A Minimal Set of Unix Commands Exit Logs You Off the System: ALWAYS
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Linux Kernel Module Programming Guide
The Linux Kernel Module Programming Guide Peter Jay Salzman Michael Burian Ori Pomerantz Copyright © 2001 Peter Jay Salzman 2007−05−18 ver 2.6.4 The Linux Kernel Module Programming Guide is a free book; you may reproduce and/or modify it under the terms of the Open Software License, version 1.1. You can obtain a copy of this license at http://opensource.org/licenses/osl.php. This book is distributed in the hope it will be useful, but without any warranty, without even the implied warranty of merchantability or fitness for a particular purpose. The author encourages wide distribution of this book for personal or commercial use, provided the above copyright notice remains intact and the method adheres to the provisions of the Open Software License. In summary, you may copy and distribute this book free of charge or for a profit. No explicit permission is required from the author for reproduction of this book in any medium, physical or electronic. Derivative works and translations of this document must be placed under the Open Software License, and the original copyright notice must remain intact. If you have contributed new material to this book, you must make the material and source code available for your revisions. Please make revisions and updates available directly to the document maintainer, Peter Jay Salzman <[email protected]>. This will allow for the merging of updates and provide consistent revisions to the Linux community. If you publish or distribute this book commercially, donations, royalties, and/or printed copies are greatly appreciated by the author and the Linux Documentation Project (LDP). -

Introduction to Linux – Part 1
Introduction to Linux – Part 1 Brett Milash and Wim Cardoen Center for High Performance Computing May 22, 2018 ssh Login or Interactive Node kingspeak.chpc.utah.edu Batch queue system … kp001 kp002 …. kpxxx FastX ● https://www.chpc.utah.edu/documentation/software/fastx2.php ● Remote graphical sessions in much more efficient and effective way than simple X forwarding ● Persistence - can be disconnected from without closing the session, allowing users to resume their sessions from other devices. ● Licensed by CHPC ● Desktop clients exist for windows, mac, and linux ● Web based client option ● Server installed on all CHPC interactive nodes and the frisco nodes. Windows – alternatives to FastX ● Need ssh client - PuTTY ● http://www.chiark.greenend.org.uk/~sgtatham/putty/download.html - XShell ● http://www.netsarang.com/download/down_xsh.html ● For X applications also need X-forwarding tool - Xming (use Mesa version as needed for some apps) ● http://www.straightrunning.com/XmingNotes/ - Make sure X forwarding enabled in your ssh client Linux or Mac Desktop ● Just need to open up a terminal or console ● When running applications with graphical interfaces, use ssh –Y or ssh –X Getting Started - Login ● Download and install FastX if you like (required on windows unless you already have PuTTY or Xshell installed) ● If you have a CHPC account: - ssh [email protected] ● If not get a username and password: - ssh [email protected] Shell Basics q A Shell is a program that is the interface between you and the operating system -

CS101 Lecture 9
How do you copy/move/rename/remove files? How do you create a directory ? What is redirection and piping? Readings: See CCSO’s Unix pages and 9-2 cp option file1 file2 First Version cp file1 file2 file3 … dirname Second Version This is one version of the cp command. file2 is created and the contents of file1 are copied into file2. If file2 already exits, it This version copies the files file1, file2, file3,… into the directory will be replaced with a new one. dirname. where option is -i Protects you from overwriting an existing file by asking you for a yes or no before it copies a file with an existing name. -r Can be used to copy directories and all their contents into a new directory 9-3 9-4 cs101 jsmith cs101 jsmith pwd data data mp1 pwd mp1 {FILES: mp1_data.m, mp1.m } {FILES: mp1_data.m, mp1.m } Copy the file named mp1_data.m from the cs101/data Copy the file named mp1_data.m from the cs101/data directory into the pwd. directory into the mp1 directory. > cp ~cs101/data/mp1_data.m . > cp ~cs101/data/mp1_data.m mp1 The (.) dot means “here”, that is, your pwd. 9-5 The (.) dot means “here”, that is, your pwd. 9-6 Example: To create a new directory named “temp” and to copy mv option file1 file2 First Version the contents of an existing directory named mp1 into temp, This is one version of the mv command. file1 is renamed file2. where option is -i Protects you from overwriting an existing file by asking you > cp -r mp1 temp for a yes or no before it copies a file with an existing name. -

