One Time Pad
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Basic Cryptography
Basic cryptography • How cryptography works... • Symmetric cryptography... • Public key cryptography... • Online Resources... • Printed Resources... I VP R 1 © Copyright 2002-2007 Haim Levkowitz How cryptography works • Plaintext • Ciphertext • Cryptographic algorithm • Key Decryption Key Algorithm Plaintext Ciphertext Encryption I VP R 2 © Copyright 2002-2007 Haim Levkowitz Simple cryptosystem ... ! ABCDEFGHIJKLMNOPQRSTUVWXYZ ! DEFGHIJKLMNOPQRSTUVWXYZABC • Caesar Cipher • Simple substitution cipher • ROT-13 • rotate by half the alphabet • A => N B => O I VP R 3 © Copyright 2002-2007 Haim Levkowitz Keys cryptosystems … • keys and keyspace ... • secret-key and public-key ... • key management ... • strength of key systems ... I VP R 4 © Copyright 2002-2007 Haim Levkowitz Keys and keyspace … • ROT: key is N • Brute force: 25 values of N • IDEA (international data encryption algorithm) in PGP: 2128 numeric keys • 1 billion keys / sec ==> >10,781,000,000,000,000,000,000 years I VP R 5 © Copyright 2002-2007 Haim Levkowitz Symmetric cryptography • DES • Triple DES, DESX, GDES, RDES • RC2, RC4, RC5 • IDEA Key • Blowfish Plaintext Encryption Ciphertext Decryption Plaintext Sender Recipient I VP R 6 © Copyright 2002-2007 Haim Levkowitz DES • Data Encryption Standard • US NIST (‘70s) • 56-bit key • Good then • Not enough now (cracked June 1997) • Discrete blocks of 64 bits • Often w/ CBC (cipherblock chaining) • Each blocks encr. depends on contents of previous => detect missing block I VP R 7 © Copyright 2002-2007 Haim Levkowitz Triple DES, DESX, -

Block Ciphers and the Data Encryption Standard
Lecture 3: Block Ciphers and the Data Encryption Standard Lecture Notes on “Computer and Network Security” by Avi Kak ([email protected]) January 26, 2021 3:43pm ©2021 Avinash Kak, Purdue University Goals: To introduce the notion of a block cipher in the modern context. To talk about the infeasibility of ideal block ciphers To introduce the notion of the Feistel Cipher Structure To go over DES, the Data Encryption Standard To illustrate important DES steps with Python and Perl code CONTENTS Section Title Page 3.1 Ideal Block Cipher 3 3.1.1 Size of the Encryption Key for the Ideal Block Cipher 6 3.2 The Feistel Structure for Block Ciphers 7 3.2.1 Mathematical Description of Each Round in the 10 Feistel Structure 3.2.2 Decryption in Ciphers Based on the Feistel Structure 12 3.3 DES: The Data Encryption Standard 16 3.3.1 One Round of Processing in DES 18 3.3.2 The S-Box for the Substitution Step in Each Round 22 3.3.3 The Substitution Tables 26 3.3.4 The P-Box Permutation in the Feistel Function 33 3.3.5 The DES Key Schedule: Generating the Round Keys 35 3.3.6 Initial Permutation of the Encryption Key 38 3.3.7 Contraction-Permutation that Generates the 48-Bit 42 Round Key from the 56-Bit Key 3.4 What Makes DES a Strong Cipher (to the 46 Extent It is a Strong Cipher) 3.5 Homework Problems 48 2 Computer and Network Security by Avi Kak Lecture 3 Back to TOC 3.1 IDEAL BLOCK CIPHER In a modern block cipher (but still using a classical encryption method), we replace a block of N bits from the plaintext with a block of N bits from the ciphertext. -

1 Perfect Secrecy of the One-Time Pad
1 Perfect secrecy of the one-time pad In this section, we make more a more precise analysis of the security of the one-time pad. First, we need to define conditional probability. Let’s consider an example. We know that if it rains Saturday, then there is a reasonable chance that it will rain on Sunday. To make this more precise, we want to compute the probability that it rains on Sunday, given that it rains on Saturday. So we restrict our attention to only those situations where it rains on Saturday and count how often this happens over several years. Then we count how often it rains on both Saturday and Sunday. The ratio gives an estimate of the desired probability. If we call A the event that it rains on Saturday and B the event that it rains on Sunday, then the intersection A ∩ B is when it rains on both days. The conditional probability of A given B is defined to be P (A ∩ B) P (B | A)= , P (A) where P (A) denotes the probability of the event A. This formula can be used to define the conditional probability of one event given another for any two events A and B that have probabilities (we implicitly assume throughout this discussion that any probability that occurs in a denominator has nonzero probability). Events A and B are independent if P (A ∩ B)= P (A) P (B). For example, if Alice flips a fair coin, let A be the event that the coin ends up Heads. If Bob rolls a fair six-sided die, let B be the event that he rolls a 3. -

