Managing Patches Using Sanernow 4.0 User Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Adobe Golive 5 Gratis Epub, Ebook
ADOBE GOLIVE 5 GRATIS Auteur: Deborah Shadovitz Aantal pagina's: 1024 pagina's Verschijningsdatum: none Uitgever: none EAN: 9789039516010 Taal: nl Link: Download hier letsland.nl Up to two pounds, will most likely ship priority. Over 2 pounds, will ship FedEx or parcel. International buyers: we ship using only the eBay global shipping program. We do not control what eBay charges, nor can we even see the amount. We cannot combine international shipping unless you contact us prior to any bids being placed on the items you want. We leave positive feedback as soon as payment is received, and would ask you to do the courtesy of allowing us to solve any issues you might have. Software might not work on other version of Mac OS. Please make sure it works on your machine before you buy it. Create and publish content for print and the Web faster and more easily than ever before--all at an outstanding value. Adobe integration makes it possible. The Adobe Creative Suite makes it affordable. Get the functionality most suited to your needs or install everything at once to ensure that the right tool is always there when you need it. With over new features, Adobe GoLive 5. Move from creative concepts to dynamic, high-impact Web sites with the power of one of the industry's most comprehensive and integrated Web applications. Despite a slightly delayed release, Adobe's GoLive 5. Graphically oriented designers will enjoy the program's drag-and-drop simplicity and tight integration with other Adobe packages such as PhotoShop and Illustrator; and serious coders should appreciate GoLive's new customization options and Code feature that protects existing code from undesired modification. -

Adobe Trademark Database for General Distribution
Adobe Trademark List for General Distribution As of May 17, 2021 Please refer to the Permissions and trademark guidelines on our company web site and to the publication Adobe Trademark Guidelines for third parties who license, use or refer to Adobe trademarks for specific information on proper trademark usage. Along with this database (and future updates), they are available from our company web site at: https://www.adobe.com/legal/permissions/trademarks.html Unless you are licensed by Adobe under a specific licensing program agreement or equivalent authorization, use of Adobe logos, such as the Adobe corporate logo or an Adobe product logo, is not allowed. You may qualify for use of certain logos under the programs offered through Partnering with Adobe. Please contact your Adobe representative for applicable guidelines, or learn more about logo usage on our website: https://www.adobe.com/legal/permissions.html Referring to Adobe products Use the full name of the product at its first and most prominent mention (for example, “Adobe Photoshop” in first reference, not “Photoshop”). See the “Preferred use” column below to see how each product should be referenced. Unless specifically noted, abbreviations and acronyms should not be used to refer to Adobe products or trademarks. Attribution statements Marking trademarks with ® or TM symbols is not required, but please include an attribution statement, which may appear in small, but still legible, print, when using any Adobe trademarks in any published materials—typically with other legal lines such as a copyright notice at the end of a document, on the copyright page of a book or manual, or on the legal information page of a website. -

How to Use Encryption and Privacy Tools to Evade Corporate Espionage
How to use Encryption and Privacy Tools to Evade Corporate Espionage An ICIT White Paper Institute for Critical Infrastructure Technology August 2015 NOTICE: The recommendations contained in this white paper are not intended as standards for federal agencies or the legislative community, nor as replacements for enterprise-wide security strategies, frameworks and technologies. This white paper is written primarily for individuals (i.e. lawyers, CEOs, investment bankers, etc.) who are high risk targets of corporate espionage attacks. The information contained within this briefing is to be used for legal purposes only. ICIT does not condone the application of these strategies for illegal activity. Before using any of these strategies the reader is advised to consult an encryption professional. ICIT shall not be liable for the outcomes of any of the applications used by the reader that are mentioned in this brief. This document is for information purposes only. It is imperative that the reader hires skilled professionals for their cybersecurity needs. The Institute is available to provide encryption and privacy training to protect your organization’s sensitive data. To learn more about this offering, contact information can be found on page 41 of this brief. Not long ago it was speculated that the leading world economic and political powers were engaged in a cyber arms race; that the world is witnessing a cyber resource buildup of Cold War proportions. The implied threat in that assessment is close, but it misses the mark by at least half. The threat is much greater than you can imagine. We have passed the escalation phase and have engaged directly into full confrontation in the cyberwar. -

