Do Programmers Do Change Impact Analysis?
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

DVD-Ofimática 2014-02
(continuación 2) CamStudio 2.7.316 - CamStudio Codec 1.5 - CDex 1.70 beta 4 - CDisplayEx 1.9.09 - cdrTools FrontEnd 1.5.1 - Classic Shell 3.6.8 - Clavier+ 10.6.7 - Clementine 1.2.1 - Cobian Backup 8.4.0.202 - Comical 0.8 - ComiX 0.2.1.24 - CoolReader 3.0.56.42 - CubicExplorer 0.95.1 - Daphne 1.55 - Data Crow 3.12.5 - DejaVu Fonts 2.34 - DVD-Ofimática Deluge 1.3.6 - DeSmuME 0.9.10 - Dia 0.97.2.2 - Diashapes 0.2.2 - digiKam 3.4.0 - Disk Imager 1.4 - DiskCryptor 1.0.802.118 - Ditto 3.18.46.0 - DjVuLibre 3.5.25.4 - DocFetcher 1.1.9 - DoISO 2.0.0.6 - DOSBox 0.74 - DosZip Commander 3.21 - Double Commander 0.5.8 2014-02 beta - DrawPile 0.8.0 - DrawPile 0.8.3 actualización - DVD Flick 1.3.0.7 - DVDStyler 2.6.1 - DVDx 4.1.1.0 - Eagle Mode 0.84.0 - EasyTAG 2.1 - Ekiga 4.0.1 2013.08.20 - Electric Sheep 2.7.b35 - eLibrary 2.5.13 - emesene 2.12.9 2012.09.13 - eMule 0.50.a - Eraser 6.0.10 - DVD-Ofimática es una recopilación de programas libres para Windows eSpeak 1.47.11 - Eudora OSE 1.0 - eViacam 1.7.0 - Evince 2.32.0.145 - Exodus 0.10.0.0 - dirigidos a la ofimática en general (ofimática, sonido, gráficos y vídeo, Explore2fs 1.08 beta9 - Ext2Fsd 0.51 - FBReader 0.12.10 - FileBot 3.8 - FileVerifier++ 0.6.3 - Internet y utilidades). -