Related-Key Cryptanalysis of 3-WAY, Biham-DES,CAST, DES-X, Newdes, RC2, and TEA
Related-Key Cryptanalysis of 3-WAY, Biham-DES,CAST, DES-X, NewDES, RC2, and TEA John Kelsey Bruce Schneier David Wagner Counterpane Systems U.C. Berkeley kelsey,schneier @counterpane.com [email protected] f g Abstract. We present new related-key attacks on the block ciphers 3- WAY, Biham-DES, CAST, DES-X, NewDES, RC2, and TEA. Differen- tial related-key attacks allow both keys and plaintexts to be chosen with specific differences [KSW96]. Our attacks build on the original work, showing how to adapt the general attack to deal with the difficulties of the individual algorithms. We also give specific design principles to protect against these attacks. 1 Introduction Related-key cryptanalysis assumes that the attacker learns the encryption of certain plaintexts not only under the original (unknown) key K, but also under some derived keys K0 = f(K). In a chosen-related-key attack, the attacker specifies how the key is to be changed; known-related-key attacks are those where the key difference is known, but cannot be chosen by the attacker. We emphasize that the attacker knows or chooses the relationship between keys, not the actual key values. These techniques have been developed in [Knu93b, Bih94, KSW96]. Related-key cryptanalysis is a practical attack on key-exchange protocols that do not guarantee key-integrity|an attacker may be able to flip bits in the key without knowing the key|and key-update protocols that update keys using a known function: e.g., K, K + 1, K + 2, etc. Related-key attacks were also used against rotor machines: operators sometimes set rotors incorrectly. -

Simple Substitution and Caesar Ciphers
Spring 2015 Chris Christensen MAT/CSC 483 Simple Substitution Ciphers The art of writing secret messages – intelligible to those who are in possession of the key and unintelligible to all others – has been studied for centuries. The usefulness of such messages, especially in time of war, is obvious; on the other hand, their solution may be a matter of great importance to those from whom the key is concealed. But the romance connected with the subject, the not uncommon desire to discover a secret, and the implied challenge to the ingenuity of all from who it is hidden have attracted to the subject the attention of many to whom its utility is a matter of indifference. Abraham Sinkov In Mathematical Recreations & Essays By W.W. Rouse Ball and H.S.M. Coxeter, c. 1938 We begin our study of cryptology from the romantic point of view – the point of view of someone who has the “not uncommon desire to discover a secret” and someone who takes up the “implied challenged to the ingenuity” that is tossed down by secret writing. We begin with one of the most common classical ciphers: simple substitution. A simple substitution cipher is a method of concealment that replaces each letter of a plaintext message with another letter. Here is the key to a simple substitution cipher: Plaintext letters: abcdefghijklmnopqrstuvwxyz Ciphertext letters: EKMFLGDQVZNTOWYHXUSPAIBRCJ The key gives the correspondence between a plaintext letter and its replacement ciphertext letter. (It is traditional to use small letters for plaintext and capital letters, or small capital letters, for ciphertext. We will not use small capital letters for ciphertext so that plaintext and ciphertext letters will line up vertically.) Using this key, every plaintext letter a would be replaced by ciphertext E, every plaintext letter e by L, etc. -

Cryptanalysis of Mono-Alphabetic Substitution Ciphers Using Genetic Algorithms and Simulated Annealing Shalini Jain Marathwada Institute of Technology, Dr
Vol. 08 No. 01 2018 p-ISSN 2202-2821 e-ISSN 1839-6518 (Australian ISSN Agency) 82800801201801 Cryptanalysis of Mono-Alphabetic Substitution Ciphers using Genetic Algorithms and Simulated Annealing Shalini Jain Marathwada Institute of Technology, Dr. Babasaheb Ambedkar Marathwada University, India Nalin Chhibber University of Waterloo, Ontario, Canada Sweta Kandi Marathwada Institute of Technology, Dr. Babasaheb Ambedkar Marathwada University, India ABSTRACT – In this paper, we intend to apply the principles of genetic algorithms along with simulated annealing to cryptanalyze a mono-alphabetic substitution cipher. The type of attack used for cryptanalysis is a ciphertext-only attack in which we don’t know any plaintext. In genetic algorithms and simulated annealing, for ciphertext-only attack, we need to have the solution space or any method to match the decrypted text to the language text. However, the challenge is to implement the project while maintaining computational efficiency and a high degree of security. We carry out three attacks, the first of which uses genetic algorithms alone, the second which uses simulated annealing alone and the third which uses a combination of genetic algorithms and simulated annealing. Key words: Cryptanalysis, mono-alphabetic substitution cipher, genetic algorithms, simulated annealing, fitness I. Introduction II. Mono-alphabetic substitution cipher Cryptanalysis involves the dissection of computer systems by A mono-alphabetic substitution cipher is a class of substitution unauthorized persons in order to gain knowledge about the ciphers in which the same letters of the plaintext are replaced unknown aspects of the system. It can be used to gain control by the same letters of the ciphertext. -

