Modernizing the Common Access Card - Streamlining Identity and Improving Operational Interoperability
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Alphabetical Channel Listing
Alphabetical Channel Listing 129 A&E 131 Discovery Channel 203 FUEL TV 566 MUN2 75 Speed Channel 761 A&E-HD 557 Discovery en Espanol 124 FX 130 National Geographic 141 Spike TV 122 ABC Family 558 Discovery Familia 147 Game Show Network 751 NATIONAL GEOGRAPHIC-HD 84 Sportsman’s Channel 794 ABC Family-HD 108 Discovery Kids Channel 86 Golf Channel 241 National Geographic Wild 641 STANDARD JAZZ 174 ABC News Now 242 Discovery Health 646 GOSPEL 48 NBC - WAFF Huntsville 800 STARZ E-HD 31 ABC - WAAY Huntsville 98 Disney Channel 202 Great American Country 748 NBC-WAFF Huntsville-HD 402 Starz Cinema E 731 ABC-WAAY Huntsville-HD 795 Disney-HD 128 Hallmark 3 NBC - WRCB Chattanooga 403 Starz Cinema W 9 ABC - WTVC Chattanooga 99 Disney XD 308 Hallmark Movie Channel 703 NBC-WRCB Chattanooga-HD 406 Starz Comedy E 709 ABC-WTVC Chattanooga-HD 796 Disney XD-HD 500 HBO E 101 Nick 2 400 Starz East 653 ACOUSTIC CHILL (MooD) 234 DIY 900 HBO E-HD 658 NICK KIDS 408 Starz Edge E 522 ActionMax 652 MDREA SEQUENCE (MooD) 902 HBO 2 E-HD 100 Nickelodeon/Nick at Nite 410 Starz in Black E 622 ADULT ROCK 240 E! Entertainment TV 508 HBO Comedy 102 NickToons 404 Starz Kids & Family E 621 ALTERNATIVE ROCK 999 EAS (EMERGENCY ALERT SYSTEM) 506 HBO Family 104 Noggin 804 STARZ Kids & Family E-HD 107 Animal Planet 639 EASY LISTENING 512 HBO Latino 657 NOGGIN 405 Starz Kids & Family W 620 ARENA ROCK 617 ELECTRONICA 502 HBO 2 643 OPERA 401 Starz West 135 BBC America 420 Encore Action E 504 HBO Signature 85 Outdoor Channel 309 Sundance E 136 BBC World News 421 Encore Action W 510 -

UCF Digital Channel Line Up
University of Central Florida Computer Services and Telecommunications Bright House Networks UCF Digital Channel Line Up Digital Channel availability will depend on the make and model of digital TV. 2.1 NBC HD (WESH 2-HD) 27 The Weather Channel 67 BET 2.2 MeTV 27.1 WRDQ-HD 68 Spike 3 FOX (WOFL 35) 27.2 WRDQ-AN 68.1 WUCF-TV 4 NBC (WESH 2, Daytona Bch) 28 FOX News 68.2 WBCC-TV 5 CBS (WKMG 6, Orlando) 29 ESPN 68.3 UCF-TV 6 UPN (WRBW 65) 30 ESPN2 68.4 WBCC+ 6.1 CBS HD (WKMG-HD 6, Orlando) 31 Sun Sports 69 SyFy 6.2 LATV 32 Speed Channel 70 FX 7 ABC (WFTV 9, Orlando) 34 Nickelodeon 71 CMT 8 CW (WKCF 18, Clermont) 35 Disney Channel 72 VH-1 9 UCF Housing (Movie Channel) 35.1 FOX HD (WOFL-HD 35) 73 MTV 9.1 ABC HD (WFTV-HD 9, Orlando) 36 Cartoon Network 81.1 Infomercials 9.2 Local Weather (WFTV-WX 9) 37 WE 84.5 Local 27 (WRDQ-27, Ind Orlando) 10 Local 27 (WRDQ-27, Ind Orlando) 38 TV Land 84.7 Univision 11 TNT 39 USA 84.8 WESH 2 HD 12 TBS 40 Lifetime 84.10 UPN (WRBW 65) 13 Local News 13 40.1 WACX-DT 84.11 C-SPAN 13.1 Local News 13 HD (CFN-HD 13) 41 Discovery 84.12 Telefutura 14 Local 55 (WACX, Leesburg) 42 A&E 85.5 HSN 15.1 PBS (WCEU-DT 15, Daytona) 43 History 85.7 WDSC 15 15.2 The Florida Channel (DSC-ED) 43.1 Telefutura HD (WOTF-HD) 85.8 WGN 15.3 CCTV 9 44 Animal Planet 85.9 ABC (WFTV 9, Orlando) 15.13 Galavision HD 45 TLC 85.10 Good Life 45 16 ION (WOPX 56, Orlando) 45.1 WTGL-DT 85.11 FOX (WOFL 35) 17 Telefutura (WOTF 43, Melb.) 46 Turner Movie Classics 86.4 Brighthouse Ads 18 Univision (WVEN 26, Orlando) 47.1 BHSN 87.3 WUCF 18.1 CW HD (WKFC-HD -