Adobe Acrobat
Adobe Acrobat PDF, využití, seznámení a funkce AA9 Portable Document Format . Formát pro přenositelné dokumenty . Nezávislý na SW i HW . Založeno na PostScript . Může obsahovat Text Formulářová pole Bitmapovou i vektorovou grafiku Multimedia … Portable Document Format . Speciální verze PDF/A – archivace PDF/E – výměna technických výkresů PDF/X – tisk a grafika PDF – historie . 1982: Adobe Systems Inc. 1993: PDF v pro výměnu dokumentů . Rychlý nárůst uživatelů . Mnoho nových funkcí . 2008: ISO 32000 . 2009: v9 Výhody PDF . Snadná tvorba . Věrné zobrazení ve všech programech . Rozšířenost . Interaktivní prvky . Zabezpečení . Prohlížeče zdarma . Možnosti editace Nevýhody PDF . Starší prohlížeče a nové funkce . Možnosti editace Použití . Prohlížení . Vytváření . Úprava . Formuláře Soubory ve . Sběr informací formátu PDF . Anotace . Technická grafika . atd. Čtení PDF . Adobe Reader . Foxit Reader . GSview . Xpdf . PalmPDF . Nitro PDF Reader . PDF-XChange Viewer . … Vytváření PDF . Adobe Acrobat . PDFCreator . PDF Factory . BullZip PDF Printer . Scribus . PRIMO PDF . Print2PDF . … Editace PDF . Adobe Acrobat . Foxit Editor . OpenOffice.org . PDF Split and Merge Acrobat vs. Reader . Acrobat Prohlížení a správa balíčku . Reader Omezená práva Nelze přidávat nebo mazat části dokumentu Acrobat vs. Reader Acrobat 9 . Standard (cca 10 000 Kč) . Pro (cca 15 000 Kč) Student (cca 1 245 Kč) . Pro Extended (cca 23 000 Kč) Reader . Zdarma Acrobat vs. Reader . Acrobat Prohlížení a správa balíčku/portfolia . Reader Omezená práva Nelze přidávat nebo mazat soubory Možnost vyplnění formuláře Reader . Prohlížení a čtení . Vyhledávání textu . Od v8 navíc práce s formuláři a elektronickým podpisem Acrobat Standard . Vytváření dokumentů PDF . Ochrana heslem, omezení práv tisku a kopírování . Spojování dokumentů . Digitální podepsání . Práce s metadaty, přílohami, záložkami . Ukládání PDF do DOC . -
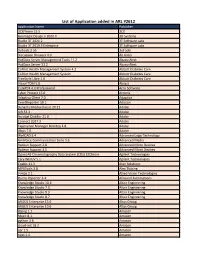
List of Application Added in ARL #2612
List of Application added in ARL #2612 Application Name Publisher 3CXPhone 15.5 3CX Geomagic Design X 2020.0 3D Systems Studio 3T 2021.2 3T Software Labs Studio 3T 2019.3 Enterprise 3T Software Labs 3uTools 2.55 3uTools Discussion Browser 4.0 Ab Initio HotDocs Server Management Tools 11.2 AbacusNext HotDocs Server 11.2 AbacusNext CoPilot Health Management System 4.2 Abbott Diabetes Care CoPilot Health Management System Abbott Diabetes Care FreeStyle Libre 1.0 Abbott Diabetes Care Visual TOM 5.8 Absyss CutePDF 4.0 Professional Acro Software Cyber Protect 15.0 Acronis Adaptiva Client 7.0 Adaptiva EventReporter 10.1 Adiscon Dynamic Media Classic 20.21 Adobe AIR 33.1 Adobe Acrobat Distiller 21.0 Adobe Connect 2021.3 Adobe Experience Manager Desktop 1.8 Adobe JBoss 7.0 Adobe WellCAD 5.4 Advanced Logic Technology AmiVoice Communication Suite 3.6 Advanced Media Radeon Support 2.8 Advanced Micro Devices Radeon Support 3.5 Advanced Micro Devices OpenLAB Chromatography Data System (CDS) EZChrom Agilent Technologies Cary WinUV 5.1 Agilent Technologies Coabis 11.3 Aker Solutions MP4Tools 3.8 Alex Thüring Vimba 2.1 Allied Vision Technologies Query Reporter 3.4 Allround Automations Knowledge Studio 10.4 Altair Engineering Knowledge Studio 7.0. Altair Engineering Knowledge Studio 9.3 Altair Engineering Knowledge Studio 8.7 Altair Engineering ARGUS Enterprise 13.0 Altus Group ARGUS Enterprise 10.6 Altus Group libpng 1.2 Amazon Music 8.1 Amazon python 3.6 Amazon cloud-init 18.2 Amazon apr 1.5 Amazon cups 1.4 Amazon java-1.7.0-openjdk 1.7 Amazon java-1.8.0-openjdk-devel -

Read Ebook {PDF EPUB} Vendetta by Elise Valente Vendetta
Read Ebook {PDF EPUB} Vendetta by Elise Valente Vendetta. “The odd scent she’d picked up earlier, combined with this girl’s unnatural speed, suddenly clicked in her mind. Rage flooded her when she realized what it meant. 'They've turned her,' she thought as she followed the girl into the woods. 'They turned a child and set her loose to hunt her. Sick.'” When the immortals have alternate cover edition ISBN 1477633731/9781477633731. “The odd scent she’d picked up earlier, combined with this girl’s unnatural speed, suddenly clicked in her mind. Rage flooded her when she realized what it meant. 'They've turned her,' she thought as she followed the girl into the woods. 'They turned a child and set her loose to hunt her. Sick.'” When the immortals have an eternity, the games they play become more macabre. It’s Sanaan’s job, and personal mission, to see the game’s masters annihilated. After all, they are the same people who destroyed her life and all her hopes for the future, creating a monster with an obsessive need for revenge. Vendetta is the first book in Amaranthine Blood series—the tale of a vampire whose only desire is to annihilate the Xul, once and for all. Sanaan thinks she’s got it under control, until the arrival of a stranger finds her precariously balancing on a knife’s edge between change and a descent into darkness. And there’s more going on in the fight than she ever knew—things that could change the course of the world’s fate forever. -