Chapter 2 the Data Encryption Standard (DES)
Chapter 2 The Data Encryption Standard (DES) As mentioned earlier there are two main types of cryptography in use today - symmet- ric or secret key cryptography and asymmetric or public key cryptography. Symmet- ric key cryptography is the oldest type whereas asymmetric cryptography is only being used publicly since the late 1970’s1. Asymmetric cryptography was a major milestone in the search for a perfect encryption scheme. Secret key cryptography goes back to at least Egyptian times and is of concern here. It involves the use of only one key which is used for both encryption and decryption (hence the use of the term symmetric). Figure 2.1 depicts this idea. It is necessary for security purposes that the secret key never be revealed. Secret Key (K) Secret Key (K) ? ? - - - - Plaintext (P ) E{P,K} Ciphertext (C) D{C,K} Plaintext (P ) Figure 2.1: Secret key encryption. To accomplish encryption, most secret key algorithms use two main techniques known as substitution and permutation. Substitution is simply a mapping of one value to another whereas permutation is a reordering of the bit positions for each of the inputs. These techniques are used a number of times in iterations called rounds. Generally, the more rounds there are, the more secure the algorithm. A non-linearity is also introduced into the encryption so that decryption will be computationally infeasible2 without the secret key. This is achieved with the use of S-boxes which are basically non-linear substitution tables where either the output is smaller than the input or vice versa. 1It is claimed by some that government agencies knew about asymmetric cryptography before this. -

Recommendation for Block Cipher Modes of Operation Methods
NIST Special Publication 800-38A Recommendation for Block 2001 Edition Cipher Modes of Operation Methods and Techniques Morris Dworkin C O M P U T E R S E C U R I T Y ii C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 December 2001 U.S. Department of Commerce Donald L. Evans, Secretary Technology Administration Phillip J. Bond, Under Secretary of Commerce for Technology National Institute of Standards and Technology Arden L. Bement, Jr., Director iii Reports on Information Security Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the Nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analyses to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security, and its collaborative activities with industry, government, and academic organizations. Certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. Such identification is not intended to imply recommendation or endorsement by the National Institute of Standards and Technology, nor is it intended to imply that the entities, materials, or equipment are necessarily the best available for the purpose. -

Polish Mathematicians Finding Patterns in Enigma Messages
Fall 2006 Chris Christensen MAT/CSC 483 Machine Ciphers Polyalphabetic ciphers are good ways to destroy the usefulness of frequency analysis. Implementation can be a problem, however. The key to a polyalphabetic cipher specifies the order of the ciphers that will be used during encryption. Ideally there would be as many ciphers as there are letters in the plaintext message and the ordering of the ciphers would be random – an one-time pad. More commonly, some rotation among a small number of ciphers is prescribed. But, rotating among a small number of ciphers leads to a period, which a cryptanalyst can exploit. Rotating among a “large” number of ciphers might work, but that is hard to do by hand – there is a high probability of encryption errors. Maybe, a machine. During World War II, all the Allied and Axis countries used machine ciphers. The United States had SIGABA, Britain had TypeX, Japan had “Purple,” and Germany (and Italy) had Enigma. SIGABA http://en.wikipedia.org/wiki/SIGABA 1 A TypeX machine at Bletchley Park. 2 From the 1920s until the 1970s, cryptology was dominated by machine ciphers. What the machine ciphers typically did was provide a mechanical way to rotate among a large number of ciphers. The rotation was not random, but the large number of ciphers that were available could prevent depth from occurring within messages and (if the machines were used properly) among messages. We will examine Enigma, which was broken by Polish mathematicians in the 1930s and by the British during World War II. The Japanese Purple machine, which was used to transmit diplomatic messages, was broken by William Friedman’s cryptanalysts. -