1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27
Case 3:16-cv-04144-JST Document 49 Filed 11/15/16 Page 1 of 38 1 2 3 4 5 6 7 8 UNITED STATES DISTRICT COURT 9 NORTHERN DISTRICT OF CALIFORNIA 10 SAN FRANCISCO COURTHOUSE 11 12 ADOBE SYSTEMS INCORPORATED, a Case No.: 3:16-cv-04144-JST 13 Delaware Corporation, [PROPOSED] 14 Plaintiff, PERMANENT INJUNCTION AGAINST DEFENDANT ITR 15 v. CONSULING GROUP, LLC, AND DISMISSAL OF DEFENDANT ITR 16 A & S ELECTRONICS, INC., a California CONSULTING GROUP, LLC Corporation d/b/a TRUSTPRICE; SPOT.ME 17 PRODUCTS LLC, a Nevada Limited Liability Honorable Jon S. Tigar Company; ALAN Z. LIN, an Individual; 18 BUDGET COMPUTER, a business entity of unknown status; COMPUTECHSALE, LLC, a 19 New Jersey Limited Liability Company; EXPRESSCOMM INTERNATIONAL INC., a 20 California Corporation; FAIRTRADE CORPORATION, a business entity of unknown 21 status, FCO ELECTRONICS, a business entity of unknown status; ITR CONSULTING 22 GROUP, LLC, a Texas Limited Liability Company; RELIABLE BUSINESS PARTNER, 23 INC., a New York Corporation; LESTER WIEGERS, an individual doing business as 24 ULTRAELECTRONICS; and DOES 1-10, Inclusive, 25 Defendants. 26 27 28 - 1 - [PROPOSED] PERMANENT INJUNCTION & DISMISSAL – Case No.: 3:16-cv-04144-JST Case 3:16-cv-04144-JST Document 49 Filed 11/15/16 Page 2 of 38 1 The Court, pursuant to the Stipulation for Entry of Permanent Injunction & Dismissal 2 (“Stipulation”), between Plaintiff Adobe Systems Incorporated (“Plaintiff”), on the one hand, and 3 Defendant ITR Consulting Group, LLC (“ITR”), on the other hand, hereby ORDERS, 4 ADJUDICATES and DECREES that a permanent injunction shall be and hereby is entered against 5 ITR as follows: 6 1. -
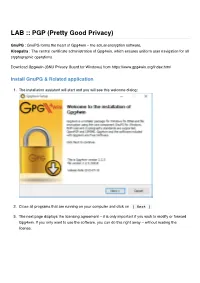
LAB :: PGP (Pretty Good Privacy)
LAB :: PGP (Pretty Good Privacy) GnuPG : GnuPG forms the heart of Gpg4win – the actual encryption software. Kleopatra : The central certificate administration of Gpg4win, which ensures uniform user navigation for all cryptographic operations. Download Gpg4win (GNU Privacy Guard for Windows) from https://www.gpg4win.org/index.html Install GnuPG & Related application 1. The installation assistant will start and you will see this welcome dialog: 2. Close all programs that are running on your computer and click on [ Next ] 3. The next page displays the licensing agreement – it is only important if you wish to modify or forward Gpg4win. If you only want to use the software, you can do this right away – without reading the license. Click on [ Next ] 4. On the page that contains the selection of components you can decide which programs you want to install. A default selection has already been made for you. You can also install individual components at a later time. Moving your mouse cursor over a component will display a brief description. Another useful feature is the display of required hard drive space for all selected components. Bellow are the application and there fucntion: a. GnuPG: Gnu Privacy Guard b. Kleopatra: Keymanager for OpenPGP c. GPA: GNU Privacy Assistant d. GpgOL: GnuPG for Outlook e. GpgEX: GnuPG Shell Extension f. Claws-Mail: Claws Mail user client g. Gpg4win Compedium: The Gpg4Win documentation Click on [ Next ] 5. The system will suggest a folder for the installation, e.g.: C:\Programme Files (x86)\GNU\GnuPG You can accept the suggestion or select a different folder for installing Gpg4win. -

Obstacles to the Adoption of Secure Communication Tools
Obstacles to the Adoption of Secure Communication Tools Ruba Abu-Salma M. Angela Sasse Joseph Bonneau University College London, UK University College London, UK Stanford University & EFF, USA Anastasia Danilova Alena Naiakshina Matthew Smith University of Bonn, Germany University of Bonn, Germany University of Bonn, Germany Abstract—The computer security community has advocated Recent mobile phone-based secure communication tools widespread adoption of secure communication tools to counter have often been designed to hide security from the user com- mass surveillance. Several popular personal communication tools pletely (albeit at some security cost [1]). WhatsApp famously (e.g., WhatsApp, iMessage) have adopted end-to-end encryption, and many new tools (e.g., Signal, Telegram) have been launched deployed E2E encryption to approximately a billion users with security as a key selling point. However it remains unclear through a code update to its application for messages, voice if users understand what protection these tools offer, and if they calls and video communications [18], with only negligible value that protection. In this study, we interviewed 60 partici- changes to the user experience. Some other communication pants about their experience with different communication tools tools (e.g., Signal, Threema) have launched with security and their perceptions of the tools’ security properties. We found that the adoption of secure communication tools is hindered by as an explicit selling point, but they also hide nearly all fragmented user bases and incompatible tools. Furthermore, the cryptographic details. vast majority of participants did not understand the essential There are key differences in the security model of dif- concept of end-to-end encryption, limiting their motivation to ferent E2E-encrypted tools, in addition to a large gap in adopt secure tools. -

