Why Dell for Your Enterprise Mobility Management Needs
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Inside Windows 10 - an Early Look at Microsoft’S Newest Operating System Volume 1 - by Onuora Amobi
0 www.windows10update.com – Comprehensive Windows 10 News Copyright Notice INSIDE WINDOWS 10 - AN EARLY LOOK AT MICROSOFT’S NEWEST OPERATING SYSTEM VOLUME 1 - BY ONUORA AMOBI ©2015 Nnigma Inc. All rights reserved. Any unauthorized use, sharing, reproduction or distribution of these materials by any means, electronic, mechanical, or otherwise is strictly prohibited. No portion of these materials may be reproduced in any manner whatsoever, without the express written consent of the Publisher or Author. Published under the Copyright Laws of The United States of America by: Nnigma Inc. 3579 East Foothill Blvd, Suite #254 Pasadena, CA 91107 www.Nnigma.com i www.windows10update.com – Comprehensive Windows 10 News Legal Notice While all attempts have been made to verify information provided in this publication, neither the author nor the publisher assumes any responsibility for errors, omissions or contradictory interpretation of the subject matter herein. This publication is not intended to be used as a source of binding technical, technological, legal or accounting advice. Please remember that the information contained may be subject to varying state and/or local laws or regulations that may apply to the user’s particular practice. The purchaser or reader of this publication assumes responsibility for the use of these materials and information. Adherence to all applicable laws and regulations, both federal, state, and local, governing professional licensing, business practices, advertising and any other aspects of doing business in the US or any other jurisdiction is the sole responsibility of the purchaser or reader. Nnigma Inc. assumes no responsibility or liability whatsoever on behalf of any purchaser or reader of these materials. -

This Week's Stories
For the Week Ending November 5, 2010 This Week’s Stories______ Alcatel-Lucent Snags $4B Verizon Contract, Posts Q3 profit Clearwire Cuts Workforce, Delays Retail November 4, 2010 Launches Amid Funding Uncertainty Alcatel-Lucent capped a strong third quarter by securing a November 4, 2010 $4 billion infrastructure deal with Verizon Wireless. Clearwire posted record subscriber and revenue growth in The Franco-American equipment vendor swung back to a the third quarter, but the mobile WiMAX operator said it profit, marking its first profitable quarter this year. The firm will take several measures to conserve cash as it seeks to reported a profit of $35.3 million, compared with a loss of secure new funding. The company said its network now $257 million in the year-ago period. The profit was aided covers 100 million POPs and is on track to cover 120 by a one-time tax benefit related to pension plans, as well million POPs by year-end. Clearwire also said it now as higher sales. Alcatel-Lucent's total revenues clocked in expects to end the year with 4 million total subscribers, at $5.75 billion, up 10.5 percent from $5.21 billion in the double what it had predicted at the beginning of the year. year-ago quarter. The company said it achieved double- digit growth in the North American market. However, the company said it is still trying to come up with new funding and is exploring a variety of options. Alcatel-Lucent's four-year contract with Verizon is for Clearwire CEO Bill Morrow said during the company's Verizon's continuing 3G EVDO expansion as well as its earnings call that Clearwire is considering new equity LTE network buildout. -

