The Icon Analyst
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Indesign CS Basics
InDesign CS Basics InDesign CS Basics InDesign Basics Training Objective To learn the tools and features of InDesign CS to create publications efficiently and effectively. What you can expect to learn from this class: • How to use the InDesign environment/layout • How to create and navigate through a new document • How to use rulers and guides • How to create and use Master Pages, headers, and footers • How to import, place, manipulate, and format text frames • How to add and manipulate graphics • How to draw and edit shapes • How to export and publish the final document Who should take this class? Any person with a basic knowledge of computers and who is interested in learning how to use InDesign to create newsletters, brochures, and flyers. InDesign Tips and Shortcuts: Command-Z: Undo Command-N: New Document Shift + Command-B: Bold Shift + Command-I: Italics Command-0: Fit to Window Command-1: Actual Size Command-; Show Hide Guides Command-spacebar: Zoom into a Selected Area Command-spacebar-Option: Zoom out of a Selected Area Tab: Hide all Palettes and the Toolbox Shift-Tab: Hide Palettes Center for Instruction and Technology 1 5/5/05 InDesign CS Basics Getting Started InDesign is a page layout program. It allows you work with text and graphics to develop professional looking newsletters, brochures, books and other types of publications. InDesign Help To access InDesign’s Help Index from the Help menu, go to Help > InDesign Help. Select the Contents or Index link for general searches. Select the Search link to type specific topics. Creating a New Document To create a new document go to: 1. -

Cisco Video Surveillance 8400 IP Camera Reference Guide Release 1.0.0
Cisco Video Surveillance 8400 IP Camera Reference Guide Release 1.0.0 July 12, 2017 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB’s public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS” WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

CT-PIVOTW512 Manual
Product Code: CT-PIVOTC512 CT-PIVOTW512 V1.10 This manual contains important information. Please read before operating product. INDEX WARNINGS ..................................................................................................................................... 5 DISPOSAL OF OLD ELECTRICAL & ELECTRONIC EQUIPMENT ........................................................ 5 GENERAL SAFETY INSTRUCTIONS ................................................................................................ 5 IN CASE OF ISSUES ...................................................................................................................... 5 PACKAGING, SHIPPING AND CLAIMS ........................................................................................... 6 WARRANTY AND PRODUCTS RETURN ............................................................................................. 7 POWER SUPPLY ........................................................................................................................... 8 CE CONFORMITY ......................................................................................................................... 8 WHAT’S IN THE BOX .................................................................................................................... 8 GLOSSARY ....................................................................................................................................... 9 INTRODUCTION ........................................................................................................................... -

A Guide to Quarkxpress 9.5.1 CONTENTS
A Guide to QuarkXPress 9.5.1 CONTENTS Contents About this guide.............................................................................18 What we're assuming about you..........................................................................18 Where to go for help............................................................................................18 Conventions..........................................................................................................19 Technology note...................................................................................................19 The user interface...........................................................................21 Tools......................................................................................................................21 Web tools..............................................................................................................24 Menus...................................................................................................................24 QuarkXPress menu (Mac OS only).................................................................................25 File menu.......................................................................................................................25 Edit menu......................................................................................................................26 Style menu.....................................................................................................................28 -

Advisory Committee
MGDS-GeoMapApp Exercises, January 2009 MGDS Data Exploration Tools – Hands-on exercises and usability feedback Please try the following short exercises. Remember, there are multimedia tutorials and help pages at this web page: http://www.geomapapp.org/ GeoMapApp: Search for geochemical signatures using PetDB petrology Zoom to the EPR 9N Integrated Study Site. Most of this seafloor is mapped with high-resolution multibeam; fuzzy areas around the edges are the background satellite altimetry-derived bathymetry. Load the PetDB samples chemistry (Focus Sites -> Select From Searchable List, type “MORB” into search box, click once on EPR Rock samples and MORB chemistry from PetDB, then hit OK). When the table is loaded, use the Colour By Value button to colour the symbols on, say, MgO. In the colour palette window, slide the grey lines sideways to change the colour scale. Use the Graph button to plot FeOT against MgO. In the graph plot window, click on the Lasso tool and use the mouse to encircle the high-MgO outliers. This lights up the symbols both on the graph and in the map window. Bonus: On the right, use the Save drop-down menu to copy the selected points into an Excel spreadsheet and open the spreadsheet. Note: you can also pull up these samples using the real-time PetDB Web Feature Service, as follows. File -> Import Dataset from WFS. From the drop-down menu, select PetDB, hit Connect. Hit Load Feature (may take a few minutes depending upon the internet connection). Page 1 of 16 MGDS-GeoMapApp Exercises, January 2009 GeoMapApp: Central America geochemical signatures using EarthChem petrology Zoom to the Central America area. -

