Cross Tier Framework for Rapid Web Application Development
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Php: Variabile
Service Oriented Architectures / busaco ~ / programare Web ____ _ _ ____ profs.info.uaic.ro ( _ \( )_( )( _ \ )___/ ) _ ( )___/ (__) (_) (_)(__) Dr. Sabin Sabin Buraga Dr. dezvoltarea aplicațiilor Web în PHP / busaco ~ „E mediocru ucenicul / care nu-și depășește maestrul.” profs.info.uaic.ro Leonardo da Vinci Dr. Sabin Sabin Buraga Dr. Personal Home Page Tools (1995) Rasmus Lerdorf / PHP 3 (1998) busaco ~ dezvoltat de Zend – Zeev Suraski & Andi Gutmans / PHP 4 (2000) suport pentru programare obiectuală profs.info.uaic.ro PHP 5 (2004) – varianta cea mai recentă: PHP 5.6 (2014) noi facilități inspirate de Java PHP 6 (actualmente abandonat) Dr. Sabin Sabin Buraga Dr. phpngPHP 7 (2015), PHP 7.1 (la final de 2016) strong typing, suport pentru Unicode, performanță,… php: caracterizare / busaco ~ Server de aplicații Web / oferă un limbaj de programare profs.info.uaic.ro de tip script, interpretat poate fi inclus direct și în cadrul documentelor HTML Dr. Sabin Sabin Buraga Dr. php: caracterizare / busaco ~ Limbajul PHP este procedural, oferind suport și / pentru alte paradigme de programare (obiectuală și, mai recent, funcțională) profs.info.uaic.ro Dr. Sabin Sabin Buraga Dr. php: caracterizare / busaco ~ Limbajul PHP este procedural, oferind suport și / pentru alte paradigme de programare (obiectuală și, mai recent, funcțională) profs.info.uaic.ro poate fi folosit și ca limbaj de uz general Dr. Sabin Sabin Buraga Dr. php: caracterizare / busaco ~ Sintaxă inspirată de C, Perl și Java – case sensitive / uzual, programele PHP au extensia .php profs.info.uaic.ro Dr. Sabin Sabin Buraga Dr. php: caracterizare / busaco ~ / Disponibil gratuit – open source – pentru diverse platforme (Linux, Windows, macOS, UNIX) profs.info.uaic.ro și servere Web: Apache, IIS, nginx,… www.php.net Sabin Buraga Dr. -

Gabor De Mooij Freelance Software Developer (PHP, Javascript, Python and C)
Contact [email protected] Gabor de Mooij Freelance Software Developer (PHP, JavaScript, Python and C). www.linkedin.com/in/gabor-de- The Hague Area, Netherlands mooij-8164593 (LinkedIn) www.redbeanphp.com (Personal) Summary Top Skills Freelance software developer focusing on PHP, Python, JavaScript PHP and C. JavaScript Git Experience Languages Dutch (Native or Bilingual) Gabor Software English (Full Professional) C Developer and Owner September 2016 - Present The Hague Certifications I am currently working as a freelance (web)application developer under the Zend Certified Engineer PHP 5.3 name Gabor Software. My main focus is to help organizations to refactor their Zend Certified Engineer PHP 4 applications to make them less complex and easier to maintain. I also build MySQL Core Certified Engineer new software with simplicity in mind. As part of my own company I create my ECE JAVA Engineer own programming language: The Citrine Programming Language (written in Publications C). Escape from systemd Royal Schiphol Group Python Lead Developer (freelance) June 2017 - October 2018 (1 year 5 months) Amsterdam Area, Netherlands Lead Developer Wayfinding APIs. Created a Python-based API for indoor navigation. The API can be consumed by websites and applications to guide passengers from home to gate (including all possible challenges in between like checking in luggage, finding an applicable security filter and, of course, finding the right gate). LeasePlan Java Developer (freelance) January 2017 - April 2017 (4 months) Almere Stad Area, Netherlands Interim developer. Helped to finish the Private Lease Platform before deadline. While I started as an AngularJS frontend engineer, they quickly discovered I also have experience with Java/Spring so I did a little of both. -

