Anti-Theft Atm Robbery Detection Using Big Surveillance Video Data
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Aho Tnpsc 591 Horti Blo
SL. Register No. Date of Birth, Controlling Officer to Post to which No. (TNPSC) Name of the Community & whom joining to be appointed Candidate & Address Qualification reported 1 170001002 23/06/1996 GOBICHETTI PALAYAM DDH, ERODE SUKUMAR M BC 139 SIVIYARPALAYAM (OBC|DA(LD/DF/CP/MU KOMARRAPALAYAM D) STHYAMANGALAM HSC& DIP.IN ERODE HORTICULTURE ERODE DISTRICT 2 010001012 30/05/1997 KOLIYANUR DDH, VILLUPURAM PRIYANKA V BC(OBCM) NO.128 NADU STREET HSC& DIP.IN DHADHPRUAM VILLAGE HORTICULTURE TINDIVANAM TK VILLUPURAM DISTRICT TAMIL NADU 3 170001067 27/06/1998 ATHUR DDH, SALEM KARTHI R MBC/DC KARTHI R S/O HSC& DIP.IN RAMASAMY HORTICULTURE DOOR NO-3/14, GANAPATHI GOUNDER ST.PN PATTY, 4 020001017 07/07/1991 MUGAIYUR DDH, VILLUPURAM ARIVAZHAGAN S MBC/DC 185, MIDDLE STREET HSC& DIP.IN CHINNAVADAVADI, HORTICULTURE ERUMANUR POST B.SC VIRUDHACHALAM TALUK 5 010001099 31/07/1996 OLAKKUR DDH, VILLUPURAM AJITHKUMAR S MBC/DC 1/2 MIDDEL STREET HSC& DIP.IN EZHUSEMPON HORTICULTURE KANJANUR POST, VIKRAVANDI TALUK VILLUPURAM DISTRICT 6 010001061 03/03/1992 ALANGAYAM DDH, VELLORE KALAIARASAN M MBC/DC NO:5/251, PERIYAR HSC& DIP.IN STREET HORTICULTURE PERIYA VINJIYAMPAKKAM SINGAPERUMAL KOIL 7 170001122 02/06/1992 EDAPADY DDH, SALEM GUNASEKAR R MBC/DC 4/59 KARATTUR KATTU HSC& DIP.IN KOTTAI HORTICULTURE KATCHUPALLI-VIL, K.VADUGAPATTI IDAPPADI TK 8 170001061 03/02/1997 KOLATHUR DDH, SALEM PRAVEENKUMAR P MBC/DC 12/14 THERKUKADU HSC& DIP.IN KATCHUPPALLI PO HORTICULTURE IDAPPADI TK SALEM DISTRICT TAMIL NADU 9 170001017 09/06/1981 ANNAVASAL DDH, PUDUKKOTTAI ILAKKIYASELVAN B MBC/DC NO 462, VATHANGAN HSC& DIP.IN STREET HORTICULTURE ANAVAYAL TALUK PUDUKKOTTAI DISTRICT SL. -

The India Cements Limited
THE INDIA CEMENTS LIMITED UNCLAIMED DIVIDEND FOR THE YEAR 2010-11 TO BE TRANSFERRED TO INVESTOR EDUCATION AND PROTECTION FUND AS REQUIRED UNDER SECTION 124 OF THE COMPANIES ACT 2013 READ WITH THE INVESTOR EDUCATION AND PROTECTION FUND AUTHORITY (ACCOUNTING, AUDIT, TRANSFER AND REFUND) RULES, 2016, AS AMENDED FOLIO / DPID_CLID NAME CITY PINCODE 1201040000010433 KUMAR KRISHNA LADE BHILAI 490006 1201060000057278 Bhausaheb Trimbak Pagar Nasik 422005 1201060000138625 Rakesh Dutt Panvel 410206 1201060000175241 JAI KISHAN MOHATA RAIPUR 492001 1201060000288167 G. VINOD KUMAR JAIN MANDYA 571401 1201060000297034 MALLAPPA LAGAMANNA METRI BELGAUM 591317 1201060000309971 VIDYACHAND RAMNARAYAN GILDA LATUR 413512 1201060000326174 LEELA K S UDUPI 576103 1201060000368107 RANA RIZVI MUZAFFARPUR 842001 1201060000372052 S KAILASH JAIN BELLARY 583102 1201060000405315 LAKHAN HIRALAL AGRAWAL JALNA 431203 1201060000437643 SHAKTI SHARAN SHUKLA BHADOHI 221401 1201060000449205 HARENDRASINH LALUBHA RANA