International Journal of Engineering and Advanced Technology Vol
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
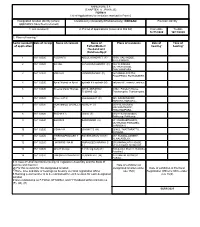
(CHAPTER V , PARA 25) FORM 9 List of Applications for Inclusion
ANNEXURE 5.8 (CHAPTER V , PARA 25) FORM 9 List of Applications for inclusion received in Form 6 Designated location identity (where Constituency (Assembly/£Parliamentary): KONGAD Revision identity applications have been received) 1. List number@ 2. Period of applications (covered in this list) From date To date 16/11/2020 16/11/2020 3. Place of hearing * Serial number$ Date of receipt Name of claimant Name of Place of residence Date of Time of of application Father/Mother/ hearing* hearing* Husband and (Relationship)# 1 16/11/2020 RUBIYATH ABDUL KHADAR T (F) 10/06, VALIKKODE, KALLADIKODE, , 2 16/11/2020 SUHAIL KUNJU MUHAMMED (F) 142/ CHEMBAN, MUTHUKURISSI, THACHAMPARA, , 3 16/11/2020 VINU A U UNNIKRISHNAN (F) 167 AMBALAVATTA, PALLIPPADI, POTTASSERY, , 4 16/11/2020 Ajmal Nishad vn Ajmal ayshabi k k ayshabi (M) valiyaveetil , mannur, mannur, , 5 16/11/2020 Aneena Maria Thomas AKHIL ABRAHAM 2/362 , Puliyileth House, THOMAS (O) Thachampara, Thachampara, , 6 16/11/2020 Praveen P R Ramadasan P (F) 965, KAKKENKODE KONGAD, KONGAD, , 7 16/11/2020 MUHAMMED BASHEER AIDRU P (F) 210 PALAKKANNI, P MACHAMTHODE, THACHAMPARA, , 8 16/11/2020 SNEHA K C Chami (F) 03/281 Kundukandam, Pallikurup, Pallikurup, , 9 16/11/2020 SOUMYA SASIKUMAR (H) 681 KUNDAMTHARIS, MUTHUKAD PARAMBU, KARIMBA II, , 10 16/11/2020 JISHA V K JAYAN T S (H) 06/462, THATTARATTU, KONGAD, , 11 16/11/2020 KRISHNAPRAKASH T RAVEENDRAN T M (F) 257, KUNDALASSERY, M KERALASSERY, , 12 16/11/2020 HARIKRISHNA M MURALEEDHARAN K S 206,KANNALATH HOUSE, (F) VELLAR OAD, MANKARA, , 13 16/11/2020 Ginu -

Martian Crater Morphology
ANALYSIS OF THE DEPTH-DIAMETER RELATIONSHIP OF MARTIAN CRATERS A Capstone Experience Thesis Presented by Jared Howenstine Completion Date: May 2006 Approved By: Professor M. Darby Dyar, Astronomy Professor Christopher Condit, Geology Professor Judith Young, Astronomy Abstract Title: Analysis of the Depth-Diameter Relationship of Martian Craters Author: Jared Howenstine, Astronomy Approved By: Judith Young, Astronomy Approved By: M. Darby Dyar, Astronomy Approved By: Christopher Condit, Geology CE Type: Departmental Honors Project Using a gridded version of maritan topography with the computer program Gridview, this project studied the depth-diameter relationship of martian impact craters. The work encompasses 361 profiles of impacts with diameters larger than 15 kilometers and is a continuation of work that was started at the Lunar and Planetary Institute in Houston, Texas under the guidance of Dr. Walter S. Keifer. Using the most ‘pristine,’ or deepest craters in the data a depth-diameter