Attacking the Antivirus
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
LZ Based Compression Benchmark on PE Files Introduction LZ Based
LZ based compression benchmark on PE files Zsombor Paróczi Abstract: The key element in runtime compression is the compression algorithm, that is used during processing. It has to be small in enough in decompression bytecode size to fit in the final executable, yet have to provide the best compression ratio. In our work we benchmark the top LZ based compression methods on Windows PE files (both exe and dll files), and present the results including the decompres- sion overhead and the compression rates. Keywords: lz based compression, compression benchmark, PE benchmark Introduction During runtime executable compression an already compiled executable is modified in ways, that it still retains the ability to execute, yet the transformation produces smaller file size. The transformations usually exists from multiple steps, changing the structure of the executable by removing unused bytes, adding a compression layer or modifying the code in itself. During the code modifications the actual bytecode can change, or remain the same depending on the modification itself. In the world of x86 (or even x86-64) PE compression there are only a few benchmarks, since the ever growing storage capacity makes this field less important. Yet in new fields, like IOT and wearable electronics every application uses some kind of compression, Android apk-s are always compressed by a simple gzip compression. There are two mayor benchmarks for PE compression available today, the Maximum Compression benchmark collection [1] includes two PE files, one DLL and one EXE, and the Pe Compression Test [2] has four exe files. We will use the exe files during our benchmark, referred as small corpus. -
How to Disable to Antivirus
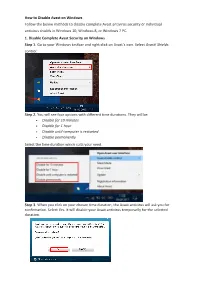
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

DEFINICIÓN Un Antivirus
ANTIVIRUS DEFINICIÓN Un antivirus es un programa de computadora cuyo propósito es combatir y erradicar los virus informáticos. Para que el antivirus sea productivo y efectivo hay que configurarlo cuidadosamente de tal forma que aprovechemos todas las cualidades que ellos poseen. Hay que saber cuales son sus fortalezas y debilidades y tenerlas en cuenta a la hora de enfrentar a los virus. Un antivirus es una solución para minimizar los riesgos y nunca será una solución definitiva, lo principal es mantenerlo actualizado. Para mantener el sistema estable y seguro el antivirus debe estar siempre actualizado, tomando siempre medidas preventivas y correctivas y estar constantemente leyendo sobre los virus y nuevas tecnologías. ¿CÓMO FUNCIONA? Básicamente, un antivirus compara el código de cada archivo con una base de datos de los códigos (también conocidos como firmas o vacunas) de los virus conocidos, por lo que es importante actualizarla periódicamente a fin de evitar que un virus nuevo no sea detectado. También se les ha agregado funciones avanzadas, como la búsqueda de comportamientos típicos de virus (técnica conocida como Heurística) o la verificación contra virus en redes de computadores. Normalmente un antivirus tiene un componente que se carga en memoria y permanece en ella para verificar todos los archivos abiertos, creados, modificados y ejecutados en tiempo real. Es muy común que tengan componentes que revisen los adjuntos de los correos electrónicos salientes y entrantes, así como los scripts y programas que pueden ejecutarse en un navegador web (ActiveX, Java, JavaScript). ALGUNOS ANTIVIRUS 1 CLAM ANTIVIRUS Comodo AntiVirus FProt Antivirus FSecure AntiVirus ZoneAlarm Antivirus ANTIVIRUS HEURISTICOS Los heurísticos analizan el código de cada archivo con métodos genéricos y detectan virus nuevos que todavía no se han incluido en la base de datos de virus del programa antivirus. -