LATHI 365430 1201060000460605 PARASHURAMAPPA A SHIMOGA 577201 1201060000466932 SHASHI KAPOOR BHAGALPUR 812001 1201060000472832 SHARAD GANESH KENI RATNAGIRI 415612 1201060000507881 NAYNA KESHAVLAL DAVE NALLASOPARA (E) 401209 1201060000549512 SANDEEP OMPRAKASH NEVATIA MAHAD 402301 1201060000555617 SYED QUAMBER HUSSAIN MUZAFFARPUR 842001 Page 1 of 301 FOLIO / DPID_CLID NAME CITY PINCODE 1201060000567221 PRASHANT RAMRAO KONDEBETTU BELGAUM 591201 1201060000599735 VANDANA MISHRA ALLAHABAD 211016 1201060000630654 SANGITA AGARWAL CUTTACK 753004 1201060000646546 SUBODH T -
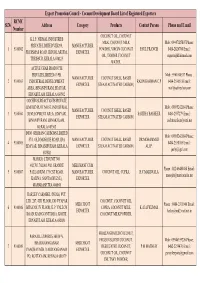
Exporters List
Export Promotion Council - Coconut Development Board List of Registered Exporters RCMC Sl.No Address Category Products Contact Person Phone and E mail Number COCONUT OIL, COCONUT K.L.F. NIRMAL INDUSTRIES MILK, COCONUT MILK Mob : 09447025807 Phone : PRIVATE LIMITED VIII/295, MANUFACTURER 1 9100002 POWDER, VIRGIN COCONUT PAUL FRANCIS 0480-2826704 Email : FR.DISMAS ROAD, IRINJALAKUDA, EXPORTER OIL, TENDER COCONUT [email protected] THRISSUR, KERALA 680125 WATER, ACTIVE CHAR PRODUCTS PRIVATE LIMITED 63/9B, Mob : 9961000337 Phone : MANUFACTURER COCONUT SHELL BASED 2 9100003 INDUSTRIAL DEVELOPMENT RAZIN RAHMAN C.P 0484-2556518 Email : EXPORTER STEAM ACTIVATED CARBON, AREA, BINANIPURAM, EDAYAR, [email protected] ERNAKULAM, KERALA 683502 COCHIN SURFACTANTS PRIVATE LIMITED PLOT NO.63, INDUSTRIAL Mob : 09895242184 Phone : MANUFACTURER COCONUT SHELL BASED 3 9100004 DEVELOPMENT AREA, EDAYAR, SAJITHA BASHEER 0484-2557279 Email : EXPORTER STEAM ACTIVATED CARBON, BINANIPURAM, ERNAKULAM, [email protected] KERALA 683502 INDO GERMAN CARBONS LIMITED Mob : 09895242184 Phone : 57/3, OLD MOSQUE ROAD, IDA MANUFACTURER COCONUT SHELL BASED DR.MOHAMMED 4 9100005 0484-2558105 Email : EDAYAR, BINANIPURAM, KERALA EXPORTER STEAM ACTIVATED CARBON, ALI.P. [email protected] 683502 MARICO LTD UNIT NO. 402,701,702,801,902, GRANDE MERCHANT CUM Phone : 022-66480480 Email : 5 9100007 PALLADIUM, 175 CST ROAD, MANUFACTURER COCONUT OIL, COPRA, H.C MARIWALA [email protected] KALINA, SANTACRUZ (E), EXPORTER MAHARASHTRA 400098 HARLEY CARMBEL (INDIA) PVT. LTD. 287, -

District Census Handbook, Thanjavur, Part X-A, Series-19
CENSUS OF INDIA, 1971 SERIES 19 TAMIL NADU PART X-A DISTRICT CENSUS HANDBOOK village and Town Directory THANJAVUR K. C HOC K A II N GAM of the Indian Administratire Service DIRECTOR OF CENSUS OPERATIONS. TAMIL NADU AND PONDICHERRY. 1972 jo Ang o 0 I I oj (/) L __________ -- o~~ ~ .., ~• II II II I .... ,: I·0 - -----_-----""- _...;.. -- CONTENTS Page No. Preface ... v Part-A VILLA GE AND TOWN DIRECTORY Introductory Note: vii-xiii (I) Village Directory ••• Amenities and land use Appendix-I Land use particulars of NOD - city urban area (Non-Municipal area) Appendix-II Abstr<lct showing Educationa), Medica1 aad other amenities available in Taluks. Alphabetical Jist of Villages. 