Writing Your First Linux Kernel Module
Writing your first Linux kernel module Praktikum Kernel Programming University of Hamburg Scientific Computing Winter semester 2014/2015 Outline ● Before you start ● Hello world module ● Compile, load and unload ● User space VS. kernel space programing ● Summary Before you start ● Define your module’s goal ● Define your module behaviour ● Know your hardware specifications ○ If you are building a device driver you should have the manual ● Documentation ○ /usr/src/linux/Documentation ○ make { htmldocs | psdocs | pdfdocks | rtfdocks } ○ /usr/src/linux/Documentation/DocBook Role of the device driver ● Software layer between application and device “black boxes” ○ Offer abstraction ■ Make hardware available to users ○ Hide complexity ■ User does not need to know their implementation ● Provide mechanism not policy ○ Mechanism ■ Providing the flexibility and the ability the device supports ○ Policy ■ Controlling how these capabilities are being used Role of the device driver ● Policy-free characteristics ○ Synchronous and asynchronous operations ○ Exploit the full capabilities of the hardware ○ Often a client library is provided as well ■ Provides capabilities that do not need to be implemented inside the module Outline ● Before you start ● Hello world module ● Compile, load and unload ● User space VS. kernel space programing ● Summary Hello world module /* header files */ #include <linux/module.h> #include <linux/init.h> /* the initialization function */ /* the shutdown function */ static int __init hello_init(void) { static void __exit hello_exit(void) -

Name Synopsis Description
Perl version 5.10.0 documentation - vmsish NAME vmsish - Perl pragma to control VMS-specific language features SYNOPSIS use vmsish; use vmsish 'status';# or '$?' use vmsish 'exit'; use vmsish 'time'; use vmsish 'hushed'; no vmsish 'hushed'; vmsish::hushed($hush); use vmsish; no vmsish 'time'; DESCRIPTION If no import list is supplied, all possible VMS-specific features areassumed. Currently, there are four VMS-specific features available:'status' (a.k.a '$?'), 'exit', 'time' and 'hushed'. If you're not running VMS, this module does nothing. vmsish status This makes $? and system return the native VMS exit statusinstead of emulating the POSIX exit status. vmsish exit This makes exit 1 produce a successful exit (with status SS$_NORMAL),instead of emulating UNIX exit(), which considers exit 1 to indicatean error. As with the CRTL's exit() function, exit 0 is also mappedto an exit status of SS$_NORMAL, and any other argument to exit() isused directly as Perl's exit status. vmsish time This makes all times relative to the local time zone, instead of thedefault of Universal Time (a.k.a Greenwich Mean Time, or GMT). vmsish hushed This suppresses printing of VMS status messages to SYS$OUTPUT andSYS$ERROR if Perl terminates with an error status. and allowsprograms that are expecting "unix-style" Perl to avoid having to parseVMS error messages. It does not suppress any messages from Perlitself, just the messages generated by DCL after Perl exits. The DCLsymbol $STATUS will still have the termination status, but with ahigh-order bit set: EXAMPLE:$ perl -e"exit 44;" Non-hushed error exit%SYSTEM-F-ABORT, abort DCL message$ show sym $STATUS$STATUS == "%X0000002C" $ perl -e"use vmsish qw(hushed); exit 44;" Hushed error exit $ show sym $STATUS $STATUS == "%X1000002C" The 'hushed' flag has a global scope during compilation: the exit() ordie() commands that are compiled after 'vmsish hushed' will be hushedwhen they are executed. -