Laravel. Tworzenie Aplikacji. Receptury
Tytuł oryginału: Laravel Application Development Cookbook Tłumaczenie: Mirosław Gołda ISBN: 978-83-283-0302-7 Copyright © Packt Publishing 2013. First published in the English language under the title: „Laravel Application Development Cookbook”. Polish edition copyright © 2015 by Helion S.A. All rights reserved. All rights reserved. No part of this book may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording or by any information storage retrieval system, without permission from the Publisher. Wszelkie prawa zastrzeżone. Nieautoryzowane rozpowszechnianie całości lub fragmentu niniejszej publikacji w jakiejkolwiek postaci jest zabronione. Wykonywanie kopii metodą kserograficzną, fotograficzną, a także kopiowanie książki na nośniku filmowym, magnetycznym lub innym powoduje naruszenie praw autorskich niniejszej publikacji. Wszystkie znaki występujące w tekście są zastrzeżonymi znakami firmowymi bądź towarowymi ich właścicieli. Autor oraz Wydawnictwo HELION dołożyli wszelkich starań, by zawarte w tej książce informacje były kompletne i rzetelne. Nie biorą jednak żadnej odpowiedzialności ani za ich wykorzystanie, ani za związane z tym ewentualne naruszenie praw patentowych lub autorskich. Autor oraz Wydawnictwo HELION nie ponoszą również żadnej odpowiedzialności za ewentualne szkody wynikłe z wykorzystania informacji zawartych w książce. Wydawnictwo HELION ul. Kościuszki 1c, 44-100 GLIWICE tel. 32 231 22 19, 32 230 98 63 e-mail: [email protected] WWW: http://helion.pl (księgarnia internetowa, katalog książek) Drogi Czytelniku! Jeżeli chcesz ocenić tę książkę, zajrzyj pod adres http://helion.pl/user/opinie/larare Możesz tam wpisać swoje uwagi, spostrzeżenia, recenzję. Printed in Poland. • Kup książkę • Księgarnia internetowa • Poleć książkę • Lubię to! » Nasza społeczność • Oceń książkę Spis treĂci O autorze 7 O recenzentach 8 WstÚp 9 Rozdziaï 1. -
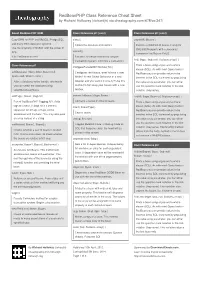
Redbeanphp Class Reference Cheat Sheet by Richardjh
RedBeanPHP Class Reference Cheat Sheet by Richard Holloway (richardjh) via cheatography.com/478/cs/347/ About RedBeanPHP ORM Class Reference pt1 (cont) Class Reference pt1 (cont) Easy ORM for PHP and MySQL, PostgreSQL close() exportAll( $beans ) and many other database systems. Closes the database connect ion. Exports a collection of beans. Handy for Use the simplicity of NoSQL with the power of XML/JSON exports with a Javascript SQL. commit() framework like Dojo or ExtJS. http:// red bea nph p.com/ Facade Convience method for adapter transac tion system. Commits a transac tion. find( $type, $sql=null, $values=array() ) Class Reference pt1 Finds a bean using a type and a where configu reF aca deW ith Too lbox( $tb ) clause (SQL). As with most Query tools in addData base ( $key, $dsn, $user=n ull, Configures the facade, want to have a new RedBean you can provide values to be $pass=n ull, $frozen =false ) Writer? A new Object Database or a new inserted in the SQL statement by populating Adds a database to the facade, afterwards Adapter and you want it on-the- fly? Use this the value array parameter; you can either you can select the database using method to hot-swap your facade with a new use the question mark notation or the slot- selectD ata bas e($ key). toolbox. no tation (:keyna me). addTags ( $bean, $tagList ) convert ToB eans( $type, $rows ) findAll( $type, $sql=null, $values =ar ray() ) Part of RedBeanPHP Tagging API. Adds Converts a series of rows to beans. Finds a bean using a type and a where tags to a bean. -

Zašto Smo Odabrali Laravel (4)?