1. Sirkali Taluk ... 2 -13 2. Mayuram ,. 14:- 35 S. Kumbakonam ,. 36 - 54 4:. Nannilam .. 55 - 84 5. Papanasam .. ... 85 -108 6. Thanjavur .. 109-134: 7. Orthanad 135-152 " ... 153 -172 8. Mannargudi .. '" 9. Nagapattinam .. - 173-190 191-210 10. Thiruthuraipundi " 11. Pattukkottai '0 211-234 12. Peravurani .. - 235-251 13. Arantangi ,. - 252-282 iv Page No. (II) Town Directory Statement: I - Status. Growth History and FunctIOnal Category of Tov.ns. 286 - 291 II - PhysIcal Aspects and Location of Towns, 1969. 292-297 lIt - Municipal Finance, 1968- 69 298-30:1 IV - Civic and other amenitle", 1969 304-309 , , V- Medical, Educational. Recreational and Cultural Facll.t1es in Towns. 1969 310 315 .. VI - Trade. Commerce. Industry and Banking, 1969 316- 321 ,. V/I- Population by rehgion. 1971 322-327 Maps f'i!'.trict map of Thanjavur Frontispiece PRf:FAGE It has been the practice since 1951 to publish for each District a Census Hand book, contaming the Census Statistics for each village and town in the Distnct together wIth certain administrative statistics collected from the various Departments of the State Government. -
Tiruvarur District EXTRACT of RULE 4(1)
Tiruvarur District EXTRACT OF RULE 4(1)(b) OF THE RIGHT TO INFORMATION ACT 2005. (i) The Particulars of its organization, functions and duties. Tiruvarur District is subdivided into 5 Sub – Divisions each headed by a Deputy Superintendent of Police. The Sub – Division are divided into a total of 25 Police station and 4 All women Police Station which is the basic unit of police functioning. A list of Police station and Sub – divisions, besides the law and order Sub – Division there are special units as follows. S.No. Name of the Police station S.No. Name of the Police station Tiruvarur Sub – Division Nannilam Sub – Division 1 Tiruvarur Town P.S. 1 Nannilam P.S. 2 Tiruvarur Taluk P.S. 2 Peralam P.S. 3 Vaipoor P.S. 3 Kodavasal P.S. 4 Koradachery P.S. 4 Eravanchery P.S. 5 Koothanallur P.S. 6. Vadapathimangalam P.S. Muthupet Sub – Division Thiruthuraipoondi Sub – Divison 1 Muthupet P.S 1 Thiruthuraipoondi P.S. 2 Perugavalanthan P.S. 2 Alivalam P.S 3 Edaiyur P.S 3 Kottur P.S. 4 Kalappal P.S. 5 Thirukkalar P.S. Mannargudi Sub – Division All Women Police station 1 Mannargudi Town P.S 1 Tiruvarur 2 Mannargudi Taluk P.S. 2 Nannilam 3 Thalayamangalam P.S 3 Mannargudi 4 Paravakottai P.S. 4 Thiruthuraipoondi 5 Thirumakottai P.S 2 6 Vaduvoor P.S. 7 Needamangalam P.S. Special units 1 Prohibition Enforcement Wing, Tiruvarur 2 Prohibition Enforcement Wing, Thiruthuraipoondi, 3. District Crime Branch, Tiruvarur. 4 Social justice & Human Right Unit, Tiruvaur 5 Single Digit Finger Print Bureau, Tiruvaur, 6 District Crime Records Bureau, Tiruvarur. -

