Relations Among Notions of Security for Public-Key Encryption Schemes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mihir Bellare Curriculum Vitae Contents
Mihir Bellare Curriculum vitae August 2018 Department of Computer Science & Engineering, Mail Code 0404 University of California at San Diego 9500 Gilman Drive, La Jolla, CA 92093-0404, USA. Phone: (858) 534-4544 ; E-mail: [email protected] Web Page: http://cseweb.ucsd.edu/~mihir Contents 1 Research areas 2 2 Education 2 3 Distinctions and Awards 2 4 Impact 3 5 Grants 4 6 Professional Activities 5 7 Industrial relations 5 8 Work Experience 5 9 Teaching 6 10 Publications 6 11 Mentoring 19 12 Personal Information 21 2 1 Research areas ∗ Cryptography and security: Provable security; authentication; key distribution; signatures; encryp- tion; protocols. ∗ Complexity theory: Interactive and probabilistically checkable proofs; approximability ; complexity of zero-knowledge; randomness in protocols and algorithms; computational learning theory. 2 Education ∗ Massachusetts Institute of Technology. Ph.D in Computer Science, September 1991. Thesis title: Randomness in Interactive Proofs. Thesis supervisor: Prof. S. Micali. ∗ Massachusetts Institute of Technology. Masters in Computer Science, September 1988. Thesis title: A Signature Scheme Based on Trapdoor Permutations. Thesis supervisor: Prof. S. Micali. ∗ California Institute of Technology. B.S. with honors, June 1986. Subject: Mathematics. GPA 4.0. Class rank 4 out of 227. Summer Undergraduate Research Fellow 1984 and 1985. ∗ Ecole Active Bilingue, Paris, France. Baccalauréat Série C, June 1981. 3 Distinctions and Awards ∗ PET (Privacy Enhancing Technologies) Award 2015 for publication [154]. ∗ Fellow of the ACM (Association for Computing Machinery), 2014. ∗ ACM Paris Kanellakis Theory and Practice Award 2009. ∗ RSA Conference Award in Mathematics, 2003. ∗ David and Lucille Packard Foundation Fellowship in Science and Engineering, 1996. (Twenty awarded annually in all of Science and Engineering.) ∗ Test of Time Award, ACM CCS 2011, given for [81] as best paper from ten years prior. -

Design and Analysis of Secure Encryption Schemes
UNIVERSITY OF CALIFORNIA, SAN DIEGO Design and Analysis of Secure Encryption Schemes A dissertation submitted in partial satisfaction of the requirements for the degree Doctor of Philosophy in Computer Science by Michel Ferreira Abdalla Committee in charge: Professor Mihir Bellare, Chairperson Professor Yeshaiahu Fainman Professor Adriano Garsia Professor Mohan Paturi Professor Bennet Yee 2001 Copyright Michel Ferreira Abdalla, 2001 All rights reserved. The dissertation of Michel Ferreira Abdalla is approved, and it is acceptable in quality and form for publication on micro¯lm: Chair University of California, San Diego 2001 iii DEDICATION To my father (in memorian) iv TABLE OF CONTENTS Signature Page . iii Dedication . iv Table of Contents . v List of Figures . vii List of Tables . ix Acknowledgements . x Vita and Publications . xii Fields of Study . xiii Abstract . xiv I Introduction . 1 A. Encryption . 1 1. Background . 2 2. Perfect Privacy . 3 3. Modern cryptography . 4 4. Public-key Encryption . 5 5. Broadcast Encryption . 5 6. Provable Security . 6 7. Concrete Security . 7 B. Contributions . 8 II E±cient public-key encryption schemes . 11 A. Introduction . 12 B. De¯nitions . 17 1. Represented groups . 17 2. Message Authentication Codes . 17 3. Symmetric Encryption . 19 4. Asymmetric Encryption . 21 C. The Scheme DHIES . 23 D. Attributes and Advantages of DHIES . 24 1. Encrypting with Di±e-Hellman: The ElGamal Scheme . 25 2. De¯ciencies of ElGamal Encryption . 26 3. Overcoming De¯ciencies in ElGamal Encryption: DHIES . 29 E. Di±e-Hellman Assumptions . 31 F. Security against Chosen-Plaintext Attack . 38 v G. Security against Chosen-Ciphertext Attack . 41 H. ODH and SDH . -

