Report of the Joint Inquiry Into the Terrorist
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

137-148 Book Review -Eng.Qxd
POLICY IN SLAM DUNK STYLE George Tenet, with Bill Harlow. At the Center of the Storm: My Years at the CIA. New York: Harper Collins Publishers, 2007, 832 p. Reviewed by Gennady Evstafiev I have in front of me a huge 2007published volume (832 pages with appendices) of recollec tions of George Tenet, exDirector of the CIA. The book contains his memories of seven years that he spent at the head of this notorious department. Strictly speaking, Mr. Tenet served in the agency for nine years – during the first two he was a deputy of notorious John Deutch, whose 18 months of disgrace in the CIA ended in 1997. However, this is a different instructive story. So George Tenet and his directorship of the intelligence occurred during, probably, the most aggressive years of U.S. foreign policy and arrogant selfconfidence of Washington in its unsurpassable global power. Decisions taken in these years by two American administrations shook the stability of the world and continue to have their destructive impact on the prospects of international cooperation and peaceful democratic development of many countries. Reliance on military power, neglect of the opinion of the majority of nations, armstwisting pol icy towards weak countries and U.S. allies, enlightened use of official lies – all this resulted in an unenviable situation, in which the United States finds itself now. George Tenet is a partici pant of this process and an executor of many acts that have nothing to do with international law, the commitment to which is a popular topic of propaganda for the fans of U.S. -

Visa Information for Exchange Programs
Visa Information for Exchange Programs In general, you will want to start this process 2-3 months before you plan to travel, or as prompted by your program. You may need to travel to another city to personally make application. For example, the closest embassies/consulates for Greece, Norway, South Korea and China are in Chicago. There are visa service providers, such as Travisa, which will do the legwork for you, saving you the travel. However, please note that it will cost more to acquire your visa through these services. Documentation ● Some documents, such as a letter of admission and verification of housing, will be provided by your program. ● Others, such as verification of insurance and a certificate of enrollment, will be provided by Augsburg. ● You may also be asked for tax returns or bank statements to verify funding, a health form, college (and possibly high school) transcripts. Augsburg University Exchange Partners 1) American College of Greece 2) American University of Beirut 3) Arcada University 4) Hong Kong Baptist University 5) iCLA Yamanshi Gakuin University 6) NTNU Norwegian University of Science and Technology 7) Nord University College 8) Oslo Metropolitan University 9) Østfold University College 10) Sejong University 11) Sungshin Women’s University 12) UiT: The Arctic University of Norway 13) United International College 14) Universidad Centroamericana 15) University of Warwick 16) Volda University College 17) Western Norway University of Applied Sciences 18) Yonsei University A merican College of Greece Fee: $124 Travel to Chicago: varies Cost of background check: approximately $50 Cost for photo: $15 You are required to apply for you visa in person at the Greek Consulate in Chicago (650 North Saint Clair Street, Chicago IL 60611), and will need to make an appointment in advance. -

2003 Iraq War: Intelligence Or Political Failure?
2003 IRAQ WAR: INTELLIGENCE OR POLITICAL FAILURE? A Thesis submitted to the Faculty of The School of Continuing Studies and of The Graduate School of Arts and Sciences in partial fulfillment of the requirements for the degree of Master of Arts in Liberal Studies By Dione Brunson, B.A. Georgetown University Washington, D.C. April, 2011 DISCLAIMER THE VIEWS EXPRESSED IN THIS ACADEMIC RESEARCH PAPER ARE THOSE OF THE AUTHOR AND DO NOT REFLECT THE OFFICIAL POLICIES OR POSITIONS OF THE U.S. GOVERNMENT, DEPARTMENT OF DEFENSE, OR THE U.S. INTELLIGENCE COMMUNITY. ALL INFORMATION AND SOURCES FOR THIS PAPER WERE DRAWN FROM OPEN SOURCE MATERIALS. ii 2003 IRAQ WAR: INTELLIGENCE OR POLITICAL FAILURE? Dione Brunson, B.A. MALS Mentor: Ralph Nurnberger, Ph.D. ABSTRACT The bold U.S. decision to invade Iraq in 2003 was anchored in intelligence justifications that would later challenge U.S. credibility. Policymakers exhibited unusual bureaucratic and public dependencies on intelligence analysis, so much so that efforts were made to create supporting information. To better understand the amplification of intelligence, the use of data to justify invading Iraq will be explored alongside events leading up to the U.S.-led invasion in 2003. This paper will examine the use of intelligence to invade Iraq as well as broader implications for politicization. It will not examine the justness or ethics of going to war with Iraq but, conclude with the implications of abusing intelligence. iii ACKNOWLEDGMENTS Thank you God for continued wisdom. Thank you Dr. Nurnberger for your patience. iv DEDICATION This work is dedicated to Mom and Dad for their continued support. -

