WAPT Documentation Release 2.1.0
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
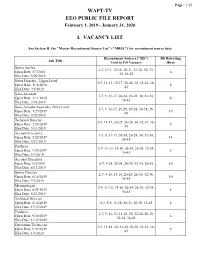
Wapt-Tv Eeo Public File Report I. Vacancy List
Page: 1/15 WAPT-TV EEO PUBLIC FILE REPORT February 1, 2019 - January 31, 2020 I. VACANCY LIST See Section II, the "Master Recruitment Source List" ("MRSL") for recruitment source data Recruitment Sources ("RS") RS Referring Job Title Used to Fill Vacancy Hiree Sports Anchor 2-3, 5-13, 15-16, 20-21, 23-28, 30, 32- Open Date: 5/7/2018 6 34, 36-45 Hire Date: 5/29/2019 News Director - Upper Level 2-9, 11-13, 15-17, 20-28, 30, 32-34, 36- Open Date: 11/6/2018 8 45 Hire Date: 3/3/2019 Sales Assistant 1-7, 9, 11-17, 20-24, 26-28, 30, 32-34, Open Date: 1/11/2019 6 36-45 Hire Date: 3/18/2019 Sales Account Associate- Entry Level 1-7, 9, 11-17, 19-24, 26-28, 30-34, 36- Open Date: 1/29/2019 19 45 Hire Date: 5/20/2019 Technical Director 2-9, 11-17, 20-24, 26-28, 30, 32-34, 36- Open Date: 2/25/2019 8 45 Hire Date: 5/13/2019 Account Executive 1-7, 9, 11-17, 20-24, 26-28, 30, 32-34, Open Date: 2/28/2019 14 36-45 Hire Date: 5/27/2019 Producer 2-9, 11-13, 15-18, 20-24, 26-30, 32-34, Open Date: 4/26/2019 8 36-45 Hire Date: 9/1/2019 Account Executive Open Date: 6/5/2019 1-7, 9-18, 20-24, 26-30, 32-34, 36-45 10 Hire Date: 8/12/2019 Sports Director 2-7, 9-13, 15-18, 20-24, 26-30, 32-34, Open Date: 6/18/2019 10 36-45 Hire Date: 9/3/2019 Meteorologist 2-9, 11-13, 15-18, 20-24, 26-30, 32-34, Open Date: 6/21/2019 8 36-45 Hire Date: 8/23/2019 Technical Director Open Date: 8/12/2019 2-3, 5-9, 11-18, 20-23, 26-30, 32-45 8 Hire Date: 11/11/2019 Producer 1-7, 9, 11-13, 15-18, 20, 22-24, 26-30, Open Date: 9/30/2019 6 32-34, 36-45 Hire Date: 11/11/2019 Operations Technician 2-9, 11-18, 20, 22-24, 26-30, 32-34, 36- Open Date: 9/30/2019 8 45 Hire Date: 1/3/2020 Page: 2/15 WAPT-TV EEO PUBLIC FILE REPORT February 1, 2019 - January 31, 2020 II. -
Entertainment & Syndication Fitch Group Hearst Health Hearst Television Magazines Newspapers Ventures Real Estate & O
hearst properties WPBF-TV, West Palm Beach, FL SPAIN Friendswood Journal (TX) WYFF-TV, Greenville/Spartanburg, SC Hardin County News (TX) entertainment Hearst España, S.L. KOCO-TV, Oklahoma City, OK Herald Review (MI) & syndication WVTM-TV, Birmingham, AL Humble Observer (TX) WGAL-TV, Lancaster/Harrisburg, PA SWITZERLAND Jasper Newsboy (TX) CABLE TELEVISION NETWORKS & SERVICES KOAT-TV, Albuquerque, NM Hearst Digital SA Kingwood Observer (TX) WXII-TV, Greensboro/High Point/ La Voz de Houston (TX) A+E Networks Winston-Salem, NC TAIWAN Lake Houston Observer (TX) (including A&E, HISTORY, Lifetime, LMN WCWG-TV, Greensboro/High Point/ Local First (NY) & FYI—50% owned by Hearst) Winston-Salem, NC Hearst Magazines Taiwan Local Values (NY) Canal Cosmopolitan Iberia, S.L. WLKY-TV, Louisville, KY Magnolia Potpourri (TX) Cosmopolitan Television WDSU-TV, New Orleans, LA UNITED KINGDOM Memorial Examiner (TX) Canada Company KCCI-TV, Des Moines, IA Handbag.com Limited Milford-Orange Bulletin (CT) (46% owned by Hearst) KETV, Omaha, NE Muleshoe Journal (TX) ESPN, Inc. Hearst UK Limited WMTW-TV, Portland/Auburn, ME The National Magazine Company Limited New Canaan Advertiser (CT) (20% owned by Hearst) WPXT-TV, Portland/Auburn, ME New Canaan News (CT) VICE Media WJCL-TV, Savannah, GA News Advocate (TX) HEARST MAGAZINES UK (A+E Networks is a 17.8% investor in VICE) WAPT-TV, Jackson, MS Northeast Herald (TX) VICELAND WPTZ-TV, Burlington, VT/Plattsburgh, NY Best Pasadena Citizen (TX) (A+E Networks is a 50.1% investor in VICELAND) WNNE-TV, Burlington, VT/Plattsburgh, -