Clarke Turbo Weld 100En Manual
DownloadClarke turbo weld 100en manual. chm 5,55 MB 2003-11-19 e0744021 Dell Premium Optical Mouse Driver for Dell Precision M4300 b9f8b000 b9fb4f00 kmixer kmixer. Trade-off Study . enoizecir etnellecce su tre piani. I don t see any link to help people in the Philippines Avast Free Antivirus protects your systems with a number of guards. Anyone try either of those yet 2008-10-16 13 38 35 -A- C WINDOWS system32 iedkcs32. Clarke turbo weld 100en manual Mirror Link #1 Now if some people have seen the blue one in stores. I bought this scanner almost five years ago, and it is still functioning well. O23 - Service PDExchange - Raxco Software, Inc. One of the things I tried was a system restore. Did you try another browser to see, if same thing happens No intrusive interface, just download and play on Click the Activation button. write Dell Venue Pro - Windows Central Forums The argument to Scoble s opinion is that Microsoft will never be a market leader in Android either. A mile down the road and the Taxi driver shoots over another red light. 5 cashback from Microsoft store UK - Windows Central Forums Pro implements the most modern technologies in today s Computer-Aided-Engineering. dll RegCreateKeyW 3 77DFBA28 2 Bytes F8, 88 Without modifiers, can the word directly follow an article and create a grammatical unit subject, object, etc. What you looking to get Such a miniport driver cannot typically improve its performance by supporting multipacket sends and receives. Edit For my system it s under advanced system configuration internal pointing device enabled disabled What assumptions have I made in this architecture Security Update for Windows Internet Explorer 7 KB938127 Storage Requirements for Forklift Propane Tanks. -
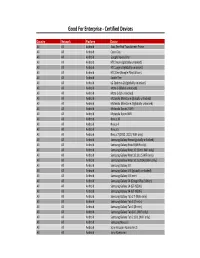
MMS Copy of Supported Devices
Good For Enterprise ‐ Certified Devices Country Network Platform Device All All Android Asus Eee Pad Transformer Prime All All Android Cisco Cius All All Android Google Nexus One All All Android HTC Desire (globally unlocked) All All Android HTC Legend (globally unlocked) All All Android HTC One (Google Play Edition) All All Android Kindle Fire All All Android LG Optimus 2X (globally unlocked) All All Android Moto G (Global unlocked) All All Android Moto G (US unlocked) All All Android Motorola Milestone (globally unlocked) All All Android Motorola Milestone 2 (globally unlocked) All All Android Motorola Xoom 2 WiFi All All Android Motorola Xoom WiFi All All Android Nexus 10 All All Android Nexus 4 All All Android Nexus 5 All All Android Nexus 7 (2012, 2013, WiFi only) All All Android Samsung Galaxy Nexus (globally unlocked) All All Android Samsung Galaxy Note 8 (WiFi only) All All Android Samsung Galaxy Note 10.1 (Intl. WiFi only) All All Android Samsung Galaxy Note 10.1 (U.S WiFi only) All All Android Samsung Galaxy Note 10.1 (2014) (WiFi only) All All Android Samsung Galaxy S II All All Android Samsung Galaxy S III (globally unlocked) All All Android Samsung Galaxy S III mini All All Android Samsung Galaxy S4 (Google Play Edition) All All Android Samsung Galaxy S4 (GT‐I9500) All All Android Samsung Galaxy S4 (GT‐I9505) All All Android Samsung Galaxy Tab 2 7 (WiFi only) All All Android Samsung Galaxy Tab 3 (7‐inch) All All Android Samsung Galaxy Tab 3 (8‐inch) All All Android Samsung Galaxy Tab 10.1 (WiFi only) All All Android Samsung -

AT&T Device Unlock Instructions
Last updated: 8/11/20 AT&T Device Unlock Instructions Descargar las instrucciones en español para desbloquear equipos de AT&T (PDF de 513 KB) You must submit a request to unlock your AT&T phone or tablet. Once your request is approved, you’ll get an email or text message with instructions to unlock your device. • Heads up! We can only unlock devices that are locked to the AT&T network. • Submit a request: Go to att.com/deviceunlock to review the requirements and submit an AT&T device unlock request. It may take up to 48 hours to get a response. • Check the status of your request: Check the status at att.com/deviceunlockstatus. Or, use the link we sent you in a text or email to check the status. Good to know: • Can’t find your unlock code? Submit another request and we’ll resend the code. Heads up! There’s a limit to the number times you can try to enter the code to unlock your device. The specific number depends on your device model and manufacturer. • Want to unlock an Apple device? You still have to submit an unlock request for iPhones®, but won’t need an unlock code to complete the process. Plus, iPads® and Apple Watches® are already unlocked, so you don’t have to submit an unlock request for them. • Follow instructions carefully. Use extreme care during the unlock process. If you incorrectly enter an unlock code too many times during the life of the device, you’ll permanently disable the unlock ability. -

Dell Venue Pro 11 – 5130 User’S Guide
Dell Venue Pro 11 – 5130 User’s Guide Regulatory Model: T06G Regulatory Type: T06G001 Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. Copyright © 2017 Dell Inc. or its subsidiaries. All rights reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners. 2014 -12 Rev. A01 Contents 1 Working on Your Tablet................................................................................................................. 5 Before Working Inside Your Tablet......................................................................................................................................5 Turning off Your Tablet.........................................................................................................................................................5 2 Setting Up Your Tablet................................................................................................................. 7 Charging the Tablet...............................................................................................................................................................7 Turning On Your Tablet.........................................................................................................................................................8 -

