AFS Directory Access Rights [Pdf]
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
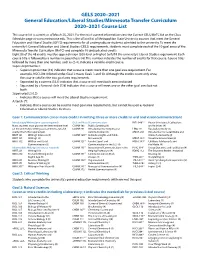
General Education and Liberal Studies Course List
GELS 2020–2021 General Education/Liberal Studies/Minnesota Transfer Curriculum 2020–2021 Course List This course list is current as of March 25, 2021. For the most current information view the Current GELS/MnTC list on the Class Schedule page at www.metrostate.edu. This is the official list of Metropolitan State University courses that meet the General Education and Liberal Studies (GELS) requirements for all undergraduate students admitted to the university. To meet the university’s General Education and Liberal Studies (GELS) requirements, students must complete each of the 10 goal areas of the Minnesota Transfer Curriculum (MnTC) and complete 48 unduplicated credits. Eight (8) of the 48 credits must be upper division (300-level or higher) to fulfill the university’s Liberal Studies requirement. Each course title is followed by a number in parenthesis (4). This number indicates the number of credits for that course. Course titles followed by more than one number, such as (2-4), indicate a variable-credit course. Superscript Number: • Superscript number (10) indicates that a course meets more than one goal area requirement. For example, NSCI 20410 listed under Goal 3 meets Goals 3 and 10. Although the credits count only once, the course satisfies the two goal area requirements. • Separated by a comma (3,LS) indicates that a course will meet both areas indicated. • Separated by a forward slash (7/8) indicates that a course will meet one or the other goal area but not both. Superscript LS (LS): • Indicates that a course will meet the Liberal Studies requirement. Asterisk (*): • Indicates that a course can be used to meet goal area requirements, but cannot be used as General Education or Liberal Studies Electives. -

Filesystem Hierarchy Standard
Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Filesystem Hierarchy Standard LSB Workgroup, The Linux Foundation Version 3.0 Publication date March 19, 2015 Copyright © 2015 The Linux Foundation Copyright © 1994-2004 Daniel Quinlan Copyright © 2001-2004 Paul 'Rusty' Russell Copyright © 2003-2004 Christopher Yeoh Abstract This standard consists of a set of requirements and guidelines for file and directory placement under UNIX-like operating systems. The guidelines are intended to support interoperability of applications, system administration tools, development tools, and scripts as well as greater uniformity of documentation for these systems. All trademarks and copyrights are owned by their owners, unless specifically noted otherwise. Use of a term in this document should not be regarded as affecting the validity of any trademark or service mark. Permission is granted to make and distribute verbatim copies of this standard provided the copyright and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this standard under the conditions for verbatim copying, provided also that the title page is labeled as modified including a reference to the original standard, provided that information on retrieving the original standard is included, and provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this standard into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the copyright holder. Dedication This release is dedicated to the memory of Christopher Yeoh, a long-time friend and colleague, and one of the original editors of the FHS. -