District Survey Report of Thiruvarur District
DISTRICT SURVEY REPORT OF THIRUVARUR DISTRICT DEPARTMENT OF GEOLOGY AND MINING THIRUVARUR DISTRICT 1 DISTRICT SURVEY REPORT- THIRUVARUR CONTENTS S.No Chapter Page No. 1.0 Introduction 1 2.0 Overview of Mining Activity in the District; 4 3.0 General profile of the district 4 4.0 Geology of the district; 9 5.0 Drainage of irrigation pattern 10 6.0 Land utilisation pattern in the district; Forest, Agricultural, 10 Horticultural, Mining etc 7.0 Surface water and ground water scenario of the district 11 8.0 Rainfall of the district and climate condition 11 9.0 Savudu/Earth - Details of the mining lease in the district as per 13 following format 10.0 Details of Royalty / Revenue received in the last three years 17 (2015-16 to 2017-18) 11.0 Details of Production of Minor Mineral in last three Years 26 12.0 Mineral map of the district 26 13.0 List of letter of intent (LOI) holder in the district along with its 27 validity 14.0 Total mineral reserve available in the district. 28 15.0 Quality / Grade of mineral available in the district 28 16.0 Use of mineral 29 17.0 Demand and supply of the mineral in the lase three years 30 2 DISTRICT SURVEY REPORT- THIRUVARUR 18.0 Mining leases marked on the map of the district 31 19.0 Details of the area where there is a cluster of mining leases viz., 33 number of mining leases, location (latitude & longitude) 20.0 Details of eco-sensitive area 33 21.0 Impact on the environment due to mining activity 35 22.0 Remedial measure to mitigate the impact of mining on the 36 environment 23.0 Reclamation of mined out -

Thiruvarur District
CENSUS OF INDIA 2011 TOTAL POPULATION AND POPULATION OF SCHEDULED CASTES AND SCHEDULED TRIBES FOR VILLAGE PANCHAYATS AND PANCHAYAT UNIONS THIRUVARUR DISTRICT DIRECTORATE OF CENSUS OPERATIONS TAMILNADU ABSTRACT THIRUVARUR DISTRICT No. of Total Total Sl. No. Panchayat Union Total Male Total SC SC Male SC Female Total ST ST Male ST Female Village Population Female 1 Valangaiman 50 88,891 44,394 44,497 40,423 20,274 20,149 56 28 28 2 Nannilam 48 1,00,999 50,705 50,294 37,164 18,712 18,452 25 10 15 3 Kodavasal 49 96,965 49,022 47,943 24,490 12,450 12,040 82 37 45 4 Thiruvarur 34 93,395 46,408 46,987 40,519 20,293 20,226 80 41 39 5 Koradacheri 44 1,03,301 51,228 52,073 44,810 22,356 22,454 38 15 23 6 Mannargudi 51 1,31,164 65,281 65,883 46,217 22,986 23,231 43 22 21 7 Needamangalam 44 1,15,373 56,935 58,438 31,386 15,610 15,776 151 77 74 8 Kottur 49 1,07,525 53,218 54,307 50,118 24,912 25,206 129 66 63 9 Thiruthuraipoondi 32 91,278 45,158 46,120 47,167 23,342 23,825 300 147 153 10 Muthupettai 29 77,591 37,605 39,986 26,446 12,953 13,493 35 18 17 Grand Total 430 10,06,482 4,99,954 5,06,528 3,88,740 1,93,888 1,94,852 939 461 478 VALANGAIMAN PANCHAYAT UNION Sl. -

PUBLIC WORKS DEPARTMENT IRRIGATION Demand No: 40
