January 2019 Slides .Pdf Format
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CPAS04 Authenticator Options Version 1.0 11 November 2015
GSM Association Non-confidential Official Document PDATA.03 - CPAS04 Authenticator Options CPAS04 Authenticator Options Version 1.0 11 November 2015 This is a Non-binding Permanent Reference Document of the GSMA Security Classification: Non-confidential Access to and distribution of this document is restricted to the persons permitted by the security classification. This document is confidential to the Association and is subject to copyright protection. This document is to be used only for the purposes for which it has been supplied and information contained in it must not be disclosed or in any other way made available, in whole or in part, to persons other than those permitted under the security classification without the prior written approval of the Association. Copyright Notice Copyright © 2016 GSM Association Disclaimer The GSM Association (“Association”) makes no representation, warranty or undertaking (express or implied) with respect to and does not accept any responsibility for, and hereby disclaims liability for the accuracy or completeness or timeliness of the information contained in this document. The information contained in this document may be subject to change without prior notice. Antitrust Notice The information contain herein is in full compliance with the GSM Association’s antitrust compliance policy. V1.0 Page 1 of 38 GSM Association Non-confidential Official Document PDATA.03 - CPAS04 Authenticator Options Table of Contents 1 Introduction 3 1.1 Overview 3 1.2 Scope 3 1.3 Abbreviations 3 1.4 References 5 2 Level -

Modern Password Security for System Designers What to Consider When Building a Password-Based Authentication System
Modern password security for system designers What to consider when building a password-based authentication system By Ian Maddox and Kyle Moschetto, Google Cloud Solutions Architects This whitepaper describes and models modern password guidance and recommendations for the designers and engineers who create secure online applications. A related whitepaper, Password security for users, offers guidance for end users. This whitepaper covers the wide range of options to consider when building a password-based authentication system. It also establishes a set of user-focused recommendations for password policies and storage, including the balance of password strength and usability. The technology world has been trying to improve on the password since the early days of computing. Shared-knowledge authentication is problematic because information can fall into the wrong hands or be forgotten. The problem is magnified by systems that don't support real-world secure use cases and by the frequent decision of users to take shortcuts. According to a 2019 Yubico/Ponemon study, 69 percent of respondents admit to sharing passwords with their colleagues to access accounts. More than half of respondents (51 percent) reuse an average of five passwords across their business and personal accounts. Furthermore, two-factor authentication is not widely used, even though it adds protection beyond a username and password. Of the respondents, 67 percent don’t use any form of two-factor authentication in their personal life, and 55 percent don’t use it at work. Password systems often allow, or even encourage, users to use insecure passwords. Systems that allow only single-factor credentials and that implement ineffective security policies add to the problem. -

Linux Kernel Contributions by ANSSI
Linux kernel contributions by ANSSI Yves-Alexis Perez ANSSI LSS-EU 2018 Introduction Who am I? Yves-Alexis Perez ANSSI head of software and hardware architectures lab I OS security (Linux, micro-kernels) I mobile and embedded device security I CLIP OSa development Debian developer I security team I Linux kernel packaging I Xfce, strongSwan, imobiledevice packaging Mostly interested in low-level security and hardening a. https://www.clip-os.org [email protected] Linux kernel contributions by ANSSI LSS-EU 2018 3/28 ANSSI Missions I not an intelligence agency I protect French administration & industry networks I defensive only Labs I pool of expertise on relevant area: cryptography, network, OS, … I research & development I academic publications I free-software contributions [email protected] Linux kernel contributions by ANSSI LSS-EU 2018 4/28 French government & free software User I Large user of free software I Linux distributions widely used accross the whole government I cost reason, sometime about control Contributor I some large projects (SPIP, …) I DINSIC maintains a repository list[8] I 2016 Digital Republic law[11] introduced open-data by default I including code [email protected] Linux kernel contributions by ANSSI LSS-EU 2018 5/28 Current situation with Linux Linux usage quite diverse I Linux servers from various distribution I Linux-based appliances (firewalls, IDS, VPN…) I some Linux workstations ANSSI can’t secure everything downstream I upstream work benefits more people I Linux distributions -