A Concurrent PASCAL Compiler for Minicomputers
512 Appendix A DIFFERENCES BETWEEN UCSD'S PASCAL AND STANDARD PASCAL The PASCAL language used in this book contains most of the features described by K. Jensen and N. Wirth in PASCAL User Manual and Report, Springer Verlag, 1975. We refer to the PASCAL defined by Jensen and Wirth as "Standard" PASCAL, because of its widespread acceptance even though no international standard for the language has yet been established. The PASCAL used in this book has been implemented at University of California San Diego (UCSD) in a complete software system for use on a variety of small stand-alone microcomputers. This will be referred to as "UCSD PASCAL", which differs from the standard by a small number of omissions, a very small number of alterations, and several extensions. This appendix provides a very brief summary Of these differences. Only the PASCAL constructs used within this book will be mentioned herein. Documents are available from the author's group at UCSD describing UCSD PASCAL in detail. 1. CASE Statements Jensen & Wirth state that if there is no label equal to the value of the case statement selector, then the result of the case statement is undefined. UCSD PASCAL treats this situation by leaving the case statement normally with no action being taken. 2. Comments In UCSD PASCAL, a comment appears between the delimiting symbols "(*" and "*)". If the opening delimiter is followed immediately by a dollar sign, as in "(*$", then the remainder of the comment is treated as a directive to the compiler. The only compiler directive mentioned in this book is (*$G+*), which tells the compiler to allow the use of GOTO statements. -
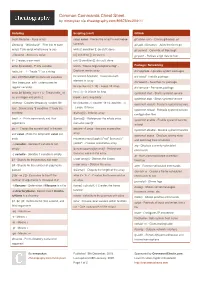
Common Commands Cheat Sheet by Mmorykan Via Cheatography.Com/89673/Cs/20411
Common Commands Cheat Sheet by mmorykan via cheatography.com/89673/cs/20411/ Scripting Scripting (cont) GitHub bash filename - Runs script sleep value - Forces the script to wait value git clone <url > - Clones gitkeeper url Shebang - "# !bi n/b ash " - First line of bash seconds git add <fil ena me> - Adds the file to git script. Tells script what binary to use while [[ condition ]]; do stuff; done git commit - Commits all files to git ./file name - Also runs script if [[ condition ]]; do stuff; fi git push - Pushes all git files to host # - Creates a comment until [[ condition ]]; do stuff; done echo ${varia ble} - Prints variable words=" h ouse dogs telephone dog" - Package / Networking hello_int = 1 - Treats "1 " as a string Declares words array dnf upgrade - Updates system packages Use UPPERC ASE for constant variables for word in ${words} - traverses each dnf install - Installs package element in array Use lowerc ase _wi th_ und ers cores for dnf search - Searches for package for counter in {1..10} - Loops 10 times regular variables dnf remove - Removes package for ((;;)) - Is infinite for loop echo $(( ${hello _int} + 1 )) - Treats hello_int systemctl start - Starts systemd service as an integer and prints 2 break - exits loop body systemctl stop - Stops systemd service mktemp - Creates temporary random file for ((count er=1; counter -le 10; counter ++)) systemctl restart - Restarts systemd service test - Denoted by "[[ condition ]]" tests the - Loops 10 times systemctl reload - Reloads systemd service condition -

Shell Code for Beginners
Shell Code For Beginners Beenu Arora Site: www.BeenuArora.com Email: [email protected] ################################################################ # .___ __ _______ .___ # # __| _/____ _______| | __ ____ \ _ \ __| _/____ # # / __ |\__ \\_ __ \ |/ // ___\/ /_\ \ / __ |/ __ \ # # / /_/ | / __ \| | \/ <\ \___\ \_/ \/ /_/ \ ___/ # # \____ |(______/__| |__|_ \\_____>\_____ /\_____|\____\ # # \/ \/ \/ # # ___________ ______ _ __ # # _/ ___\_ __ \_/ __ \ \/ \/ / # # \ \___| | \/\ ___/\ / # # \___ >__| \___ >\/\_/ # # est.2007 \/ \/ forum.darkc0de.com # ################################################################ What is a shell Code? Shellcode is defined as a set of instructions injected and then executed by an exploited program. Shellcode is used to directly manipulate registers and the functionality of a exploited program. We can of course write shell codes in the high level language but would let you know later why they might not work for some cases, so assembly language is preferred for this. I would take an clean example of the exit() syscall used for exiting from a program. Many of you might be wondered to see why this being used is, the reason is the newer kernel don’t allow anymore the code execution from the stack so we have to use some C library wrapper or libc (responsible for providing us the malloc function). Usage at darker site: We write shellcode because we want the target program to function in a manner other than what was intended by the designer. One way to manipulate the program is to force it to make a system call or syscall. System calls in Linux are accomplished via software interrupts and are called with the int 0x80 instruction. -