Improved Related-Key Attacks on DESX and DESX+
Improved Related-key Attacks on DESX and DESX+ Raphael C.-W. Phan1 and Adi Shamir3 1 Laboratoire de s´ecurit´eet de cryptographie (LASEC), Ecole Polytechnique F´ed´erale de Lausanne (EPFL), CH-1015 Lausanne, Switzerland [email protected] 2 Faculty of Mathematics & Computer Science, The Weizmann Institute of Science, Rehovot 76100, Israel [email protected] Abstract. In this paper, we present improved related-key attacks on the original DESX, and DESX+, a variant of the DESX with its pre- and post-whitening XOR operations replaced with addition modulo 264. Compared to previous results, our attack on DESX has reduced text complexity, while our best attack on DESX+ eliminates the memory requirements at the same processing complexity. Keywords: DESX, DESX+, related-key attack, fault attack. 1 Introduction Due to the DES’ small key length of 56 bits, variants of the DES under multiple encryption have been considered, including double-DES under one or two 56-bit key(s), and triple-DES under two or three 56-bit keys. Another popular variant based on the DES is the DESX [15], where the basic keylength of single DES is extended to 120 bits by wrapping this DES with two outer pre- and post-whitening keys of 64 bits each. Also, the endorsement of single DES had been officially withdrawn by NIST in the summer of 2004 [19], due to its insecurity against exhaustive search. Future use of single DES is recommended only as a component of the triple-DES. This makes it more important to study the security of variants of single DES which increase the key length to avoid this attack. -

Models and Algorithms for Physical Cryptanalysis
MODELS AND ALGORITHMS FOR PHYSICAL CRYPTANALYSIS Dissertation zur Erlangung des Grades eines Doktor-Ingenieurs der Fakult¨at fur¨ Elektrotechnik und Informationstechnik an der Ruhr-Universit¨at Bochum von Kerstin Lemke-Rust Bochum, Januar 2007 ii Thesis Advisor: Prof. Dr.-Ing. Christof Paar, Ruhr University Bochum, Germany External Referee: Prof. Dr. David Naccache, Ecole´ Normale Sup´erieure, Paris, France Author contact information: [email protected] iii Abstract This thesis is dedicated to models and algorithms for the use in physical cryptanalysis which is a new evolving discipline in implementation se- curity of information systems. It is based on physically observable and manipulable properties of a cryptographic implementation. Physical observables, such as the power consumption or electromag- netic emanation of a cryptographic device are so-called `side channels'. They contain exploitable information about internal states of an imple- mentation at runtime. Physical effects can also be used for the injec- tion of faults. Fault injection is successful if it recovers internal states by examining the effects of an erroneous state propagating through the computation. This thesis provides a unified framework for side channel and fault cryptanalysis. Its objective is to improve the understanding of physi- cally enabled cryptanalysis and to provide new models and algorithms. A major motivation for this work is that methodical improvements for physical cryptanalysis can also help in developing efficient countermea- sures for securing cryptographic implementations. This work examines differential side channel analysis of boolean and arithmetic operations which are typical primitives in cryptographic algo- rithms. Different characteristics of these operations can support a side channel analysis, even of unknown ciphers. -

Compact E-Cash and Simulatable Vrfs Revisited
Compact E-Cash and Simulatable VRFs Revisited Mira Belenkiy1, Melissa Chase2, Markulf Kohlweiss3, and Anna Lysyanskaya4 1 Microsoft, [email protected] 2 Microsoft Research, [email protected] 3 KU Leuven, ESAT-COSIC / IBBT, [email protected] 4 Brown University, [email protected] Abstract. Efficient non-interactive zero-knowledge proofs are a powerful tool for solving many cryptographic problems. We apply the recent Groth-Sahai (GS) proof system for pairing product equations (Eurocrypt 2008) to two related cryptographic problems: compact e-cash (Eurocrypt 2005) and simulatable verifiable random functions (CRYPTO 2007). We present the first efficient compact e-cash scheme that does not rely on a ran- dom oracle. To this end we construct efficient GS proofs for signature possession, pseudo randomness and set membership. The GS proofs for pseudorandom functions give rise to a much cleaner and substantially faster construction of simulatable verifiable random functions (sVRF) under a weaker number theoretic assumption. We obtain the first efficient fully simulatable sVRF with a polynomial sized output domain (in the security parameter). 1 Introduction Since their invention [BFM88] non-interactive zero-knowledge proofs played an important role in ob- taining feasibility results for many interesting cryptographic primitives [BG90,GO92,Sah99], such as the first chosen ciphertext secure public key encryption scheme [BFM88,RS92,DDN91]. The inefficiency of these constructions often motivated independent practical instantiations that were arguably conceptually less elegant, but much more efficient ([CS98] for chosen ciphertext security). We revisit two important cryptographic results of pairing-based cryptography, compact e-cash [CHL05] and simulatable verifiable random functions [CL07], that have very elegant constructions based on non-interactive zero-knowledge proof systems, but less elegant practical instantiations. -

