An Analysis of Pre-Installed Android Software
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

On Client Ledger System™ Software
Focus on Client Ledger System™ Software A Financial MicroSystems, Inc. Publication • Volume 18, Issue 1 • 4th Quarter of 2012 CLS II (1.61) and CLS-DOS (6.3) Updates are Scheduled for Release December 4th Year-end CLS updates for both CLS II and CLS-DOS are currently scheduled for release December 4th. We originally planned to discontinue CLS-DOS at the end of this year, because it has become increasingly difficult for us to make the required programming changes. However, we have decided to release one final year-end update for CLS-DOS and will continue to support it through September 2013. All future development will focus on CLS II. CLS updates include the new 2012 W-2 and 1099/1098 formats for both laser-printed plain-paper and preprinted forms. Dot-matrix preprinted W-2 and 1099 forms are available only in CLS-DOS. Formats for the standard, two-up, preprinted W-2 and W-3 forms are basically unchanged for 2012. However, the 1099- MISC form has alignment changes and formats for the 1099-INT, 1099-DIV, 1099-B, 1099-C, 1098 and 1096 forms are new. All W-2 and W-3 forms (including Copy A) may be printed on plain paper. Submittable 940, 941, 943 and 944 forms may also be printed on plain paper. For 1099, 1098 and 1096 forms, all copies except Copy A may be printed on plain-paper. Copy A must be filed using “official” scannable forms (the IRS may impose a penalty for using non-scannable forms). The CLS updates also include required changes to the federal 940, 941, 943 and 944 forms for the 2012 year-end. -

Radare2 Book
Table of Contents introduction 1.1 Introduction 1.2 History 1.2.1 Overview 1.2.2 Getting radare2 1.2.3 Compilation and Portability 1.2.4 Compilation on Windows 1.2.5 Command-line Flags 1.2.6 Basic Usage 1.2.7 Command Format 1.2.8 Expressions 1.2.9 Rax2 1.2.10 Basic Debugger Session 1.2.11 Contributing to radare2 1.2.12 Configuration 1.3 Colors 1.3.1 Common Configuration Variables 1.3.2 Basic Commands 1.4 Seeking 1.4.1 Block Size 1.4.2 Sections 1.4.3 Mapping Files 1.4.4 Print Modes 1.4.5 Flags 1.4.6 Write 1.4.7 Zoom 1.4.8 Yank/Paste 1.4.9 Comparing Bytes 1.4.10 Visual mode 1.5 Visual Disassembly 1.5.1 2 Searching bytes 1.6 Basic Searches 1.6.1 Configurating the Search 1.6.2 Pattern Search 1.6.3 Automation 1.6.4 Backward Search 1.6.5 Search in Assembly 1.6.6 Searching for AES Keys 1.6.7 Disassembling 1.7 Adding Metadata 1.7.1 ESIL 1.7.2 Scripting 1.8 Loops 1.8.1 Macros 1.8.2 R2pipe 1.8.3 Rabin2 1.9 File Identification 1.9.1 Entrypoint 1.9.2 Imports 1.9.3 Symbols (exports) 1.9.4 Libraries 1.9.5 Strings 1.9.6 Program Sections 1.9.7 Radiff2 1.10 Binary Diffing 1.10.1 Rasm2 1.11 Assemble 1.11.1 Disassemble 1.11.2 Ragg2 1.12 Analysis 1.13 Code Analysis 1.13.1 Rahash2 1.14 Rahash Tool 1.14.1 Debugger 1.15 3 Getting Started 1.15.1 Registers 1.15.2 Remote Access Capabilities 1.16 Remoting Capabilities 1.16.1 Plugins 1.17 Plugins 1.17.1 Crackmes 1.18 IOLI 1.18.1 IOLI 0x00 1.18.1.1 IOLI 0x01 1.18.1.2 Avatao 1.18.2 R3v3rs3 4 1.18.2.1 .intro 1.18.2.1.1 .radare2 1.18.2.1.2 .first_steps 1.18.2.1.3 .main 1.18.2.1.4 .vmloop 1.18.2.1.5 .instructionset 1.18.2.1.6 -

