IPS Signature Release Note V9.17.78
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Presentation Slides
ColdBox Platform 4.0 AND BEYOND Who am I? ● ColdFusion Architect (12 years) ● Geek ● Android Lover ● Blogger (codersrevolution.com) ● ColdBox Platform Evangelist ● Musician ● Shade-Tree Mechanic ● Husband (11 years) ● Dad (3 beautiful girls) What we will cover? History of ColdBox What is ColdBox? Why ColdBox? Major ColdBox Parts Demos History & Facts Did not start as open source Designed and built for a high availability application in 2005 1st Conventions CFML Framework in 2006 30 releases -> 3.8.1 Active roadmap, collaboration & development High-profile company adoptions Community Large and Active Community Incredible download rates Mailing List & Forums growth Many hours of video training ForgeBox : *Box CFML Community! Share modules, plugins, interceptors, contentbox, etc Professional Open Source Company backing and funding Professional Training Courses Books Support & Mentoring Plans Architecture & Design Sessions Server Tuning & Optimizations Code Reviews & Sanity Checks Dancing lessons Why use a framework? Common Vocabulary Separation of Concerns Tested in multiple environments Performance-tuned Reduces ramp up time for new developers Do not reinvent the wheel Should address most infrastructure concerns Increases Maintainability, Scalability, and keeps your sanity! What is ColdBox? A place for root beer? “Address most infrastructure concerns of typical ColdFusion applications” How we build our apps? Usually start with a need for MVC Requirements are more than just MVC MVC is not enough What about? SES/URL Mappings RESTful Services -
![Ispconfig 3 Manual]](https://docslib.b-cdn.net/cover/9381/ispconfig-3-manual-89381.webp)
Ispconfig 3 Manual]
[ISPConfig 3 Manual] ISPConfig 3 Manual Version 1.0 for ISPConfig 3.0.3 Author: Falko Timme <[email protected]> Last edited 09/30/2010 1 The ISPConfig 3 manual is protected by copyright. No part of the manual may be reproduced, adapted, translated, or made available to a third party in any form by any process (electronic or otherwise) without the written specific consent of projektfarm GmbH. You may keep backup copies of the manual in digital or printed form for your personal use. All rights reserved. This copy was issued to: Thomas CARTER - [email protected] - Date: 2010-11-20 [ISPConfig 3 Manual] ISPConfig 3 is an open source hosting control panel for Linux and is capable of managing multiple servers from one control panel. ISPConfig 3 is licensed under BSD license. Managed Services and Features • Manage one or more servers from one control panel (multiserver management) • Different permission levels (administrators, resellers and clients) + email user level provided by a roundcube plugin for ISPConfig • Httpd (virtual hosts, domain- and IP-based) • FTP, SFTP, SCP • WebDAV • DNS (A, AAAA, ALIAS, CNAME, HINFO, MX, NS, PTR, RP, SRV, TXT records) • POP3, IMAP • Email autoresponder • Server-based mail filtering • Advanced email spamfilter and antivirus filter • MySQL client-databases • Webalizer and/or AWStats statistics • Harddisk quota • Mail quota • Traffic limits and statistics • IP addresses 2 The ISPConfig 3 manual is protected by copyright. No part of the manual may be reproduced, adapted, translated, or made available to a third party in any form by any process (electronic or otherwise) without the written specific consent of projektfarm GmbH. -

THE FUTURE of SCREENS from James Stanton a Little Bit About Me
THE FUTURE OF SCREENS From james stanton A little bit about me. Hi I am James (Mckenzie) Stanton Thinker / Designer / Engineer / Director / Executive / Artist / Human / Practitioner / Gardner / Builder / and much more... Born in Essex, United Kingdom and survived a few hair raising moments and learnt digital from the ground up. Ok enough of the pleasantries I have been working in the design field since 1999 from the Falmouth School of Art and onwards to the RCA, and many companies. Ok. less about me and more about what I have seen… Today we are going to cover - SCREENS CONCEPTS - DIGITAL TRANSFORMATION - WHY ASSETS LIBRARIES - CODE LIBRARIES - COST EFFECTIVE SOLUTION FOR IMPLEMENTATION I know, I know, I know. That's all good