relationship was determined: d = 0.610D 0.327 , where d is the depth of the crater and D is the diameter of the crater, both in kilometers. This relationship can then be used to estimate the theoretical depth of any impact radius, and therefore can be used to estimate the pristine shape of the crater. With a depth-diameter ratio for a particular crater, the measured depth can then be compared to this theoretical value and an estimate of the amount of material within the crater, or fill, can then be calculated. The data includes 140 named impact craters, 3 basins, and 218 other impacts. The named data encompasses all named impact structures of greater than 100 kilometers in diameter. -

PROVISIONAL RANK LIST for M.A Economics (Environmental Economics)
PROVISIONAL RANK LIST FOR M.A Economics (Environmental Economics) Sl. Total No. RegNo RollNo Candidate's Name Father's Name Gender Cateogry Mark 1 PG20003570 21240487 AKALANKPRAKASH J JAYA KUMAR A MALE GENERAL 88.75 2 PG20027277 21763258 ANIRUDH KHAKOLIA KRISHNA KANT KHAKOLIA MALE GENERAL 88.00 3 PG20024331 21991387 ALBERT ABRAHAM ABRAHAM N C MALE GENERAL 86.50 4 PG20007025 21763077 PARNIKA SETHI DHARMENDRA SETHI FEMALE GENERAL 84.00 5 PG20042887 21710142 ARNAV ASHISH DESHPANDE ASHISH LALIT DESHPANDE MALE GENERAL 83.50 6 PG20019986 21763197 NEHA CHAUHAN GAJENDRA SINGH CHAUHAN FEMALE GENERAL 82.50 7 PG20009278 22031033 STENY RAPHEAL RAPHEAL SEBASTIAN FEMALE GENERAL 82.50 8 PG20011706 21390790 SIMRAN K KARUNAKAR K FEMALE GENERAL 82.25 9 PG20015934 21571613 ANTARIKHYA OJHA SAROJ KUMAR OJHA MALE GENERAL 81.50 10 PG20021643 21791430 SHAMBHAVI PATNAIK BHUBANA NANDA PATNAIK FEMALE GENERAL 81.50 11 PG20050266 21763406 NIDHI MAHESHWARI VINEET MAHESHWARI FEMALE GENERAL 81.00 12 PG20024080 21571639 PARNADIP DASGUPTA PRADIP DASGUPTA MALE GENERAL 80.25 13 PG20006560 21571573 TANWISHA CHAUDHURI ARUP PRAKASH CHAUDHURI FEMALE GENERAL 79.75 14 PG20000240 21762995 KSHITIJ SAHDEV KSHITIJ SAHDEV MALE GENERAL 79.50 15 PG20003460 21763031 ASHWARIYA SAH HARSHIT SAH FEMALE GENERAL 79.50 16 PG20031793 21571675 SENJUTI KARMAKAR PARTHA KARMAKAR FEMALE GENERAL 79.50 17 PG20054945 21030095 G ANJANALAKSHMI P GANESH FEMALE GENERAL 79.25 18 PG20064066 21763489 AKASH AGARWAL PANKAJ AGARWAL MALE GENERAL 79.25 19 PG20070272 21763531 VIBHU JAIN BIJENDRA KUMAR JAIN FEMALE -

1607/2015 Listed Before Hon'ble DB-I at Item No.12 Is Deleted
19.07.2017 SUPPLEMENTARY LIST SUPPLEMENTARY LIST FOR TODAY IN CONTINUATION OF THE ADVANCE LIST ALREADY CIRCULATED. THE WEBSITE OF DELHI HIGH COURT IS www.delhihighcourt.nic.in INDEX PRONOUNCEMENT OF JUDGMENTS -----------------> 01 TO 01 REGULAR MATTERS ----------------------------> 01 TO 105 FINAL MATTERS (ORIGINAL SIDE) --------------> 01 TO 12 ADVANCE LIST -------------------------------> 01 TO 82 APPELLATE SIDE (SUPPLEMENTARY