Zašto smo odabrali Laravel (4)? Denis Stančer Prije framework-a • Razvijate web aplikacije od ranih početaka (kraj XX stoljeća) • Perl – CGI • PHP (3.0 - 6/1998, 4.0 - 5/2000, 5.0 - 7/2004, 5.3 - 6/2009 ) • Tijekom vremena sami razvijete elemente frameworka • Prednosti: • Brži razvoj • Neka vrsta standarda • Nedostaci: • Još uvijek velika količina spaghetti kôda • Pojedini developer ima svoj framework • Ne razvijaju se svi jednako brzo • Nama pravovremenih sigurnosnih zakrpi U Srcu • Koji PHP framework koristite ili ste koristili? Zašto framework? • Brži razvoj • Standardizirana organizacija kôda • Pojednostavljeno • Pristupu bazi/bazama • Zaštita od osnovnih sigurnosnih propusta • Modularnost • Razmjena gotovih rješenja među developerima • Copy/paste ili Composer • U MVC framework-u razdvojen HTML/JS od PHP-a • U konačnici - bolja suradnja unutar tima = efikasniji razvoj i održavanje MVC – Model-View-Controller • Programski predložak kojim se komunikacija s korisnikom dijeli na tri dijela: • data model: podaci • najčešće baza • user interface: prikaz stanja u modelu • najčešće templating engine • bussines model: šalje naredbe modelu Koji framework odabrati? • Koji su najpopularniji? • Koji imaju mogućnosti koje nama trebaju? • Popis općih kriterija • Composer • ORM • Testna okruženja • Migracije i seeding • Templating engine • Bootstrap • Git • Kvaliteta dokumentacije • Stanje zajednice: forumi, članci, konferencije,… Koji framework odabrati? (2) • Popis specifičnih kriterija • Mali (rijetko srednje veliki) projekti • simpleSAMLphp: jednostavno -

Object Relational Mapping in PHP5
! § ! Bachelor thesis Object Relational Mapping in PHP5 ! Author: Michelle Sanver Supervisor: Martin Blomberg Semester: Spring 2011 Course code: 2DV40E Acknowledgements Many thanks to Matthew Weier O'Phinney and Ryan Mauger for taking the time to participate in interviews and sharing information very valuable to this thesis. I would also like to thank my classmates Martin Lindberg, Tobias Åström, Fredrik Johansson and Dennis Sangmo at Linnaeus University who have given their constant support. Abstract Using an object relational mapper, ORM, is a good idea if you have an object relational code base and are following standards. By using an ORM you get a separation between actual objects and data persistence. This also makes it possible for the programmer to fully focus on the application without knowing much about how the database itself works. However, this doesn’t come without drawbacks. Depending what ORM you use and how you use it, it may sacrifice performance. The research in this thesis shows that using an ORM in a very small application does not sacrifice performance. Sammanfattning Det är en bra idé att använda en “Object relational mapper, ORM” om du har en objektorienterad kodbas och följer standarder och objektorienterade regler. Genom att använda en ORM separerar du objekten och hur de förvaras för att enkelt kunna refaktorera i ett senare stadie. Det medför också att programmeraren kan fokusera på sitt uppdrag, applikationen och behöver inte veta något om databaser. Men, detta kommer inte utan nackdelar. Beroende på vilket ORM system du använder och hur du använder det kan det påverka prestandan. Forskningen i den här rapporten pekar på att när man använder en ORM i en väldigt liten applikation berörs inte prestandan. -

Rene López Flores Doctorado En Ingeniería Industrial