Page 1 1/26/2018 55 Bravo 447 SEC Network 675 STARZ Cinema East
G R I D L E Y C A B L E S E R V I C E C H A N N E L L I N E U P BASIC 55 Bravo 447 SEC Network 675 STARZ Cinema East 110 Weather Channel HD 2 WEEK-D3, CW, Peoria 56 Lifetime Television 448 FOX Sports 2 676 STARZ Kids & Family East 111 GETTV 3 WEEK-D2, ABC, 19 Peoria 57 USA Network 453 FXX 677 STARZ Comedy East 112 BOUNCE HD 4 WEEK-TV, NBC, 25 Peoria 58 Paramount Network (Spike) 457 FOX Sports 1 Cinemax Multiplex 113 Antenna TV HD 5 WMBD CBS 31 Peoria 59 Comedy Central 458 Discovery Life 600 Cinemax East 114 FOX Sports Midwest PLUS HD 6 WTVP PBS 47 Peoria 60 FX 465 MTV 601 Cinemax West 115 NFL Network HD 7 TBS Superstation 61 TNT 466 MTV2 602 More Max East 116 ESPN HD 8 WYZZ FOX 43 Bloomington 62 Syfy 467 Nick Music 603 More Max West 117 Fox Sports Midwest HD 9 WGN America 63 FXX 468 BET Jams 604 Action Max East 118 Big Ten Network HD 10 WAOE UPN 59 Peoria/Blm 78 E! 470 VH1 605 Thriller Max East 119 NBC Sports Chicago HD 11 The Weather Channel 82 Oxygen 471 MTV Classic Ask about special pricing for 120 NBC Sports Chicago+HD 12 Community Channel 93 OWN 472 BET Soul HBO & Cinemax Combo 121 ESPNU HD 13 CNN 94 Investigation Discovery 474 Fuse Showtime 122 ESPN2 HD 14 Home Shopping Network 475 CMT 650 SHOWTIME East 123 NBCSN HD 15 MSNBC 476 CMT Music 651 SHOWTIME West 124 FS1 HD 16 FOX News Channel Analog Premium 477 Great American Country 652 SHOWTIME 2 East 125 OUT HD 17 FOX Business News 52 STARZ ENCORE 480 TBN Trinity Broadcasting Network 653 SHOWTIME 2 West 130 FBN HD 18 CNBC Digital Channels 490 FX Movie Channel 654 SHOWTIME SHOWCASE -

Basic Plus Cable $93.75
Riviera Cable www.rivierautilities.com Basic Plus Cable $93.75 (104 Channels) 23.3 WSRE World* 55.2 Bounce TV* 2 WEIQ - PBS 42 23.4 WSRE PBS Kids* 55.3 Justice Network* 3 WEAR - ABC 3 25 Lifetime Television 55.4 WFNA GRIT TV* 3.1 WEAR - ABC 3 HD* 26 Home and Garden TV 56 Disney XD 3.2 TBD* 27 Travel Channel 57 Cartoon Network 3.3 CHARGE* 28 WTBS Superstation 58 Animal Planet 4 WSRE - PBS 23 29 TNT 59 Freeform 5 WKRG - CBS 5 30 ESPNU 60 A & E Network 5.1 WKRG - CBS 5 HD* 31 WGN America 61 AMC 5.3 Me TV* 32 EWTN 62 History Channel 5.4 WKRG LAFF TV* 33 ESPN 63 Bravo 6 WFNA - CW 55 33.1 WHBR HD* 64 SyFy 7 Local Weather/WHEP 33.2 WHBR CTNi* 65 Oxygen 7.1 Local Weather/WHEP* 33.3 WHBR LifeStyle TV* 66 E! Entertainment 8 WMPV - TBN 21 34 ESPN2 67 Disney Jr. 9 WJTC - IND 44 35 ESPN Classic 68 Food Network 10 WALA - FOX 10 35.1 WFGX – MYTV 35 HD* 69 Great American Country 10.1 WALA - FOX 10 HD* 35.2 get TV* 70 OWN 10.2 COZI TV* 35.3 COMET TV* 71 C-SPAN2 10.3 WALA LAFF* 36 Fox Sports South 72 The Hallmark Channel 10.4 ESCAPE* 37 National Geographic 73 truTV 11 WPMI - NBC 15 38 Discovery Channel 74 Outdoor Channel 12 QVC 39 The Learning Channel 75 NBC Sports 13 WHBR- CTN 33 40 Fox News Channel 76 SEC Network 14 WFGX – MYTV 35 41 CNN 77 FXX 15 The Weather Channel 42 CNN Headline News 78 Fox Sports 1 15.1 WPMI - NBC 15 HD* 42.1 WEIQ - PBS 42 HD* 79 Investigation Discovery 15.2 WPMI Weather Plus* 42.2 APT Kids* 80 Tennis Channel 15.3 Stadium* 42.3 APT Create* 106.2 QVC HD* 16 Baldwin County 42.4 APT World* 108.3 SEC Rollover* Commission 43 CNBC 110.1 -

Activid® Activclient®
ActivID® ActivClient® Advanced security client protects workstations and networks with smart cards and smart USB keys HID Global’s ActivID® ActivClient® ensures strong authentication of employees, contractors and suppliers when they access enterprise resources, helping IT managers, security professionals and auditors to manage the risk of unauthorized access to workstations and networks by enabling the deployment of Zero Trust security framework. AT-A-GLANCE ACTIVCLIENT BENEFITS: • Increases security with proven As a market-leading middleware for Microsoft® Outlook®, Adobe technology that is widely adopted smart cards and smart USB keys, Acrobat® and popular web because of its user-friendly, familiar, ATM-like authentication experience ActivID ActivClient consolidates browsers), smart cards, smart card identity credentials (private keys readers and smart USB keys • Optimizes productivity with a single, versatile strong authentication for public key infrastructure [PKI] • Compatibility with major certificate tool for both Windows Login and certificates and symmetric keys for authorities and encryption utilities Remote Access (e.g., PIN-protected one-time password [OTP] generation) PKI certificates or OTPs for VPN) • Simple automated deployment, on a single, secure, portable updates and diagnostics • Improves compliance with device. This capability, combined government and industry with support for a wide range of • An open, standards-based regulations desktop and network applications, architecture, which is easily • Reduces costs with easy -

Joint Statement of Sumner M. Redstone Chairman and Chief Executive Officer Viacom Inc
CORE Metadata, citation and similar papers at core.ac.uk Provided by Indiana University Bloomington Maurer School of Law Federal Communications Law Journal Volume 52 | Issue 3 Article 3 5-2000 Joint Statement of Sumner M. Redstone Chairman and Chief Executive Officer Viacom Inc. and Mel Karmazin President and Chief Executive Officer of CBS Corp. Summer M. Redstone Viacom Mel Karmazin CBS Follow this and additional works at: http://www.repository.law.indiana.edu/fclj Part of the Antitrust and Trade Regulation Commons, and the Communications Law Commons Recommended Citation