Transferable Constant-Size Fair E-Cash
Transferable Constant-Size Fair E-Cash Georg Fuchsbauer, David Pointcheval, and Damien Vergnaud Ecole´ normale sup´erieure,LIENS - CNRS - INRIA, Paris, France http://www.di.ens.fr/f~fuchsbau,~pointche,~vergnaudg Abstract. We propose an efficient blind certification protocol with interesting properties. It falls in the Groth-Sahai framework for witness-indistinguishable proofs, thus extended to a certified signature it immediately yields non-frameable group signatures. We use blind certification to build an efficient (offline) e-cash system that guarantees user anonymity and transferability of coins without increasing their size. As required for fair e-cash, in case of fraud, anonymity can be revoked by an authority, which is also crucial to deter from double spending. 1 Introduction 1.1 Motivation The issue of anonymity in electronic transactions was introduced for e-cash and e-mail in the early 1980's by Chaum, with the famous primitive of blind signatures [Cha83,Cha84]: a signer accepts to sign a message, without knowing the message itself, and without being able to later link a message- signature pair to the transaction it originated from. In e-cash systems, the message is a serial number to make a coin unique. The main security property is resistance to \one-more forgeries" [PS00], which guarantees the signer that after t transactions a user cannot have more than t valid signatures. Blind signatures have thereafter been widely used for many variants of e-cash systems; in particular fair blind signatures [SPC95], which allow to provide revocable anonymity. They deter from abuse since in such a case the signer can ask an authority to reveal the identity of the defrauder. -

On the Related-Key Attacks Against Aes*
THE PUBLISHING HOUSE PROCEEDINGS OF THE ROMANIAN ACADEMY, Series A, OF THE ROMANIAN ACADEMY Volume 13, Number 4/2012, pp. 395–400 ON THE RELATED-KEY ATTACKS AGAINST AES* Joan DAEMEN1, Vincent RIJMEN2 1 STMicroElectronics, Belgium 2 KU Leuven & IBBT (Belgium), Graz University of Technology, Austria E-mail: [email protected] Alex Biryukov and Dmitry Khovratovich presented related-key attacks on AES and reduced-round versions of AES. The most impressive of these were presented at Asiacrypt 2009: related-key attacks against the full AES-256 and AES-192. We discuss the applicability of these attacks and related-key attacks in general. We model the access of the attacker to the key in the form of key access schemes. Related-key attacks should only be considered with respect to sound key access schemes. We show that defining a sound key access scheme in which the related-key attacks against AES-256 and AES- 192 can be conducted, is possible, but contrived. Key words: Advanced Encryption Standard, AES, security, related-key attacks. 1. INTRODUCTION Since the start of the process to select the Advanced Encryption Standard (AES), the block cipher Rijndael, which later became the AES, has been scrutinized extensively for security weaknesses. The initial cryptanalytic results can be grouped into three categories. The first category contains attacks variants that were weakened by reducing the number of rounds [0]. The second category contains observations on mathematical properties of sub-components of the AES, which don’t lead to a cryptanalytic attack [0]. The third category consists of side-channel attacks, which target deficiencies in hardware or software implementations [0]. -
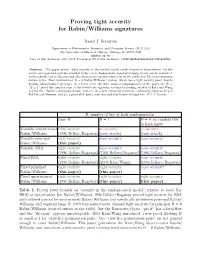
Proving Tight Security for Rabin/Williams Signatures
Proving tight security for Rabin/Williams signatures Daniel J. Bernstein Department of Mathematics, Statistics, and Computer Science (M/C 249) The University of Illinois at Chicago, Chicago, IL 60607–7045 [email protected] Date of this document: 2007.10.07. Permanent ID of this document: c30057d690a8fb42af6a5172b5da9006. Abstract. This paper proves “tight security in the random-oracle model relative to factorization” for the lowest-cost signature systems available today: every hash-generic signature-forging attack can be converted, with negligible loss of efficiency and effectiveness, into an algorithm to factor the public key. The most surprising system is the “fixed unstructured B = 0 Rabin/Williams” system, which has a tight security proof despite hashing unrandomized messages. At a lower level, the three main accomplishments of the paper are (1) a “B ≥ 1” proof that handles some of the lowest-cost signature systems by pushing an idea of Katz and Wang beyond the “claw-free permutation pair” context; (2) a new expository structure, elaborating upon an idea of Koblitz and Menezes; and (3) a proof that uses a new idea and that breaks through the “B ≥ 1” barrier. B, number of bits of hash randomization large B B = 1 B = 0: no random bits in hash input Variable unstructured tight security no security no security Rabin/Williams (1996 Bellare/Rogaway) (easy attack) (easy attack) Variable principal tight security loose security loose security∗ Rabin/Williams (this paper) Variable RSA tight security loose security loose security (1996 Bellare/Rogaway) (1993 Bellare/Rogaway) (1993 Bellare/Rogaway) Fixed RSA tight security tight security loose security (1996 Bellare/Rogaway) (2003 Katz/Wang) (1993 Bellare/Rogaway) Fixed principal tight security tight security loose security∗ Rabin/Williams (this paper) (this paper) Fixed unstructured tight security tight security tight security Rabin/Williams (1996 Bellare/Rogaway) (this paper) (this paper) Table 1. -