Linux Mint - 2Nde Partie
Linux Mint - 2nde partie - Mise à jour du 10.03.2017 1 Sommaire 1. Si vous avez raté l’épisode précédent… 2. Utiliser Linux Mint au quotidien a) Présentation de la suite logicielle par défaut b) Et si nous testions un peu ? c) Windows et Linux : d’une pratique logicielle à une autre d) L’installation de logiciels sous Linux 3. Vous n’êtes toujours pas convaincu(e)s par Linux ? a) Encore un argument : son prix ! b) L’installer sur une vieille ou une nouvelle machine, petite ou grande c) Par philosophie et/ou curiosité d) Pour apprendre l'informatique 4. À retenir Sources 2 1. Si vous avez raté l’épisode précédent… Linux, c’est quoi ? > Un système d’exploitation > Les principaux systèmes d'exploitation > Les distributions 3 1. Si vous avez raté l’épisode précédent… Premiers pas avec Linux Mint > Répertoire, dossier ou fichier ? > Le bureau > Gestion des fenêtres > Gestion des fichiers 4 1. Si vous avez raté l’épisode précédent… Installation > Méthode « je goûte ! » : le LiveUSB > Méthode « j’essaye ! » : le dual-boot > Méthode « je fonce ! » : l’installation complète 5 1. Si vous avez raté l’épisode précédent… Installation L'abréviation LTS signifie Long Term Support, ou support à long terme. 6 1. Si vous avez raté l’épisode précédent… http://www.linuxliveusb.com 7 1. Si vous avez raté l’épisode précédent… Installation 8 1. Si vous avez raté l’épisode précédent… Installation 9 1. Si vous avez raté l’épisode précédent… Installation 10 1. Si vous avez raté l’épisode précédent… Installation 11 2. Utiliser Linux Mint au quotidien a) Présentation de la suite logicielle par défaut Le fichier ISO Linux Mint est compressé et contient environ 1,6 GB de données. -

Openmagazin 2-2009
openMagazin www.openmagazin.cz openMagazin openOffice.org, openSource, openMind Obsah Vážení čtenáři, Linuxexpres OpenOffice.cz OpenMagazin je jedinečný PDF e-zin, který vám každý měsíc přinese Co se děje ve světě Linuxu a open source .........................................2 Pooostřehy 2/2009: ..........................................................................36 to nejlepší, co vyšlo na portálech LinuxEXPRES.cz a OpenOffice.cz, Mandriva Linux 2009 očami začiatočníckeho profesionála ............8 Ako špecificky číslovať listy dokumentu? .........................................38 a to zcela zdarma. Můžete se těšit na návody, recenze, novinky, tipy Kniha o Mandriva Linuxu 2009 ........................................................13 Jak exportovat dokument do PDF .....................................................40 a triky, které si můžete v klidu přečíst na svém netbooku nebo jiném Recenze knihy Ubuntu 8.10 CZ ........................................................14 Práce s funkcemi – IF, AND, OR ........................................................42 přenosném zařízení. Doufáme, že vás obsah zaujme a také vás Software pro biologický výzkum čili Tučňák biologem.....................15 Jak vyhledávat a nahrazovat text ......................................................46 prosíme, abyste PDF soubor šířili, kam to jen jde. Kopírujte nás, Hry v Ubuntu – instalace a přehled vybraných komerčních her .....19 Základy: Jak vytvořit kontingenční tabulku ......................................48 posílejte, sdílejte. A pište nám, -