Table of Contents
Chapter 4 Building International Will and Capacity to Counter Terrorism The Department of State engages diplomatically with for- eign governments and in international and regional fora to accomplish the US Government’s first priority — protect- ing Americans at home and abroad. The Department of State’s diplomatic efforts help build the political will and operational skills of foreign governments to combat terror. Many countries are committed allies in the global war on terrorism. Some, however, need train- ing and resources to develop stronger institutions and capabilities. The Department of State’s counterterrorism efforts are an essential component in the success of US military, law enforcement, intelligence, and financial ac- tivities in the global fight against terrorism. Multilateral and regional organizations are also a key plat- form for developing broad international support for the adoption and implementation of policies, strategies, and “best practices” in combating terrorism and financing of terrorist activities. The Department of State works actively with foreign governments to urge adoption of all 12 inter- national counterterrorism conventions, as well as adherence to and implementation of UNSCR 1373, which imposes binding obligations on all states to suppress and prevent terrorist financing, improve their border controls, enhance information sharing and law enforcement coop- eration, suppress terrorist recruitment, and deny terrorists safe haven. Antiterrorism Assistance Program Ambassador J. Cofer Black, former US State Department Coordinator Congress authorized the Antiterrorism Assistance (ATA) Pro- for Counterterrorism, during a news conference at the IV Regular gram in 1983 as part of a major initiative against international Session of the Organization of American States Inter-American terrorism. -

VULCAN HISTORICAL REVIEW Vol
THE VULCAN HISTORICAL REVIEW Vol. 16 • 2012 The Vulcan Historical Review Volume 16 • 2012 ______________________________ Chi Omicron Chapter Phi Alpha Theta History Honor Society University of Alabama at Birmingham The Vulcan Historical Review Volume 16 • 2012 Published annually by the Chi Omicron Chapter of Phi Alpha Theta at the University of Alabama at Birmingham 2012 Editorial Staff Executive Editors Beth Hunter and Maya Orr Graphic Designer Jacqueline C. Boohaker Editorial Board Chelsea Baldini Charles Brooks Etheredge Brittany Richards Foust Faculty Advisor Dr. George O. Liber Co-Sponsors The Linney Family Endowment for The Vulcan Historical Review Dr. Carol Z. Garrison, President, UAB Dr. Linda Lucas, Provost, UAB Dr. Suzanne Austin, Vice Provost for Student and Faculty Success, UAB Dr. Bryan Noe, Dean of the Graduate School, UAB Dr. Thomas DiLorenzo, Dean, College of Arts and Sciences, UAB Dr. Rebecca Ann Bach, Associate Dean for Research and Creative Activities in the Humanities and Arts, UAB Dr. Carolyn A. Conley, Chair, Department of History, UAB The Department of History, UAB The Vulcan Historical Review is published annually by the Chi Omicron Chapter (UAB) of Phi Alpha Theta History Honor Society. The journal is completely student-written and student-edited by undergraduate and masters level graduate students at the University of Alabama at Birmingham. ©2012 Chi Omicron Chapter of Phi Alpha Theta History Honor Society, the University of Alabama at Birmingham. All rights reserved. No material may be duplicated or quoted without the expressed written permission of the author. The University of Alabama at Birmingham, its departments, and its organizations disclaim any responsibility for statements, either in fact or opinion, made by contributors. -