Microsoft Ignite 2018 September 24–28 // Orlando, FL Contents | 2 Contents
Microsoft Ignite 2018 September 24–28 // Orlando, FL contents | 2 contents Foreword by Frank X. Shaw 5 Chapter 1 Security 6 1.1 Microsoft Threat Protection 1.2 Password-free sign-in for thousands of apps 1.3 Microsoft Secure Score 1.4 Azure confidential computing public preview 1.5 Modern Compliance enhancements 1.6 Expansion of work to bring the entire tech sector together through the Cybersecurity Tech Accord Chapter 2 Artificial intelligence and data 8 2.1 Artificial intelligence 2.1.1 AI for Humanitarian Action 2.1.2 Cortana Skills Kit for Enterprise 2.1.3 New Azure Machine Learning capabilities 2.1.4 Azure Cognitive Services update – Speech Service general availability 2.1.5 Microsoft Bot Framework v4 general availability 2.1.6 Unified search across Microsoft 365 2.1.7 New AI-powered meeting features in Microsoft 365 2.1.8 Ideas in Office 2.1.9 Intelligent enhancements in Excel 2.2 Data 2.2.1 SQL Server 2019 public preview 2.2.2 Azure SQL Database Hyperscale and Managed Instance 2.2.3 Azure Data Explorer public preview 2.2.4 Azure Cosmos DB Multi-master general availability 2.2.5 Azure Databricks Delta preview 2.2.6 Azure SQL Database intelligent features 2.2.7 New Azure SQL Data Warehouse pricing tier contents | 3 Chapter 3 Internet of things and edge computing 12 3.1 Internet of things 3.1.1 Azure Digital Twins 3.1.2 Azure IoT Central general availability 3.1.3 Azure Maps: Map Control update 3.1.4 New Azure IoT Edge features and capabilities 3.1.5 Azure IoT Hub Device Provisioning Service updates 3.1.6 Azure IoT Hub message routing -