Consolidate Home Directories to Improve Workforce Productivity
Solution brief Consolidate home directories to improve workforce productivity HPE 3PAR File Persona Software Empower and enable users while increasing security Efficient: Improve your primary storage efficiency and control • One-third the data center footprint and significant power savings • One converged capacity eliminates Challenge Truly converged storage for wasted block or file space reservation home directory consolidation Localized user data with inadequate and Effortless: Simplify your storage inefficient protection and control HPE 3PAR StoreServ is highly efficient, deployment and administration Every IT organization has a need to store • Autonomic provisioning of all capacity flash-optimized storage engineered for and manage user-generated data such as the true convergence of block, file, and • Single, simple, and streamlined business documents, images, audio, and administration of block, file, and object access. HPE 3PAR Operating System object access video files. Traditionally, this has been done and converged controllers incorporate in local home directories on individual users’ multi-protocol support into the heart Bulletproof: Deploy your file shares laptops and desktops resulting in higher of the system architecture. This unique with confidence than necessary client device costs, ineffective • Resilient Mesh-Active architecture solution delivers tightly integrated, truly and intrusive backup processes, complex converged storage for provisioning both • Mission-critical proven HPE file system and time-consuming restore processes, and block volumes for server workloads and file poor data governance. IT needs a solution and object shares for client workloads such that maximizes workforce productivity while as home directory consolidation—efficiently, ensuring that data is effectively protected, effortlessly, and without compromise. secured, and controlled—all with minimal cost and effort. -
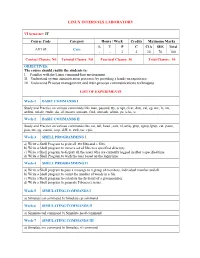
LINUX INTERNALS LABORATORY III. Understand Process
LINUX INTERNALS LABORATORY VI Semester: IT Course Code Category Hours / Week Credits Maximum Marks L T P C CIA SEE Total AIT105 Core - - 3 2 30 70 100 Contact Classes: Nil Tutorial Classes: Nil Practical Classes: 36 Total Classes: 36 OBJECTIVES: The course should enable the students to: I. Familiar with the Linux command-line environment. II. Understand system administration processes by providing a hands-on experience. III. Understand Process management and inter-process communications techniques. LIST OF EXPERIMENTS Week-1 BASIC COMMANDS I Study and Practice on various commands like man, passwd, tty, script, clear, date, cal, cp, mv, ln, rm, unlink, mkdir, rmdir, du, df, mount, umount, find, unmask, ulimit, ps, who, w. Week-2 BASIC COMMANDS II Study and Practice on various commands like cat, tail, head , sort, nl, uniq, grep, egrep,fgrep, cut, paste, join, tee, pg, comm, cmp, diff, tr, awk, tar, cpio. Week-3 SHELL PROGRAMMING I a) Write a Shell Program to print all .txt files and .c files. b) Write a Shell program to move a set of files to a specified directory. c) Write a Shell program to display all the users who are currently logged in after a specified time. d) Write a Shell Program to wish the user based on the login time. Week-4 SHELL PROGRAMMING II a) Write a Shell program to pass a message to a group of members, individual member and all. b) Write a Shell program to count the number of words in a file. c) Write a Shell program to calculate the factorial of a given number. -

APPENDIX a Aegis and Unix Commands
APPENDIX A Aegis and Unix Commands FUNCTION AEGIS BSD4.2 SYSS ACCESS CONTROL AND SECURITY change file protection modes edacl chmod chmod change group edacl chgrp chgrp change owner edacl chown chown change password chpass passwd passwd print user + group ids pst, lusr groups id +names set file-creation mode mask edacl, umask umask umask show current permissions acl -all Is -I Is -I DIRECTORY CONTROL create a directory crd mkdir mkdir compare two directories cmt diff dircmp delete a directory (empty) dlt rmdir rmdir delete a directory (not empty) dlt rm -r rm -r list contents of a directory ld Is -I Is -I move up one directory wd \ cd .. cd .. or wd .. move up two directories wd \\ cd . ./ .. cd . ./ .. print working directory wd pwd pwd set to network root wd II cd II cd II set working directory wd cd cd set working directory home wd- cd cd show naming directory nd printenv echo $HOME $HOME FILE CONTROL change format of text file chpat newform compare two files emf cmp cmp concatenate a file catf cat cat copy a file cpf cp cp Using and Administering an Apollo Network 265 copy std input to std output tee tee tee + files create a (symbolic) link crl In -s In -s delete a file dlf rm rm maintain an archive a ref ar ar move a file mvf mv mv dump a file dmpf od od print checksum and block- salvol -a sum sum -count of file rename a file chn mv mv search a file for a pattern fpat grep grep search or reject lines cmsrf comm comm common to 2 sorted files translate characters tic tr tr SHELL SCRIPT TOOLS condition evaluation tools existf test test -

The Complete Freebsd
The Complete FreeBSD® If you find errors in this book, please report them to Greg Lehey <grog@Free- BSD.org> for inclusion in the errata list. The Complete FreeBSD® Fourth Edition Tenth anniversary version, 24 February 2006 Greg Lehey The Complete FreeBSD® by Greg Lehey <[email protected]> Copyright © 1996, 1997, 1999, 2002, 2003, 2006 by Greg Lehey. This book is licensed under the Creative Commons “Attribution-NonCommercial-ShareAlike 2.5” license. The full text is located at http://creativecommons.org/licenses/by-nc-sa/2.5/legalcode. You are free: • to copy, distribute, display, and perform the work • to make derivative works under the following conditions: • Attribution. You must attribute the work in the manner specified by the author or licensor. • Noncommercial. You may not use this work for commercial purposes. This clause is modified from the original by the provision: You may use this book for commercial purposes if you pay me the sum of USD 20 per copy printed (whether sold or not). You must also agree to allow inspection of printing records and other material necessary to confirm the royalty sums. The purpose of this clause is to make it attractive to negotiate sensible royalties before printing. • Share Alike. If you alter, transform, or build upon this work, you may distribute the resulting work only under a license identical to this one. • For any reuse or distribution, you must make clear to others the license terms of this work. • Any of these conditions can be waived if you get permission from the copyright holder. Your fair use and other rights are in no way affected by the above. -