DVD-Ofimática 2014-07
(continuación 2) Calizo 0.2.5 - CamStudio 2.7.316 - CamStudio Codec 1.5 - CDex 1.70 - CDisplayEx 1.9.09 - cdrTools FrontEnd 1.5.2 - Classic Shell 3.6.8 - Clavier+ 10.6.7 - Clementine 1.2.1 - Cobian Backup 8.4.0.202 - Comical 0.8 - ComiX 0.2.1.24 - CoolReader 3.0.56.42 - CubicExplorer 0.95.1 - Daphne 2.03 - Data Crow 3.12.5 - DejaVu Fonts 2.34 - DeltaCopy 1.4 - DVD-Ofimática Deluge 1.3.6 - DeSmuME 0.9.10 - Dia 0.97.2.2 - Diashapes 0.2.2 - digiKam 4.1.0 - Disk Imager 1.4 - DiskCryptor 1.1.836 - Ditto 3.19.24.0 - DjVuLibre 3.5.25.4 - DocFetcher 1.1.11 - DoISO 2.0.0.6 - DOSBox 0.74 - DosZip Commander 3.21 - Double Commander 0.5.10 beta - DrawPile 2014-07 0.9.1 - DVD Flick 1.3.0.7 - DVDStyler 2.7.2 - Eagle Mode 0.85.0 - EasyTAG 2.2.3 - Ekiga 4.0.1 2013.08.20 - Electric Sheep 2.7.b35 - eLibrary 2.5.13 - emesene 2.12.9 2012.09.13 - eMule 0.50.a - Eraser 6.0.10 - eSpeak 1.48.04 - Eudora OSE 1.0 - eViacam 1.7.2 - Exodus 0.10.0.0 - Explore2fs 1.08 beta9 - Ext2Fsd 0.52 - FBReader 0.12.10 - ffDiaporama 2.1 - FileBot 4.1 - FileVerifier++ 0.6.3 DVD-Ofimática es una recopilación de programas libres para Windows - FileZilla 3.8.1 - Firefox 30.0 - FLAC 1.2.1.b - FocusWriter 1.5.1 - Folder Size 2.6 - fre:ac 1.0.21.a dirigidos a la ofimática en general (ofimática, sonido, gráficos y vídeo, - Free Download Manager 3.9.4.1472 - Free Manga Downloader 0.8.2.325 - Free1x2 0.70.2 - Internet y utilidades). -

DVD-Ofimática 2014-03
(continuación 2) CamStudio 2.7.316 - CamStudio Codec 1.5 - CDex 1.70 beta 4 - CDisplayEx 1.9.09 - cdrTools FrontEnd 1.5.2 - Classic Shell 3.6.8 - Clavier+ 10.6.7 - Clementine 1.2.1 - Cobian Backup 8.4.0.202 - Comical 0.8 - ComiX 0.2.1.24 - CoolReader 3.0.56.42 - CubicExplorer 0.95.1 - Daphne 1.55 - Data Crow 3.12.5 - DejaVu Fonts 2.34 - DVD-Ofimática Deluge 1.3.6 - DeSmuME 0.9.10 - Dia 0.97.2.2 - Diashapes 0.2.2 - digiKam 3.4.0 - Disk Imager 1.4 - DiskCryptor 1.0.802.118 - Ditto 3.18.46.0 - DjVuLibre 3.5.25.4 - DocFetcher 1.1.10 - DoISO 2.0.0.6 - DOSBox 0.74 - DosZip Commander 3.21 - Double Commander 2014-03 0.5.8 beta - DrawPile 0.8.0 - DrawPile 0.8.5 actualización - DVD Flick 1.3.0.7 - DVDStyler 2.7 - DVDx 4.1.1.1 - Eagle Mode 0.84.0 - EasyTAG 2.1.10 - Ekiga 4.0.1 2013.08.20 - Electric Sheep 2.7.b35 - eLibrary 2.5.13 - emesene 2.12.9 2012.09.13 - eMule 0.50.a - Eraser 6.0.10 DVD-Ofimática es una recopilación de programas libres para Windows - eSpeak 1.48.02 - Eudora OSE 1.0 - eViacam 1.7.0 - Evince 2.32.0.145 - Exodus 0.10.0.0 - dirigidos a la ofimática en general (ofimática, sonido, gráficos y vídeo, Explore2fs 1.08 beta9 - Ext2Fsd 0.51 - FBReader 0.12.10 - FileBot 3.8 - FileVerifier++ 0.6.3 - Internet y utilidades). -