and well, but what does this all mean to a company like mine? We are about to see a massive change in consumer behavior so let's get ready. DIGITAL TRANSFORMATION AS A USP Getting this correct will change your company forever. DIGITAL TRANSFORMATION USP-01 Digital transformation (DT) – the use of technology to radically improve performance or reach of enterprises – is becoming a hot topic for companies across the globe. VERY DIGITAL CHANGING NOT VERY DIGITAL DIGITAL TRANSFORMATION USP-02 Companies face common pressures from customers, employees and competitors to begin or speed up their digital transformation. However they are transforming at different paces with different results. VERY DIGITAL CHANGING NOT VERY DIGITAL DIGITAL TRANSFORMATION USP-03 Successful digital transformation comes not from implementing new technologies but from transforming your organisation to take advantage of the possibilities that new technologies provide. -
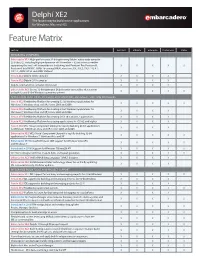
Delphi XE2 Feature Matrix
Delphi® XE2 The fastest way to build native applications for Windows, Mac and iOS Feature Matrix Feature Architect Ultimate Enterprise Professional Starter INTEGRATED COMPILERS Enhanced in XE2! High-performance 32-bit optimizing Delphi® native code compiler 23.0 (dcc32), including High performance x86 Assembler – 32-bit inline assembler supporting the Intel® x86 instruction set (including Intel Pentium® Pro, Pentium III, X X X X X Pentium 4, Intel MMX™, SIMD, Streaming SIMD Extensions, SSE, SSE2, SSE3, SSE 4.1, SSE 4.2, AMD SSE4A and AMD® 3DNow!® New in XE2! Delphi 64-bit compiler X X X X New in XE2! Delphi OS X compiler X X X X Delphi command line compiler (dcc32.exe) X X X X Enhanced in XE2! Create 32-bit optimized Delphi native executables that can run X X X X X on both 32 and 64-bit Windows operating systems APPLICATION PLATFORMS, INTEGRATED FRAMEWORKS, DESIGNERS, SDKS AND INSTALLERS New in XE2! FireMonkey Platform for creating 32-bit Windows applications for X X X X X Windows 7, Windows Vista and XP; Server 2003 and 2008. New in XE2! FireMonkey Platform for creating 64-bit Windows applications for X X X X Windows 7, Windows Vista and XP; Server 2003 and 2008. New in XE2! FireMonkey Platform for creating OS X 10.6 and 10.7 applications X X X X New in XE2! FireMonkey Platform for creating applications for iOS 4.2 and higher X X X X New in XE2! VCL (Visual Component Library) for rapidly building 64-bit applications X X X X for Windows 7,Windows Vista and XP; Server 2003 and 2008. -

Web Vulnerabilities (Level 1 Scan)
Web Vulnerabilities (Level 1 Scan) Vulnerability Name CVE CWE Severity .htaccess file readable CWE-16 ASP code injection CWE-95 High ASP.NET MVC version disclosure CWE-200 Low ASP.NET application trace enabled CWE-16 Medium ASP.NET debugging enabled CWE-16 Low ASP.NET diagnostic page CWE-200 Medium ASP.NET error message CWE-200 Medium ASP.NET padding oracle vulnerability CVE-2010-3332 CWE-310 High ASP.NET path disclosure CWE-200 Low ASP.NET version disclosure CWE-200 Low AWStats script CWE-538 Medium Access database found CWE-538 Medium Adobe ColdFusion 9 administrative login bypass CVE-2013-0625 CVE-2013-0629CVE-2013-0631 CVE-2013-0 CWE-287 High 632 Adobe ColdFusion directory traversal CVE-2013-3336 CWE-22 High Adobe Coldfusion 8 multiple linked XSS CVE-2009-1872 CWE-79 High vulnerabilies Adobe Flex 3 DOM-based XSS vulnerability CVE-2008-2640 CWE-79 High AjaxControlToolkit directory traversal CVE-2015-4670 CWE-434 High Akeeba backup access control bypass CWE-287 High AmCharts SWF XSS vulnerability CVE-2012-1303 CWE-79 High Amazon S3 public bucket CWE-264 Medium AngularJS client-side template injection CWE-79 High Apache 2.0.39 Win32 directory traversal CVE-2002-0661 CWE-22 High Apache 2.0.43 Win32 file reading vulnerability CVE-2003-0017 CWE-20 High Apache 2.2.14 mod_isapi Dangling Pointer CVE-2010-0425 CWE-20 High Apache 2.x version equal to 2.0.51 CVE-2004-0811 CWE-264 Medium Apache 2.x version older than 2.0.43 CVE-2002-0840 CVE-2002-1156 CWE-538 Medium Apache 2.x version older than 2.0.45 CVE-2003-0132 CWE-400 Medium Apache 2.x version -
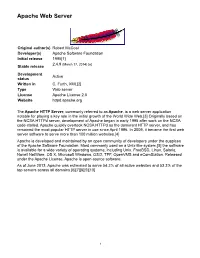
Apache Web Server ______
