Computer Basics II: Disks and File Systems
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Active@ Boot Disk User Guide Copyright © 2008, LSOFT TECHNOLOGIES INC
Active@ Boot Disk User Guide Copyright © 2008, LSOFT TECHNOLOGIES INC. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without written permission from LSOFT TECHNOLOGIES INC. LSOFT TECHNOLOGIES INC. reserves the right to revise this documentation and to make changes in content from time to time without obligation on the part of LSOFT TECHNOLOGIES INC. to provide notification of such revision or change. LSOFT TECHNOLOGIES INC. provides this documentation without warranty of any kind, either implied or expressed, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. LSOFT may make improvements or changes in the product(s) and/or the program(s) described in this documentation at any time. All technical data and computer software is commercial in nature and developed solely at private expense. As the User, or Installer/Administrator of this software, you agree not to remove or deface any portion of any legend provided on any licensed program or documentation contained in, or delivered to you in conjunction with, this User Guide. LSOFT.NET logo is a trademark of LSOFT TECHNOLOGIES INC. Other brand and product names may be registered trademarks or trademarks of their respective holders. 2 Active@ Boot Disk User Guide Contents 1.0 Product Overview .......................................................................................................... -

The Rise of Autorun- Based Malware by Vinoo Thomas, Prashanth Ramagopal, and Rahul Mohandas Report the Rise of Autorun-Based Malware
Report The Rise of AutoRun- Based Malware By Vinoo Thomas, Prashanth Ramagopal, and Rahul Mohandas Report The Rise of AutoRun-Based Malware Table of Contents Abstract 3 The Return of Removable-Disk Malware 3 Distribution of AutoRun-Based Malware 4 AutoRun Woes 6 Incomplete autorun.inf cleaning 7 Traditional detection methods 8 Smart removal of autorun.inf 8 Leveraging In-the-Cloud Computing Technology 10 The Road Ahead 11 About the authors 12 Report The Rise of AutoRun-Based Malware Abstract Most people associate today’s computer viruses and other prevalent malware with the Internet. But that’s not where they started. Lest we forget, the earliest computer threats came from the era of floppy disks and removable media. With the arrival of the Internet, email and network-based attacks became the preferred infection vector for hackers to spread malicious code—while security concerns about removable media took a back seat. Now, however, our attention is returning to plug-in media. Over the years, floppy disks have been replaced by portable hard drives, flash media cards, memory sticks, and other forms of data storage. Today’s removable devices can hold 10,000 times more data than yesterday’s floppy disks. Not only can they store more data, today’s devices are “smart”—with the ability to run portable software programs1 or boot operating systems. 2,3 Seeing the popularity of removable storage, virus authors realized the potential of using this media as an infection vector. And they are greatly aided by a convenience feature in operating systems called AutoRun, which launches the content on a removable disk without any user interaction. -

Active@ UNDELETE Documentation
Active @ UNDELETE Users Guide | Contents | 2 Contents Legal Statement.........................................................................................................5 Active@ UNDELETE Overview............................................................................. 6 Getting Started with Active@ UNDELETE.......................................................... 7 Active@ UNDELETE Views And Windows...................................................................................................... 7 Recovery Explorer View.......................................................................................................................... 8 Logical Drive Scan Result View..............................................................................................................9 Physical Device Scan View......................................................................................................................9 Search Results View...............................................................................................................................11 File Organizer view................................................................................................................................ 12 Application Log...................................................................................................................................... 13 Welcome View........................................................................................................................................14 Using -