Redstone, Summer M. and Karmazin, Mel (2000) "Joint Statement of Sumner M. Redstone Chairman and Chief Executive Officer Viacom Inc. and Mel Karmazin President and Chief Executive Officer of CBS Corp.," Federal Communications Law Journal: Vol. 52: Iss. 3, Article 3. Available at: http://www.repository.law.indiana.edu/fclj/vol52/iss3/3 This Article is brought to you for free and open access by the Law School Journals at Digital Repository @ Maurer Law. It has been accepted for inclusion in Federal Communications Law Journal by an authorized administrator of Digital Repository @ Maurer Law. For more information, please contact [email protected]. Joint Statement of Sumner M. Redstone Chairman and Chief Executive Officer Viacom Inc. and Mel Karmazin President and Chief Executive Officer of CBS Corp.* Viacom CBS I. INTRODUCTION ............................................................................. 499 II. DEPARTMENT OF JUSTICE REVIEW .............................................. 503 III. FEDERAL COMMUNICATIONS COMMISSION REVIEW ................... 507 I. INTRODUCTION On September 6, 1999, Viacom Inc. and CBS Corporation agreed to combine the two companies in a merger of equals. Sumner Redstone will lead the new company, to be called Viacom, in his continued role as Chairman and Chief Executive Officer, as well as majority shareholder. -

Hawaiian Telcom TV Channel Packages
Hawaiian Telcom TV 604 Stingray Everything 80’s ADVANTAGE PLUS 1003 FOX-KHON HD 1208 BET HD 1712 Pets.TV 525 Thriller Max 605 Stingray Nothin but 90’s 21 NHK World 1004 ABC-KITV HD 1209 VH1 HD MOVIE VARIETY PACK 526 Movie MAX Channel Packages 606 Stingray Jukebox Oldies 22 Arirang TV 1005 KFVE (Independent) HD 1226 Lifetime HD 380 Sony Movie Channel 527 Latino MAX 607 Stingray Groove (Disco & Funk) 23 KBS World 1006 KBFD (Korean) HD 1227 Lifetime Movie Network HD 381 EPIX 1401 STARZ (East) HD ADVANTAGE 125 TNT 608 Stingray Maximum Party 24 TVK1 1007 CBS-KGMB HD 1229 Oxygen HD 382 EPIX 2 1402 STARZ (West) HD 1 Video On Demand Previews 126 truTV 609 Stingray Dance Clubbin’ 25 TVK2 1008 NBC-KHNL HD 1230 WE tv HD 387 STARZ ENCORE 1405 STARZ Kids & Family HD 2 CW-KHON 127 TV Land 610 Stingray The Spa 28 NTD TV 1009 QVC HD 1231 Food Network HD 388 STARZ ENCORE Black 1407 STARZ Comedy HD 3 FOX-KHON 128 Hallmark Channel 611 Stingray Classic Rock 29 MYX TV (Filipino) 1011 PBS-KHET HD 1232 HGTV HD 389 STARZ ENCORE Suspense 1409 STARZ Edge HD 4 ABC-KITV 129 A&E 612 Stingray Rock 30 Mnet 1017 Jewelry TV HD 1233 Destination America HD 390 STARZ ENCORE Family 1451 Showtime HD 5 KFVE (Independent) 130 National Geographic Channel 613 Stingray Alt Rock Classics 31 PAC-12 National 1027 KPXO ION HD 1234 DIY Network HD 391 STARZ ENCORE Action 1452 Showtime East HD 6 KBFD (Korean) 131 Discovery Channel 614 Stingray Rock Alternative 32 PAC-12 Arizona 1069 TWC SportsNet HD 1235 Cooking Channel HD 392 STARZ ENCORE Classic 1453 Showtime - SHO2 HD 7 CBS-KGMB 132 -