Rene López Flores Doctorado en Ingeniería Industrial Datos personales CVU 299134 Fecha y lugar de 11 de Abril de 1984, Omealca Veracruz nacimiento Dirección Mérida, Yucatán Estado civil Casado Contacto Celular: 272 18 18 453, e-mail: [email protected] Adscripción actual Nombramiento Profesor Investigador Titular "A", Tiempo Completo Ingreso Agosto-2016 Dependencia Facultad de Ingeniería Química Institución Universidad Autónoma de Yucatán (UADY) Dirección Periférico Norte Kilometro 33.5, Perif. de Mérida Lic. Manuel Berzunza 13615, Chuburna de Hidalgo Inn, 97203 Mérida, Yucatán Contacto Teléfono oficina: +52 (999) 9460956 Ext. 1197, e-mail: [email protected] Formación académica 2015 Doctorado en Ingeniería Industrial, Institut National Polytechnique de Toulouse, Toulouse, Francia. Cedula profesional: 11412339 2011 Maestría en Sistemas Computacionales, Instituto Tecnológico de Orizaba, Orizaba, México. Cedula profesional: 7349731 2006 Ingeniería en Sistemas Computacionales, Instituto Tecnológico de Orizaba, Orizaba, México. Cedula profesional: 5316090 Actividades de Investigación Líneas de investigación Orientadas en el campo de la administración estratégica de la innovación tecnológica, la innovación asistida por computadora, ingeniería de procesos, la inteligencia colectiva y análisis de datos. Experiencia investigación Página 1 de 8 2018 Ayuntamiento Mérida-FIQ. Responsable del proyecto "Programa para el control de emisiones contaminantes de fuentes móviles. Caso de estudio: parque vehicular del Ayuntamiento de Mérida 2015-2018, Yucatán". Vigencia 05/2018-08/2018. Financiamiento Ayuntamiento Mérida 2017-2019 PRODEP. Responsable del proyecto "Sistema experto para el diagnóstico de aspectos de sustentabilidad en PyMES de la región de Yucatán". Vigencia 07/2017- 03/2019. Financiamiento PRODEP 2017 Ayuntamiento Mérida-FIQ. Planeación de proyecto "Unidad de verificación y análisis de gases contaminantes provenientes de vehículos automotores(gasolina y diésel)". -

The PHP Security Checklist INTRODUCTION
The PHP Security Checklist INTRODUCTION Damn, but security is hard. It’s not always obvious what needs doing, and the payofs of good security are at best obscure. Who is surprised when it falls of our priority lists? We’d like to ofer a little help if you don’t mind. And by « help » we don’t mean « pitch you our product »—we genuinely mean it. Sqreen’s mission is to empower engineers to build secure web applications. We’ve put our security knowledge to work in compiling an actionable list of best practices to help you get a grip on your DevSecOps priorities. It’s all on the following pages. We hope your find if useful. If you do, share it with your network. And if you don’t, please take to Twitter to complain loudly—it’s the best way to get our attention. The Screen Team @SqreenIO [email protected] !1 CODE ✔ Use PHP 7! PHP 7 includes a range of built-in security-specific improvements (such as libsodium in PHP 7.2) and deprecates older, insecure features and functionality. As a result, it is far easier to create more secure applications with PHP 7, than any previous version of PHP. Use it whenever possible. Read more: • Deprecated features in PHP 7.0.x • Deprecated features in PHP 7.1.x • Deprecated features in PHP 7.2.x • Migrating a PHP 5 App to PHP 7 ✔ Use a SAST A SAST is a Static Application Security Tester (or testing service). A SAST scans source code looking for vulnerable code or potentially vulnerable code. -

Vergleich Verschiedener PHP-Basierter ORM-Frameworks Mit Fokus Auf Ihrem Anwendungspotenzial Für Content-Management-Systeme