Unix: Beyond the Basics
Unix: Beyond the Basics BaRC Hot Topics – September, 2018 Bioinformatics and Research Computing Whitehead Institute http://barc.wi.mit.edu/hot_topics/ Logging in to our Unix server • Our main server is called tak4 • Request a tak4 account: http://iona.wi.mit.edu/bio/software/unix/bioinfoaccount.php • Logging in from Windows Ø PuTTY for ssh Ø Xming for graphical display [optional] • Logging in from Mac ØAccess the Terminal: Go è Utilities è Terminal ØXQuartz needed for X-windows for newer OS X. 2 Log in using secure shell ssh –Y user@tak4 PuTTY on Windows Terminal on Macs Command prompt user@tak4 ~$ 3 Hot Topics website: http://barc.wi.mit.edu/education/hot_topics/ • Create a directory for the exercises and use it as your working directory $ cd /nfs/BaRC_training $ mkdir john_doe $ cd john_doe • Copy all files into your working directory $ cp -r /nfs/BaRC_training/UnixII/* . • You should have the files below in your working directory: – foo.txt, sample1.txt, exercise.txt, datasets folder – You can check they’re there with the ‘ls’ command 4 Unix Review: Commands Ø command [arg1 arg2 … ] [input1 input2 … ] $ sort -k2,3nr foo.tab -n or -g: -n is recommended, except for scientific notation or start end a leading '+' -r: reverse order $ cut -f1,5 foo.tab $ cut -f1-5 foo.tab -f: select only these fields -f1,5: select 1st and 5th fields -f1-5: select 1st, 2nd, 3rd, 4th, and 5th fields $ wc -l foo.txt How many lines are in this file? 5 Unix Review: Common Mistakes • Case sensitive cd /nfs/Barc_Public vs cd /nfs/BaRC_Public -bash: cd: /nfs/Barc_Public: -

LAB MANUAL for Computer Network
LAB MANUAL for Computer Network CSE-310 F Computer Network Lab L T P - - 3 Class Work : 25 Marks Exam : 25 MARKS Total : 50 Marks This course provides students with hands on training regarding the design, troubleshooting, modeling and evaluation of computer networks. In this course, students are going to experiment in a real test-bed networking environment, and learn about network design and troubleshooting topics and tools such as: network addressing, Address Resolution Protocol (ARP), basic troubleshooting tools (e.g. ping, ICMP), IP routing (e,g, RIP), route discovery (e.g. traceroute), TCP and UDP, IP fragmentation and many others. Student will also be introduced to the network modeling and simulation, and they will have the opportunity to build some simple networking models using the tool and perform simulations that will help them evaluate their design approaches and expected network performance. S.No Experiment 1 Study of different types of Network cables and Practically implement the cross-wired cable and straight through cable using clamping tool. 2 Study of Network Devices in Detail. 3 Study of network IP. 4 Connect the computers in Local Area Network. 5 Study of basic network command and Network configuration commands. 6 Configure a Network topology using packet tracer software. 7 Configure a Network topology using packet tracer software. 8 Configure a Network using Distance Vector Routing protocol. 9 Configure Network using Link State Vector Routing protocol. Hardware and Software Requirement Hardware Requirement RJ-45 connector, Climping Tool, Twisted pair Cable Software Requirement Command Prompt And Packet Tracer. EXPERIMENT-1 Aim: Study of different types of Network cables and Practically implement the cross-wired cable and straight through cable using clamping tool. -

Unix (And Linux)
AWK....................................................................................................................................4 BC .....................................................................................................................................11 CHGRP .............................................................................................................................16 CHMOD.............................................................................................................................19 CHOWN ............................................................................................................................26 CP .....................................................................................................................................29 CRON................................................................................................................................34 CSH...................................................................................................................................36 CUT...................................................................................................................................71 DATE ................................................................................................................................75 DF .....................................................................................................................................79 DIFF ..................................................................................................................................84 -

Install and Run External Command Line Softwares
job monitor and control top: similar to windows task manager (space to refresh, q to exit) w: who is there ps: all running processes, PID, status, type ps -ef | grep yyin bg: move current process to background fg: move current process to foreground jobs: list running and suspended processes kill: kill processes kill pid (could find out using top or ps) 1 sort, cut, uniq, join, paste, sed, grep, awk, wc, diff, comm, cat All types of bioinformatics sequence analyses are essentially text processing. Unix Shell has the above commands that are very useful for processing texts and also allows the output from one command to be passed to another command as input using pipe (“|”). less cosmicRaw.txt | cut -f2,3,4,5,8,13 | awk '$5==22' | cut -f1 | sort -u | wc This makes the processing of files using Shell very convenient and very powerful: you do not need to write output to intermediate files or load all data into the memory. For example, combining different Unix commands for text processing is like passing an item through a manufacturing pipeline when you only care about the final product 2 Hands on example 1: cosmic mutation data - Go to UCSC genome browser website: http://genome.ucsc.edu/ - On the left, find the Downloads link - Click on Human - Click on Annotation database - Ctrl+f and then search “cosmic” - On “cosmic.txt.gz” right-click -> copy link address - Go to the terminal and wget the above link (middle click or Shift+Insert to paste what you copied) - Similarly, download the “cosmicRaw.txt.gz” file - Under your home, create a folder