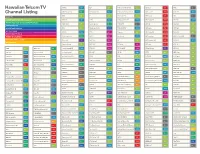
Hawaiian Telcom TV Channel Listing
Hawaiian Telcom TV CMT HD 1200 DIY 234 FOX Sports Prime Ticket 82 HBO East 501 KFVE 13 Channel Listing CMT Pure Country 201 DIY Network HD 1234 FOX Sports Prime Ticket HD 1082 HBO East HD 1501 KFVE HD* 1013 CNBC 176 E! 240 FOX Sports West 81 HBO Family 507 KHII 5 BASIC TV ADVANTAGE (INCLUDES BASIC TV) CNBC HD 1176 E! HD 1240 FOX Sports West HD 1081 HBO Family HD 1507 KHII HD* 1005 ADVANTAGE PLUS (INCLUDES ADVANTAGE) CNBC World 177 Eleven Sports 91 FOX-KHON 3 HBO HD 1502 KHJZ 93.9 665 ADVANTAGE HD ADVANTAGE PLUS HD CNN 172 Eleven Sports HD 1091 FOX-KHON HD* 1003 HBO Latino 512 KHPR 88.1 661 HD PLUS PACK *HD SERVICE WITH BASIC TV PACK includes these channels. CNN HD 1172 EPIX 381 Freeform 122 HBO Latino HD 1512 Kid’s Stuff 627 MOVIE VARIETY PACK CNN International 304 EPIX 2 382 Freeform HD 1122 HBO Signature 505 KIKU-TV (Jpn/UPN) 20 PREMIUM CHANNELS INTERNATIONAL / OTHER Comedy.TV 1707 EPIX 2 HD 1382 FX 124 HBO Signature HD 1505 KIKU HD* 1020 PAY PER VIEW Comedy Central 142 EPIX 3 HD 1383 FX Movie 398 HBO Zone 511 KINE 105.1 675 A&E 129 BET Soul 211 Comedy Central HD 1142 EPIX HD 1381 FX Movie HD 1398 HDNet Movies 1703 KIPO 89.3 662 A&E HD 1129 Big Ten Network 79 Cooking Channel 235 ESCAPE 46 FX HD 1124 HGTV 232 KKEA 1420 678 ABC-KITV 4 Big Ten Network HD 1079 Cooking Channel HD 1235 ESPN 70 FXX 110 HGTV HD 1232 KORL 101.1 672 ABC-KITV HD* 1004 Bloomberg TV 171 COZI 15 ESPN Classic Sports 71 FXX HD 1110 History Channel 133 KPHW 104.3 674 Action Max 523 Bloomberg TV HD 1171 Crime & Investigation 303 ESPN HD 1070 FYI 300 History Channel HD -

Joint Statement of Sumner M. Redstone Chairman and Chief Executive Officer Viacom Inc
Federal Communications Law Journal Volume 52 Issue 3 Article 3 5-2000 Joint Statement of Sumner M. Redstone Chairman and Chief Executive Officer Viacom Inc. and Mel Karmazin esidentPr and Chief Executive Officer of CBS Corp. Summer M. Redstone Viacom Mel Karmazin CBS Follow this and additional works at: https://www.repository.law.indiana.edu/fclj Part of the Antitrust and Trade Regulation Commons, and the Communications Law Commons Recommended Citation Redstone, Summer M. and Karmazin, Mel (2000) "Joint Statement of Sumner M. Redstone Chairman and Chief Executive Officer Viacom Inc. and Mel Karmazin esidentPr and Chief Executive Officer of CBS Corp.," Federal Communications Law Journal: Vol. 52 : Iss. 3 , Article 3. Available at: https://www.repository.law.indiana.edu/fclj/vol52/iss3/3 This Article is brought to you for free and open access by the Law School Journals at Digital Repository @ Maurer Law. It has been accepted for inclusion in Federal Communications Law Journal by an authorized editor of Digital Repository @ Maurer Law. For more information, please contact [email protected]. Joint Statement of Sumner M. Redstone Chairman and Chief Executive Officer Viacom Inc. and Mel Karmazin President and Chief Executive Officer of CBS Corp.