A Practical Attack on the Fixed RC4 in the WEP Mode
A Practical Attack on the Fixed RC4 in the WEP Mode Itsik Mantin NDS Technologies, Israel [email protected] Abstract. In this paper we revisit a known but ignored weakness of the RC4 keystream generator, where secret state info leaks to the gen- erated keystream, and show that this leakage, also known as Jenkins’ correlation or the RC4 glimpse, can be used to attack RC4 in several modes. Our main result is a practical key recovery attack on RC4 when an IV modifier is concatenated to the beginning of a secret root key to generate a session key. As opposed to the WEP attack from [FMS01] the new attack is applicable even in the case where the first 256 bytes of the keystream are thrown and its complexity grows only linearly with the length of the key. In an exemplifying parameter setting the attack recov- ersa16-bytekeyin248 steps using 217 short keystreams generated from different chosen IVs. A second attacked mode is when the IV succeeds the secret root key. We mount a key recovery attack that recovers the secret root key by analyzing a single word from 222 keystreams generated from different IVs, improving the attack from [FMS01] on this mode. A third result is an attack on RC4 that is applicable when the attacker can inject faults to the execution of RC4. The attacker derives the internal state and the secret key by analyzing 214 faulted keystreams generated from this key. Keywords: RC4, Stream ciphers, Cryptanalysis, Fault analysis, Side- channel attacks, Related IV attacks, Related key attacks. 1 Introduction RC4 is the most widely used stream cipher in software applications. -

Implementation of Secure Image Transferring by Using Rsa and Sha-1
© IJCIRAS | ISSN (O) - 2581-5334 April 2020 | Vol. 2 Issue. 11 IMPLEMENTATION OF SECURE IMAGE TRANSFERRING BY USING RSA AND SHA-1 Khet Khet Khaing Oo1, Yan Naung Soe2 Faculty of Computer System and Technologies, University of Computer Studies, Myitkyina and 1011, Myanmar encryption. A public key which encrypted data only be Abstract decrypted key but it requires a private key which is Nowadays, security is an important thing that needs associated together. It must be careful that the to transfer data from admin to user safely. encrypted public key and decrypted public key must not Communication security requires the integration of be the same. people, process, and technology. There are so many different techniques should be used to safe 2.PUBLIC KEY CRYPTOSYSTEM confidential image data from unauthorized access. Information security is becoming more in data RSA cryptosystem was invented by Ron Rivest, Adi storage and transmission from data exchange in Shamir, and Leonard Adleman at MIT in 1978. [4,6] RSA electronic way. Industrial process is used to images, (Rivest–Shamir–Adleman) algorithm is a public-key this is useful to protect the secure image data files cryptography system. These algorithm is profoundly from unauthorized access. To implement this system used in electronic commerce protocols, and is confided RSA ( Rivest Shamir Adelman) public key to be secure given enough long keys and the use of up- cryptography with OAEP (Optimal Asymmetric to-date implementations. They went on to patent the Encryption Padding ) and SHA-1 hash algorithms are system and to form a company of the same name— used. -