Download Qoppa Reseller Product Guide (PDF)
Product Guide Table of Contents Qoppa Software® offers a suite of products that cover every aspect of PDF processes and integrate seamlessly into document workflows. Qoppa solutions include Java class libraries to incorporate PDF manipulation capabilities; Java components to integrate PDF viewing and annotating into applications; and two commercial applications: PDF Automation Server™ to automate workflows and document handling, and PDF Studio™ All In One Tool to edit and manipulate PDF documents. We now deliver these same PDF solutions on the Android platform with apps: qPDF NotesTM and qPDF ViewerTM; and a PDF SDK for Android developers: qPDF ToolkitTM. Qoppa Software created our own PDF technology, making our solutions independent of all third party software on every Java enabled platform. We support all major platforms including Windows, Unix/Linux (Ubuntu, Suse, Fedora, AIX and others), Mac OSX and any other platform Our libraries are ready to that has full support for Java™. Our products are carefully designed and developed to provide integrate into your applets or the highest level of performance and reliability and are proven to be industry leaders. applications without modification. TABLE OF CONTENTS We are also open to PAGE TOPIC discussions about desired 2 PDF Studio – desktop all-in-one tool modifications for a particular 3 PDF Automation Server – workflow automation tool integration project. 4 jPDFAssemble product sheet – class library 5 jPDFEditor product sheet – visual component Contact us with 6 jPDFFields product sheet -

Vue.Js up & Running
Vue.js Up & Running BUILDING ACCESSIBLE AND PERFORMANT WEB APPS Callum Macrae www.allitebooks.com Vue.js: Up and Running Building Accessible and Performant Web Apps Callum Macrae Beijing Boston Farnham Sebastopol Tokyo www.allitebooks.com Vue.js: Up and Running by Callum Macrae Copyright © 2018 Callum Macrae. All rights reserved. Printed in the United States of America. Published by O’Reilly Media, Inc., 1005 Gravenstein Highway North, Sebastopol, CA 95472. O’Reilly books may be purchased for educational, business, or sales promotional use. Online editions are also available for most titles (http://oreilly.com/safari). For more information, contact our corporate/insti‐ tutional sales department: 800-998-9938 or [email protected]. Editors: Allyson MacDonald and Virginia Wilson Indexer: Ellen Troutman-Zaig Production Editor: Justin Billing Interior Designer: David Futato Copyeditor: Sharon Wilkey Cover Designer: Karen Montgomery Proofreader: Jasmine Kwityn Illustrator: Rebecca Demarest March 2018: First Edition Revision History for the First Edition 2018-02-23: First Release See http://oreilly.com/catalog/errata.csp?isbn=9781491997246 for release details. The O’Reilly logo is a registered trademark of O’Reilly Media, Inc. Vue.js: Up and Running, the cover image, and related trade dress are trademarks of O’Reilly Media, Inc. While the publisher and the author have used good faith efforts to ensure that the information and instructions contained in this work are accurate, the publisher and the author disclaim all responsibility for errors or omissions, including without limitation responsibility for damages resulting from the use of or reliance on this work. Use of the information and instructions contained in this work is at your own risk. -