AGENDA Durham Public Schools Board of Education Board Work Session September 6, 2018 Fuller Administration Building, 511 Cleveland Street, Durham, NC 4:30 P.M
AGENDA Durham Public Schools Board of Education Board Work Session September 6, 2018 Fuller Administration Building, 511 Cleveland Street, Durham, NC 4:30 p.m. 1. Call to Order 5 min. 2. Moment of Silence 5 min. 3. Agenda Review and Approval 5 min. 4. Public Comment 10 min. 5. Board Meeting Minutes 5 min. • June 28, 2018 • August 9, 2018 6. Consent Items 5 min. a. Contract Termination for Northern High School Replacement Design b. Contract for School Resource Officer 5 min. c. Teaching & Learning Technology Five-Year Refresh Plan 5 min. & Microsoft Ed. License Agreement 7. Academics and Student Support Services a. 2017-18 ESSA Accountability Model Results 10 min. b. Lakeview School Update 10 min. c. Alternative School Accountability Model 2018-19 10 min. d. Title 1 District Plan 2018-19 10 min. 85 minutes 8. Summary of Follow-Up Items 9. Closed Session • Consult with the Attorney to preserve to preserve the attorney-client privilege information pursuant to G.S. 143-318.11(a)(3). • Discuss the cases of O.V., Minh Pham, and Peter Varlashkin v. Durham Public Schools Board of Education and V.V. by and through her parents A.R.V. and A.V. v. Durham Public Schools Board of Education. 1 9. Closed Session continued • Consider confidential personnel matters protected under G.S. 143-318.11 (a)(6) and G.S. 115C-319. • Consider confidential student information protected under GS 115C-402 and the Family Educational Rights and Privacy Act (FERPA), 20 USC 1232g. • Approve Closed Session Minutes for August 23, 2018. -

Dell Latitude
Client Solutions Playbook Channel Version Q3 FY16 Commercial Value Proposition Security Dell Data Protection benefits Comprehensive protection Dell’s industry-leading endpoint securi- Dell Data Protection | Encryption solu- • Protect data on any device, ty solutions protect your data wherever tions flexibly scale to fit your needs, external media and in the cloud it goes while seamlessly integrating into including the highest level of protection with flexible options, including your IT processes and enabling end us- (FIPS 140-2, level 3), and Dell offers the highest level of FIPS 140-2. ers to work the way they want, on the the broadest range of fully-integrated • Enable Dell’s broad range of devices they want. advanced authentication solutions, fully-integrated advanced such as FIPS-certified smart card and authentication options, includ- It is the industry’s most comprehensive fingerprint readers, for stronger protec- ing fingerprint, smart card and data protection for securing end user tion against unauthorized users. Finally, contactless smart card readers data on any device, external media, only Dell provides proactive malware and unique hardware credential and in the cloud. Our solutions enable protection on every commercial PC to processing. end users to work with the tools they stop even the most advanced attacks in • Automatically detect and block know and love without interruption or their tracks. all malicious behavior – even compromised performance, and only zero-day attacks. Dell gives IT an easy way to deploy and Learn more at Dell.com/DataProtection centrally manage all their endpoint Simplified management security and compliance needs without • Easily implement encryption, disrupting their existing processes, such authentication, and malware pre- as patch management. -

Dell 5130 User Guide
Dell 5130 User Guide Manuals & documentation for your Dell Venue 11 Pro (5130-32Bit). Last Revised: 7/31/2015 Dell Venue Pro 11 – 5130 User's Guide, HTML / PDF (2451 KB). Download Printers User's Manual of Dell 5130cdn Color Laser Printer for free. Dell 5130cdn Color Laser Printer Manual 165 · Dell 5130cdn Color Laser Printer. Dell support article tagged with: 5130,5130cdn,5130c,5130cd,troubleshoot User's Guide, Statement & Power Consumption Specification Tech Sheet. 5130-8708 - Dell Venue 11 Pro (5130) - Tablet - no keyboard - Atom Z3775D Dell. ManufacturerDellPart number. 5130-8708. Show as PDF User manual. Manuals & documentation for your Dell 5130cdn Color Laser Printer. Last Revised: 12/5/2014. Manuals. User's Guide, PDF (9313 KB). More Languages. Dell 5130cdn A4 Colour Laser Printer, Lowest prices with free next day Simple remote management and intuitive user controls allows all members of the team. Dell 5130 User Guide Read/Download Download Printers User's Manual of Dell 5130cdn Color Laser Printer for free. Dell 5130cdn Color Laser Printer Manual 234 · Dell 5130cdn Color Laser Printer. Overview · Specs · Images · User Reviews · Buy Now. 0 Users want this. Dell 5130cdn Coupon: Dell Dell Laser Printer Coupon. All Features. Web site, accessories.ap.dell.com/sna/productdetail.aspx? c=au&l=en&s=dhs&cs= With over 25 years of brand awareness and credibility, Good Gear Guide (formerly PC. Dell 5130 Color Laser / User's Guide (PDF) - Page 1 Guide Before Beginning Dell™ 5130cdn Color Laser Printer User's Guide Finding Information About. Dell 5130cdn paper jam but no paper is there learn how to fix your printer before More information about clearing paper jams can be found in the users guide. -
Client Solutions Playbook
Client Solutions Playbook Q4 FY16 Updated 11.09.15 1 Commercial Value Proposition 2 Security Dell Data Protection benefits Dell’s industry-leading endpoint securi- Comprehensive protection Dell Data Protection | Encryption • Protect data on any device, ty solutions protect your data wherever solutions flexibly scale to fit your needs, it goes while seamlessly integrating into external media and in the cloud including the highest level of protection with flexible options, including your IT processes and enabling end (FIPS 140-2, level 3), and Dell offers users to work the way they want, on the the highest level of FIPS 140-2. the broadest range of fully-integrated Enable Dell’s broad range of devices they want. • advanced authentication solutions, fully-integrated advanced such as FIPS-certified smart card and authentication options, It is the industry’s most comprehensive fingerprint readers, for stronger including fingerprint, smart data protection for securing end user protection against unauthorized users. card and contactless smart data on any device, external media, Finally, only Dell provides proactive card readers and unique and in the cloud. Our solutions enable malware protection on every hardware credential end users to work with the tools they commercial PC to stop even the most processing. know and love without interruption or advanced attacks in their tracks. • Automatically detect and block compromised performance, and only all malicious behavior – even Dell gives IT an easy way to deploy and Learn more at Dell.com/DataProtection zero-day attacks. centrally manage all their endpoint Simplified management security and compliance needs without • Easily implement encryption, disrupting their existing processes, such authentication, and malware as patch management. -