Apache Web Server _____________________________________________________________________________________________________ Original author(s) Robert McCool Developer(s) Apache Software Foundation Initial release 1995[1] 2.4.9 (March 17, 2014) [±] Stable release Development Active status Written in C, Forth, XML[2] Type Web server License Apache License 2.0 Website httpd.apache.org The Apache HTTP Server , commonly referred to as Apache , is a web server application notable for playing a key role in the initial growth of the World Wide Web.[3] Originally based on the NCSA HTTPd server, development of Apache began in early 1995 after work on the NCSA code stalled. Apache quickly overtook NCSA HTTPd as the dominant HTTP server, and has remained the most popular HTTP server in use since April 1996. In 2009, it became the first web server software to serve more than 100 million websites.[4] Apache is developed and maintained by an open community of developers under the auspices of the Apache Software Foundation. Most commonly used on a Unix-like system,[5] the software is available for a wide variety of operating systems, including Unix, FreeBSD, Linux, Solaris, Novell NetWare, OS X, Microsoft Windows, OS/2, TPF, OpenVMS and eComStation. Released under the Apache License, Apache is open-source software. As of June 2013, Apache was estimated to serve 54.2% of all active websites and 53.3% of the top servers across all domains.[6][7][8][9][10] 1 Apache Web Server _____________________________________________________________________________________________________ Name According to the FAQ in the Apache project website, the name Apache was chosen out of respect to the Native American tribe Apache and its superior skills in warfare and strategy. -

A Requirements-Based Exploration of Open-Source Software Development Projects – Towards a Natural Language Processing Software Analysis Framework
Georgia State University ScholarWorks @ Georgia State University Computer Information Systems Dissertations Department of Computer Information Systems 8-7-2012 A Requirements-Based Exploration of Open-Source Software Development Projects – Towards a Natural Language Processing Software Analysis Framework Radu Vlas Georgia State University Follow this and additional works at: https://scholarworks.gsu.edu/cis_diss Recommended Citation Vlas, Radu, "A Requirements-Based Exploration of Open-Source Software Development Projects – Towards a Natural Language Processing Software Analysis Framework." Dissertation, Georgia State University, 2012. https://scholarworks.gsu.edu/cis_diss/48 This Dissertation is brought to you for free and open access by the Department of Computer Information Systems at ScholarWorks @ Georgia State University. It has been accepted for inclusion in Computer Information Systems Dissertations by an authorized administrator of ScholarWorks @ Georgia State University. For more information, please contact [email protected]. PERMISSION TO BORROW In presenting this dissertation as a partial fulfillment of the requirements for an advanced degree from Georgia State University, I agree that the Library of the University shall make it available for inspection and circulation in accordance with its regulations governing materials of this type. I agree that permission to quote from, to copy from, or publish this dissertation may be granted by the author or, in his/her absence, the professor under whose direction it was written or, in his absence, by the Dean of the Robinson College of Business. Such quoting, copying, or publishing must be solely for the scholarly purposes and does not involve potential financial gain. It is understood that any copying from or publication of this dissertation which involves potential gain will not be allowed without written permission of the author. -

Awstats Logfile Analyzer Documentation