Pyqgis Testing Developer Cookbook
PyQGIS testing developer cookbook QGIS Project Sep 25, 2021 CONTENTS 1 Introduction 1 1.1 Scripting in the Python Console ................................... 1 1.2 Python Plugins ............................................ 2 1.2.1 Processing Plugins ...................................... 3 1.3 Running Python code when QGIS starts ............................... 3 1.3.1 The startup.py file ................................... 3 1.3.2 The PYQGIS_STARTUP environment variable ...................... 3 1.4 Python Applications ......................................... 3 1.4.1 Using PyQGIS in standalone scripts ............................. 4 1.4.2 Using PyQGIS in custom applications ............................ 5 1.4.3 Running Custom Applications ................................ 5 1.5 Technical notes on PyQt and SIP ................................... 6 2 Loading Projects 7 2.1 Resolving bad paths .......................................... 8 3 Loading Layers 9 3.1 Vector Layers ............................................. 9 3.2 Raster Layers ............................................. 12 3.3 QgsProject instance .......................................... 14 4 Accessing the Table Of Contents (TOC) 15 4.1 The QgsProject class ......................................... 15 4.2 QgsLayerTreeGroup class ...................................... 16 5 Using Raster Layers 19 5.1 Layer Details ............................................. 19 5.2 Renderer ............................................... 20 5.2.1 Single Band Rasters .................................... -

Federal Register/Vol. 85, No. 103/Thursday, May 28, 2020
32256 Federal Register / Vol. 85, No. 103 / Thursday, May 28, 2020 / Proposed Rules FEDERAL COMMUNICATIONS closes-headquarters-open-window-and- presentation of data or arguments COMMISSION changes-hand-delivery-policy. already reflected in the presenter’s 7. During the time the Commission’s written comments, memoranda, or other 47 CFR Part 1 building is closed to the general public filings in the proceeding, the presenter [MD Docket Nos. 19–105; MD Docket Nos. and until further notice, if more than may provide citations to such data or 20–105; FCC 20–64; FRS 16780] one docket or rulemaking number arguments in his or her prior comments, appears in the caption of a proceeding, memoranda, or other filings (specifying Assessment and Collection of paper filers need not submit two the relevant page and/or paragraph Regulatory Fees for Fiscal Year 2020. additional copies for each additional numbers where such data or arguments docket or rulemaking number; an can be found) in lieu of summarizing AGENCY: Federal Communications original and one copy are sufficient. them in the memorandum. Documents Commission. For detailed instructions for shown or given to Commission staff ACTION: Notice of proposed rulemaking. submitting comments and additional during ex parte meetings are deemed to be written ex parte presentations and SUMMARY: In this document, the Federal information on the rulemaking process, must be filed consistent with section Communications Commission see the SUPPLEMENTARY INFORMATION 1.1206(b) of the Commission’s rules. In (Commission) seeks comment on several section of this document. proceedings governed by section 1.49(f) proposals that will impact FY 2020 FOR FURTHER INFORMATION CONTACT: of the Commission’s rules or for which regulatory fees. -
Free Open Source Vnc