Vergleich verschiedener PHP-basierter ORM-Frameworks mit Fokus auf ihrem Anwendungspotenzial für Content-Management-Systeme von Ingmar Szmais 3113419 Databay AG 1. Prüfer: Prof. Dr. rer. nat. Volker Sander 2. Prüfer: Thomas Joussen Reichshof, 26. Dezember 2018 1 Eidesstattliche Erklärung Hiermit versichere ich, dass ich die Seminararbeit mit dem Thema “Vergleich verschiedener PHP-basierter ORM-Frameworks mit Fokus auf ihrem Anwendungspotenzial für Content-Management-Systeme” selbstständig verfasst und keine anderen als die angegebenen Quellen und Hilfsmittel benutzt habe, alle Ausführungen, die anderen Schriften wörtlich oder sinngemäß entnommen wurden, kenntlich gemacht sind und die Arbeit in gleicher oder ähnlicher Fassung noch nicht Bestandteil einer Studien- oder Prüfungsleistung war. Ich verpflichte mich, ein Exemplar der Seminararbeit fünf Jahre aufzubewahren und auf Verlangen dem Prüfungsamt des Fachbereiches Medizintechnik und Technomathematik auszuhändigen. Name: Ingmar Szmais Reichshof, den 26.12.2018 Unterschrift des Studenten 1. Prüfer: Prof. Dr. rer. nat. Volker Sander 2. Prüfer: Thomas Joussen Reichshof, 26. Dezember 2018 2 Inhaltsverzeichnis ● 1. Einleitung 4 ● 2. Umgebung 5 ● 3. Voraussetzung und Einrichtung 6 ○ RedbeanPHP 6 ○ Doctrine 7 ○ Maghead 9 ● 4. Erweiterte Nutzung und Performance 11 ○ RedbeanPHP 11 ○ Doctrine 14 ○ Maghead 19 ● 5. Fazit 23 ● 6. Quellen 27 ● 7. Anhang 28 3 1. Einleitung Durch den Fortschritt der globalen Vernetzung und deren Integration in die Gesellschaft werden immer mehr analoge Datenverwaltungssysteme durch digitale Content-Management-Systeme (CMS) ersetzt. Besonders in der Web-basierten CMS Entwicklung sorgt die dadurch steigende Datenmenge und Datenverknüpfung in Korrelation mit der steigenden Komplexität der Anwendungen für Probleme, die sich meist durch eine verbesserte Datenstruktur und Reduzierung trivialer Datenbankabfragen beheben lassen. Besonders die Migration der meist prozeduralen, analogen Daten hin zu objektorientierten digitalen Daten stellt bei der Datenverwaltung eine der größten Schwierigkeiten dar. -

Database, Tables and Columns
http://redbeanphp.com/manual.php Introduction Welcome RedBeanPHP is an easy-to-use, on-the-fly ORM for PHP. It's 'zero config', relying on strict conventions instead. Let's look at the code, this is how you do CRUD in RedBeanPHP: require 'rb.php'; R::setup(); $post = R::dispense('post'); $post->text = 'Hello World'; $id = R::store($post); //Create or Update $post = R::load('post',$id); //Retrieve R::trash($post); //Delete This automatically generates the database, tables and columns... on-the-fly. It infers relations based on naming conventions. Download RedBeanPHP Now. RedBeanPHP is written by BDFL Gabor de Mooij and the RedBeanPHP community. News 2014-06-29: RedBeanPHP 4.0.5 improved UUID/GUID support. 2014-06-01: Restructuring documentation 2014-05-27: RedBeanPHP 4.0.4 has been released (see below). 2014-05-21: Backport via-cache fix to 3.5.9 2014-05-18: RedBeanPHP 4.0.3 fixed issue with Via Cache. 2014-05-12: RedBeanPHP 4.0.2 fixed issue with nullifying parent bean. 2014-04-23: RedBeanPHP 4.0.1 link() now also accept camelcase type (converts to snake_case). 2014-04-06: RedBeanPHP 3.5 update 8 has been released, this is a maintenance update. 2014-04-01: We are proud to announce the official release of RedBeanPHP 4.0, right on time! (as always). Zero Config No need to configure anything. No annotations or lengthy XML files. Just follow the conventions and everything works. Installation is also easy, just one file! No autoloaders, package management or include paths. RedBeanPHP also automatically configures your database 1 of 64 13-07-14 15:15 http://redbeanphp.com/manual.php connection to use UTF-8 encoding. -

Atviro Kodo (Atvirosios) Programinės Įrangos Vartojimo Situacijos Ir Patikimo Aptarnavimo Infrastruktūros Sukūrimo Galimybių Lietuvoje Tyrimo Ataskaita