AWStats logfile analyzer 7.4 Documentation Table of contents Release Notes Reference manual What is AWStats / Features Install, Setup and Use AWStats New Features / Changelog Configuration Directives/Options Upgrade Configuration for Extra Sections feature Contribs, plugins and resources Other provided utilities Glossary of terms Other Topics Comparison with other log analyzers FAQ and Troubleshooting Benchmarks AWStats License Plugin Developement AWStats modules for third tools AWStats module for Webmin AWStats module for Dolibarr ERP & CRM Table of contents 1/103 14/07/2015 AWStats logfile analyzer 7.4 Documentation What is AWStats / Features Overview AWStats is short for Advanced Web Statistics. AWStats is powerful log analyzer which creates advanced web, ftp, mail and streaming server statistics reports based on the rich data contained in server logs. Data is graphically presented in easy to read web pages. AWStats development started in 1997 and is still developed today by same author (Laurent Destailleur). However, development is now done on "maintenance fixes" or small new features. Reason is that author spend, since July 2008, most of his time as project leader on another major OpenSource projet called Dolibarr ERP & CRM and works also at full time for TecLib, a french Open Source company. A lot of other developers maintains the software, providing patches, or packages, above all for Linux distributions (fedora, debian, ubuntu...). Designed with flexibility in mind, AWStats can be run through a web browser CGI (common gateway interface) or directly from the operating system command line. Through the use of intermediary data base files, AWStats is able to quickly process large log files, as often desired. -

C++Builder XE5 Feature Matrix | Multi-Device, True Native App
C++Builder® XE5 Multi-device, true native app development with C++ Feature Matrix Feature Architect Ultimate Enterprise Professional Starter INTEGRATED COMPILERS AND TOOLCHAINS Introduced in XE3! C++ 64-bit compiler for Windows X X X X Enhanced in XE3! C++ OS X compiler X X X X Enhanced in XE5! Embarcadero C++ Compiler 6.70 (bcc64) X X X X Enhanced in XE5! Embarcadero C++ Compiler 6.70 (bcc32) X X X X Enhanced in XE3! C++ command line toolchains for Windows X X X X X Enhanced in XE3! C++ command line toolchains for OS X (bccosx) X X X X Create 32-bit optimized native executables that can run on both 32 X X X X X and 64-bit Windows operating systems Enhanced in XE3! ANSI/ISO C++11 and 99 Standard language X X X X conformance and Boost support for 64-bit #pragma once support that allows for better compatibility with MSVC X X X X X and also acts as a header guard [[deprecated]] attribute to flag constructs as deprecated X X X X X Build C++ packages for 32-bit applications X X X X X Secure C library functions X X X X X Enhanced compiler switches for XML representation of source code X X X X X Custom evaluators for C++ Strings types X X X X X Linker error handling to improve memory management flexibility and X X X X X resolution APPLICATION PLATFORMS, INTEGRATED FRAMEWORKS, DESIGNERS AND SDKS Enhanced in XE3! FM Application Platform for creating 32-bit Windows applications for Windows 8, Windows 7, Windows Vista and X X X X X XP; Server 2008 and 2012. -

Are Spiders Eating Your Servers? the Impact of Their Unexpected Load and How to Counter It
ARE SPIDERS EATING YOUR SERVERS? THE IMPACT OF THEIR UNEXPECTED LOAD AND HOW TO COUNTER IT Charlie Arehart, Independent Consultant CF Server Troubleshooter [email protected] @carehart (Tw, Fb, Li, Slack) Updated July 17, 2017 SOME INTRO QUESTIONS FOR YOU Good news: there are solutions to mitigate impact, perhaps reduce load That said, some automated requests are getting smarter, harder to control Beware: think your intranet/private/login-required site is safe from impact? We’ll cover all this and more in this talk THERE IS GOOD NEWS Focus on CF server troubleshooting, as an independent consultant Satisfaction guaranteed. More on rates, approach, etc at carehart.org/consulting Love to share info, with my clients and the community Contributor to/creator of many CF community resources Online CFMeetup, CF411.com, UGTV, CF911.com, CFUpdate.com, and more I’m also manning the Intergral (FusionReactor) booth for them ABOUT ME Understanding automated requests The nature of such automated requests (many, varied, not always friendly) How we can generally identify such requests Their generally unexpected volume The impact of such request volume, CF-specific and more generally Observing the volume in your environment Dealing with automated requests: tools and techniques Preventing undesirable ones Mitigating the impact of expected ones, CF-specifically and more generally Resources for more Slides at carehart.org/presentations TOPICS UNDERSTANDING AUTOMATED REQUESTS Of course most common automated agents are search engine crawlers The intent/approach of such search engine crawlers/bots/spiders There are many: Some legit and desirable (google, bing, yahoo, etc.) Some legit but maybe not your market: Yandex (Russian search engine), Baidu (China, also SoGou, Youdau), Goo (Japan), Naver (Korea), etc. -