THE FUTURE of IDEAS This Work Is Licensed Under a Creative Commons Attribution-Noncommercial License (US/V3.0)
less_0375505784_4p_fm_r1.qxd 9/21/01 13:49 Page i THE FUTURE OF IDEAS This work is licensed under a Creative Commons Attribution-Noncommercial License (US/v3.0). Noncommercial uses are thus permitted without any further permission from the copyright owner. Permissions beyond the scope of this license are administered by Random House. Information on how to request permission may be found at: http://www.randomhouse.com/about/ permissions.html The book maybe downloaded in electronic form (freely) at: http://the-future-of-ideas.com For more permission about Creative Commons licenses, go to: http://creativecommons.org less_0375505784_4p_fm_r1.qxd 9/21/01 13:49 Page iii the future of ideas THE FATE OF THE COMMONS IN A CONNECTED WORLD /// Lawrence Lessig f RANDOM HOUSE New York less_0375505784_4p_fm_r1.qxd 9/21/01 13:49 Page iv Copyright © 2001 Lawrence Lessig All rights reserved under International and Pan-American Copyright Conventions. Published in the United States by Random House, Inc., New York, and simultaneously in Canada by Random House of Canada Limited, Toronto. Random House and colophon are registered trademarks of Random House, Inc. library of congress cataloging-in-publication data Lessig, Lawrence. The future of ideas : the fate of the commons in a connected world / Lawrence Lessig. p. cm. Includes index. ISBN 0-375-50578-4 1. Intellectual property. 2. Copyright and electronic data processing. 3. Internet—Law and legislation. 4. Information society. I. Title. K1401 .L47 2001 346.04'8'0285—dc21 2001031968 Random House website address: www.atrandom.com Printed in the United States of America on acid-free paper 24689753 First Edition Book design by Jo Anne Metsch less_0375505784_4p_fm_r1.qxd 9/21/01 13:49 Page v To Bettina, my teacher of the most important lesson. -

Filling Terrorism Gaps: Veos, Evaluating Databases, and Applying Risk Terrain Modeling to Terrorism RH Hagan
PNNL-25727 Filling Terrorism Gaps: VEOs, Evaluating Databases, and Applying Risk Terrain Modeling to Terrorism RH Hagan August 2016 PNNL-25727 Filling Terrorism Gaps: VEOs, Evaluating Databases, and Applying Risk Terrain Modeling to Terrorism RH Hagan August 2016 Prepared for the U.S. Department of Energy under Contract DE-AC05-76RL01830 Pacific Northwest National Laboratory Richland, Washington 99352 PNNL-25727 Abstract This paper aims to address three issues: the lack of literature differentiating terrorism and violent extremist organizations (VEOs), terrorism incident databases, and the applicability of Risk Terrain Modeling (RTM) to terrorism. Current open source literature and publicly available government sources do not differentiate between terrorism and VEOs; furthermore, they fail to define them. Addressing the lack of a comprehensive comparison of existing terrorism data sources, a matrix comparing a dozen terrorism databases is constructed, providing insight toward the array of data available. RTM, a method for spatial risk analysis at a micro level, has some applicability to terrorism research, particularly for studies looking at risk indicators of terrorism. Leveraging attack data from multiple databases, combined with RTM, offers one avenue for closing existing research gaps in terrorism literature. iii Acknowledgments The author would like to sincerely thank several individuals for their contributions to this research. My mentor, Chrissie Noonan, for her guidance and support throughout this process, Carolyn Cramer for her operational support and insight, Alex Stephan, Lead for the Special Programs and Scientific Studies Team at PNNL, George Muller for his support and direction, Hannah Trump for her substantial help with the appendices, and Dan Fortin, Sam Chatterjee, and Thomas Johansen for the constant discussions. -