* Viacom CBS I. INTRODUCTION ............................................................................. 499 II. DEPARTMENT OF JUSTICE REVIEW .............................................. 503 III. FEDERAL COMMUNICATIONS COMMISSION REVIEW ................... 507 I. INTRODUCTION On September 6, 1999, Viacom Inc. and CBS Corporation agreed to combine the two companies in a merger of equals. Sumner Redstone will lead the new company, to be called Viacom, in his continued role as Chairman and Chief Executive Officer, as well as majority shareholder. -

Harbor Communications
HARBOR COMMUNICATIONS - TELEVISION LINE-UP Note: HD Channels may not be available until the end of October, at which time it will require another channel scan of your TV's. Chan Channel Chan Channel Type Channel Name Type Channel Name # Abbv. # Abbv. 3 ABC-3 ABC 57 Bravo BRAVO 3-1 ABC-3 HD ABC-3-HD 58 Comedy Central CMDY 5 CBS-5 CBS-5 59 C-SPAN CSPN 5-1 CBS-5 HD CBS-5-HD 60 C-SPAN2 CSPN2 6 CBS-5 Radar CBS-5 RADAR 61 Cooking Channel COOK 9-1 Local Channel HD LOCAL-HD 62 Food Network FOOD Local Channels 10 FOX-10 FOX-10 63 Discovery Channel DISC 10-1 FOX-10 HD FOX-10-HD 64 DIY DIY 12 Bloomberg Television BLOOM 65 E! E! 13 CNBC CNBC 66 EWTN EWTN 14 CNBC World CNBCW 67 FX FXNWS 15 NBC-15 NBC-15 68 G4 G4 15-1 NBC-15 HD NBC-15-HD 69 Game Show Network GSN 16 NBC-15 Weather Plus NBC-15w+ 70 Hallmark Channel HALMRK 17 CNN CNN 71 HGTV HGTV News/Weather 18 FOX NEWS CHANNEL FXNWS 72 History Channel HIST 19 HLN HLN 73 IFC IFC 20 msNBC MSNBC 74 Investigation Discovery ID 21 Weather Channel TWC 75 ION ION Variety 22 CBS College Sports CBSSN 76 Lifetime LIFE 23 Fox Soccer FSC 77 Military Channel MIL 24 ESPN ESPN 78 NATIONAL GEOGRAPHIC NTGEO 25 ESPN2 ESPN2 79 Oprah Winfrey Network Oxygen OWN 26 ESPNNEWS ESPNNEWS 80 RFD-TV RFD-TV 27 ESPNU ESPNU 81 Science Channel SCI 28 ESPNCLASSIC ESPNCLASSIC 82 Style STYLE 29 Golf Channel GOLF 83 SYFY SYFY Sports 30 NFL Network NFL 84 TBN TBN 31 Outdoor Channel OTDCH 85 TBS TBS 32 SPEED SPEED 86 TNT TNT 33 Spike TV SPIKE 87 Travel Channel TRV 34 Tennis Channel TENNIS 88 truTv TRU 35 Versus VS 89 TV Land TVLND 36 ABC -

Resume: Tony Westman DGA, DGC, CSC Photographic Exhibits Simon
Resume: Tony Westman DGA, DGC, CSC Photographic Exhibits Simon Fraser University, Centre for the Arts: 1969 Children of Bella Coola ( One Man Show) Simon Fraser University, Centre for the Arts 1970 Man vs. Environment (One Man Show) National Film Board Still Division Archive 1970 Image Series Six ( Survey of Contemporary Photography) Vancouver Public Library 1971 Selected Works (One Man Show) National Gallery of Canada Collection 1973 Centaur Theater Gallery, Montreal 1973 Dark Visions (Group Show) Canada Council Short Term Grant for Still Photography 1973 Gallery Of Photography, North Vancouver 1974 Rites de Passage (One Man Show) Vancouver Gallery of