Network Address Translator Traversal Using Interactive Connectivity Establishment
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

N2N: a Layer Two Peer-To-Peer VPN
N2N: A Layer Two Peer-to-Peer VPN Luca Deri1, Richard Andrews2 ntop.org, Pisa, Italy1 Symstream Technologies, Melbourne, Australia2 {deri, andrews}@ntop.org Abstract. The Internet was originally designed as a flat data network delivering a multitude of protocols and services between equal peers. Currently, after an explosive growth fostered by enormous and heterogeneous economic interests, it has become a constrained network severely enforcing client-server communication where addressing plans, packet routing, security policies and users’ reachability are almost entirely managed and limited by access providers. From the user’s perspective, the Internet is not an open transport system, but rather a telephony-like communication medium for content consumption. This paper describes the design and implementation of a new type of peer-to- peer virtual private network that can allow users to overcome some of these limitations. N2N users can create and manage their own secure and geographically distributed overlay network without the need for central administration, typical of most virtual private network systems. Keywords: Virtual private network, peer-to-peer, network overlay. 1. Motivation and Scope of Work Irony pervades many pages of history, and computing history is no exception. Once personal computing had won the market battle against mainframe-based computing, the commercial evolution of the Internet in the nineties stepped the computing world back to a substantially rigid client-server scheme. While it is true that the today’s Internet serves as a good transport system for supplying a plethora of data interchange services, virtually all of them are delivered by a client-server model, whether they are centralised or distributed, pay-per-use or virtually free [1]. -
NAT Traversal About
NAT Traversal About Some difficulties have been encountered with devices that have poor NAT support. FreeSWITCH goes to great lengths to repair broken NAT support in phones and gateway devices. In order to aid FreeSWITCH in traversing NAT please see the External profile page. Some routers offer an Application Layer Gateway feature which can prevent FreeSWITCH NAT traversal from working. See the ALG page for more information, including how to disable it. Using STUN to aid in NAT Traversal STUN is a method to allow an end host (i.e. phone) to discover its public IP address if it is located behind a NAT . Using this method requires a STUN server on the public internet and a client on the phone. The phone's STUN client queries the STUN server for it's own public IP and transmits the information it has received in it's connection information in the SIP packets it sends to the SIP server. Enable and configure STUN settings on your phone in order correctly to report your phone's contact information to FreeSWITCH when registering. Unfortunately, not all phones have a properly working STUN client. STUN servers This site contains a list of public STUN servers: https://gist.github.com/zziuni/3741933 stun.freeswitch.org is never guaranteed to be up and running so use it in production at your own risk. There are several open source projects to run your own STUN server, e.g. STUNTMAN Using FreeSWITCH built-in methods to aid in NAT Traversal nat-options-ping This parameter causes FreeSWITCH to regularly (every 20 - 40s) send an OPTIONS packet to NATed registered endpoints in order to keep the port on the clients firewall open. -

NAT and NAT Traversal Lecturer: Andreas Müller [email protected]
NAT and NAT Traversal lecturer: Andreas Müller [email protected] NetworkIN2097 - MasterSecurity, Course WS 2008/09, Computer Chapter Networks, 9 WS 2009/2010 39 NAT: Network Address Translation Problem: shortage of IPv4 addresses . more and more devices . only 32bit address field Idea: local network uses just one IP address as far as outside world is concerned: . range of addresses not needed from ISP: just one IP address for all devices . can change addresses of devices in local network without notifying outside world . can change ISP without changing addresses of devices in local network . devices inside local net not explicitly addressable, visible by outside world (a security plus). NetworkIN2097 - MasterSecurity, Course WS 2008/09, Computer Chapter Networks, 9 WS 2009/2010 40 NAT: Network Address (and Port) Translation rest of local network Internet (e.g., home network) 10.0.0/24 10.0.0.1 10.0.0.4 10.0.0.2 138.76.29.7 10.0.0.3 All datagrams leaving local Datagrams with source or network have same single source destination in this network NAT IP address: 138.76.29.7, have 10.0.0/24 address for different source port numbers source, destination (as usual) NetworkIN2097 - MasterSecurity, Course WS 2008/09, Computer Chapter Networks, 9 WS 2009/2010 41 NAT: Network Address Translation Implementation: NAT router must: . outgoing datagrams: replace (source IP address, port #) of every outgoing datagram to (NAT IP address, new port #) . remote clients/servers will respond using (NAT IP address, new port #) as destination addr. remember (in NAT translation table) every (source IP address, port #) to (NAT IP address, new port #) translation pair -> we have to maintain a state in the NAT . -
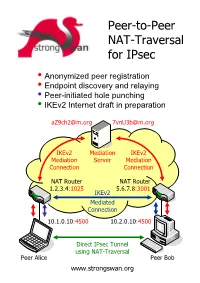
Peer-To-Peer NAT-Traversal for Ipsec
Peer-to-Peer NAT-Traversal for IPsec y Anonymized peer registration y Endpoint discovery and relaying y Peer-initiated hole punching y IKEv2 Internet draft in preparation [email protected] [email protected] IKEv2 Mediation IKEv2 Mediation Server Mediation Connection Connection NAT Router NAT Router 1.2.3.4:1025 5.6.7.8:3001 IKEv2 Mediated Connection 10.1.0.10:4500 10.2.0.10:4500 Direct IPsec Tunnel using NAT-Traversal Peer Alice Peer Bob www.strongswan.org The double NAT case - where punching holes counts! ● You are selling automation systems all over the world. In order to save on travel expenses you want to remotely diagnose and update your deployed systems via the Internet. But security counts – thus IPsec is a must! Unfortunately both you and your customer are behind NAT routers so that no direct VPN connection is possible. You are helplessly blocked! ● You own an apartment at home, in the mountains or even abroad. You want to remotely control the heating or your sophisticated intrusion detection system via ADSL or Cable access. But since you and your apartment are separated by two NAT routers your are helplessly blocked. How it works! ● Two peers want to set up a direct IPsec tunnel using the established NAT traversal mechanism of encapsulating ESP packets in UDP datagrams. Unfortunately they cannot achieve this by themselves because neither host is seen from the Internet under the standard IKE NAT-T port 4500. Therefore both peers need to set up a mediation connection with an IKEv2 mediation server. In order to prevent unsolicited connection attempts by foreign peers, the mediation connections use randomized pseudonyms as IKE peer identities. -