Adobe Trademark Database for General Distribution United States & General International As of June 12, 2008
a Adobe Trademark Database for General Distribution United States & General International As of June 12, 2008 Please refer to the Permissions and trademark guidelines on our company web site at http://www.adobe.com/misc/agreement.html and to the publication Adobe Trademark Guidelines for third parties who license, use or refer to Adobe trademarks for specific information on proper trademark usage. The latter Guidelines and a copy of this database (and future updates) are available from our company web site at: http://www.adobe.com/misc/trademarks.html. If you are distributing materials exclusively or primarily in Japan, please contact your Adobe representative for a copy of the appropriate Adobe trademark information for Japan. The database shows the proper marking for first use of the mark in a publication. The marking shown for compound word trademarks is for the first use of both components, e.g. Adobe® Premiere®. Once marked, subsequent references to word marks do not require repeated marking, but trademark symbols must always be used with logos and logotypes (stylized word marks). For specific Adobe logos or product signatures, please contact your Adobe representative for a copy of our Guidelines publication and camera-ready master art or an electronic file for reproduction of the logo or signature. Please keep in mind that you must sign a trademark license agreement with Adobe before using one of our logos or product signatures. Please note that the basic formula for attribution is: [“Adobe” and “the Adobe logo” first, if used, followed by other Adobe marks used in alphabetical order] are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. -

USING ADOBE MEDIA ENCODER CS4 2 Resources
Using ADOBE® MEDIA ENCODER™ CS4 ©Copyright 2011 Adobe Systems Incorporated. All rights reserved. Using Adobe® Media Encoder CS5.5 This user guide is protected under copyright law, furnished for informational use only, is subject to change without notice, and should not be construed as a commitment by Adobe Systems Incorporated. Adobe Systems Incorporated assumes no responsibility or liability for any errors or inaccuracies that may appear in the informational content contained in this guide. This user guide is licensed for use under the terms of the Creative Commons Attribution Non-Commercial 3.0 License. This License allows users to copy, distribute, and transmit the user guide for noncommercial purposes only so long as (1) proper attribution to Adobe is given as the owner of the user guide; and (2) any reuse or distribution of the user guide contains a notice that use of the user guide is governed by these terms. The best way to provide notice is to include the following link. To view a copy of this license, visit http://creativecommons.org/licenses/by-nc-sa/3.0/. Adobe, the Adobe logo, Acrobat, Acrobat Capture, Acrobat Connect, Acrobat Messenger, Acrobat 3D Capture, ActionScript, ActiveTest, Adobe ActionSource, Adobe AIR, Adobe AIR logo, Adobe Audition, Adobe Caslon, Adobe Connect, Adobe DataWarehouse, Adobe Dimensions, Adobe Discover, Adobe Financial Services, Adobe Garamond, Adobe Genesis, Adobe Griffo, Adobe Jenson, Adobe Kis, Adobe OnLocation, Adobe Originals logo, Adobe PDF logo, Adobe Premiere, AdobePS, Adobe SiteSearch, Adobe -

Adbe 10K Fy11- Final
UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 _____________________________ FORM 10-K (Mark One) ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 2, 2011 or TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to Commission File Number: 0-15175 ADOBE SYSTEMS INCORPORATED (Exact name of registrant as specified in its charter) _____________________________ Delaware 77-0019522 (State or other jurisdiction of (I.R.S. Employer incorporation or organization) Identification No.) 345 Park Avenue, San Jose, California 95110-2704 (Address of principal executive offices and zip code) (408) 536-6000 (Registrant’s telephone number, including area code) Securities registered pursuant to Section 12(b) of the Act: Title of Each Class Name of Each Exchange on Which Registered Common Stock, $0.0001 par value per share The NASDAQ Stock Market LLC (NASDAQ Global Select Market) Securities registered pursuant to Section 12(g) of the Act: None _____________________________ Indicate by checkmark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes No Indicate by checkmark if the registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. Yes No Indicate by checkmark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15 (d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports) and (2) has been subject to such filing requirements for the past 90 days. -