Photography 1975 Current Works (Group Show) Simon Fraser University Gallery 1981 Artists in Vancouver (Group Show) Beau Xi Gallery 1983 Portraits of Vancouver Artists Presentation House Gallery 2003 Unfinished Business (Group Show) West Vancouver Ferry Building Gallery 2004 Polar Bears (Group Show) Film Director 2007 The 4400 USA Cable/Paramount series Executive Producer: Ira Steven Behr/Scott Peters `Producer: Kathy Gilroy-Sereda No Exit 2004 Dead Like Me:. MGM/Showtime Executive Producer: John Masius Producer: Steve Beers Be Still My Heart 2000- Fearing Mind:.Fox Family Executive Producer: Dan Angel Producer: JP Finn Maximum-Security 1999- Higher Ground:. Lions Gate Films Executive Producer: Doug Swartz/Michael Braverman Producer: Gordon Mark/Harold Tichenor Our Strongest Link 1998- The Crow:. Polygram Executive Producer: Bryce Zabel Like its 1999 1996-98- The Sentinel: UPN/Paramount Executive Producer: Danny Bilson/Paul DeMeo Producer: Bob Hargrove True Lies (Director and DoP credit) Mirror Image Blind Man's Bluff Poachers ( Writer and Director Credit) Sentinel Too Smart Alec(Director and Dop Credit) 1992-Charlton Heston Presents the Bible. -

CAC Broch:Layout 1 10/5/09 10:55 AM Page 1
CAC Broch:Layout 1 10/5/09 10:55 AM Page 1 Introducing a bizhub Solution for: Common Access Card (CAC) and Personal Identification Verification (PIV) Card Authentication CAC Broch:Layout 1 10/5/09 10:55 AM Page 2 WHO’S USING YOUR MFPS? WHICH DOCUMENTS ARE THEY SCANNING – AND WHERE ARE THEY SENDING YOUR MOST SENSITIVE INFORMATION? TO ANSWER THESE CRITICALLY IMPORTANT QUESTIONS, KONICA MINOLTA HAS TEAMED WITH ACTIVIDENTITY™ CORPORATION IN CREATING THE BIZHUB CAC (COMMON ACCESS CARD) & PIV (PERSONAL IDENTIFICATION VERIFICATION) CARD SOLUTION: A COMPREHENSIVE AUTHENTICATION SYSTEM FOR THE DEPARTMENT OF DEFENSE (DOD) AND OTHER GOVERNMENT FACILITIES UTILIZING EITHER CAC OR PIV CARD AUTHENTICATION. Who? Which? Where? With bizhub, you’ll know the answer. A smart solution for digital ID. Increase security, speed workflow. ActivIdentity and Konica Minolta. CAC and PIV cards represent the latest advance The Konica Minolta bizhub CAC & PIV Solution is This partnership solution fulfills the technically in “smart card” identification. Used by the United a comprehensive application layer developed to aggressive security requirements of the States Department of Defense as a standard ID for reside within one or more bizhub MFP devices. government – and ensures compliance with military, government and civilian employees, CAC It meets the federal government’s requirement the latest security standards and mandates, and PIV cards are used for general identification for “two factor” authentication and facilitates including FIPS 140, FIPS 201, and ISO 15408 purposes – and can also be used to control access the use of public key information (PKI) (Common Criteria) Security Certification at to computers, networks, and facilities.