LIST)---------> 83 TO 100 APPELLATE SIDE (SUPPLEMENTARY LIST)---------> 101 TO 124 ORIGINAL SIDE (SUPPLEMENTARY I)-------------> 125 TO 130 COMPANY ------------------------------------> 131 TO 131 SECOND SUPPLEMENTARY -----------------------> 132 TO 142 MEDIATION CAUSE LIST -----------------------> 01 TO 03 PRE-LOK ADALAT ----------------------> 01 TO 01 NOTES 1. Mentioning of urgent matters will be before Hon'ble DB-I at 10.30 A.M. DELETIONS 1. W.P.(C) 1607/2015 listed before Hon'ble DB-I at item No.12 is deleted. 2. LPA 271/2016 listed before Hon'ble DB-VI at item No.2 is deleted as the same is listed before special DB comprising Hon'ble Ms. Justice Hima Kohli and Hon'ble Ms. Justice Sangita Dhingra Sehgal. 3. W.P.(CRL.) 889/2016 listed before Hon'ble DB-VIII at item No.4 is deleted as the same is fixed for 21.07.2017. 4. CRL.M.C. 2734/2017 listed before Hon'ble Mr. Justice I.S.Mehta at item No.50 is deleted as the same is returned to Filing Counter. 5. CONT.CAS.(C) 418/2017 listed before Hon'ble Mr. Justice A.K.Chawla at item No.40 is deleted as the same is fixed for 19.08.2017. 6. CRL.L.P. -

Appendix I Lunar and Martian Nomenclature
APPENDIX I LUNAR AND MARTIAN NOMENCLATURE LUNAR AND MARTIAN NOMENCLATURE A large number of names of craters and other features on the Moon and Mars, were accepted by the IAU General Assemblies X (Moscow, 1958), XI (Berkeley, 1961), XII (Hamburg, 1964), XIV (Brighton, 1970), and XV (Sydney, 1973). The names were suggested by the appropriate IAU Commissions (16 and 17). In particular the Lunar names accepted at the XIVth and XVth General Assemblies were recommended by the 'Working Group on Lunar Nomenclature' under the Chairmanship of Dr D. H. Menzel. The Martian names were suggested by the 'Working Group on Martian Nomenclature' under the Chairmanship of Dr G. de Vaucouleurs. At the XVth General Assembly a new 'Working Group on Planetary System Nomenclature' was formed (Chairman: Dr P. M. Millman) comprising various Task Groups, one for each particular subject. For further references see: [AU Trans. X, 259-263, 1960; XIB, 236-238, 1962; Xlffi, 203-204, 1966; xnffi, 99-105, 1968; XIVB, 63, 129, 139, 1971; Space Sci. Rev. 12, 136-186, 1971. Because at the recent General Assemblies some small changes, or corrections, were made, the complete list of Lunar and Martian Topographic Features is published here. Table 1 Lunar Craters Abbe 58S,174E Balboa 19N,83W Abbot 6N,55E Baldet 54S, 151W Abel 34S,85E Balmer 20S,70E Abul Wafa 2N,ll7E Banachiewicz 5N,80E Adams 32S,69E Banting 26N,16E Aitken 17S,173E Barbier 248, 158E AI-Biruni 18N,93E Barnard 30S,86E Alden 24S, lllE Barringer 29S,151W Aldrin I.4N,22.1E Bartels 24N,90W Alekhin 68S,131W Becquerei -
In Pdf Format
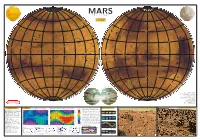