Investigating Powershell Attacks
Investigating PowerShell Attacks Black Hat USA 2014 August 7, 2014 PRESENTED BY: Ryan Kazanciyan, Matt Hastings © Mandiant, A FireEye Company. All rights reserved. Background Case Study WinRM, Victim VPN SMB, NetBIOS Attacker Victim workstations, Client servers § Fortune 100 organization § Command-and-control via § Compromised for > 3 years § Scheduled tasks § Active Directory § Local execution of § Authenticated access to PowerShell scripts corporate VPN § PowerShell Remoting © Mandiant, A FireEye Company. All rights reserved. 2 Why PowerShell? It can do almost anything… Execute commands Download files from the internet Reflectively load / inject code Interface with Win32 API Enumerate files Interact with the registry Interact with services Examine processes Retrieve event logs Access .NET framework © Mandiant, A FireEye Company. All rights reserved. 3 PowerShell Attack Tools § PowerSploit § Posh-SecMod § Reconnaissance § Veil-PowerView § Code execution § Metasploit § DLL injection § More to come… § Credential harvesting § Reverse engineering § Nishang © Mandiant, A FireEye Company. All rights reserved. 4 PowerShell Malware in the Wild © Mandiant, A FireEye Company. All rights reserved. 5 Investigation Methodology WinRM PowerShell Remoting evil.ps1 backdoor.ps1 Local PowerShell script Persistent PowerShell Network Registry File System Event Logs Memory Traffic Sources of Evidence © Mandiant, A FireEye Company. All rights reserved. 6 Attacker Assumptions § Has admin (local or domain) on target system § Has network access to needed ports on target system § Can use other remote command execution methods to: § Enable execution of unsigned PS scripts § Enable PS remoting © Mandiant, A FireEye Company. All rights reserved. 7 Version Reference 2.0 3.0 4.0 Requires WMF Requires WMF Default (SP1) 3.0 Update 4.0 Update Requires WMF Requires WMF Default (R2 SP1) 3.0 Update 4.0 Update Requires WMF Default 4.0 Update Default Default Default (R2) © Mandiant, A FireEye Company. -

The NTFS File System
The NTFS File System OVERVIEW: This lab is part of a series of lab exercises intended to support courseware for Forensics training. The development of this document is funded by the Department of Labor (DOL) Trade Adjustment Assistance Community College and Career Training (TAACCCT) Grant No. TC-22525-11-60-A-48. In this lab, students will enumerate hosts on the network using various tools. This lab includes the following tasks: 1 – Examining the NTFS File System 2 – Using a HEX Editor to explore an NTFS Partition 3 – Verifying and viewing the image details 4 – Analyzing an NTFS Partition With Autopsy Key TermDescription The acronym NTFS stands for New Technology File System. The NTFS File System was originally introduced with the Windows NT. NTFS is a journaling file system which means it keeps a log of changes being written to the disk. If a computer is shutdown improperly, it will have a better NTFS chance of recovery if it has a journaling file system. Files and folder access can be restricted with the security feature of NTFS. Starting with Windows 2000, Microsoft included the Encrypted File System, or EFS, as an NTFS feature. EFS allows users to encrypt files to protect against unauthorized access. A Feature of the NTFS File system that allows you to encrypt files and folders. The feature EFS became available on the NTFS File system starting with Windows 2000, and is still available today on Windows 10 and Server 2016. An Alternate Data Stream, or ADS, is a feature of the NTFS file system that allowed compatibility ADS with older versions of the Mac OS. -