Acorn Archimedes
Copyright © Acorn Computers Limited 1988 Neither the whole nor any part of the information contained in, nor the product described in this Guide may be adapted or reproduced in any material form except with the prior written approval of Acorn Computers Limited. The products described in this manual are subject to continuous development and improvement. All information of a technical nature and particulars of the products and their use (including the information and particulars in this Guide) are given by Acorn Computers Limited in good faith. However, Acorn Computers Limited cannot accept any liability for any loss or damage arising from the use of any information or particulars in this manual, or any incorrect use of the products. All maintenance and service on the products must be carried out by Acorn Computers' authorised dealers. Acorn Computers Limited can accept no liability whatsoever for any loss or damage caused by service, maintenance or repair by unauthorised personnel. All correspondence should be addressed to: Customer Support and Service Acorn Computers Limited Fulbourn Road Cherry Hinton Cambridge CB1 4JN Information can also be obtained from the Acorn Support Information Database (SID). This is a direct dial viewdata system available to registered SID users. Initially, access SID on Cambridge (0223) 243642: this will allow you to inspect the system and use a response frame for registration. ACORN, ARCHIMEDES and ECONET are trademarks of Acorn Computers Limited. Within this publication, the term 'BBC' is used as an abbreviation for 'British Broadcasting Corporation'. Edition 2 First published 1988 Published by Acorn Computers Limited ISBN 1 85250 055 7 Part number 0483,000 Issue 1 1 2 Welcome to the Archimedes personal workstation This guide introduces your new Archimedes personal workstation. -

(12) United States Patent (10) Patent No.: US 6,269,187 B1 Frink Et Al
US006269187B1 (12) United States Patent (10) Patent No.: US 6,269,187 B1 Frink et al. (45) Date of Patent: *Jul. 31, 2001 (54) METHOD AND SYSTEM FOR DATA ENTRY (56) References Cited OF HANDWRITTEN SYMBOLS _ U.S. PATENT DOCUMENTS (75) Inventors: Lloyd Frink, Seattle; Bryon Dean BlShOp, Redmond, bOth Of WA (US) 4,817,034 * 3/1989 Hardin et al. ...................... .. 382/187 4,918,740 * 4/1990 ROSS . .. 382/187 (73) Assignee: Microsoft Corporation, Redmond, WA 4,953,225 * 8/1990 Togawa et al. 382/187 (US) 4,972,496 * 11/1990 Sklarew .... .. .. 382/187 5,063,600 * 11/1991 Norwood ........................... .. 382/187 (*) Notice: This patent issued on a continued pros- 5,956,423 * 9/1999 Frink et al. ........................ .. 382/187 ecution application ?led under 37 CFR 1.53(d), and is subject to the tWenty year * Cited by examiner patent term provisions of 35 U.S.C. 154(a)(2). Primary Examiner—Jose L. Couso Snbjeet to any disclaimer, the term of this (74) Attorney, Agent, or Firm—Michalik & Wylie, PLLC patent is extended or adjusted under 35 U.S.C. 154(b) by 0 days. (57) ABSTRACT Amethod and system for data entry of handwritten text into (21) APPL N05 09/386,248 a computer program that is not designed to accept hand (22) Filed, Aug 31’ 1999 Written text is provided. In preferred embodiments, the computer program is designed to operate in a WindoWing Related US Application Data environment. A data entry program receives handwritten data, recognizes the data, and sends the recognized data to (63) Continuation of application No. -

Macdraft Professional Release Notes
MacDraft Professional Release Notes This document contains the release notes for all versions of MacDraft after version 4.2.2. Version 6.2.1 (27th March 2018) Bug Fixes • Fixed an issue where grid snapping was not aligning to the grid. • Added a “Center Working Drawing” option in the View menu, to make it easier and faster to center the document view. • Fixed an issue with selected text being invisible. • Fixed an issue where palettes were not having their state saved. • Fixed an issue with text shifting in DWG files saved using MacDraft. • Fixed a crash issue when rotating disassembled dimensions. • Fixed an issue with the “Load Layer” warning displaying when attempting to open some older documents. • Fixed an issue when adding guides with a position. • Fixed Export PDF... to now allow transparent backgrounds. • Fixed Export PDF... so that it doesn’t include items in the gray space. • Fixed an issue where certain DWG files were not opening • Fixed other smaller performance related issues. • Fixed various issues with localized versions. • Fixed an issue where the line weights panel was empty. • Fixed crash issues when adding library items to the document, by rewriting the library code for modern systems. • Fixed an obscure issue with file corruption on Save As... • Fixed crash issue when adding dimensions from the library. • Fixed other 10.13 specific issues. Version 6.2 (26th September 2016) New Features / Improvements • Smart Snapping Feature: o Objects can now snap to each other using smart handles. o This option can be turned on and off at any time o Snap to centers, edges, corners and bounds. -