Design Principles and Patterns for Computer Systems That Are
Bibliography [AB04] Tom Anderson and David Brady. Principle of least astonishment. Ore- gon Pattern Repository, November 15 2004. http://c2.com/cgi/wiki? PrincipleOfLeastAstonishment. [Acc05] Access Data. Forensic toolkit—overview, 2005. http://www.accessdata. com/Product04_Overview.htm?ProductNum=04. [Adv87] Display ad 57, February 8 1987. [Age05] US Environmental Protection Agency. Wastes: The hazardous waste mani- fest system, 2005. http://www.epa.gov/epaoswer/hazwaste/gener/ manifest/. [AHR05a] Ben Adida, Susan Hohenberger, and Ronald L. Rivest. Fighting Phishing Attacks: A Lightweight Trust Architecture for Detecting Spoofed Emails (to appear), 2005. Available at http://theory.lcs.mit.edu/⇠rivest/ publications.html. [AHR05b] Ben Adida, Susan Hohenberger, and Ronald L. Rivest. Separable Identity- Based Ring Signatures: Theoretical Foundations For Fighting Phishing Attacks (to appear), 2005. Available at http://theory.lcs.mit.edu/⇠rivest/ publications.html. [AIS77] Christopher Alexander, Sara Ishikawa, and Murray Silverstein. A Pattern Lan- guage: towns, buildings, construction. Oxford University Press, 1977. (with Max Jacobson, Ingrid Fiksdahl-King and Shlomo Angel). [AKM+93] H. Alvestrand, S. Kille, R. Miles, M. Rose, and S. Thompson. RFC 1495: Map- ping between X.400 and RFC-822 message bodies, August 1993. Obsoleted by RFC2156 [Kil98]. Obsoletes RFC987, RFC1026, RFC1138, RFC1148, RFC1327 [Kil86, Kil87, Kil89, Kil90, HK92]. Status: PROPOSED STANDARD. [Ale79] Christopher Alexander. The Timeless Way of Building. Oxford University Press, 1979. 429 430 BIBLIOGRAPHY [Ale96] Christopher Alexander. Patterns in architecture [videorecording], October 8 1996. Recorded at OOPSLA 1996, San Jose, California. [Alt00] Steven Alter. Same words, different meanings: are basic IS/IT concepts our self-imposed Tower of Babel? Commun. AIS, 3(3es):2, 2000. -

Deep Learning-Based Cryptanalysis of Lightweight Block Ciphers
Hindawi Security and Communication Networks Volume 2020, Article ID 3701067, 11 pages https://doi.org/10.1155/2020/3701067 Research Article Deep Learning-Based Cryptanalysis of Lightweight Block Ciphers Jaewoo So Department of Electronic Engineering, Sogang University, Seoul 04107, Republic of Korea Correspondence should be addressed to Jaewoo So; [email protected] Received 5 February 2020; Revised 21 June 2020; Accepted 26 June 2020; Published 13 July 2020 Academic Editor: Umar M. Khokhar Copyright © 2020 Jaewoo So. +is is an open access article distributed under the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. Most of the traditional cryptanalytic technologies often require a great amount of time, known plaintexts, and memory. +is paper proposes a generic cryptanalysis model based on deep learning (DL), where the model tries to find the key of block ciphers from known plaintext-ciphertext pairs. We show the feasibility of the DL-based cryptanalysis by attacking on lightweight block ciphers such as simplified DES, Simon, and Speck. +e results show that the DL-based cryptanalysis can successfully recover the key bits when the keyspace is restricted to 64 ASCII characters. +e traditional cryptanalysis is generally performed without the keyspace restriction, but only reduced-round variants of Simon and Speck are successfully attacked. Although a text-based key is applied, the proposed DL-based cryptanalysis can successfully break the full rounds of Simon32/64 and Speck32/64. +e results indicate that the DL technology can be a useful tool for the cryptanalysis of block ciphers when the keyspace is restricted.