Free open source vnc click here to download TightVNC - VNC-Compatible Remote Control / Remote Desktop Software. free for both personal and commercial usage, with full source code available. TightVNC - VNC-Compatible Remote Control / Remote Desktop Software. It's completely free but it does not allow integration with closed-source products. UltraVNC: Remote desktop support software - Remote PC access - remote desktop connection software - VNC Compatibility - FileTransfer - Encryption plugins - Text chat - MS authentication. This leading-edge, cloud-based program offers Remote Monitoring & Management, Remote Access &. Popular open source Alternatives to VNC Connect for Linux, Windows, Mac, Self- Hosted, BSD and Free Open Source Mac Windows Linux Android iPhone. Download the original open source version of VNC® remote access technology. Undeniably, TeamViewer is the best VNC in the market. Without further ado, here are 8 free and some are open source VNC client/server. VNC remote access software, support server and viewer software for on demand remote computer support. Remote desktop support software for remote PC control. Free. All VNCs Start from the one piece of source (See History of VNC), and. TigerVNC is a high- performance, platform-neutral implementation of VNC (Virtual Network Computing), Besides the source code we also provide self-contained binaries for bit and bit Linux, installers for Current list of open bounties. VNC (Virtual Network Computing) software makes it possible to view and fully- interact with one computer from any other computer or mobile. Find other free open source alternatives for VNC. Open source is free to download and remember that open source is also a shareware and freeware alternative. -

Guide Pédagogique
2de SCIENCES NUMÉRIQUES ET TECHNOLOGIE GUIDE PÉDAGOGIQUE foucherconnect.fr Dans ce manuel, des ressources en accès direct pour tous SCIENCES NUMÉRIQUES ET TECHNOLOGIE 2de GUIDE PÉDAGOGIQUE Coordination : Dominique Lescar Cédric Blivet, professeur de sciences de l’ingénieur, lycée Gustave Monod Enghien-les-Bains (95) Fabrice Danes, professeur de sciences de l’ingénieur, lycée Pierre Mendès-France, Rennes (35) Hassan Dibesse, professeur de sciences de l’ingénieur, lycée Lesage, Vannes (56) Patricia Kerner, professeure de sciences de l’ingénieur, lycée Yves Thépot, Quimper (29) Yannig Salaun, professeur de mathématiques, lycée de l’Élorn, Landerneau (29) Édition : Emmanuelle Mary Mise en page : Grafatom « Le photocopillage, c’est l’usage abusif et collectif de la photocopie sans auto- risation des auteurs et des éditeurs. Largement répandu dans les établissements d’enseignement, le photocopillage menace l’avenir du livre, car il met en danger son équilibre économique. Il prive les auteurs d’une juste rémunération. En dehors de l’usage privé du copiste, toute reproduction totale ou partielle de cet ouvrage est interdite. » ISBN : 978-2-216-15505-7 Toute reproduction ou représentation intégrale ou partielle, par quelque procédé que ce soit, des pages publiées dans le présent ouvrage, faite sans autorisation de l’éditeur ou du Centre français du Droit de copie (20, rue des Grands-Augustins, 75006 Paris), est illicite et constitue une contrefaçon. Seules sont autorisées, d’une part, les reproductions strictement réservées à l’usage privé du copiste et non destinées à une utilisation collective, et, d’autre part, les analyses et courtes citations justifiées par le caractère scien- tifique ou d’information de l’œuvre dans laquelle elles sont incorporées (Loi du 1er juillet 1992 - art. -