Creationstation ® Guide
SAFARI Montage CreationStation User Guide SAFARI Montage CreationStation® Overview SAFARI Montage CreationStation is an easy-to-use integrated module that enables schools and districts to upload user-created digital content and licensed media to the SAFARI Montage system's Learning Object Repository (LOR). User types granted upload privileges, such as Student with Upload, Teacher with Upload and higher level user types can add items either individually or in bulk. Once uploaded, content can be meta-tagged with information such as a detailed description, relevant grade ranges and year of copyright, uploads can be correlated to curriculum standards and designated for home access, download, etc. Video and audio content can be segmented into chapters and key concepts, each with their own segment descriptions. Flexible Digital Rights Management provides control over the content to ensure that the correct users have access to digital resources. Media and web links uploaded via CreationStation are fully searchable in conjunction with licensed content, providing a wealth of digital resources that are easily accessible and able to be used with other system features for instructional purposes. When used in conjunction with SAFARI Montage WAN Manager, digital resources can be shared with others in the same school as the user who uploaded it, or published to all schools in the district. Student user types have an appropriately limited ability to upload to the SAFARI Montage system through the CreationStation feature, My Locker. To learn more, refer to the following Help topics: Uploading Media into CreationStation Adding and Editing Metadata Searching for Uploaded Content Using Uploaded Content My Locker for Students - CreationStation video tutorial Accessing CreationStation 1 SAFARI_Montage_creation 1. -

Microsoft Security Intelligence Report
Microsoft Security Intelligence Report Volume 20 | July through December, 2015 This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS, IMPLIED, OR STATUTORY, AS TO THE INFORMATION IN THIS DOCUMENT. This document is provided “as-is.” Information and views expressed in this document, including URL and other Internet website references, may change without notice. You bear the risk of using it. Copyright © 2016 Microsoft Corporation. All rights reserved. The names of actual companies and products mentioned herein may be the trademarks of their respective owners. Authors Charlie Anthe Dana Kaufman Anthony Penta Cloud and Enterprise Security Azure Active Directory Team Safety Platform Nir Ben Zvi Nasos Kladakis Ina Ragragio Enterprise and Cloud Group Azure Active Directory Team Windows and Devices Group Patti Chrzan Daniel Kondratyuk Tim Rains Microsoft Digital Crimes Unit Azure Active Directory Team Commercial Communications Bulent Egilmez Andrea Lelli Paul Rebriy Office 365 - Information Windows Defender Labs Bing Protection Geoff McDonald Stefan Sellmer Elia Florio Windows Defender Labs Windows Defender Labs Windows Defender Labs Michael McLaughlin Mark Simos Chad Foster Identity Services Enterprise Cybersecurity Bing Group Nam Ng Roger Grimes Enterprise Cybersecurity Vikram Thakur Microsoft IT Group Windows Defender Labs Paul Henry Niall O'Sullivan Alex Weinert Wadeware LLC Microsoft Digital Crimes Unit Azure Active Directory Team Beth Jester Daryl Pecelj Terry Zink Windows Defender Microsoft IT Information -

Initial Setup of Your IOS Device
1. When you first turn on your iOS device, you'll see a screen displaying Hello in different languages. Slide from left to right anywhere on this screen. 2. Select the language you want your iOS device to use, and then the region in which you'll be using your iOS device. This will affect things such as date, time, and contact formatting. 3. Your iOS device requires an Internet connection to set up. Tap the name of your desired Wi-Fi network to begin device activation. § If you're activating an iPhone or iPad (Wi-Fi + Cellular) with active cellular service, you can instead choose cellular activation. 4. Choose whether to enable Location Services. 5. Set up your iPhone as a new device, from an iCloud backup, or from an iTunes backup. § If restoring from backup, you can learn how to restore your content. 6. Sign in with your Apple ID, which you've created previously, or create a free Apple ID. § Alternatively, you can tap Skip This Step to sign in or create an Apple ID later. § If necessary, learn how to create a free Apple ID: 1. Select your birthday, then tap Next: 2. Enter your first and last name, then tap Next: 3. You can then use either your current email address, or choose to get a free iCloud email address. Select the option you'd like, then tap Next. 4. Enter your current email address, or what you'd like for your iCloud email, then tap Next. 5. Enter what you'd like for your password and tap Next. -