Staff Statement No
Outline of the 9/11 Plot Staff Statement No. 16 Members of the Commission, your staff is prepared to report its preliminary findings regarding the conspiracy that produced the September 11 terrorist attacks against the United States. We remain ready to revise our understanding of this subject as our work continues. Dietrich Snell, Rajesh De, Hyon Kim, Michael Jacobson, John Tamm, Marco Cordero, John Roth, Douglas Greenburg, and Serena Wille did most of the investigative work reflected in this statement. We are fortunate to have had access to the fruits of a massive investigative effort by the Federal Bureau of Investigation and other law enforcement agencies, as well intelligence collection and analysis from the Central Intelligence Agency, the National Security Agency, the State Department, and the Department of Defense. Much of the account in this statement reflects assertions reportedly made by various 9/11 conspirators and captured al Qaeda members while under interrogation. We have sought to corroborate this material as much as possible. Some of this material has been inconsistent. We have had to make judgment calls based on the weight and credibility of the evidence. Our information on statements attributed to such individuals comes from written reporting; we have not had direct access to any of them. Plot Overview Origins of the 9/11 Attacks The idea for the September 11 attacks appears to have originated with a veteran jihadist named Khalid Sheikh Mohammed (KSM). A Kuwaiti from the Baluchistan region of Pakistan, KSM grew up in a religious family and claims to have joined the Muslim Brotherhood at the age of 16. -

Indien – China – USA: Das Neue Mächtedreieck Asiens
Indien – China – USA: Das neue Mächtedreieck Asiens Heinrich Kreft1 1 Die Entstehung eines neuen Mächtedreiecks in Asien seit Ende des Kalten Krieges Das Ende des Kalten Krieges führte nicht nur in Europa zu erheblichen politischen Veränderungen und Machtverschiebungen, sondern auch in Asien. Hinzu kam, dass zeitgleich mehrere Länder und Regionen Asiens einen beispiellosen wirtschaftlichen Boom erlebten. 1.1 Der Untergang der Sowjetunion Der wichtigste Einzelfaktor für die Veränderung der politischen Landschaft in Asien war der Zusammenbruch der Sowjetunion und das sich daran anschließende Schwin- den des russischen Einflusses in Südasien. Die UdSSR war lange Zeit der wichtigste Verbündete Indiens gewesen, festgeschrieben im indisch-sowjetischen Vertrag von 1971, in dem Moskau Indiens Schutz garantierte. Allerdings wurde dieses Abkom- men bereits Ende der 1980er-Jahre durch die Bemühungen Gorbatschows unter- höhlt, die sowjetischen Beziehungen zu China zu verbessern. Die Russische Förde- ration als Rechtsnachfolger der Sowjetunion war Anfang der 1990er-Jahre kaum noch in der Lage, den sowjetischen Einfluss in Südasien aufrecht zu erhalten. Der ökonomische Niedergang Moskaus ging auch nach dem Zusammenbruch der UdSSR weiter, die russische Marine war nie in der Lage, die Rolle ihrer sowjeti- schen Vorgängerin im Indischen Ozean zu übernehmen. Die indisch-russischen Beziehungen laborieren auch heute noch an den Folgen der Auflösung der Sowjetunion, mit der Indien seinen bis dahin wichtigsten politi- schen und auch ökonomischen Partner verloren -