“Saved with a Click” from National Capital Freenet
“Saved with a Click” From National Capital FreeNet With thanks to the City of Ottawa's Community Economic Development Funding Program Open Source software “From free and robust operating systems to free software that can work on your existing system” You may already be using free software! Like Firefox: What is free software? Types of software: • Proprietary software – costs money, (like Microsoft Office) • Proprietary freeware, given away for free (like Google Chrome) • Proprietary shareware: ◦ Adware - has adverting ◦ Crippleware – downgraded version ◦ Trialware – limited time use (i.e. 30 day free trial) ◦ Nagware – free, but bugs you to pay for it regularly ◦ Freemium – free version with limited features, full version available for a cost (Like Kaspersky Anti-Virus or AVG AntiVirus Free) Free Software Free Software Foundation definition: • The freedom to run the program as you wish, for any purpose (freedom 0) • The freedom to study how the program works, and change it so it does your computing as you wish (freedom 1). Access to the source code is a precondition for this. • The freedom to redistribute copies so you can help others (freedom 2). • The freedom to distribute copies of your modified versions to others (freedom 3). By doing this you can give the whole community a chance to benefit from your changes. Access to the source code is a precondition for this. Free Licences Examples: • Gnu Public Licence • BSD Licence • Mozilla Public License • Many others • Licensing matters! Who Cares? The case of Skype: • Skype is voice, text and video communication software for talking to people, that was created by Niklas Zennström of Sweden and the Janus Friis of Denmark, in cooperation with Ahti Heinla, Priit Kasesalu and Jaan Tallinn, both of Estonia. -

Το Παιχνιδι ‘Binary Droids’»
Α ΡΙΣΤΟΤΕΛΕΙΟ Π ΑΝΕΠΙΣΤΗΜΙΟ Θ ΕΣΣΑΛΟΝΙΚΗΣ ΣΧΟΛΗ ΘΕΤΙΚΩΝ ΕΠΙΣΤΗΜΩΝ ΤΜΗΜΑ ΠΛΗΡΟΦΟΡΙΚΗΣ ΠΤΥΧΙΑΚΗ ΕΡΓΑΣΙΑ ΣΤΡΑΝΤΖΗ ΑΝΤΩΝΙΑ Α.Ε.Μ. 2090 «ΑΝΑΠΤΥΞΗ ΠΑΙΧΝΙΔΙΩΝ ΜΑΘΗΣΗΣ ΣΕ ΓΛΩΣΣΑ PYTHON: ΤΟ ΠΑΙΧΝΙΔΙ ‘BINARY DROIDS’» (Learning Games Development in Python: The ‘Binary Droids’ Game) ΕΠΙΒΛΕΠΩΝ ΚΑΘΗΓΗΤΗΣ: ΔΗΜΗΤΡΙΑΔΗΣ ΣΤΑΥΡΟΣ Επ. Καθηγητής ΘΕΣΣΑΛΟΝΙΚΗ 2015 ΠΕΡΙΛΗΨΗ Π ΕΡΙΛΗΨΗ Αντικείμενο της παρούσας εργασίας είναι η παιχνιδοκεντρική μάθηση και η ανάπτυξη ενός εκπαιδευτικού παιχνιδιού. Με την ανάπτυξη της τεχνολογίας στις μέρες μας, η διαδικασία της εκπαίδευσης και της μάθησης έχουν αλλάξει δραματικά. Η μάθηση δεν είναι πλέον μια κλασσική διαδικασία που στηρίζεται μόνο στα βιβλία. Η εργασία ασχολείται με την παιχνιδοκεντρική μάθηση και τη χρήση των παιχνιδιών σε αυτή τη διαδικασία, ενώ περιγράφεται και η ανάπτυξη ενός τέτοιου εκπαιδευτικού παιχνιδιού. Στο πρώτο μέρος περιγράφεται η έννοια της παιχνιδοκεντρικής μάθησης, εκείνης της διαδικασίας μάθησης που χρησιμοποιεί ως μηχανισμό το παιχνίδι. Επίσης περιγράφονται οι διάφορες κατηγορίες εκπαιδευτικών παιχνιδιών. Στο δεύτερο μέρος γίνεται αναφορά στη γλώσσα Python, το μοντέλο εκτέλεσής της και την ιστορία της. Έπειτα γίνεται αναφορά στη βιβλιοθήκη Pygame και στα εργαλεία που χρησιμοποιήθηκαν στην ανάπτυξη του παιχνιδιού. Στο τρίτο μέρος της εργασίας αναλύεται η υλοποίηση ενός εκπαιδευτικού ψηφιακού παιχνιδιού με τίτλο «Binary Droids», υλοποιημένο σε Python, με χρήση της Pygame. Το παιχνίδι έχει σκοπό την εκμάθηση μιας βασικής έννοιας της Πληροφορικής, αυτήν του δυαδικού συστήματος αρίθμησης, και της μετατροπής αριθμών από το δυαδικό σύστημα στο γνωστό σε όλους δεκαδικό. Το παιχνίδι χρησιμοποιεί επιβραβεύσεις και ποινές, όταν ο χρήστης εκτελεί τις μετατροπές των αριθμών σωστά και όταν τις εκτελεί λάθος, αντίστοιχα. Όσο ο χρήστης επιβραβεύεται για τις επιδόσεις του στο παιχνίδι, ανεβαίνει επίπεδα και συνεπώς αυξάνεται και η δυσκολία. -