IT-Empfehlungen Für Den Nachhaltigen Umgang Mit Digitalen Daten in Den Altertumswissenschaften
IT-Empfehlungen für den nachhaltigen Umgang mit digitalen Daten in den Altertumswissenschaften Herausgeber: IANUS Version 1.0.0.0 29. März 2017 Koordination Förderung Herausgeber IANUS Autoren: siehe Autorenverzeichnis Titel: IT-Empfehlungen für den nachhaltigen Umgang mit digitalen Daten in den Altertumswissenschaften Sprache: Deutsch doi:10.13149/000.y47clt-t Zitierhinweis: IANUS (Hrsg.), IT-Empfehlungen für den nachhaltigen Umgang mit digi- talen Daten in den Altertumswissenschaften (2017) [Version 1.0.0.0] doi: http://dx.doi.org/10.13149/000.y47clt-t Kontakt: [email protected] www.ianus-fdz.de Lizenz: cba BYSA Dieses Werk bzw. Inhalt ist lizenziert unter einer Creative Commons Namensnennung – Weitergabe unter gleichen Bedingungen 4.0 International Lizenz. http://creativecommons.org/licenses/by-sa/4.0/ Versionshistorie Version Autor Datum Beschreibung 0.9 IANUS 18.02.2014 Erste veröffentlichte Fassung. 0.9 IANUS 11.03.2014 Änderung der Lizenzbedingungen. 0.95 IANUS 05.02.2015 Kapitel „3D und Virtual Reality“ und „Textdokumente“ neu. Anpassungen im Layout und kleinere Korrekturen. 0.96 IANUS 27.05.2015 Kapitel „Datenmanagement“ neu, Ergänzung Versionskontrolle und Korrekturen. Fortsetzung auf der nächsten Seite Fortsetzung der vorhergehenden Seite Version Autor Datum Beschreibung 0.97 IANUS 09.12.2015 Kapitel „Tabellen“ neu, Ergänzungen im Glossar und Korrekturen. 0.97.5 IANUS 21.07.2016 Kapitel „Video“, „Audio“ und „RTI“ neu, Ergänzungen im Glossar, Anpassungen im Kapitel „Archivierung bei IANUS“ und Korrekturen. 0.97.5 IANUS 13.09.2016 Einarbeitung Reviews für „Video“, „Audio“ und „RTI“, Ergänzungen im Glossar und Korrekturen. 0.98 IANUS 22.11.2016 Überarbeitung „Datenmanagement“ und „3D und Virtual Reality“, Ergänzung Bild in „RTI“. -

DVD-Libre 2015-10 DVD-Libre Libreoffice 5.0.2 - Libreoffice Libreoffice - 5.0.2 Libreoffice Octubre De 2015 De Octubre
(continuación) LenMus 5.3.1 - Liberation Fonts 1.04 - LibreOffice 5.0.2 - LibreOffice 5.0.2 Ayuda en español - Lilypond 2.18.2 - Linphone 3.8.5 - LockNote 1.0.5 - 0 1 Luminance HDR 2.4.0 - MahJongg Solitaire 3D 1.0.1 - MALTED 3.0 2012.10.23 - - Marble 1.09.1 - MD5summer 1.2.0.05 - MediaInfo 0.7.78 - MediaPortal 2.0.0 Update 1 - 5 DVD-Libre 1 Miranda IM 0.10.36 - Miro Video Converter 3.0 - Mixxx 1.11.0 - Mnemosyne 2.3.3 - 0 2 Mozilla Backup 1.5.1 - Mozilla Backup 1.5.1 Españ ol - muCommander 0.9.0 - 2015-10 MuseScore 2.0.2 - MyPaint 1.0.0 - Nightingale 1.12.1 - ODF Add-in para Microsoft e r Office 4.0.5309 - Password Safe 3.36 - PDF Split and Merge 2.2.4 2015.01.13 - b i PdfBooklet 2.3.2 - PDFCreator 2.1.2 - PeaZip 5.7.2 - Peg-E 1.2.1 - PicToBrick 1.0 - L DVD-Libre es una recopilación de programas libres para Windows. - Pidgin 2.10.11 - PNotes.Net 3.1.0.3 - Pooter 5.0 - Portable Puzzle Collection D 2015.09.19 - PosteRazor 1.5.2 - ProjectLibre 1.6.2 - PuTTY 0.65 - PuTTY Tray V En http://www.cdlibre.org puedes conseguir la versión más actual de este 0.65.t026 - Pyromaths 15.02 - PyTraffic 2.5.3 - R 3.2.2 - Remove Empty Directories 2.2 D DVD, así como otros CDs y DVDs recopilatorios de programas y fuentes.