Problem 1 : Write-Based Skippy. Problem 2 : Skippy Variant
CMU 18-746 Storage Systems Assigned: 1 Feb 2010 Spring 2010 Homework 2 Due: 22 Feb 2010 Solutions are due at the beginning of class on the due date and must be typed and neatly organized. Late homeworks will not be accepted. You are permitted to discuss these problems with your classmates; how- ever, your work and answers must be your own. All questions should be directed to the teaching assistant. Problem 1 : Write-based Skippy. Before answering the following two problems, please read the following paper: Microbenchmark-based Extraction of Local and Global Disk Characteristics by Nisha Talagala, Remzi H. Arpaci-Dusseau, and David Patterson (Berkeley TR CSD-99-1063). It is available from the course website. (a) First, describe in words the functionality of lseek. Specifically, what happens when lseek(fd, 1048576, SEEK CUR) is issued? (b) Refer to Figure 1, which shows the result of simulating the Skippy experiment on a disk simulator. Label this graph with the following values: rotational latency, MTM, sectors per track, number of heads, head switch time, and cylinder switch time. Also label the head and cylinder switches. Make sure you mark the parts of the figure that indicate these values. (c) How would Figure 1 change, if the disk were replaced with one that has a higher rotation speed, but is the same in every other respect? (d) If the WRITEs used in the Skippy experiment were replaced with READs, do you think the observed value for MTM would change? Explain your answer. Problem 2 : Skippy variant. Assume the skippy algorithm is replaced with the following: fd = open ( ‘ ‘ raw d i s k d e v i c e ’ ’ ) ; ¡ f o r ( i = 0 ; i measurements ; i + + ) l s e e k ( fd , 0 , SEEK SET ) ; w r i t e ( fd , b u f f e r , SINGLE SECTOR ) ; / / time t h e f o l l o w i n g w r i t e and o u t p u t i , time ¢ / / i i s t h e hop s i z e l s e e k ( fd , i £ SINGLE SECTOR , SEEK SET ) ; w r i t e ( fd , b u f f e r , SINGLE SECTOR ) ; ¤ c l o s e ( fd ) ; Figure 2 shows the results of running this experiment (it is a plot of time vs. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Hunting Red Team Activities with Forensic Artifacts
Hunting Red Team Activities with Forensic Artifacts By Haboob Team 1 [email protected] Table of Contents 1. Introduction .............................................................................................................................................. 5 2. Why Threat Hunting?............................................................................................................................. 5 3. Windows Forensic.................................................................................................................................. 5 4. LAB Environment Demonstration ..................................................................................................... 6 4.1 Red Team ......................................................................................................................................... 6 4.2 Blue Team ........................................................................................................................................ 6 4.3 LAB Overview .................................................................................................................................. 6 5. Scenarios .................................................................................................................................................. 7 5.1 Remote Execution Tool (Psexec) ............................................................................................... 7 5.2 PowerShell Suspicious Commands ...................................................................................... -
[JUMP FLOPPY Bios PARAMETER BLOCK—\20
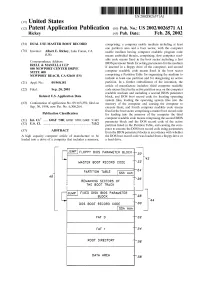
US 20020026571A1 (19) United States (12) Patent Application Publication (10) Pub. No.: US 2002/0026571 A1 Rickey (43) Pub. Date: Feb. 28, 2002 (54) DUAL USE MASTER BOOT RECORD comprising: a computer usable medium including at least one partition area and a boot sector, With the computer (76) Inventor: Albert E. Rickey, Lake Forest, CA usable medium having computer readable program code (Us) means embodied therein, comprising: ?rst computer read able code means ?xed in the boot sector including a ?rst Correspondence Address: BIOS parameter block for setting parameters for the medium IRELL & MANELLA LLP if inserted in a ?oppy drive of the computer; and second 840 NEWPORT CENTER DRIVE SUITE 400 computer readable code means ?xed in the boot sector NEWPORT BEACH, CA 92660 (US) comprising a Partition Table for organizing the medium to include at least one partition and for designating an active (21) Appl. No.: 09/960,181 partition. In a further embodiment of the invention, the article of manufacture includes: third computer readable (22) Filed: Sep. 20, 2001 code means ?xed in the active partition area on the computer readable medium and including a second BIOS parameter Related US. Application Data block, and DOS boot record code for locating operating system ?les, loading the operating system ?les into the (63) Continuation of application No. 09/163,359, ?led on memory of the computer and causing the computer to Sep. 30, 1998, noW Pat. No. 6,308,264. execute them; and fourth computer readable code means ?xed in the boot sector comprising a master boot record code Publication Classi?cation for loading into the memory of the computer the third computer readable code means comprising the second BIOS (51) Int. -

Dolphin Power Tools User's with Windows Embedded Handheld 6.5
Dolphin™ Power Tools with Windows® Mobile 6.X for the Dolphin 6000 Scanphone User’s Guide Disclaimer Honeywell International Inc. (“HII”) reserves the right to make changes in specifications and other information contained in this document without prior notice, and the reader should in all cases consult HII to determine whether any such changes have been made. The information in this publication does not represent a commitment on the part of HII. HII shall not be liable for technical or editorial errors or omissions contained herein; nor for incidental or consequential damages resulting from the furnishing, performance, or use of this material. This document contains proprietary information that is protected by copyright. All rights are reserved. No part of this document may be photocopied, reproduced, or translated into another language without the prior written consent of HII. © 2011 Honeywell International Inc. All rights reserved. Microsoft® Windows®, Windows NT®, Windows 2000, Windows ME, Windows XP, Windows Vista, Windows .NET Framework, Windows ActiveSync®, and the Windows logo are trademarks or registered trademarks of Microsoft Corporation. The Bluetooth® word mark and logos are owned by Bluetooth SIG, Inc. Other product names or marks mentioned in this document may be trademarks or registered trademarks of other companies and are the property of their respective owners. Web Address: www.honeywellaidc.com Table of Contents Chapter 1 - Introduction Dolphin Power Tools Overview............................................................................................1-1 -