Hearst Television Inc
HEARST TELEVISION INC 175 198 194 195 203 170 197 128 201 DR. OZ 3RD QUEEN QUEEN MIND OF A SEINFELD 4TH SEINFELD 5TH DR. OZ CYCLE LATIFAH LATIFAH MAN CYCLE CYCLE KING 2nd Cycle KING 3rd Cycle RANK MARKET %US STATION 2011-2014 2014-2015 2013-2014 2014-2015 2015-2016 4th Cycle 5th Cycle 2nd Cycle 3rd Cycle 7 BOSTON (MANCHESTER) MA 2.13% WCVB/WMUR WFXT WFXT WBZ/WSBK WBZ/WSBK WBZ/WSBK WBZ/WSBK WBZ/WSBK WBZ/WSBK 13 TAMPA-ST PETERSBURG (SARASOTA) FL 1.60% WMOR WFLA WFTS WTOG WTOG WTTA WTTA WTOG WTOG 18 ORLANDO-DAYTONA BEACH-MELBOURNE FL 1.29% WESH/WKCF WFTV/WRDQ WOFL/WRBW WKMG WKMG WESH/WKCF WFTV/WRDQ WFTV/WRDQ WFTV/WRDQ 20 SACRAMENTO-STOCKTON-MODESTO CA 1.18% KCRA/KCRA-DT2/KQCA KCRA/KQCA KCRA/KQCA KMAX/KOVR KMAX/KOVR KTXL KTXL KMAX/KOVR 22 PITTSBURGH PA 1.03% WTAE WTAE WTAE KDKA/WPCW KDKA/WPCW WPGH/WPMY WPGH/WPMY KDKA/WPCW KDKA/WPCW 26 BALTIMORE MD 0.96% WBAL/WBAL-DT2 WBAL WBAL WBFF/WNUV/WUTB WBFF/WNUV/WUTB WBFF/WNUV/WUTB WBFF/WNUV WBFF/WNUV 31 KANSAS CITY MO 0.81% KCWE/KMBC KCWE/KMBC KCWE/KMBC WDAF WDAF WDAF WDAF KMCI/KSHB KMCI 35 MILWAUKEE WI 0.79% WISN WISN WISN WDJT/WMLW WDJT/WMLW WITI WITI WCGV/WVTV 36 CINCINNATI OH 0.77% WLWT WLWT WLWT WLWT WKRC/WSTR EKRC/WKRC EKRC/WKRC/WSTR WXIX WXIX 37 GREENVILLE-SPARTANBURG (SC)-ASHEVILLE 0.74% WYFF WYFF WYFF WLOS/WMYA WLOS/WMYA WSPA/WYCW WSPA/WYCW WYCW WSPA/WYCW 38 WEST PALM BEACH-FT PIERCE FL 0.69% WPBF WPBF WPBF WPTV WPTV WFLX WFLX WTCN/WTVX 43 BIRMINGHAM (ANNISTON-TUSCALOOSA) AL 0.62% WVTM WBMA WBMA WBRC WBRC WABM/WTTO WABM/WTTO WABM/WTTO 44 OKLAHOMA CITY OK 0.62% KOCO KOCO KOCO KOCB/KOKH KOCB/KOKH -

Laura Tateosian Python for Arcgis Python for Arcgis
Laura Tateosian Python For ArcGIS Python For ArcGIS Laura Tateosian Python For ArcGIS Laura Tateosian North Carolina State University Raleigh , NC , USA ISBN 978-3-319-18397-8 ISBN 978-3-319-18398-5 (eBook) DOI 10.1007/978-3-319-18398-5 Library of Congress Control Number: 2015943490 Springer Cham Heidelberg New York Dordrecht London © Springer International Publishing Switzerland 2015 This work is subject to copyright. All rights are reserved by the Publisher, whether the whole or part of the material is concerned, specifi cally the rights of translation, reprinting, reuse of illustrations, recitation, broadcasting, reproduction on microfi lms or in any other physical way, and transmission or information storage and retrieval, electronic adaptation, computer software, or by similar or dissimilar methodology now known or hereafter developed. The use of general descriptive names, registered names, trademarks, service marks, etc. in this publication does not imply, even in the absence of a specifi c statement, that such names are exempt from the relevant protective laws and regulations and therefore free for general use. The publisher, the authors and the editors are safe to assume that the advice and information in this book are believed to be true and accurate at the date of publication. Neither the publisher nor the authors or the editors give a warranty, express or implied, with respect to the material contained herein or for any errors or omissions that may have been made. Esri images are used by permission. Copyright © 2015 Esri. All rights reserved. Python is copyright the Python Software Foundation. Used by permission. PyScripter is an OpenSource software authored by Kiriakos Vlahos. -