PUBLIC WORKS DEPARTMENT IRRIGATION Demand No: 40 POLICY NOTE 2011 -2012 K.V.RAMALINGAM MINISTER FOR PUBLIC WORKS © Government of Tamil Nadu 2011 INDEX 11 Flood Mitigation Schemes 77 12 Tamil Nadu Irrigated 82 Sl. Subject Page Agriculture Modernisation and No. Water - Bodies Restoration 1 Water Resources Department 1 and Management (TN IAMWARM) Project 2 Special Initiative Schemes of 4 13 Jawaharlal Nehru National 86 the Hon’ble Chief Minister Urban Renewal Mission. (JNNURM) 3 Inter State River Water Issues 11 14 Artificial Recharge Scheme 89 4 Construction of Groyne field 39 along Puduchery Coast 15 Participatory Irrigation 91 Management (PIM) 5 Draft Dam Safety Bill, 2010 41 16 Linking of Rivers within the 94 6 Dam Rehabilitation and 48 State Improvement Project (DRIP) 17 Repairs, Renovation and 98 th 7 13 Finance Commission 51 Restoration of Water Bodies in Grants-in-Aid Programme the 51 Drought Prone Blocks in Tamil Nadu 8 Irrigation Schemes 58 18 Irrigation Management 98 9 National Agriculture 69 Training Institute (IMTI) Development Programme Under Centrally Sponsored 19 State Ground and Surface 100 Scheme Water Resources Data Centre 10 Part – II Schemes 69 20 Institute for Water Studies 103 21 Directorate of Boilers 107 22 Providing last mile 110 connectivity through wide area network connections to Water Resources Department. PREFACE The necessity for intra-linking of rivers for diversion of flood water and Public Works Department is one of enhancing the storage capacity of water the oldest Service Departments of the bodies to provide adequate water for Government, serving in the construction irrigation, drinking and other purposes field and maintenance of Irrigation have been well taken. -

Tamil Nadu Government Gazette
© [Regd. No. TN/CCN/467/2012-14. GOVERNMENT OF TAMIL NADU [R. Dis. No. 197/2009. 2015 [Price: Rs. 32.00 Paise. TAMIL NADU GOVERNMENT GAZETTE PUBLISHED BY AUTHORITY No. 28] CHENNAI, WEDNESDAY, JULY 15, 2015 Aani 30, Manmadha, Thiruvalluvar Aandu – 2046 Part VI—Section 4 Advertisements by private individuals and private institutions CONTENTS PRIVATE ADVERTISEMENTS Pages. Change of Names .. 2125-2204 Notice .. 2204 NOTICE NO LEGAL RESPONSIBILITY IS ACCEPTED FOR THE PUBLICATION OF ADVERTISEMENTS REGARDING CHANGE OF NAME IN THE TAMIL NADU GOVERNMENT GAZETTE. PERSONS NOTIFYING THE CHANGES WILL REMAIN SOLELY RESPONSIBLE FOR THE LEGAL CONSEQUENCES AND ALSO FOR ANY OTHER MISREPRESENTATION, ETC. (By Order) Director of Stationery and Printing. CHANGE OF NAMES 31011. My son, Udhaya, born on 16th February 2005 31014. I, D. Petchiammal, wife of Thiru G. Dhanasekaran, (native district: Madurai), residing at No. 52, Sayakkarar born on 7th May 1969 (native district: Virudhunagar), Street, Virudhunagar-626 001, shall henceforth be residing at Old No. 12, New No. 48, Mandalanadar Colony, known as UDHAYA VITHAL KADAM. Satchiyapuram Road, Thiruthangal, Virudhunagar-626 130, VITHAL BAL KADAM. shall henceforth be known as D. MAGESWARI. Virudhunagar, 6th July 2015. (Father.) D. «ð„Cò‹ñ£œ. Thiruthangal, 6th July 2015. 