Measuring Production TRIALS
May 20, 2014 Enabling PantoneLIVE in Colorcert 2.5 and above Be sure to follow the instructions in your PantoneLIVE license email to initially claim your PantoneLIVE license and assign it to yourself before continuing. The My X-Rite credentials used in the instructions below must be the credentials that the license was assigned to. If someone else received the license, use their credentials or have them assign (or reassign) them to you. Enabling PantoneLIVE in ColorCert 2.5 and above 1. In the ColorCert Chooser, select PantoneLIVE from the main menu and then User Login. 2. In the PantoneLIVE menu, enter the following server: http://ws.pantonelive.com Enter your My X-Rite Username and Password into the appropriate fields. Click Log In. May 20, 2014 Enabling PantoneLIVE in Colorcert 2.5 and above 3. The PantoneLIVE Palette window will open. 4 Double-Click the palette you wish to use, or single click and click ‘Select’. A dialog box will open indicating that the palette you wish to use has been loaded May 20, 2014 Enabling PantoneLIVE in Colorcert 2.5 and above To download additional palettes, select PantoneLIVE>Select Palette from the ColorCert Chooser. Refer to the ColorCert Startup and Configuration Guide for more information on how to use your ColorCert software. May 20, 2014 Enabling PantoneLIVE in Colorcert 2.5 and above If PantoneLIVE does not appear in the Chooser toolbar: If PantoneLIVE does not appear in the Chooser window as an option, select Window>Preferences and select the Network Tab. At the bottom of the screen you will see a checkbox to enable PantoneLIVE. -
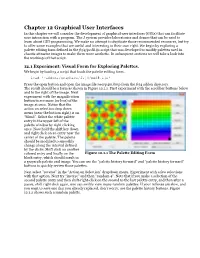
Chapter 12 Graphical User Interfaces
Chapter 12 Graphical User Interfaces In this chapter we will consider the development of graphical user interfaces (GUIs) that can facilitate user interaction with a program. The J system provides laboratories and demos that can be used to learn about GUI programming. We make no attempt to duplicate those recommended resources, but try to offer some examples that are useful and interesting in their own right. We begin by exploring a palette editing form defined in the fvj4/ped8.ijs script that was developed to modify palettes used in chaotic attractor images to make them more aesthetic. In subsequent sections we will take a look into the workings of that script. 12.1 Experiment: Visual Form for Exploring Palettes. We begin by loading a script that loads the palette editing form. load '~addons/graphics/fvj4/ped8.ijs' Press the open button and open the image file nearp4m.bmp from the fvj4 addon directory. The result should be a form as shown in Figure 12.1.1. First experiment with the scrollbar buttons below and to the right of the image. Next experiment with the magnification button to see more (or less) of the image at once. Notice that the action on selection drop down menu (near the bottom right) is on “blend”. Select the white palette entry in the upper left of the palette window by right clicking once. Now hold the shift key down and right click on an entry near the center of the palette. The palette should be modified to smoothly change along the interval defined by the clicks. -

INTRODUCTION Introducing Bella Corporation's DV Keyboard
KillerKeys® Express User Guide Windows Edition For KillerKeys Express software version 2.0 and later 1 Introduction ........................................................................................................................... 3 1.1 System Requirements .................................................................................................... 3 1.2 Installation ...................................................................................................................... 3 1.3 Launching the KillerKeys Program ............................................................................... 3 1.4 Interface Overview: Master Palette ............................................................................... 4 1.5 Interface Overview: Master Palette Compact View ...................................................... 5 1.6 Interface Overview: Floating Palette ............................................................................. 6 1.7 Interface Overview: Settings ......................................................................................... 7 1.8 Interface Overview: Group Settings .............................................................................. 8 2 Interface ................................................................................................................................. 9 2.1 Master Palette and Floating Palettes ............................................................................ 9 2.2 Favorites Groups...........................................................................................................11 -

Imagemaster Basic Paint
0111·ooi' style Copyright The painting cursor is wmmly a small crosshair. There are three kinds of ImageMaster:Basic Paint is copyrighted by JADA Graphics, Inc. The disk crosshair yon can use. The standard one is called the in verse cursor, which is not copy protected. You may make one backup copy of the disk. You may means that the cursor wm always be the inverse color from whatever color is not copy the manual. You may not distribute oopies of the software to any under it This is usually fine, but you may be using colors that make it hard to person(s) or inslitntion(s). This product is intended for use by the original see. the c1JXsoi.-. If you press the',.,' key, the cursor will change to a white purchaser on one computer only. Any violation of these restrictions is a viola cursor. If you press '=' again, you will get a black cursor. One more '=' gets tion of United States copyright law, and is hereby expressly forbidden. you back to !he inverse cmsor. Cursor visibility You may want to hide the cmsshair cmsor sometimes, as when working with small brushes in tight areas where a cursor might interfere with your view. You can toggle the cursor on/off by pressing !he '~' key. If you need help with ImageMru.ter:Basic Paint , or to place orders for other JADA Graphics products, caU or write to: Bmsb tmck:ing llll'l.Ode JADA Graphics, Inc. The brush tracking mode is normally set to 'color' mode. This means that as 7615 S.