HEARST PROPERTIES HUNGARY HEARST MAGAZINES UK Hearst Central Kft
HEARST PROPERTIES HUNGARY HEARST MAGAZINES UK Hearst Central Kft. (50% owned by Hearst) All About Soap ITALY Best Cosmopolitan NEWSPAPERS MAGAZINES Hearst Magazines Italia S.p.A. Country Living Albany Times Union (NY) H.M.C. Italia S.r.l. (49% owned by Hearst) Car and Driver ELLE Beaumont Enterprise (TX) Cosmopolitan JAPAN ELLE Decoration Connecticut Post (CT) Country Living Hearst Fujingaho Co., Ltd. Esquire Edwardsville Intelligencer (IL) Dr. Oz THE GOOD LIFE Greenwich Time (CT) KOREA Good Housekeeping ELLE Houston Chronicle (TX) Hearst JoongAng Y.H. (49.9% owned by Hearst) Harper’s BAZAAR ELLE DECOR House Beautiful Huron Daily Tribune (MI) MEXICO Laredo Morning Times (TX) Esquire Inside Soap Hearst Expansion S. de R.L. de C.V. Midland Daily News (MI) Food Network Magazine Men’s Health (50.1% owned by Hearst UK) (51% owned by Hearst) Midland Reporter-Telegram (TX) Good Housekeeping Prima Plainview Daily Herald (TX) Harper’s BAZAAR NETHERLANDS Real People San Antonio Express-News (TX) HGTV Magazine Hearst Magazines Netherlands B.V. Red San Francisco Chronicle (CA) House Beautiful Reveal The Advocate, Stamford (CT) NIGERIA Marie Claire Runner’s World (50.1% owned by Hearst UK) The News-Times, Danbury (CT) HMI Africa, LLC O, The Oprah Magazine Town & Country WEBSITES Popular Mechanics NORWAY Triathlete’s World Seattlepi.com Redbook HMI Digital, LLC (50.1% owned by Hearst UK) Road & Track POLAND Women’s Health WEEKLY NEWSPAPERS Seventeen Advertiser North (NY) Hearst-Marquard Publishing Sp.z.o.o. (50.1% owned by Hearst UK) Town & Country Advertiser South (NY) (50% owned by Hearst) VERANDA MAGAZINE DISTRIBUTION Ballston Spa/Malta Pennysaver (NY) Woman’s Day RUSSIA Condé Nast and National Magazine Canyon News (TX) OOO “Fashion Press” (50% owned by Hearst) Distributors Ltd. -

Cognitive Model of the Closed Environment of a Mobile Robot Based on Measurements
Article Cognitive Model of the Closed Environment of a Mobile Robot Based on Measurements Tomislav Pavlic 1,*, Krunoslav Kušec 1, Danijel Radočaj 1, Alen Britvić 1, Marin Lukas 2, Vladimir Milić 2 and Mladen Crneković 2 1 Mechatronics Department, Bjelovar University of Applied Sciences, 43000 Bjelovar, Croatia; [email protected] (K.K.); [email protected] (D.R.); [email protected] (A.B.) 2 Faculty of Mechanical Engineering and Naval Architecture, University of Zagreb, 10000 Zagreb, Croatia; [email protected] (M.L.); [email protected] (V.M.); [email protected] (M.C.) * Correspondence: [email protected]; Tel.: +385-43-241-204 Abstract: In recent years in mobile robotics, the focus has been on methods, in which the fusion of measurement data from various systems leads to models of the environment that are of a probabil- istic type. The cognitive model of the environment is less accurate than the exact mathematical one, but it is unavoidable in the robot collaborative interaction with a human. The subject of the research proposed in this paper is the development of a model for learning and planning robot operations. The task of operations and mapping the unknown environment, similar to how humans do the same tasks in the same conditions has been explored. The learning process is based on a virtual dynamic model of a mobile robot, identical to a real mobile robot. The mobile robot’s motion with developed artificial neural networks and genetic algorithms is defined. The transfer method of obtained knowledge from simulated to a real system (Sim-To-Real; STR) is proposed.