VILNIAUS UNIVERSITETAS Atviro kodo (atvirosios) programin ės įrangos vartojimo situacijos ir patikimo aptarnavimo infrastrukt ūros suk ūrimo galimybi ų Lietuvoje tyrimo A T A S K A I T A VILNIUS, 2018 Tyrim ą atliko ir ataskait ą pareng ė: Valentina Dagien ė, Tolmantas Dagys, Viktoras Dagys, Egl ė Jasut ė, Tatjana Jevsikova, Gabriel ė Stupurien ė, Lina Vinikien ė. Redagavo Renata Valotkien ė. ĮVADAS 4 ATVIRO KODO PROGRAMINĖS ĮRANGOS ŠALTINI Ų ANALIZ Ė 9 1. Atviro kodo program ų naudojimo tendencij ų kaita 9 2. Užsienio šali ų patirtis 16 3. Atviro kodo program ų naudojimo Lietuvoje patirtis 24 4. Populiariausios atviro kodo programos 36 5. Atviro kodo program ų lokalizavimas 46 6. Atviro kodo programin ės įrangos saugumas ir jo užtikrinimo b ūdai 56 LIETUVOS VISUOMEN ĖS SLUOKSNI Ų NUOMONI Ų TYRIMAS 77 7. Ekspert ų strukt ūrizuoto interviu analiz ės rezultatai 78 8. Institucij ų internetin ė apklausa 104 9. Moksleivi ų ir student ų internetin ė apklausa 121 10. Interviu ir internetini ų apklaus ų rezultat ų apibendrinimas 128 BENDROSIOS IŠVADOS IR REKOMENDACIJOS 141 Šaltiniai 144 PRIEDAI 153 1 priedas. Populiariausios atviro kodo programos 153 2 priedas. Operacini ų sistem ų ir raštin ės paketo lokalizavimo užbaigtumas 163 3 priedas. Institucij ų internetin ės apklausos klausimynas 165 4 priedas. Moksleivi ų ir student ų internetin ės apklausos klausimynas 169 Įvadas Atvirosios, arba atviro kodo, programos tampa m ūsų kasdien naudojamais produktais, j ų sukuriama vis daugiau ir vis įvairesni ų. Labiausiai akcentuotina atviro kodo program ų savyb ė – aplink jas telkiasi bendruomen ės, vyksta bendradarbiavimas, generuojami nauji sprendimai, kurie skatina ir nuosavybini ų program ų tobul ėjim ą. -

A Web-Based Framework for Developing Cloud Multi-Tenant Softwareasaservice Application Supervisor Dr. Adil Yousif Jan 2017
UNIVERSITY OF SCIENCE AND TECHNOLOGY COLLEGE OF GRADUATE STUDIES AND ACADEMIC ADVANCEMENT Faculty of Computer Science and Information Technology A Web-Based Framework for Developing Cloud Multi-tenant Software as aService Application by Alsadig Hamad Hamid Ismail A Thesis Submitted to the College of Graduate Studies and Academic Advancements in Partial Fulfillment of the Requirement for the Degree of Master of Science in Information Technology Supervisor Dr. Adil Yousif Jan 2017 أﻵية قال هللا تعالى : ( ْقق َر أْق ِبا ْقا ِب َر ِبِّب َر لَّل ِب َر َر َر ) او ة لع ﻵية ْقق )1( Abstract Cloud computing portrays a new model for providing IT services over the Internet. In cloud computing, resources and services are accessed from the Internet through web- based tools. Nowadays, most of the businesses are performed by using the software as a service (SaaS) business model, one of the delivery models of cloud computing by charging the services through subscription.SaaS Multi-tenancy promotes sharing of resources all the way from a single application instance to the database, This allows applications to better fit the cloud computing paradigm. Building cloud saas application from scratch is a very complex task and takes time in developing these applications especially for a university student. There is a need for a framework that makes the creation of cloud saas applications. This research aims to build a new web-based framework for usable saas application development that supports multi-tenancy. This research proposed a new framework to develop SaaS application and supporting multitenancy. The proposed framework provide simple creation of a SaaS multitenancy application without writing a Code, and easy to customize to whom know PHP and web technology.