Problems of Ipsec in Combination with NAT and Their Solutions
Problems of IPsec in Combination with NAT and Their Solutions Alexander Heinlein Abstract As the Internet becomes more and more a part of our daily life it also evolves as an at- tractive target for security attacks, often countered by Internet Protocol Security (IPsec) to establish virtual private networks (VPNs), if secure data communication is a primary objective. Then again, to provide Internet access for hosts inside Local Area Networks, a public IP address shared among all peers is often used, achieved by Network Address Translation (NAT) deployment. IPsec, however, is incompatible with NAT, leading to a variety of problems when using both in combination. Connection establishments origi- nating from the outside are blocked and NAT, as it modifies the outer IP header, breaks IPsec’s security mechanisms. In the following we analyze problems of NAT in combination with IPsec and multiple approaches to solve them. 1 Introduction The current TCP/IP protocols originate from a time where security was not a great concern. As the traditional Internet Protocol (IP) does not provide any guarantees on delivery, the receiver cannot detect whether the sender is the same one as recorded in the protocol header or if the packet was modified during transport. Moreover an attacker may also easily replay IP packets or read sensitive information out of them. In contrast, today, as the Internet becomes more and more a part of our everyday life, a more security aware protocol is needed. To fill this gap the Internet Engineering Task Force (IETF) worked on a new standard for securing IP, called Internet Protocol Security (IPsec). -

The Impact of Network Address Translation on Peer-To-Peer Live Video Streaming Systems
The Impact of Network Address Translation on Peer-to-Peer Live Video Streaming Systems by Zhonghua Wei M.Sc., University of London, 2006 B.Eng., Beijing Univ. of Posts and Telecommunications, 2005 A Thesis Submitted in Partial Fulfillment of the Requirements for the Degree of MASTER OF SCIENCE in the Department of Computer Science c Zhonghua Wei, 2011 University of Victoria All rights reserved. This thesis may not be reproduced in whole or in part, by photocopying or other means, without the permission of the author. ii The Impact of Network Address Translation on Peer-to-Peer Live Video Streaming Systems by Zhonghua Wei M.Sc., University of London, 2006 B.Eng., Beijing Univ. of Posts and Telecommunications, 2005 Supervisory Committee Dr. Jianping Pan, Supervisor (Department of Computer Science) Dr. Kui Wu, Departmental Member (Department of Computer Science) iii Supervisory Committee Dr. Jianping Pan, Supervisor (Department of Computer Science) Dr. Kui Wu, Departmental Member (Department of Computer Science) ABSTRACT Video streaming over the Internet can be very difficult under the traditional client-server model. Peer-to-peer (P2P) systems, in which each participating peer contributes its upload bandwidth to other peers while it downloads data, have been successful in file-sharing applications, and they appear to be promising in delivering video contents, too. However, the existence of network address translation (NAT) is always considered as a challenge to peer-to-peer systems. NAT has been a practical solution to the Internet Protocol version 4 (IPv4) address exhaustion problem, as it reduces the usage of IP addresses by allowing multiple private hosts to share a single public IP address, but NAT can degrade the performance of a peer-to-peer system as it limits the direction of connectivity. -