Test Coverage Guide
TEST COVERAGE GUIDE Test Coverage Guide A Blueprint for Strategic Mobile & Web Testing SUMMER 2021 1 www.perfecto.io TEST COVERAGE GUIDE ‘WHAT SHOULD I BE TESTING RIGHT NOW?’ Our customers often come to Perfecto testing experts with a few crucial questions: What combination of devices, browsers, and operating systems should we be testing against right now? What updates should we be planning for in the future? This guide provides data to help you answer those questions. Because no single data source tells the full story, we’ve combined exclusive Perfecto data and global mobile market usage data to provide a benchmark of devices, web browsers, and user conditions to test on — so you can make strategic decisions about test coverage across mobile and web applications. CONTENTS 3 Putting Coverage Data Into Practice MOBILE RECOMMENDATIONS 6 Market Share by Country 8 Device Index by Country 18 Mobile Release Calendar WEB & OS RECOMMENDATIONS 20 Market Share by Country 21 Browser Index by Desktop OS 22 Web Release Calendar 23 About Perfecto 2 www.perfecto.io TEST COVERAGE GUIDE DATA INTO PRACTICE How can the coverage data be applied to real-world executions? Here are five considerations when assessing size, capacity, and the right platform coverage in a mobile test lab. Optimize Your Lab Configuration Balance Data & Analysis With Risk Combine data in this guide with your own Bundle in test data parameters (like number of tests, analysis and risk assessment to decide whether test duration, and required execution time). These to start testing with the Essential, Enhanced, or parameters provide the actual time a full- cycle or Extended mobile coverage buckets. -

Android Malware and Analysis
ANDROID MALWARE AND ANALYSIS Ken Dunham • Shane Hartman Jose Andre Morales Manu Quintans • Tim Strazzere Click here to buy Android Malware and Analysis CRC Press Taylor & Francis Group 6000 Broken Sound Parkway NW, Suite 300 Boca Raton, FL 33487-2742 © 2015 by Taylor & Francis Group, LLC CRC Press is an imprint of Taylor & Francis Group, an Informa business No claim to original U.S. Government works Printed on acid-free paper Version Date: 20140918 International Standard Book Number-13: 978-1-4822-5219-4 (Hardback) This book contains information obtained from authentic and highly regarded sources. Reasonable efforts have been made to publish reliable data and information, but the author and publisher cannot assume responsibility for the validity of all materials or the consequences of their use. The authors and publishers have attempted to trace the copyright holders of all material reproduced in this publication and apologize to copyright holders if permission to publish in this form has not been obtained. If any copyright material has not been acknowledged please write and let us know so we may rectify in any future reprint. Except as permitted under U.S. Copyright Law, no part of this book may be reprinted, reproduced, transmit- ted, or utilized in any form by any electronic, mechanical, or other means, now known or hereafter invented, including photocopying, microfilming, and recording, or in any information storage or retrieval system, without written permission from the publishers. For permission to photocopy or use material electronically from this work, please access www.copyright. com (http://www.copyright.com/) or contact the Copyright Clearance Center, Inc. -