A Baseline for XP Boot Changes AAFS - 26 February 2010
A Baseline for XP Boot Changes AAFS - 26 February 2010 Ben Livelsberger NIST Information Technology Laboratory CFTT Project 1 Certain trade names and company products are mentioned in the text or identified. In no case does such identification imply recommendation or endorsement by the National Institute of Standards and Technology, nor does it imply that the products are necessarily the best available for the purpose. 2 Introduction Methodology/Approach Expected Results Analysis/Findings Conclusion 3 Question: What changes on a hard drive when you boot a system? Answer: Sector content of installed devices containing volumes Accessed, write, created date and time metadata Files created Files deleted 4 Build Vanilla XP system not networked Cycle through several boots and shutdowns Image with dd Boot, 2 minutes idle, shutdown, and reimage (5x) Compare images- Linux & perl Analyze differences- perl scripts and SleuthKit Tools 5 Build (vanilla) XP system DCO drive to 12 GB Partitioned 7 GB primary FAT32 2 GB secondary NTFS & 2 GB secondary FAT32 Windows XP Professional SP2 Add user files to secondary partitions 5 files - 2.4 Mb Types: .inf, .pdf, .exe, .ico, & .html 6 2.1 GB secondary NTFS partition.Payload 898,594 of 5 files copied from bootable CD (a 43 unallocated byte autorun.inf, a 17 Kb .pdf, a 2.4 sectors 7.3 GB FAT32 Mb .exe, a 13 Kb .ico, & a 13 Kb .html MBR (boot code, boot partition file). partition table, with XP SP2 Primary extended signature value) installed 2.1 GB secondary partition table + Secondary + 62 sectors) FAT32 partition. 62 sectors) extended partition table + Payload same as 62 sectors) NTFS partition Primary extended Secondary extended partition 7 partition 2.1 GB secondary NTFS partition.Payload of 5 files copied from bootable CD (a 43 byte autorun.inf, a 17 Kb .pdf, a 2.4 7.3 GB FAT32 Mb .exe, a 13 Kb .ico, & a 13 Kb .html boot partition file). -

Wikipedia: Design of the FAT File System
Design of the FAT file system A FAT file system is a specific type of computer file system architecture and FAT a family of industry-standard file systems utilizing it. Developer(s) Microsoft, SCP, IBM, [3] The FAT file system is a legacy file system which is simple and robust. It Compaq, Digital offers good performance even in very light-weight implementations, but Research, Novell, cannot deliver the same performance, reliability and scalability as some Caldera modern file systems. It is, however, supported for compatibility reasons by Full name File Allocation Table: nearly all currently developed operating systems for personal computers and FAT12 (12- many home computers, mobile devices and embedded systems, and thus is a bit version), well suited format for data exchange between computers and devices of almost FAT16 (16- any type and age from 1981 through the present. bit versions), Originally designed in 1977 for use on floppy disks, FAT was soon adapted and FAT32 (32-bit version used almost universally on hard disks throughout the DOS and Windows 9x with 28 bits used), eras for two decades. Today, FAT file systems are still commonly found on exFAT (64- floppy disks, USB sticks, flash and other solid-state memory cards and bit versions) modules, and many portable and embedded devices. DCF implements FAT as Introduced 1977 (Standalone the standard file system for digital cameras since 1998.[4] FAT is also utilized Disk BASIC-80) for the EFI system partition (partition type 0xEF) in the boot stage of EFI- FAT12: August 1980 compliant computers. (SCP QDOS) FAT16: August 1984 For floppy disks, FAT has been standardized as ECMA-107[5] and (IBM PC DOS 3.0) ISO/IEC 9293:1994[6] (superseding ISO 9293:1987[7]).