lós 1877 Mik 88 ge N 18 e N i h 80° 80° 80° ll T 80° re ly a o ndae ma p k Pl m os U has ia n anum Boreu bal e C h o A al m re u c K e o re S O a B Bo l y m p i a U n d Planum Es co e ria a l H y n d s p e U 60° e 60° 60° r b o r e a e 60° l l o C MARS · Korolev a i PHOTOMAP d n a c S Lomono a sov i T a t n M 1:320 000 000 i t V s a Per V s n a s l i l epe a s l i t i t a s B o r e a R u 1 cm = 320 km lkin t i t a s B o r e a a A a A l v s l i F e c b a P u o ss i North a s North s Fo d V s a a F s i e i c a a t ssa l vi o l eo Fo i p l ko R e e r e a o an u s a p t il b s em Stokes M ic s T M T P l Kunowski U 40° on a a 40° 40° a n T 40° e n i O Va a t i a LY VI 19 ll ic KI 76 es a As N M curi N G– ra ras- s Planum Acidalia Colles ier 2 + te . -

Govt.Vocational HSS Girls,Nadakkavu,Kozhikode Register Sl.No
Govt.Vocational HSS Girls,Nadakkavu,Kozhikode Register Sl.no. No. Roll No. Name of Candidate Center Opted Test Code Govt.Vocational HSS 1 210343 21011014 SMRUTHI HAREENDRAN Girls,Nadakkavu,Kozhikode 21011 Govt.Vocational HSS 2 210762 21011029 SHAIK JAVEED AHMED Girls,Nadakkavu,Kozhikode 21011 Govt.Vocational HSS 3 210912 21011036 AKSHAYA SURESH Girls,Nadakkavu,Kozhikode 21011 Govt.Vocational HSS 4 210927 21011040 UNNIMAYA T Girls,Nadakkavu,Kozhikode 21011 Govt.Vocational HSS 5 210929 21011041 SILPA K Girls,Nadakkavu,Kozhikode 21011 Govt.Vocational HSS 6 210934 21011043 ATHIRA O Girls,Nadakkavu,Kozhikode 21011 Govt.Vocational HSS 7 210983 21011051 ANUSREE MOHAN Girls,Nadakkavu,Kozhikode 21011 Govt.Vocational HSS 8 211091 21011062 ASWATHI P Girls,Nadakkavu,Kozhikode 21011 Govt.Vocational HSS 9 211095 21011063 JASVA USMAN Girls,Nadakkavu,Kozhikode 21011 Govt.Vocational HSS 10 211151 21011067 PRAVEENA P Girls,Nadakkavu,Kozhikode 21011 Govt.Vocational HSS 11 211632 21011097 ATHUL NALIN S DAS Girls,Nadakkavu,Kozhikode 21011 Govt.Vocational HSS 12 211909 21011128 BOSCARDIN WANIKA Girls,Nadakkavu,Kozhikode 21011 Govt.Vocational HSS 13 211990 21011135 GOKULA G NATH Girls,Nadakkavu,Kozhikode 21011 Govt.Vocational HSS 14 212291 21011147 ANEES AL JALEES Girls,Nadakkavu,Kozhikode 21011 Govt.Vocational HSS 15 210109 21021007 SREESHNA VIRUTHIYIL Girls,Nadakkavu,Kozhikode 21021 Govt.Vocational HSS 16 210112 21021008 GEETHU S BABU Girls,Nadakkavu,Kozhikode 21021 Govt.Vocational HSS 17 210121 21021009 SHAHID ANWAR Girls,Nadakkavu,Kozhikode 21021 Govt.Vocational -
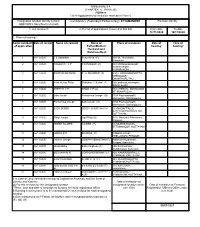
(CHAPTER V , PARA 25) FORM 9 List of Applications for Inclusion