31012. My son, V. Rohith, born on 4th November 2002 (native district: Madurai), residing at No. 52, Sayakkarar 31015. D. Selva, son of Thiru S. Dhanasekaran, born on Street, Virudhunagar-626 001, shall henceforth be 18th December 1993 (native district: Sivagangai), residing at known as ROHITH VITHAL KADAM. No. 3259, Somasundar Nagar, Kalayarkovil Post, Sivagangai- 630 551, shall henceforth be known as D. -
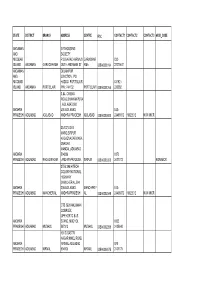
State District Branch Address Centre Ifsc Contact1 Contact2 Contact3 Micr Code
STATE DISTRICT BRANCH ADDRESS CENTRE IFSC CONTACT1 CONTACT2 CONTACT3 MICR_CODE ANDAMAN G R HOUSING AND SOCIETY NICOBAR P.O,GARACHARMA,S GARACHAR 033- ISLAND ANDAMAN GARACHARMA OUTH ANDAMAN ST AMA IOBA0003194 22270611 ANDAMAN DELANIPUR AND JUNCTION, PO NICOBAR HADDO PORT BLAIR 03192 - ISLAND ANDAMAN PORT BLAIR PIN : 744102 PORT BLAIR IOBA0001265 230392 3,&4, CINEMA ROAD,BHAWANPURA , ADILABAD 500 ANDHRA 400.ADILABAD, 040- PRADESH ADILABAD ADILABAD ANDHRA PRADESH ADILABAD IOBA0002600 23468872 10022012 NON MICR 33-137,LOYA MARG,SIRPUR KAGAZNAGAR,KAGA ZNAGAR MANDAL,ADILABAD ANDHRA 504296 0870 PRADESH ADILABAD KAGAZ NAGAR ,ANDHRAPRADESH. SIRPUR IOBA0003323 2431772 NON MICR 375& 396,HITECH COLONY NATIONAL HIGHWAY ,MANCHERIAL,504 ANDHRA 208.ADILABAD MANCHERIY 040- PRADESH ADILABAD MANCHERIAL ANDHRAPRADESH AL IOBA0002599 23468872 10022012 NON MICR CTS 2628 ANJUMAN COMPLEX, OPP.KSRTC BUS ANDHRA STAND, MUDHOL 0832 PRADESH ADILABAD MUDHOL 587313 MUDHOL IOBA0002295 2435640 131 D SASTRI NAGAR MNCL ROAD ANDHRA NIRMAL ADILABAD 870 PRADESH ADILABAD NIRMAL 504106 NIRMAL IOBA0003675 2431775 6/399M(P) A B NARAYANA REDDY COMPLEX, RAILWAY STATION ROAD, PHONE ANDHRA RAJAMPET PIN 08565 PRADESH ADILABAD RAJAMPET 516115 RAJAMPET IOBA0001478 248300 PLOT NO 36, VIDYUTH NAGAR MAIN ROAD, PHONE ANDHRA ANANTHAPUR PIN ANANTAPU 08554 PRADESH ANANTAPUR ANANTAPUR 515001 R IOBA0001281 223323 16.108,AYYAPPA COMPLEX,SLV THEATRE ANDHRA ROAD,GUNTAKAL 877 PRADESH ANANTAPUR GUNTAKAL 515801 GUNTAKAL IOBA0003683 2250048 D NO 4-7-33, LAKSHMI PLAZA, RAHMATHPUR ANDHRA CIRCLE, HINDUPUR, -

All India Council for Technical Education
ALL INDIA COUNCIL FOR TECHNICAL EDUCATION STATUS OF APPROVAL FOR AICTE APPROVED INSTITUTIONS BEYOND THE ACADEMIC YEAR 2008-09 Region: Southern State: Tamilnadu S.No. Name & Address of the institutions/YOE/Status Course(s) Existing Approved Intake for Intake for 2008-09 2009-10 1. 