Malware List.Numbers
CLASS A - Tested once a month (and as significant updates and samples are available) (95% or higher detection rate) CLASS B - Tested every two months (and if many new samples or significant updates are available) (95 - 85% detection rate) CLASS C - Tested every three months (85-75% detection rate) CLASS D - Tested every six months (75% or lower detection rates) For Comparison, not an actual Antivirus CLASS F - Excluded from future testing (read notes) Notes, comments, remarks, FAQ and everything else. McAfee Endpoint Protection for Malware Family (by year) # Malware Sample Type MD5 Hash Avast 9.0 Intego VirusBarrier X8 10.8 Norman 3.0.7664 ESET 6.0 Sophos 9 F-Secure 1.0 Kaspersky Security 14 G Data AntiVirus for Mac Dr Web 9.0.0 Avira ClamXav 2.6.4 (web version) Norton 12.6 (26) Comodo Webroot 8 Thirtyseven4 Total Security eScan 5.5-7 iAntivirus 1.1.4 (282) ProtectMac 1.3.2 - 1.4 BitDefender 2.30 - 3.0.6681 McAfee Internet Security for Mac* AVG AntiVirus for Mac Dr Web Light 6.0.6 (201207050) Max Secure Antivirus MacBooster X-Protect Gatekeeper Intego VirusBarrier 2013 10.7 Intego VirusBarrier X6 VirusBarrier Express 1.1.6 (79) Panda Antivirus 1.6 Bitdefender (App Store) 2.21 MacKeeper 2.5.1 - 2.8 (476) Panda Antivirus 10.7.6 Trend Micro Titanium 3.0 McAfee Security 1.2.0 (1549) Norton 11.1.1 (2) Trend Micro Smart Sur. 1.6.1101 McAfee VirusScan for Mac 8.6.1 FortiClient 5.0.6.131 Quick Heal Total Sec 1.0 MacScan 2.9.4 McAfee Virex 7.7 (163) Magician 1.4.3 Vipre 1.0.51 Mac Malware Remover 1.1.6 MD5 Hash Mac 1 Price -> Free $39.99 (Internet -

Q3 Consumer Endpoint Protection Jul-Sep 2020
HOME ANTI- MALWARE PROTECTION JUL - SEP 2020 selabs.uk [email protected] @SELabsUK www.facebook.com/selabsuk blog.selabs.uk SE Labs tested a variety of anti-malware (aka ‘anti-virus’; aka ‘endpoint security’) products from a range of well-known vendors in an effort to judge which were the most effective. Each product was exposed to the same threats, which were a mixture of targeted attacks using well-established techniques and public email and web-based threats that were found to be live on the internet at the time of the test. The results indicate how effectively the products were at detecting and/or protecting against those threats in real time. 2 Home Anti-Malware Protection July - September 2020 MANAGEMENT Chief Executive Officer Simon Edwards CONTENTS Chief Operations Officer Marc Briggs Chief Human Resources Officer Magdalena Jurenko Chief Technical Officer Stefan Dumitrascu Introduction 04 TEstING TEAM Executive Summary 05 Nikki Albesa Zaynab Bawa 1. Total Accuracy Ratings 06 Thomas Bean Solandra Brewster Home Anti-Malware Protection Awards 07 Liam Fisher Gia Gorbold Joseph Pike 2. Threat Responses 08 Dave Togneri Jake Warren 3. Protection Ratings 10 Stephen Withey 4. Protection Scores 12 IT SUPPORT Danny King-Smith 5. Protection Details 13 Chris Short 6. Legitimate Software Ratings 14 PUBLICatION Sara Claridge 6.1 Interaction Ratings 15 Colin Mackleworth 6.2 Prevalence Ratings 16 Website selabs.uk Twitter @SELabsUK 6.3 Accuracy Ratings 16 Email [email protected] Facebook www.facebook.com/selabsuk 6.4 Distribution of Impact Categories 17 Blog blog.selabs.uk Phone +44 (0)203 875 5000 7. -

9 Steps to Protect Against Ransomware
9 Steps to ProtectUsers/Devices Against Ransomware Home Security Dashboard Security Dashboard IT Support Analyst Task Overview Devices Vulnerability Scan With Vulnerabilities In Last 30 Days Security Manager Critical Security Dashboard 40 Devices 95 Not Scanned Self Service Important/High 85 Estimated Not Scanned 90 Devices 31 Scanned So ware Catalog Moderate/Medium 15% Launchpad 90 Devices Asset Manager NA 140 Devices So ware Asset Hardware Asset Inventory Scan Most detected Critical/High Vulnerables In Last 30 Days In Last 30 Days Sign Out MS15-080_MSU 70 Devices 169 Not Scanned 42 Scanned MS15-084_MSU White Paper 70 Devices 20% MS15-049_INTL 50 Devices MS15-049_INTL 50 Devices Contents Introduction . 1 Prevention . .. 2 1. Patch the critical operating systems and applications .................................2 2. Ensure that antivirus software is up-to-date and that regular scans are scheduled .......3 3. Manage the use of privileged accounts ..............................................4 4. Implement access control that focuses on the data ...................................4 5. Define, implement, and enforce software rules .......................................6 6. Disable macros from Microsoft Office files ...........................................6 Other considerations . 6 7. Implement applications whitelisting ................................................7 8. Restrict users to virtualized or containerized environments ............................7 9. Back up critical files frequently .....................................................7 Ransomware incidents are on the rise . Fight back! . 8 References . 8 This document contains the confidential information and/or proprietary property of Ivanti Software, Inc. and its affiliates (referred to collectively as “Ivanti”), and may not be disclosed or copied without prior written consent of Ivanti. Ivanti retains the right to make changes to this document or related product specifications and descriptions, at any time, without notice. -