Nokia Metrosite GSM Base Station, Product Description
Nokia MetroSite GSM Base Station, Product Description DN991444 © Nokia Networks Oy Internal Copy 1 (84) Issue 2 en DRAFT 1 Draft Nokia MetroSite GSM Base Station, Product Description The information in this document is subject to change without notice and describes only the product defined in the introduction of this documentation. This document is intended for the use of Nokia Networks' customers only for the purposes of the agreement under which the document is submitted, and no part of it may be reproduced or transmitted in any form or means without the prior written permission of Nokia Networks. The document has been prepared to be used by professional and properly trained personnel, and the customer assumes full responsibility when using it. Nokia Networks welcomes customer comments as part of the process of continuous development and improvement of the documentation. The information or statements given in this document concerning the suitability, capacity, or performance of the mentioned hardware or software products cannot be considered binding but shall be defined in the agreement made between Nokia Networks and the customer. However, Nokia Networks has made all reasonable efforts to ensure that the instructions contained in the document are adequate and free of material errors and omissions. Nokia Networks will, if necessary, explain issues which may not be covered by the document. Nokia Networks' liability for any errors in the document is limited to the documentary correction of errors. Nokia Networks WILL NOT BE RESPONSIBLE IN ANY EVENT FOR ERRORS IN THIS DOCUMENT OR FOR ANY DAMAGES, INCIDENTAL OR CONSEQUENTIAL (INCLUDING MONETARY LOSSES), that might arise from the use of this document or the information in it. -
Oneplus 6T User Manual Index
OnePlus 6T User Manual Index 04 What’s in The Box? 24 Notch Display Settings 05 Device 25 OnePlus Fast Charging 06 Power On 26 OxygenOS 07 Setup Wizard 27 Launcher 08 Migrating Data (OnePlus Switch) 28 App Drawer 09 Insert SIM Card (SIM Card Tray) 29 Hidden Space 10 Screen Unlock 30 Notification Shade 11 Face Unlock 31 Shelf 12 Alert Slider 32 Gestures 13 Camera 33 App Long Press 14 Camera Interface 34 Reading Mode 15 Choosing Camera Modes and Settings 35 Gaming mode 16 Studio Lighting 36 Dialer 17 Nightscape 37 Messenger 18 Portrait Mode 38 Gallery 19 Video 39 Recorder 20 Video Editor 40 File Manager 21 Pro Mode 41 App Permission 22 Pro Mode - Continued 23 Optic AMOLED Display 2 Welcome Thank You! We believe in sharing the best technology, designed to be fast, smooth, and user-centric. The OnePlus 6T offers a fast and smooth experience, with an emphasis on speed. Navigating between apps, photos and games is now easier than it’s ever been. With speed at the center of its design, the OnePlus 6T now ensures that your time receives its optimum value. With our continued attention to improve swift and smooth transitions based on a sense of speed, the OnePlus 6T is our fastest product yet. A beautiful combination of sophisticated hardware and software allows you to experience speed like you’ve never done before. 3 What’s in The Box OnePlus 6T Screen Protector Translucent Case USB Type-C Cable Power Adapter SIM Tray Ejector Quick Start Guide USB Type-C 3.5mm (pre-applied) Safety Information Adapter 4 | What’s in the Box Device OxygenOS Device Alert Slider Nano SIM Slot Volume Power Sleep/Wake USB Type-C 5 | What’s in the Box Device OxygenOS Power On Turn on your OnePlus 6T by pressing and holding the <Power> button (found on the right side of the phone) for a few seconds. -