Trusted Execution Environments
Trusted Execution Environments Assaf Rosenbaum Technion - Computer Science Department - M.Sc. Thesis MSC-2019-03 - 2019 Technion - Computer Science Department - M.Sc. Thesis MSC-2019-03 - 2019 Trusted Execution Environments Research Thesis Submitted in partial fulfillment of the requirements for the degree of Master of Science in Computer Science Assaf Rosenbaum Submitted to the Senate of the Technion | Israel Institute of Technology Kislev 5779 Haifa November 2018 Technion - Computer Science Department - M.Sc. Thesis MSC-2019-03 - 2019 Technion - Computer Science Department - M.Sc. Thesis MSC-2019-03 - 2019 This research was carried out under the supervision of Prof. Eli Biham and Dr. Sara Bitan, in the Faculty of Computer Science. Acknowledgements First and foremost, I wish to thank my advisors, Prof. Eli Biham and Dr. Sara Bitan, for their incredible support during the work on thesis. Thank you for providing me the freedom to find my own path while constantly guiding and directing me. I learned a lot from both of you. I would also like to thank my parents, siblings and my parents-in-law for their help and support during this stressful time. Thank you for being there whenever I needed. A special thanks is due to my three lovely children, you sparkle my life with moment of pure joy. Most importantly, I would like to thank my beautiful wife, Lior. Thank you for your endless support, the long hours in which you worked hard to give me the time I needed to work and for always pushing me forward. You ar the light of my life and I love you very much. -
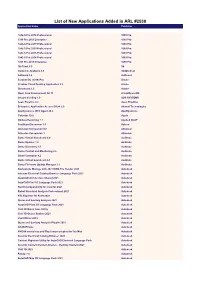
List of New Applications Added in ARL #2538 Application Name Publisher
List of New Applications Added in ARL #2538 Application Name Publisher 1042-S Pro 2018 Professional 1099 Pro 1099 Pro 2019 Enterprise 1099 Pro 1042-S Pro 2017 Professional 1099 Pro 1042-S Pro 2019 Professional 1099 Pro 1042-S Pro 2015 Professional 1099 Pro 1042-S Pro 2014 Professional 1099 Pro 1099 Pro 2015 Enterprise 1099 Pro 1E Client 5.0 1E Complete Anatomy 4.0 3D4Medical AdGuard 2.4 AdGuard Acrobat DC (2019) Pro Adobe Creative Cloud Desktop Application 5.2 Adobe Dimension 3.3 Adobe Open Java Development Kit 11 AdoptOpenJDK Integra Vending 1.0 ADS SYSTEMS Aeon Timeline 2.3 Aeon Timeline Enterprise Application Access Client 2.0 Akamai Technologies AppDynamics .NET Agent 20.4 AppDynamics Calendar 10.0 Apple Dodeca Reporting 7.1 Applied OLAP FastStats Discoverer 1.0 Apteco Atlassian Companion 0.6 Atlassian Atlassian Companion 1 Atlassian Dante Virtual Soundcard 4.0 Audinate Dante Updater 1.0 Audinate Dante Discovery 1.3 Audinate Dante Control and Monitoring 4.0 Audinate Dante Controller 4.2 Audinate Dante Virtual Soundcard 4.1 Audinate Dante Firmware Update Manager 3.1 Audinate Navisworks Manage with 2021 DWG File Reader 2021 Autodesk Inventor Electrical Catalog Browser Language Pack 2021 Autodesk AutoCAD Architecture Shared 2021 Autodesk AutoCAD Civil 3D Language Pack 2021 Autodesk Revit Interoperability for Inventor 2021 Autodesk Robot Structural Analysis Professional 2021 Autodesk STL Exporter for Revit 2020 Autodesk Storm and Sanitary Analysis 2021 Autodesk AutoCAD Plant 3D Language Pack 2021 Autodesk Civil 3D Batch Save Utility Autodesk -

A Closer Look at SQRL Research Findings
A closer look at SQRL Agenda • SQRL introduction • Related work • SQRL design details • Research questions • Research method • Research findings • Conclusion UvA-SNE-RP1 presentation 1 A closer look at SQRL SQRL introduction: trigger Secure Quick Reliable Login UvA-SNE-RP1 presentation 2 A closer look at SQRL SQRL introduction: how it works QR-scanning QR-tapping QR-clicking UvA-SNE-RP1 presentation 3 A closer look at SQRL SQRL introduction: design goals SSO 2FA out-of-band (OOB) authentication no secret(s) exchange anonymity no (additional) TTP low friction deployment UvA-SNE-RP1 presentation 4 A closer look at SQRL Related work: SSO • Open standards • OpenID • TiQR UvA-SNE-RP1 presentation 5 A closer look at SQRL SQRL design details: crypto ID site (fixed) specific secret 1-F secret 2-F Brute Elliptic Force Curve UvA-SNE-RP1 presentation 6 A closer look at SQRL SQRL design details: more crypto Compromised ID ? • ID revocation support • proves ID ownership • uses additional keys • Lock (disable) • Unlock (enable/change) UvA-SNE-RP1 presentation 7 A closer look at SQRL SQRL design details: messages UvA-SNE-RP1 presentation 8 A closer look at SQRL Research questions • How does SQRL improve authentication security compared to related solutions? • What does SQRL offer to both parties? • What constraints must be met to guaranty this behaviour? • What additional features are relevant to extend deployability? • What attacks remain feasible and what countermeasures are to be considered? UvA-SNE-RP1 presentation 9 A closer look at SQRL -