ANNEXURE 5.8 (CHAPTER V , PARA 25) FORM 9 List of Applications for inclusion received in Form 6 Designated location identity (where Constituency (Assembly/£Parliamentary): ETTUMANOOR Revision identity applications have been received) 1. List number@ 2. Period of applications (covered in this list) From date To date 16/11/2020 16/11/2020 3. Place of hearing * Serial number$ Date of receipt Name of claimant Name of Place of residence Date of Time of of application Father/Mother/ hearing* hearing* Husband and (Relationship)# 1 16/11/2020 T S Sasankan Sukumaran (F) 10/314, Thoranathu, Aymanam, , 2 16/11/2020 PRASANTH V P P D PRASAD (F) 189 VENGALIKKALAM, KUMARAKOM , KUMARAKOM, , 3 16/11/2020 SWATHY KRISHNA P G PRADEEP (F) 4/314 PADINJAREKUTTU, NEENDOOR, ONAMTHURUTHU, , 4 16/11/2020 Kiran Kurian Philip Shibymon C Kurian (F) 550, padinjattumbhagam, Athirampuzha, , 5 16/11/2020 KEERTHI C P KIRAN C P (O) 553 CHERIVIL, MANNANAM, ATHIRAMPUZHA, , 6 16/11/2020 Babu Jacob Ponnamma Joseph (O) 510A Pazhayampallil, Mannanam, Athirampuzha, , 7 16/11/2020 Ponnamma Joseph Babu Jacob (H) 510A Pazhayampallil, Mannanam, Athirampuzha, , 8 16/11/2020 SUBY BOBBY BOBBY CHERIYAN (H) 233/MADAPPALLIL, SREEKANDAMANGALAM, KOTTAYAM, , 9 16/11/2020 Philip Joseph Sigi Philip (O) B412 Maniyalil, Ettumanoor, Kottayam, , 10 16/11/2020 AMEER NAJEEB NAJEEB (F) 13,NAJEEB MANZIL, ETTUMANOOR, KOTTAYAM, , 11 16/11/2020 GOKUL K R SIVADAS (F) 1 REMALAYAM, THELLAKOM, PEROOR, , 12 16/11/2020 Naveen Joseph JOSEPH SEBASTIAN (F) Pathinanchil parambil, Karippa, Arpookara, , 13 16/11/2020 -
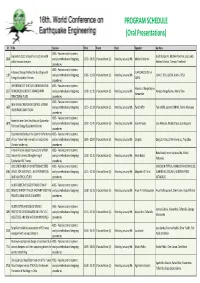
PROGRAM SCHEDULE (Oral Presentations)
PROGRAM SCHEDULE (Oral Presentations) ID Title Session Time Room Date Speaker Authors 40SS - Passive control systems: Equivalent static analysis for structures with Giada Gasparini, Michele Palermo, Luca Landi, 2030 analysis methods and designing 10:30 - 10:45 Vitacura Room (1) Monday, January 9th Michele Palermo added viscous dampers Stefano Silvestri, Tomaso Trombetti procedures 40SS - Passive control systems: A General Design Method for Buildings with JUAN CARLOS DE LA 1187 analysis methods and designing 10:45 - 11:00 Vitacura Room (1) Monday, January 9th JUAN C. DE LA LLERA, JUAN J. BESA Energy Dissipation Devices LLERA procedures IMPORTANCE OF DUCTILE CONFINEMENT IN 40SS - Passive control systems: Horacio J. Nangullasmu- 3327 REINFORCED CONCRETE FRAMES WITH analysis methods and designing 11:00 - 11:15 Vitacura Room (1) Monday, January 9th Horacio Nangullasmu, Arturo Tena Hernandez STRUCTURAL FUSES procedures 40SS - Passive control systems: NEW SEISMIC RESPONSE CONTROL SYSTEM 1652 analysis methods and designing 11:15 - 11:30 Vitacura Room (1) Monday, January 9th Taiki SAITO Taiki SAITO, Satoshi DENNO, Toshio Maekawa USING BLOCK AND TACKLE procedures 40SS - Passive control systems: Eccentric Lever Arm Amplification System for 3870 analysis methods and designing 11:30 - 11:45 Vitacura Room (1) Monday, January 9th Jose Almazan Jose Almazan, Nicolas Tapia, Juan Baquero Frictional Energy Dissipation Devices procedures Experimental Study on the Seismic Performance 40SS - Passive control systems: 1223 of Four-Tower High-rise with an isolated -