Aquaris X2 X2 Pro Complete User Manual
Aquaris X2 (X2 / X2 Pro) Complete User Manual Aquaris X2 / X2 Pro The BQ team would like to thank you for purchasing your new Aquaris X2 / X2 Pro. We hope you enjoy using it. Enjoy the fastest mobile network speeds with this unlocked smartphone thanks to 4G coverage. Its dual-SIM functionality (nano-SIM) means you can use two SIM cards at the same time, even if they are from different operators. You can browse the internet rapidly, check your email, enjoy games and apps (which can be acquired directly from the device), read e-books, transfer files via Bluetooth, record audio, watch films, take photos and record videos, listen to music, chat with your friends and family and enjoy your favourite social networks. It also comes with a fingerprint scanner, enabling you to add a digital fingerprint to unlock your smartphone, authorise purchases or sign in to an application. About this manual · To make sure that you use your smartphone correctly, please read this manual carefully before you start using it. · Some of the images and screenshots shown in this manual may differ slightly from those of the final product. Likewise, due to firmware updates, it is possible that some of the information in this manual does not correspond exactly to the operation of your device. · BQ shall not be held liable for any issues relating to performance or incompatibility resulting from modification of the registry settings by the user. Nor shall it be held liable for any incompatibility issues with third-party applications available through the app stores. -
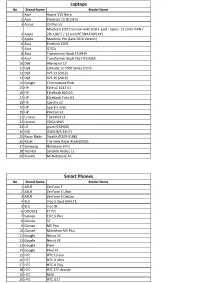
Type-C Compatible Device List 1.Xlsx
Laptops No Brand Name Model Name 1 Acer Aspire V15 Nitro 2 Acer Predator 15 (N15P3) 3 Aorus X3 Plus v5 MacBook (2015 version with USB-C port - Specs: 13.1mm THIN / 4 Apple 2lb. LIGHT / 12-inch RETINA DISPLAY) 5 Apple MacBook Pro (Late 2016 Version) 6 Asus EeeBook E202 7 Asus G752v 8 Asus Transformer Book T100HA 9 Asus Transformer Book Flip (TP200SA) 10 Dell Alienware 17 11 Dell Latitude 12 7000 Series (7275 12 Dell XPS 13 (2016) 13 Dell XPS 15 (2016) 14 Google Chromebook Pixel 15 HP Elite x2 1012 G1 16 HP EliteBook 840 G3 17 HP EliteBook Folio G1 18 HP Spectre x2 19 HP Spectre x360 20 HP Pavilion x2 21 Lenovo ThinkPad 13 22 Lenovo YOGA 900S 23 LG gram (15Z960) 24 MSI GS60 (MS-16H7) 25 Razer Blade Stealth (RZ09-0168) 26 Razer The New Razer Blade(2016) 27 Samsung Notebook 9 Pro 28 Toshiba Satellite Radius 12 29 Xiaomi Mi Notebook Air Smart Phones No Brand Name Model Name 1 ASUS ZenFone 3 2 ASUS ZenFone 3 Ultra 3 ASUS ZenFone 3 Deluxe 4 BLU Vivo 5 Dual SIM LTE 5 BLU Vivo XL 6 DOOGEE F7 Pro 7 Gionee Elife S Plus 8 Gionee S6 9 Gionee M5 Plus 10 Gionee Marathon M5 Plus 11 Google Nexus 5X 12 Google Nexus 6P 13 Google Pixel 14 Google Pixel XL 15 HTC HTC 10 evo 16 HTC HTC U Ultra 17 HTC HTC U Play 18 HTC HTC 10 Lifestyle 19 HTC M10 20 HTC HTC U11 21 Huawei Honor 22 Huawei Honor 8 23 Huawei Honor 9 24 Huawei Honor Magic 25 Huawei Hornor V9 26 Huawei Mate 9 27 Huawei Mate 9 Pro 28 Huawei Mate 9 Porsche Design 29 Huawei Nexus 6P 30 Huawei Nova2 31 Huawei P9 32 Huawei P10 33 Huawei P10 Plus 34 Huawei V8 35 Lenovo ZUK Z1(China) 36 Lenovo Zuk Z2 37 -

Secure Software Distribution System
SECURE SOFTWARE DISTRIBUTION SYSTEM Tony Bartoletti ([email protected]), Lauri A. Dobbs ([email protected]), Marcey Kelley ([email protected]) Computer Security Technology Center Lawrence Livermore National Laboratory PO Box 808 L-303 Livermore, CA 94551 June 18, 1997 Abstract Authenticating and upgrading system software plays a critical role in information security, yet practical tools for assessing and installing software are lacking in today’s marketplace. The Secure Software Distribution System (SSDS) will provide automated analysis, notification, distribution, and installation of security patches and related software to network-based computer systems in a vendor-independent fashion. SSDS will assist with the authentication of software by comparing the system’s objects with the patch’s objects. SSDS will monitor vendors’ patch sites to determine when new patches are released and will upgrade system software on target systems automatically. This paper describes the design of SSDS. Motivations behind the project, the advantages of SSDS over existing tools as well as the current status of the project are also discussed. Keywords: security, distributed, software management DISCLAIMER This document was prepared as an account of work sponsored by an agency of the United States Government. Neither the United States Government nor the University of California nor any of their employees, makes any warranty, express or implied, or assumes any legal liability or responsibility for the accuracy, completeness, or usefulness of any information, apparatus, product, or process disclosed, or represents that its use would not infringe privately owned rights. Reference herein to any specific commercial products, process or service by trade name, trademark, manufacturer, or otherwise, does not necessarily constitute or imply its endorsement, recommendation, or favoring by the United States Government or the University of California.