Developing P2P Protocols Across NAT Girish Venkatachalam
Developing P2P Protocols across NAT Girish Venkatachalam Abstract Hole punching is a possible solution to solving the NAT problem for P2P protocols. Network address translators (NATs) are something every software engineer has heard of, not to mention networking professionals. NAT has become as ubiquitous as the Cisco router in networking terms. Fundamentally, a NAT device allows multiple machines to communicate with the Internet using a single globally unique IP address, effectively solving the scarce IPv4 address space problem. Though not a long-term solution, as originally envisaged in 1994, for better or worse, NAT technology is here to stay, even when IPv6 addresses become common. This is partly because IPv6 has to coexist with IPv4, and one of the ways to achieve that is by using NAT technology. This article is not so much a description of how a NAT works. There already is an excellent article on this subject by Geoff Huston (see the on-line Resources). It is quite comprehensive, though plenty of other resources are available on the Internet as well. This article discusses a possible solution to solving the NAT problem for P2P protocols. What Is Wrong with NAT? NAT breaks the Internet more than it makes it. I may sound harsh here, but ask any peer-to-peer application developer, especially the VoIP folks, and they will tell you why. For instance, you never can do Web hosting behind a NAT device. At least, not without sufficient tweaking. Not only that, you cannot run any service such as FTP or rsync or any public service through a NAT device. -

Lecture 11 – Network Address Translators and NAT Traversal * Introduction
S38.3115 Signaling Protocols – Lecture Notes Spring 2015 lecture 11 S38.3115 Signaling Protocols – Lecture Notes Lecture 11 – Network Address Translators and NAT Traversal * Introduction ..................................................................................................................... 1* What are NATs and why are they needed ...................................................................... 3* Problems created by NATs to Voice Applications ......................................................... 4* Types of NATs ................................................................................................................ 4* Mapping behavior ....................................................................................................... 6* Address pooling behavior ........................................................................................... 7* Port Assignment .......................................................................................................... 8* Filtering behavior ........................................................................................................ 9* Need for optimization of NAT traversal ......................................................................... 9* STUN a toolbox for NAT traversal .............................................................................. 10* An extension to STUN: Relay operation .................................................................. 11* NAT traversal solutions: SIP Outbound ...................................................................... -

Firewall Setup and Nat Configuration Guide for H.323 / Sip Room Systems – Bluejeans 2018
FIREWALL SETUP AND NAT CONFIGURATION GUIDE FOR H.323 / SIP ROOM SYSTEMS – BLUEJEANS 2018 Firewall Setup and NAT Configuration Guide for 0 H.323 / SIP Room Systems – BlueJeans 2018 Firewall Setup and NAT Configuration Guide for H.323 / SIP Room Systems Table of Contents 1. How to setup Firewall and NAT to work with Blue Jeans Network - page 2 • Ports Used by Blue Jeans for H.323 and SIP Connections 2. Calling Blue Jeans from H.323 or SIP Room System - page 4 • Dialing Direct with URI Dial String 3. Firewall/NAT Traversal Solutions - page 6 4. Firewall and NAT Configuration - page 8 • The Problems of NAT and Firewalls for video conferencing • UDP Hole Punching • NAT (Network Address Translation) • H.323 and Firewalls 5. Blue Jeans POPs and Geo-location - page 12 6. H.323 Call Signaling Explained - page 14 • H.323 Call Flow Explained 7. H.323 Gatekeepers - page 18 • What is a H323 Gatekeeper for? • H.323 Gatekeeper functions • Gatekeepers can work in Direct or Routed Mode 8. SIP Call Flow Explained - page 20 9. STUN, TURN and ICE - page 22 • STUN, TURN, ICE Explained • STUN (Session Traversal Utilities for NAT) • Symmetric NAT is Different • TURN (Traversal Using Relays around NAT) • ICE (Interactive Connectivity Establishment) 10. Border Controllers and Proxies - page 27 • Cisco Video Communication Server (VCS) • Polycom Video Border Proxy (VBP) and Lifesize UVC Transit 11. Cisco VCS Configuration to Connect to Blue Jeans - page 29 12. SIP Proxy - page 30 13. Common Issues and How to Overcome Them - page 32 • Content Sharing Replaces Main Video Stream • No Content Sharing • Call Drops at the Same Interval or Time Frame on Each Call Attempt • Call Drops Quickly or Call Never Establishes • Video or Audio is Poor Quality 14. -