Scenes of Southeast Asia C
JUNE 2016 SEE ASIA AND BEYOND WITH SILKAIR TIPS FOR 7 TRAVELLING WITH A CHILD IN A WHEELCHAIR INSIDE FUJIAN’S FORTRESS HOMES COOL 5 EXPERIENCES IN LOMBOK SCENES OF SOUTHEAST ASIA C M Y CM MY CY CMY K 06.2016 22 COMING FULL CIRCLE 42 FLEETING MOMENTS Life in a Fujian tulou Tableaus of Asian life 30 THE GREAT FRONTIER 50 一碗河粉的传奇 Best of the Top End 被誉为“河内之汤”的越南河 粉 ,以 清 、甜 、香 的 独 特 风 味 36 WAY OF THE SHAN 俘虏世界,渗透灵魂 Ancient skills of Myanmar’s SO PHO, SO GOOD largest indigenous tribe Slurp up a hearty bowl of Vietnam’s favourite noodles GETTY IMAGES GETTY 20 FOLLOW US ON SOCIAL MEDIA facebook.com/SilkAir twitter.com/SilkAir instagram.com/SilkAir Take home this copy of Silkwinds and share it with your friends and family! Past issues are also available online at silkair.com LATEST AWARDS Travel Media of the Year (Merit), Media Publishers Association Singapore (MPAS) Awards 2014 Best Feature on Asian 18 Travel (Excellence) Best Wellness Feature (Excellence), Asian Publishing Awards 2014 Silkwinds is published exclusively for SilkAir by Publicitas Publishing E-mail: [email protected] publicitas.com/publishingasia REGIONAL MANAGING DIRECTOR Lee Walsh GENERAL MANAGER Betty Liswanty 16 RELATIONSHIP MANAGER Serene Lee 4 THE BIG PICTURE EDITORIAL Tug of war, Sabah EXECUTIVE CONTENT DIRECTOR Rod Mackenzie 6 HOT PICKS MANAGING EDITOR Ming Rodrigues Trends and items to covet DEPUTY EDITOR Nelissa Hernandez DESIGN DIRECTOR Fredrik Dittlau 12 4 QUESTIONS WITH... ADVERTISING Fazal Bahardeen, HalalTrip MEDIA SPECIALIST Mey Leong Tel: +65 6735 8681 ext 331 14 WHAT’S ON E-mail: [email protected] Things to do this month MATERIALS Doreen Lau E-mail: [email protected] 16 2 PERFECT DAYS IN LOMBOK Catch Bau Nyale, visit a secret Gili, and enjoy waterfall walks 68 The views and opinions expressed or 18 FOOD SNAPSHOT WELCOME ABOARD implied in Silkwinds do not necessarily Dok fak thong tod 54 SILKAIR EXPERIENCE reflect those of SilkAir or Publicitas Publishing. -

KERALA UNIVERSITY of FISHERIES and OCEAN STUDIES ADMISSION 2020-21 Reg
PRIORITIZED RANK LIST OF P.G.ENTRANCE EXAMINATION BASED ON DATE OF BIRTH FOR SAME RANK HOLDERS KERALA UNIVERSITY OF FISHERIES AND OCEAN STUDIES ADMISSION 2020-21 Reg. Category Rank No Applicant AAH - MFSc. Aquatic Animal Health Management GEN - GENERAL 1 300946 AISWARYA S GEN - GENERAL 2 301275 SHIJINA P NAMBIAR GEN - GENERAL 3 300793 POOJA CHITHIRA GEN - GENERAL 4 300988 SHILPA PRADEEP GEN - GENERAL 5 300989 ABHIRAMI N GEN - GENERAL 6 301002 JOBINS KURIAN GEN - GENERAL 7 300512 JEBARSON SOLOMON GEN - GENERAL 8 301482 PORKODI MANI GEN - GENERAL 9 301063 GANESH KUMAR T GEN - GENERAL 10 301306 SILPA R GEN - GENERAL 11 301075 ANGEL AYANA K J GEN - GENERAL 12 300869 AMALA JIJI GEN - GENERAL 13 301043 SONA G JAIN GEN - GENERAL 14 301152 LEKSHMI