Zero-Knowledge User Authentication: an Old Idea Whose Time Has Come
Zero-Knowledge User Authentication: An Old Idea Whose Time Has Come Laurent Chuat, Sarah Plocher, and Adrian Perrig ETH Zurich Abstract User authentication can rely on various factors (e.g., a pass- word, a cryptographic key, and/or biometric data) but should not re- veal any secret information held by the user. This seemingly paradoxical feat can be achieved through zero-knowledge proofs. Unfortunately, naive password-based approaches still prevail on the web. Multi-factor authen- tication schemes address some of the weaknesses of the traditional login process, but generally have deployability issues or degrade usability even further as they assume users do not possess adequate hardware. This as- sumption no longer holds: smartphones with biometric sensors, cameras, short-range communication capabilities, and unlimited data plans have become ubiquitous. In this paper, we show that, assuming the user has such a device, both security and usability can be drastically improved using an augmented password-authenticated key agreement (PAKE) pro- tocol and message authentication codes. 1 Introduction User authentication still typically involves transmitting a plaintext password to the web server, which is problematic for many reasons. First, an attacker could obtain the user’s password using malware, a keystroke logger, phishing, or a man-in-the-middle attack. Second, the user might be using the same password on different websites, allowing a malicious server operator to impersonate the user. Third, if the website’s database is breached, although passwords may be protected by a hash function, a brute-force attack could reveal low-entropy pass- words. Fourth, as password-reuse and low-entropy passwords are problematic, users are constantly advised to pick new, long, complicated passwords. -

SQRL: Anti-Phishing & Revocation
Security Now! Transcript of Episode #426 Page 1 of 30 Transcript of Episode #426 SQRL: Anti-Phishing & Revocation Description: After following-up on a week chockful of interesting security news, Steve and Leo continue with their discussion of SQRL, the Secure QR code Login system, to discuss two recent innovations in the system that bring additional valuable features. High quality (64 kbps) mp3 audio file URL: http://media.GRC.com/sn/SN-426.mp3 Quarter size (16 kbps) mp3 audio file URL: http://media.GRC.com/sn/sn-426-lq.mp3 SHOW TEASE: It's time for Security Now!. Steve Gibson has the latest - yes, another Java patch - and more information about Lavabit. More information about the NSA, too. What is a Ferret's Cannon? It's coming up next on Security Now!. Leo Laporte: This is Security Now! with Steve Gibson, Episode 426, recorded October 16th, 2013: SQRL, Anti-Phishing, and Revocation. It's time for Security Now!, the show that covers your privacy and security online. Somebody in the chatroom before we began the show today, Steve Gibson, Explainer in Chief, said we should call it "Insecurity Now!" since it really talks mostly about insecure. But not today. Today we're going to talk about better security. Steve Gibson: Well, yeah. Actually, this is one of those episodes where so much happened in the last week in security news that, I mean, we just - there's a whole bunch of really interesting stuff to talk about. And in the past when we've done that we've just said, okay, we're not going to have any major topic because too much happened. -

AZ-900 Reading Guide - Sept 2020 Document V1.0, Researched by Scott Duffy
AZ-900 Reading Guide - Sept 2020 Document v1.0, researched by Scott Duffy Don’t forget that you can watch videos on each of these topics in my very reasonably priced AZ-900: Microsoft Azure Fundamentals Exam Prep course on Udemy: https://www.udemy.com/course/az900-azure/?referralCode=CBB97C39131AE1062B29 Describe Cloud Concepts (20-25%) Identify the benefits and considerations of using cloud services ● identify the benefits of cloud computing, such as High Availability, Scalability, Elasticity, Agility, and Disaster Recovery ○ https://docs.microsoft.com/en-us/azure/architecture/framework/resiliency/over view ○ https://docs.microsoft.com/en-us/azure/architecture/guide/design-principles/re dundancy ○ https://docs.microsoft.com/en-us/azure/architecture/guide/design-principles/sc ale-out ○ https://docs.microsoft.com/en-us/azure/architecture/best-practices/auto-scalin g ○ https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/strategy/bu siness-outcomes/agility-outcomes ○ https://docs.microsoft.com/en-us/azure/architecture/framework/resiliency/mon itoring ○ https://docs.microsoft.com/en-us/azure/architecture/resiliency/recovery-loss-a zure-region ● identify the differences between Capital Expenditure (CapEx) and Operational Expenditure (OpEx) ○ https://docs.microsoft.com/en-us/azure/cloud-adoption-framework/strategy/bu siness-outcomes/fiscal-outcomes#capital-expenses-and-operating-expenses ● describe the consumption-based model ○ https://docs.microsoft.com/en-us/azure/architecture/framework/cost/design-pri ce Describe the differences -