Technical Report Sce-12-04 Nat Traversal in Peer-To
TECHNICAL REPORT SCE-12-04 DEPARTMENT OF SYSTEMS AND COMPUTER ENGINEERING CARLETON UNIVERSITY NAT TRAVERSAL IN PEER -TO -PEER ARCHITECTURE Marc-André Poulin¹, Lucas Rioux Maldague¹, Alexandre Daigle¹, François Gagnon² 1 Cégep de Sainte-Foy, Canada [email protected] , [email protected] , [email protected] 2 Carleton University, Canada [email protected] Abstract. Peer-to-peer networks are well known for file sharing between multiple computers. They establish virtual tunnels between computers to transfer data, but NATs makes it harder. A NAT, Network Address Translation , is a process which transforms private IP addresses, such as 192.168.2.1, into public addresses, such as 203.0.113.40. The idea is that multiple private addresses can hide behind a single public address and thus virtually enlarge the number of allocable public IP addresses. When an application in the local network establishes a connection to Internet, the packet passes through the NAT which adjusts the IP header and maps an external port to the computer which sent the request. When packets are received from the Internet by the NAT, they are forwarded to the internal host which is mapped to the port on which the packet was received, or dropped if no mapping exists. In this paper, we will introduce you to NAT and P2P, we will discuss the numerous ways NATs use to translate private IP addresses into public ones, we will discuss known techniques used to fix the problem and we will also present how popular peer-to-peer programs bypass NATs. This paper is written so anybody with a reasonable knowledge of networking would grasp the essentials. -

N2N: a Layer Two Peer-To-Peer VPN
N2N: A Layer Two Peer-to-Peer VPN Luca Deri1 and Richard Andrews2 1 ntop.org, Pisa, Italy 2 Symstream Technologies, Melbourne, Australia {deri,andrews}@ntop.org Abstract. The Internet was originally designed as a flat data network delivering a multitude of protocols and services between equal peers. Currently, after an explosive growth fostered by enormous and heterogeneous economic interests, it has become a constrained network severely enforcing client-server communication where addressing plans, packet routing, security policies and users’ reachability are almost entirely managed and limited by access providers. From the user’s perspective, the Internet is not an open transport system, but rather a telephony-like communication medium for content consumption. This paper describes the design and implementation of a new type of peer- to-peer virtual private network that can allow users to overcome some of these limitations. N2N users can create and manage their own secure and geographically distributed overlay network without the need for central administration, typical of most virtual private network systems. Keywords: Virtual private network, peer-to-peer, network overlay. 1 Motivation and Scope of Work Irony pervades many pages of history, and computing history is no exception. Once personal computing had won the market battle against mainframe-based computing, the commercial evolution of the Internet in the nineties stepped the computing world back to a substantially rigid client-server scheme. While it is true that the today’s Internet serves as a good transport system for supplying a plethora of data interchange services, virtually all of them are delivered by a client-server model, whether they are centralised or distributed, pay-per-use or virtually free [1]. -

The Gnunet System Christian Grothoff
The GNUnet System Christian Grothoff To cite this version: Christian Grothoff. The GNUnet System. Networking and Internet Architecture [cs.NI]. Université de Rennes 1, 2017. tel-01654244 HAL Id: tel-01654244 https://hal.inria.fr/tel-01654244 Submitted on 3 Dec 2017 HAL is a multi-disciplinary open access L’archive ouverte pluridisciplinaire HAL, est archive for the deposit and dissemination of sci- destinée au dépôt et à la diffusion de documents entific research documents, whether they are pub- scientifiques de niveau recherche, publiés ou non, lished or not. The documents may come from émanant des établissements d’enseignement et de teaching and research institutions in France or recherche français ou étrangers, des laboratoires abroad, or from public or private research centers. publics ou privés. Distributed under a Creative Commons Attribution| 4.0 International License 1 Th`esed'habilitation `adiriger des recherches Universit´eede Rennes 1 Mention: Informatique The GNUnet System Christian Grothoff Soutenue le 10 octobre 2017 devant le jury compos´ede Messieurs les Professeurs: Anne-Marie Kermarrec (Universit´ede Rennes 1) Tanja Lange (Technische Universiteit Eindhoven) George Danezis (University College London) Joe Cannataci (University of Groningen) Saddek Bensalem (University of Grenoble) Au vu des rapports de Messieurs les Professeurs: Tanja Lange (Technische Universiteit Eindhoven) George Danezis (University College London) Saddek Bensalem (University of Grenoble) Revision 1.0 2 Abstract GNUnet is an alternative network stack for building secure, decentralized and privacy-preserving distributed applications. Our goal is to replace the old inse- cure Internet protocol stack. Starting from an application for secure publication of files, it has grown to include all kinds of basic protocol components and ap- plications towards the creation of a GNU internet.