S R GEN - GENERAL 15 301048 SANDRA K S GEN - GENERAL 16 301581 RYAN BABU GEN - GENERAL 17 301016 BHARATH JAYARAM GEN - GENERAL 18 300835 LIGI JOSE GEN - GENERAL 19 301117 VRINDA P K GEN - GENERAL 20 300924 RINI MATHEW GEN - GENERAL 21 301706 P BHARATHI RAJA GEN - GENERAL 22 300393 SHIBINA M GEN - GENERAL 23 300651 ABISHA S GEN - GENERAL 24 300859 AISWARYA K P GEN - GENERAL 25 300899 LEENA DEVADAS M GEN - GENERAL 26 301013 ANJITHA T SASI GEN - GENERAL 27 301339 TREASA MERIN PIOUS GEN - GENERAL 28 301122 APARNA ANIL GEN - GENERAL 29 300947 MERIN TREESA VARGHESE GEN - GENERAL 30 301758 NAVEEN NIVAS GEN - GENERAL 31 301264 SHANIJA SHAMSUDHEEN GEN - GENERAL 32 301328 THASLEEMA ASHRAF GEN - GENERAL 33 301143 DIVYA ALEX M GEN - GENERAL 34 301763 VEERA PRITHIV RAJ GEN - GENERAL 35 300733 GOKULPRASANTH M GEN - GENERAL 36 300428 LAV KUSH GEN - GENERAL 37 301163 HENNA SHUKOOR A GEN - GENERAL 38 301186 MELBIN LAL GEN - GENERAL 39 302219 AKSHAY A GEN - GENERAL 40 301320 V RESHMA RANJITH GEN - GENERAL 41 300961 ARCHANA SANTHOSH GEN - GENERAL 42 301407 AJAY KUMAR VERMA GEN - GENERAL 43 300480 KUWAR BAHADUR YADAV GEN - GENERAL 44 301664 SREE RAM 1 | 116 Reg. -
NEWSLETTER (Affiliated to Mahatma Gandhi University) Vol
St. Paul's College NAAC Re-accredited Institution with 'A' Grade NEWSLETTER (Affiliated to Mahatma Gandhi University) Vol. 50 Issue-2 June 2016 Kalamassery-683 503 Reflections As this issue of 'Reflections' reaches its readers, St. Paul's College, Kalamassery is basking in the glory of a well deserved achievement –the award of an 'A' grade (with grade point 3.14) by the National Assesment and Accreditation Council, or 'NAAC' as it is better known. For the Pauline family, it is not a mere achievement, it is the fruit of long, hard labour; the realization of their power to dream big and the crystallization of a cherished wish. St. Paul's College officially put itself up for the process of accreditation with the submission of the Letter of Intention to the UGC office. With the strong support of the Manager, Fr. Felix Chakkalakkal, the able leadership of the Principal Dr. Edwin Xavier, the energetic NAAC The NAAC Peer team members handing over the assessment report to the college Principal convenor Dr. V. J. Peter and the acumen of the IQAC coordinator Dr. Reena J. Andrews, the teaching and non teaching staff were divided into seven teams. Each team was assigned the stupendous task of collecting, processing and analysing the data required for each of the seven criteria comprising the Self Study Report. As the name suggests, this report showcases the College, and a lot depended on how this turned out. From then on, it was a frenzy of activity. Academics could not be compromised on, the Golden The NAAC Peer team with the IQAC coordinator, Manager, Principal and NAAC Co-ordinator.