usernames need to be unique), Gmail will tell you, and you will have to choose a different Gmail account name; Google will also suggest you available name. If you find out that the User name you wanted is taken try using your name with or without a full stop between your first and last name ie [email protected] you could also try using your trust name as part of the address Ie [email protected] 5. Choose your password: Keep your account secure. Try to choose an unforgettable, but a secure password. Google may explain that you should try one with at least eight characters long to be secure.