Index-Of-Coincidence.Pdf
The Index of Coincidence William F. Friedman in the 1930s developed the index of coincidence. For a given text X, where X is the sequence of letters x1x2…xn, the index of coincidence IC(X) is defined to be the probability that two randomly selected letters in the ciphertext represent, the same plaintext symbol. For a given ciphertext of length n, let n0, n1, …, n25 be the respective letter counts of A, B, C, . , Z in the ciphertext. Then, the index of coincidence can be computed as 25 ni (ni −1) IC = ∑ i=0 n(n −1) We can also calculate this index for any language source. For some source of letters, let p be the probability of occurrence of the letter a, p be the probability of occurrence of a € b the letter b, and so on. Then the index of coincidence for this source is 25 2 Isource = pa pa + pb pb +…+ pz pz = ∑ pi i=0 We can interpret the index of coincidence as the probability of randomly selecting two identical letters from the source. To see why the index of coincidence gives us useful information, first€ note that the empirical probability of randomly selecting two identical letters from a large English plaintext is approximately 0.065. This implies that an (English) ciphertext having an index of coincidence I of approximately 0.065 is probably associated with a mono-alphabetic substitution cipher, since this statistic will not change if the letters are simply relabeled (which is the effect of encrypting with a simple substitution). The longer and more random a Vigenere cipher keyword is, the more evenly the letters are distributed throughout the ciphertext. -

Secure Communications One Time Pad Cipher
Cipher Machines & Cryptology © 2010 – D. Rijmenants http://users.telenet.be/d.rijmenants THE COMPLETE GUIDE TO SECURE COMMUNICATIONS WITH THE ONE TIME PAD CIPHER DIRK RIJMENANTS Abstract : This paper provides standard instructions on how to protect short text messages with one-time pad encryption. The encryption is performed with nothing more than a pencil and paper, but provides absolute message security. If properly applied, it is mathematically impossible for any eavesdropper to decrypt or break the message without the proper key. Keywords : cryptography, one-time pad, encryption, message security, conversion table, steganography, codebook, message verification code, covert communications, Jargon code, Morse cut numbers. version 012-2011 1 Contents Section Page I. Introduction 2 II. The One-time Pad 3 III. Message Preparation 4 IV. Encryption 5 V. Decryption 6 VI. The Optional Codebook 7 VII. Security Rules and Advice 8 VIII. Appendices 17 I. Introduction One-time pad encryption is a basic yet solid method to protect short text messages. This paper explains how to use one-time pads, how to set up secure one-time pad communications and how to deal with its various security issues. It is easy to learn to work with one-time pads, the system is transparent, and you do not need special equipment or any knowledge about cryptographic techniques or math. If properly used, the system provides truly unbreakable encryption and it will be impossible for any eavesdropper to decrypt or break one-time pad encrypted message by any type of cryptanalytic attack without the proper key, even with infinite computational power (see section VII.b) However, to ensure the security of the message, it is of paramount importance to carefully read and strictly follow the security rules and advice (see section VII). -
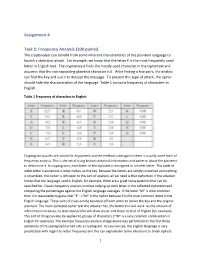
Assignment 4 Task 1: Frequency Analysis (100 Points)
Assignment 4 Task 1: Frequency Analysis (100 points) The cryptanalyst can benefit from some inherent characteristics of the plaintext language to launch a statistical attack. For example, we know that the letter E is the most frequently used letter in English text. The cryptanalyst finds the mostly-used character in the ciphertext and assumes that the corresponding plaintext character is E. After finding a few pairs, the analyst can find the key and use it to decrypt the message. To prevent this type of attack, the cipher should hide the characteristics of the language. Table 1 contains frequency of characters in English. Table 1 Frequency of characters in English Cryptogram puzzles are solved for enjoyment and the method used against them is usually some form of frequency analysis. This is the act of using known statistical information and patterns about the plaintext to determine it. In cryptograms, each letter of the alphabet is encrypted to another letter. This table of letter-letter translations is what makes up the key. Because the letters are simply converted and nothing is scrambled, the cipher is left open to this sort of analysis; all we need is that ciphertext. If the attacker knows that the language used is English, for example, there are a great many patterns that can be searched for. Classic frequency analysis involves tallying up each letter in the collected ciphertext and comparing the percentages against the English language averages. If the letter "M" is most common then it is reasonable to guess that "E"-->"M" in the cipher because E is the most common letter in the English language.