06/05/PON/ARTS/2004 Applied Arts 30 30 Bharathiar Palkalaikoodam Cuddalore Road, Ariyankuppam, MVA- Applied Art (Visual Art) 15 15 Puducherry - 605 007 Dr. M.Jayaraman Qualification: M.A., Ph.D.,PDFA DOB:05.04.1954 DOJ:16.06.1954 (PRIVATE) / 2004-2005 1. School of Management Studies, PG Course(s) Pondicherry University, Pondicherry 605 014 MBA (F T) 60 Pending Compliance 1993-1994 TOTAL: 60 report not 411/TN-29/BOS/CS/95 received Director: Qualification: Ph.D. DOB: DOJ: Ph.No:- Fax No: E-mail: Website: 1. RVS Institute of Management Studies & Computer PG Course(s) Application, Kallikuppam, Thiruvettakudi, Kottucherry Commune, MBA (F T) 60 60 Karaikal 609 609 UT of Pondicherry TOTAL: 2008-2009 60 60 PON-001/MBA/2008-09 Dr. Ani Valanteena MBA., Ph.D. (HR) DOB: 15.06.1963 DOJ:02.06.2008 Ph. No.: 04368-263100 Fax No.: 04368-263100 E-Mail: [email protected] Website: Note: Errors and omissions if any, may immediately be brought to the attention of Advisor (E&T and M & T), AICTE Hqr, New Delhi Fax No.: 011-23724174 ALL INDIA COUNCIL FOR TECHNICAL EDUCATION STATUS OF APPROVAL FOR AICTE APPROVED INSTITUTIONS BEYOND THE ACADEMIC YEAR 2008-09 Region: Southern State: Tamilnadu S.No. Name & Address of the institutions/YOE/Status Course(s) Existing Approved Intake for Intake for 2008-09 2009-10 1. -

Thiruvarur District
THIRUVARUR DISTRICT 1 THIRUVARUR DISTRICT 1. Introduction Southwest winds that set in during April i) Geographical location of the district are strongest in June and continue till September. Northeast monsoon starts The district of Thiruvarur was during the month of October and blow till carved out as a separate district by January. Cyclonic storm with varying detaching Valangaiman Taluk from wind velocity affect once in 3 or 4 years Thanjavur District and Thiruvarur, during the month of November-December. Nannilam, Kudavasal, Needamangalam, Both these storms affect the plantation Mannargudi, Thirutturaippoondi Taluks crop. During Southwest monsoon the air from Nagappatinam District on is calm and undisturbed. The Northeast o o 01.01.1997. It lies between 10 20‘ and 11 monsoon which starts in October and ends o o 07’ North latitude and 79 15’ and 79 45’ in December contributes about 60% of the East longitude. The total area of the total annual rainfall. The Southwest district is 2,377 sq.km monsoon rains from June to September ii) Administrative profile and summer rains from March to May accounts equally for the rest of the annual There are 2 revenue divisions, 7 rainfall. taluks, 10 community development blocks, 3 municipalties, 7 town panchayats and Rainfall in mm 573 villages in Thiruvarur district. South West Normal 301.8 Actual 532.5 North East Minimum 665.4 Actual 1118.8 2. Resources availability i) Land resources Since the district is represented by Cauvery Deltaic Zone, sandy coastal alluvium is the predominant soil type in this district accounting for 56.78% and other types of soil cover 43.22% of the total area.