Filesystem Hierarchy Standard
Filesystem Hierarchy Standard Filesystem Hierarchy Standard Group Edited by Rusty Russell Daniel Quinlan Filesystem Hierarchy Standard by Filesystem Hierarchy Standard Group Edited by Rusty Russell and Daniel Quinlan Published November 4 2003 Copyright © 1994-2003 Daniel Quinlan Copyright © 2001-2003 Paul ’Rusty’ Russell Copyright © 2003 Christopher Yeoh This standard consists of a set of requirements and guidelines for file and directory placement under UNIX-like operating systems. The guidelines are intended to support interoperability of applications, system administration tools, development tools, and scripts as well as greater uniformity of documentation for these systems. All trademarks and copyrights are owned by their owners, unless specifically noted otherwise. Use of a term in this document should not be regarded as affecting the validity of any trademark or service mark. Permission is granted to make and distribute verbatim copies of this standard provided the copyright and this permission notice are preserved on all copies. Permission is granted to copy and distribute modified versions of this standard under the conditions for verbatim copying, provided also that the title page is labeled as modified including a reference to the original standard, provided that information on retrieving the original standard is included, and provided that the entire resulting derived work is distributed under the terms of a permission notice identical to this one. Permission is granted to copy and distribute translations of this standard into another language, under the above conditions for modified versions, except that this permission notice may be stated in a translation approved by the copyright holder. Table of Contents 1. Introduction........................................................................................................................................................1 1.1. -

CS 103 Lab 1 - Linux and Virtual Machines
CS 103 Lab 1 - Linux and Virtual Machines 1 Introduction In this lab you will login to your Linux VM and write your first C/C++ program, compile it, and then execute it. 2 What you will learn In this lab you will learn the basic commands and navigation of Linux/Unix, its file system, the GNU C/C++ compiler and a few basic applications such as Gedit. Important: The Linux operating system and environment shares a vast majority of commands and methods with Unix. 3 Background Information and Notes 3.1 Software to Install on your PC Start by following the course virtual machine installation instructions found at the link below. http://cs103.usc.edu/tools-and-links/installing-course-vm/ Below is a list of recommended software you should install that will be helpful over multiple courses in CS and EE. These tools allow you to access remote servers, run GUI apps on those servers, and transfer files between your PC and those servers. For Windows: FileZilla FTP – Available from : https://software.usc.edu/index.aspx XWin-32 – Available from : https://software.usc.edu/index.aspx PuTTY – Available from : https://software.usc.edu/index.aspx For Mac: X Server: http://developer.apple.com/opensource/tools/runningx11.html Fetch FTP – Available from : https://software.usc.edu/index.aspx Reference: http://www.usc.edu/its/unix/ Last Revised: 8/29/2014 1 CS 103 Lab 1 - Linux and Virtual Machines 3.2 Getting Started with Unix1 and Accessing your Account Solaris vs. Unix vs. Linux UNIX was developed by AT&T Bell Labs in 1969. -

Downloading and Installing the Mobile Map for IOS, Android, Or Windows Device (See * Below) Common to All Devices: 1
Downloading and Installing the Mobile Map for IOS, Android, or Windows device (See * below) Common to all devices: 1. Open your browser (see ** below) and return to www.mobilehuntingmaps.com, login and your My Account page will open. 2. On the left side, click on Orders. 3. Your order will appear on the right side of the page. 4. At the end of the order row, click on View to open the details of your order. 5. Beneath the name of the State you will see Download: Download Now and the password needed to open the map file with the CarryMap app. 6. Write down the password then click on Download Now. IOS Devices: (see ** below) 1. Dependent on your version of IOS (Apple operating system) you might be asked a second time to confirm the download. 2. How the download progress is displayed on your phone’s screen varies dependent on the IOS version on your phone. On IOS 12.0 or newer, a blue circle with a down pointing arrow inside will appear and a tiny blue line will move from left to right just under the circle as the download is in progress. Be patient as some of the map data files are large. Dependent on your internet speed and your WIFI strength, the download can take several minutes. Do not try to download a file using a cell phone service, more than likely it will drop before the download is complete. 3. Once the download progress is complete (the blue circle moves up and down and the blue line disappears), the file has been downloaded. -