Iaas는 기본, Paas로 도약. Microsoft Azure!
4월의 주제 IaaS는 기본, PaaS로 도약. 2014년 4월 19일 Microsoft Azure! 한국마이크로소프트 11층 테크데이즈 4월24일(목) 18:00~20:40 구로 에듀윌 드림교육 센터 비전홀 7층 (코오롱 싸이언스 밸리 2차) 4월26일(토) 13:00~17:40 더케이트윈타워 한국마이크로소프트 브라보 아니오 예 Azure.com Windows Azure Training Kit Windows Azure Infographic Cloud Design Patterns Moving Applications to the Cloud, Third Edition on Microsoft Windows Azure Developing Muti-tenant Applications for the Cloud, Third Edition on Microsoft Windows Azure Building Hybrid Applications in the Cloud on Microsoft Windows Azure Enterprise Library 5.0 Integration Pack for Windows Azure CQRS Journey Pattern & practices – Windows Azure Guidance Microsoft Azure vs Amazon 클라우드 성능 비교하니 2014년 4월 IaaS는 기본, PaaS로 도약. Microsoft Azure! Keynote Microsoft Azure 현황과 방향성 -한국마이크로소프트 김명신 부장 SUMMARY • Windows Phone 8.1 Launch • IaaS features, VM, Storage, Networking • Cortana Digital Assistant • Web, Web Sites • Windows Phone for Business • Mobile Service, Active Directory, Notification Hub, SQL Database • Additional Windows Phone 8.1 features • Roslyn open source • Windows 8.1 update • .NET Foundation • Universal apps for Windows • New Azure Portal • Cross platform apps, WinJS open source • Supporting existing technology investment • Kinect v2 for Windows including desktop, WPF, and embedded • New Nokia Devices(930, 630/635) • Cloud and mobile first development • 9인치 이하 Windows/Windows Phone • Maximizing business opportunities across License 무료 platform Windows Azure renamed to Microsoft Azure HISTORY New BETA preview management portal released Web Sites Virtual Machines for -

Enhancing Exchange Mobile Device Security with the F5 BIG-IP Platform
Enhancing Exchange Mobile Device Security with the F5 BIG-IP Platform By the F5 business development team for the Microsoft Global Alliance Version 1.0 Introduction As the use of mobile devices in the workplace continues to grow, the risk to corporate assets, and the need to mitigate these risks, increases as well. For many organizations, providing remote mobile device access to corporate assets such as Microsoft Exchange is not just a luxury but also a business requirement. Therefore administrators must find ways to balance the requirements of a mobile workforce with the need to secure corporate assets. Fortunately, F5® BIG-IP® Application Delivery Controllers (ADCs) can help. This document provides guidance for utilizing BIG-IP® Access Policy Manager® (APM) and BIG-IP® Application Security Manager™ (ASM) to significantly enhance Exchange 2010 mobile device security. DISCLAIMER AND ASSUMPTIONS While this guidance presents functional and tested solutions for securing mobile devices in an Exchange 2010 environment, it by no means represents the entirety of options available. One of the greatest strengths of the BIG- IP product line (including BIG-IP LTM, APM, ASM, and more) is its flexibility. The primary goal of this technical brief is to not only provide practical guidance but also to illustrate the power and flexibility of BIG-IP products. The reader is assumed to have general administrative knowledge of BIG-IP® Local Traffic Manager™ (LTM) and familiarity with BIG-IP APM and ASM modules. The following BIG-IP products and software were