Rad Studio 10.4.2 Product Feature Matrix
Each feature in the following table has an indication if it is available in Delphi and/or C++Builder . RAD Studio editions include both languages. Each column covers multiple, similar editions, with any difference specifically called out. Community edition1 is available only for single personalities and has a limited license. Some of the features are only available for download from the IDE in the GetIt Package Manager, requiring an Internet connection. TABLE OF CONTENTS INTEGRATED COMPILERS AND TOOLCHAINS APPLICATION PLATFORMS, INTEGRATED FRAMEWORKS, LICENSING AND TOOL MANAGEABILITY DESIGNERS AND SDKS FMX APPLICATION PLATFORM (FIREMONKEY) VISUAL COMPONENT LIBRARY (VCL) COM/DCOM SUPPORT INTERNET OF THINGS (IOT) SUPPORT VISUAL LIVEBINDINGS INTEGRATED BUILD TOOLS AND PROJECT SUPPORT RECENT C++ LANGUAGE AND CORE RTL FEATURES RECENT DELPHI LANGUAGE AND CORE RTL FEATURES INTEGRATED DEVELOPMENT ENVIRONMENT SHARED RUNTIME LIBRARY FEATURES AND DEVELOPER PRODUCTIVITY SOURCE CODE MANAGEMENT INTERNATIONAL DEVELOPMENT REFACTORINGS UML MODELING INTEGRATED DEBUGGING INTEGRATED UNIT TESTING INTEGRATED HELP DATABASE APPLICATION DEVELOPMENT AND CONNECTIVITY FIREDAC MULTI-DEVICE DATA ACCESS LIBRARY DBEXPRESS AND IBX RAD SERVER DATASNAP MULTI-TIER DATABASE TOOLS INCLUDED DATABASES REST CLIENT LIBRARY AND BAAS CLOUD SUPPORT XML AND SOAP IP*WORKS! COMMUNICATION COMPONENTS CONNECT TO REST APIS WITH ENTERPRISE CONNECTORS FILE COMPARE WITH BEYOND COMPARE TEXT COMPARE TEECHART CHARTING COMPONENTS LOGGING WITH CODESITE EXPRESS FASTREPORT REPORTING SOLUTIONS SENCHA EXT JS PROFESSIONAL EDITION AQUA DATA STUDIO 1 Community edition planned for a future 11.x release. Current available Community Edition version is 10.4.2. Community Edition doesn’t include some of the bonus features available in the GetIt package manager. RAD STUDIO 11 FEATURE MATRIX 2 PROFESSIONAL / ARCHITECT / FEATURE COMMUNITY1 ENTERPRISE INTEGRATED COMPILERS AND TOOLCHAINS Delphi 32-bit native code optimizing compiler (dcc32) and toolchain for Windows. -

B 0313 DEP1900000019 01.Pdf
The following documentation is an electronically‐ submitted vendor response to an advertised solicitation from the West Virginia Purchasing Bulletin within the Vendor Self‐Service portal at wvOASIS.gov. As part of the State of West Virginia’s procurement process, and to maintain the transparency of the bid‐opening process, this documentation submitted online is publicly posted by the West Virginia Purchasing Division at WVPurchasing.gov with any other vendor responses to this solicitation submitted to the Purchasing Division in hard copy format. Purchasing Division State of West Virginia 2019 Washington Street East Solicitation Response Post Office Box 50130 Charleston, WV 25305-0130 Proc Folder : 536470 Solicitation Description : Lucee Software Support Proc Type : Central Contract - Fixed Amt Date issued Solicitation Closes Solicitation Response Version 2019-02-26 SR 0313 ESR02211900000003842 1 13:30:00 VENDOR VS0000017430 RASIA INC Solicitation Number: CRFQ 0313 DEP1900000019 Total Bid : $2,747,100.00 Response Date: 2019-02-22 Response Time: 02:05:54 Comments: FOR INFORMATION CONTACT THE BUYER Jessica S Chambers (304) 558-0246 [email protected] Signature on File FEIN # DATE All offers subject to all terms and conditions contained in this solicitation Page : 1 FORM ID : WV-PRC-SR-001 Line Comm Ln Desc Qty Unit Issue Unit Price Ln Total Or Contract Amount 1 Lucee or Equal Support 110.00000 HOUR $24,750.000000 $2,722,500.00 Comm Code Manufacturer Specification Model # 81111811 Extended Description : Lucee or Equal Server Support, Application Development Support, and CFML Conversion from Adobe Cold Fusion to Lucee Support for one (1) year. Up to 110 hours total for all listed support.