Introduction to Unix From
Introduction to Unix from http://cnl.web.arizona.edu Index • Operating Systems • Files • Unix File System o The Path • Ownership and Permissions o Ownership o Permissions • Copy, Move and Remove Files and Directories • Archiving and Zipping • Viewing and Editing Text Files • Size • Unix Help • Tips and Tricks o Cut and Paste o Filename Completion o Find Command o History • Clients and Servers • Communicating across machines Related Resources • Glossary • Printing • Shell Scripts Operating Systems An Operating System (e.g., Windows 95, Windows 98 etc. from Microsoft; Unix systems like Linux, Irix, and Solaris) organizes your files and talks to the hardware. This means the OS translates from the very crude organization system that really exists on your hard drive to the hierarchical system that it presents to you. Essentially, it works like this: The Hard Drive has an area set aside that holds a table of addresses or "pointers" to blocks of information on the rest of the HD. The table's content and organization, the number and size of blocks on the HD etc. are dependent upon the particular OS. Although Unix systems are not exactly the same as each other, they are very similar to one another; just as Windows 95 and Windows 98 are very similar to one another. Files (A Comparison of Windows and Unix) Under Microsoft Windows, file names consist of two parts: a main part and an extension, separated by a special character, the dot (e.g., bird.jpg, fred.xls). The extension tells Windows which program to use to open the file (e.g., *.xls files are opened by MS Excel). -

Linux File System and Linux Commands
Hands-on Keyboard: Cyber Experiments for Strategists and Policy Makers Review of the Linux File System and Linux Commands 1. Introduction Becoming adept at using the Linux OS requires gaining familiarity with the Linux file system, file permissions, and a base set of Linux commands. In this activity, you will study how the Linux file system is organized and practice utilizing common Linux commands. Objectives • Describe the purpose of the /bin, /sbin, /etc, /var/log, /home, /proc, /root, /dev, /tmp, and /lib directories. • Describe the purpose of the /etc/shadow and /etc/passwd files. • Utilize a common set of Linux commands including ls, cat, and find. • Understand and manipulate file permissions, including rwx, binary and octal formats. • Change the group and owner of a file. Materials • Windows computer with access to an account with administrative rights The Air Force Cyber College thanks the Advanced Cyber Engineering program at the Air Force Research Laboratory in Rome, NY, for providing the information to assist in educating the general Air Force on the technical aspects of cyberspace. • VirtualBox • Ubuntu OS .iso File Assumptions • The provided instructions were tested on an Ubuntu 15.10 image running on a Windows 8 physical machine. Instructions may vary for other OS. • The student has administrative access to their system and possesses the right to install programs. • The student’s computer has Internet access. 2. Directories / The / directory or root directory is the mother of all Linux directories, containing all of the other directories and files. From a terminal users can type cd/ to move to the root directory. -

Permissions and Ownership
Getting Started with Linux: Novell’s Guide to CompTIA’s Linux+ Objective 1 Understand User and Group Configuration Files Information on users and groups on a Linux system is kept in the following files: ■ /etc/passwd ■ /etc/shadow ■ /etc/group Whenever possible, you should not modify these files with an editor. Instead, use the Security and Users modules in YaST or the command line tools described in the next objective, “Manage User Accounts and Groups from the Command Line” on 7-12. Modifying these files with an editor can lead to errors (especially in /etc/shadow), such as a user—including the user root—no longer being able to log in. To ensure consistency of these files, you need to understand how to ■ Check /etc/passwd and /etc/shadow ■ Convert Passwords to and from Shadow /etc/passwd The file /etc/passwd stores information for each user. In the past, UNIX and Linux users were handled in a single file: /etc/passwd. The user name, the UID, the home directory, the standard shell, and the encrypted password were all stored in this file. The password was encrypted using the function crypt (man 3 crypt). In principle, the plain text password could not be deciphered from the encrypted password. 7-2 Version 2 Use the Command Line Interface to Administer the System However, there are programs (such as john) that use dictionaries to encrypt various passwords with crypt, and then compare the results with the entries in the file /etc/passwd. With the calculation power of modern computers, simple passwords can be “guessed” within minutes.