The Crypto Cat Is out of the Bag: an Illustrative Inventory of Widely-Available Encryption Applications
December 8, 2015 The Crypto Cat is Out of the Bag: An Illustrative Inventory of Widely-Available Encryption Applications When it comes to encryption, the genie is out of the bottle. But encryption isn’t magic. It’s math, and very well-known math at that. The basic principles behind modern end-to-end encryption of digital messages, where only the recipient of the message can decode it, are nearly four decades old.1 U.S. companies like Apple and Facebook, providers of the encrypted messaging services iMessage and WhatsApp, don’t have a monopoly on strong end-to-end encryption tools. Strong encryption tools are everywhere, and over a billion ordinary people around the world rely on them every day. There are countless applications that are freely available online, across the globe, with unbreakable end-to-end encryption. The vast majority of those applications are either “open source” software that anyone is free to use, review, copy or build on,2 and/or are offered by companies, organizations or developers outside of the United States. In fact, it’s so easy to create new end-to-end encryption apps, jihadists have been coding their very own secure messaging tools since at least 2007, tools with names like Mujahadeen Secrets and Security of the Mujahid.3 Another app that terrorists are claimed to have used, Telegram, is based in Berlin.4 1 The foundational work in this area began with Whitfield Diffie and Martin Hellman’s New Directions in Cryptography, IEEE Transactions in Information Theory (Nov. 6, 1976), available at http://www- ee.stanford.edu/~hellman/publications/24.pdf. -

SFTP Bulk Upload Guide Electronic Taxpayer Service Center
SFTP Bulk Upload Guide Electronic Taxpayer Service Center Revised January 2021 Indiana Department of Revenue Table of Contents Overview of Bulk Upload 2 ACH Debit Payments — Debit Block Option 3 Taxpayer Registration 4 Registration 4 Certification to File 4 Encryption for SFTP Submission 5 PGP or GPG Software 5 Secure File Transfer 5 Acknowledgements 6 File Naming Conventions 8 Quick Reference 9 Registration Steps 9 Steps to File 9 GPG Kleopatra Install and Key Generation 10 Kleopatra Usage 15 APPENDIX A – PGP setup and use 19 APPENDIX B - SFTP Client Installation and Setup Instructions (WinSCP) 20 APPENDIX C – Using WinSCP to Send a File 21 APPENDIX D – Common Troubleshooting 24 APPENDIX E – Common Acronyms 25 APPENDIX F – Supported Form Types 26 APPENDIX G – SFTP Bulk Upload Business Rules 27 1 Overview of Bulk Upload The bulk upload facility provides taxpayers submitting files with large numbers of transactions the ability to electronically submit these records to the Indiana Department of Revenue (DOR). Bulk upload files are created by the customer and then submitted to DOR for processing. The files are processed sequentially within a couple of hours. During high-volume processing, there can be an increased turnaround time. When the process is complete, an acknowledgment email is sent to the authorized representative with the results of the submission. The Indiana Department of Revenue is transitioning to a new modernized tax system, INTIME. Due to this transition we now have a new expanded file size limit of 10MB for many of the files submitted. DOR recommends INTIME as the preferred method for file submission. -

Coldfusion 8 Developer Security Guidelines
Adobe White Paper ColdFusion 8 developer security guidelines Erick Lee, Ian Melven, and Sarge Sargent October 2007 Adobe, the Adobe logo, and ColdFusion are either registered trademarks or trademarks of Adobe Systems Incorporated in the United States and/or other countries. Linux is a registered trademark of Linus Torvalds in the U.S. and other countries. Windows is either a registered trademark or a trademark of Microsoft Corporation in the United States and/or other countries. UNIX is a registered trademark of The Open Group in the U.S. and other countries. Java is a trademark or registered trademark of Sun Microsystems, Inc. in the United States and other countries. All other trademarks are the property of their respective owners. © 2007 Adobe Systems Incorporated. All rights reserved. Printed in the USA. Adobe Systems Incorporated 345 Park Avenue San Jose, CA 95110-2704 USA www.adobe.com security guidelines Contents Authentication ................................................................................................................... 1 Best practices..............................................................................................................2 Best practices in action ...............................................................................................3 Simple authentication using a database ......................................................................4 NTLM 5 LDAP 6 Logout 6 Authenticating to another server .................................................................................7