Anti-Semitism: a Pillar of Islamic Extremist Ideology
Anti-Semitism: A Pillar of Islamic Extremist Ideology In a video message in August 2015, Osama bin Laden’s son, Hamza bin Laden, utilized a range of anti-Semitic and anti-Israel narratives in his effort to rally Al Qaeda supporters and incite violence against Americans and Jews. Bin Laden described Jews and Israel as having a disproportionate role in world events and the oppression of Muslims. He compared the “Zio- Crusader alliance led by America” to a bird: “Its head is America, one wing is NATO and the other is the State of the Jews in occupied Palestine, and the legs are the tyrant rulers that sit on the chests of the peoples of the Muslim Ummah [global community].” An undated image of al-Qaeda terrorist Osama bin Laden and his son, Hamza Bin Laden then called for attacks worldwide and demanded that Muslims “support their brothers in Palestine by fighting the Jews and the Americans... not in America and occupied Palestine and Afghanistan alone, but all over the world…. take it to all the American, Jewish, and Western interests in the world.” Such violent expressions of anti-Semitism have been at the core of Al Qaeda’s ideology for decades. Even the 9/11 terrorist attacks were motivated, in part, by anti-Semitism. Mohamed Atta, a key member of the Al Qaeda Hamburg cell responsible for the attacks, reportedly considered New York City to be the center of a global Jewish conspiracy, and Khalid Sheik Mohammed, who masterminded the attack, had allegedly previously developed several plans to attack Israeli and Jewish targets. -
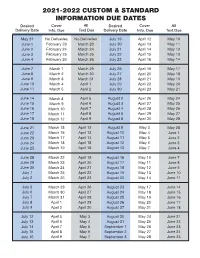
2021-2022 Custom & Standard Information Due Dates
2021-2022 CUSTOM & STANDARD INFORMATION DUE DATES Desired Cover All Desired Cover All Delivery Date Info. Due Text Due Delivery Date Info. Due Text Due May 31 No Deliveries No Deliveries July 19 April 12 May 10 June 1 February 23 March 23 July 20 April 13 May 11 June 2 February 24 March 24 July 21 April 14 May 12 June 3 February 25 March 25 July 22 April 15 May 13 June 4 February 26 March 26 July 23 April 16 May 14 June 7 March 1 March 29 July 26 April 19 May 17 June 8 March 2 March 30 July 27 April 20 May 18 June 9 March 3 March 31 July 28 April 21 May 19 June 10 March 4 April 1 July 29 April 22 May 20 June 11 March 5 April 2 July 30 April 23 May 21 June 14 March 8 April 5 August 2 April 26 May 24 June 15 March 9 April 6 August 3 April 27 May 25 June 16 March 10 April 7 August 4 April 28 May 26 June 17 March 11 April 8 August 5 April 29 May 27 June 18 March 12 April 9 August 6 April 30 May 28 June 21 March 15 April 12 August 9 May 3 May 28 June 22 March 16 April 13 August 10 May 4 June 1 June 23 March 17 April 14 August 11 May 5 June 2 June 24 March 18 April 15 August 12 May 6 June 3 June 25 March 19 April 16 August 13 May 7 June 4 June 28 March 22 April 19 August 16 May 10 June 7 June 29 March 23 April 20 August 17 May 11 June 8 June 30 March 24 April 21 August 18 May 12 June 9 July 1 March 25 April 22 August 19 May 13 June 10 July 2 March 26 April 23 August 20 May 14 June 11 July 5 March 29 April 26 August 23 May 17 June 14 July 6 March 30 April 27 August 24 May 18 June 15 July 7 March 31 April 28 August 25 May 19 June 16 July 8 April 1 April 29 August 26 May 20 June 17 July 9 April 2 April 30 August 27 May 21 June 18 July 12 April 5 May 3 August 30 May 24 June 21 July 13 April 6 May 4 August 31 May 25 June 22 July 14 April 7 May 5 September 1 May 26 June 23 July 15 April 8 May 6 September 2 May 27 June 24 July 16 April 9 May 7 September 3 May 28 June 25. -

Identifying Enemies Among Us: Evolving Terrorist Threats and the Continuing Challenges of Domestic Intelligence Collection and Information Sharing
CHILDREN AND FAMILIES The RAND Corporation is a nonprofit institution that helps improve policy and EDUCATION AND THE ARTS decisionmaking through research and analysis. ENERGY AND ENVIRONMENT HEALTH AND HEALTH CARE This electronic document was made available from www.rand.org as a public service INFRASTRUCTURE AND of the RAND Corporation. TRANSPORTATION INTERNATIONAL AFFAIRS LAW AND BUSINESS Skip all front matter: Jump to Page 16 NATIONAL SECURITY POPULATION AND AGING PUBLIC SAFETY Support RAND SCIENCE AND TECHNOLOGY Purchase this document TERRORISM AND Browse Reports & Bookstore HOMELAND SECURITY Make a charitable contribution For More Information Visit RAND at www.rand.org Explore the RAND Corporation View document details Limited Electronic Distribution Rights This document and trademark(s) contained herein are protected by law as indicated in a notice appearing later in this work. This electronic representation of RAND intellectual property is provided for non- commercial use only. Unauthorized posting of RAND electronic documents to a non-RAND website is prohibited. RAND electronic documents are protected under copyright law. Permission is required from RAND to reproduce, or reuse in another form, any of our research documents for commercial use. For information on reprint and linking permissions, please see RAND Permissions. This product is part of the RAND Corporation conference proceedings series. RAND conference proceedings present a collection of papers delivered at a conference or a summary of the conference. The material herein has been vetted by the conference attendees and both the introduction and the post-conference material have been re- viewed and approved for publication by the sponsoring research unit at RAND.