The Developer's Guide to Azure
E-book Series The Developer’s Guide to Azure Published May 2019 May The Developer’s 2 2019 Guide to Azure 03 / 40 / 82 / Introduction Chapter 3: Securing Chapter 6: Where your application and how to deploy We’re here to help your Azure services How can Azure help secure 05 / your app? How can Azure deploy your Encryption services? Chapter 1: Getting Azure Security Center Infrastructure as Code started with Azure Logging and monitoring Azure Blueprints Containers in Azure What can Azure do for you? Azure Stack Where to host your 51 / Where to deploy, application and when? Chapter 4: Adding Azure App Service Features Azure Functions intelligence to Azure Logic Apps your application 89 / Azure Batch Containers How can Azure integrate AI Chapter 7: Share your What to use, and when? into your app? code, track work, and ship Making your application Azure Search software more performant Cognitive Services Azure Front Door Azure Bot Service How can Azure help you plan Azure Content Delivery Azure Machine Learning smarter, collaborate better, and ship Network Studio your apps faster? Azure Redis Cache Developer tooling for AI Azure Boards AI and mixed reality Azure Repos Using events and messages in Azure Pipelines 22 / your application Azure Test Plans Azure Artifacts Chapter 2: Connecting your app with data 72 / 98 / What can Azure do for Chapter 5: Connect your your data? business with IoT Chapter 8: Azure in Action Where to store your data Azure Cosmos DB How can Azure connect, secure, Walk-through: Azure portal Azure SQL Database manage, monitor, -

Le Rapport Au Format
N° 7 SÉNAT SESSION ORDINAIRE DE 2019-2020 Rapport remis à M. le Président du Sénat le 1er octobre 2019 Enregistré à la Présidence du Sénat le 1er octobre 2019 RAPPORT FAIT au nom de la commission d’enquête (1) sur la souveraineté numérique, Président M. Franck MONTAUGÉ, Rapporteur M. Gérard LONGUET, Sénateurs Tome I : Rapport (1) Cette commission est composée de : M. Franck Montaugé, président ; M. Gérard Longuet, rapporteur ; M. Patrick Chaize, Mmes Sylvie Robert, Catherine Morin-Desailly, MM. Yvon Collin, M. André Gattolin, MM. Pierre Ouzoulias et Jérôme Bignon, vice-présidents ; Mme Viviane Artigalas, MM. Jérôme Bascher, Bernard Bonne, Mme Martine Filleul, MM. Christophe-André Frassa, Loïc Hervé, Laurent Lafon, Rachel Mazuir, Stéphane Piednoir, Mmes Sophie Primas, Frédérique Puissat et M. Hugues Saury. - 3 - SOMMAIRE Pages PRINCIPALES RECOMMANDATIONS ............................................................................ 7 AVANT-PROPOS .................................................................................................................13 I. QUELS SCÉNARII FACE AUX MENACES PESANT SUR NOTRE SOUVERAINETÉ ? ..........................................................................................................17 A. LA COMPÉTITION INTENSE ENTRE ÉTATS DANS LE CYBERESPACE ..................17 1. La politique américaine : la recherche d’un leadership incontesté .......................................18 a) Des relations complexes entre les Gafam et l’État américain .................................18 b) Une politique de la