Trojans and Malware on the Internet an Update
Attitude Adjustment: Trojans and Malware on the Internet An Update Sarah Gordon and David Chess IBM Thomas J. Watson Research Center Yorktown Heights, NY Abstract This paper continues our examination of Trojan horses on the Internet; their prevalence, technical structure and impact. It explores the type and scope of threats encountered on the Internet - throughout history until today. It examines user attitudes and considers ways in which those attitudes can actively affect your organization’s vulnerability to Trojanizations of various types. It discusses the status of hostile active content on the Internet, including threats from Java and ActiveX, and re-examines the impact of these types of threats to Internet users in the real world. Observations related to the role of the antivirus industry in solving the problem are considered. Throughout the paper, technical and policy based strategies for minimizing the risk of damage from various types of Trojan horses on the Internet are presented This paper represents an update and summary of our research from Where There's Smoke There's Mirrors: The Truth About Trojan Horses on the Internet, presented at the Eighth International Virus Bulletin Conference in Munich Germany, October 1998, and Attitude Adjustment: Trojans and Malware on the Internet, presented at the European Institute for Computer Antivirus Research in Aalborg, Denmark, March 1999. Significant portions of those works are included here in original form. Descriptors: fidonet, internet, password stealing trojan, trojanized system, trojanized application, user behavior, java, activex, security policy, trojan horse, computer virus Attitude Adjustment: Trojans and Malware on the Internet Trojans On the Internet… Ever since the city of Troy was sacked by way of the apparently innocuous but ultimately deadly Trojan horse, the term has been used to talk about something that appears to be beneficial, but which hides an attack within. -

Breaking Antivirus Software Joxean Koret, COSEINC 44CON, 2014
Breaking Antivirus Software Joxean Koret, COSEINC 44CON, 2014 Breaking antivirus software Introduction Attacking antivirus engines Finding vulnerabilities Exploiting antivirus engines Antivirus vulnerabilities Conclusions Recommendations Antivirus Engines Common features of AV engines: Written in C/C++. Signatures based engine + heuristics. On-access scanners. Command line/GUI on-demand scanners. Support for compressed file archives. Support for packers. Support for miscellaneous file formats. Advanced common features: Packet filters and firewalls. Drivers to protect the product, anti-rootkits, etc... Anti-exploiting toolkits. Antivirus products or engines An antivirus engine is just the core, the kernel, of an antivirus product. Some antivirus engines are used by multiple products. For example, BitDefender is the most widely used antivirus kernel. It's used by so many products like QiHoo360, G-Data, eScan, F-Secure, etc... Most “big” antivirus companies have their own engine but not all. And some companies, like F-Secure, integrate 3rd party engines in their products. In general, during this talk I will refer to AV engines, to the kernels, except when specified the word “product”. Attack surface Fact: installing an application in your computer makes you a bit more vulnerable. You just increased your attack surface. If the application is local: your local attack surface increased. If the application is remote: your remote attack surface increased. If your application runs with the highest privileges, installs kernel drivers, a packet filter and tries to handle anything your computer may do... Your attack surface dramatically increased. Myths and reality Antivirus propaganda: “We make your computer safer with no performance penalty!” “We protect against unknown zero day attacks!”. -

Cyber Warfare: Surviving an Attack
14 Cyber Warfare: Surviving an Attack By Devabhaktuni Srikrishna Cyberspace is a new domain of warfare. Created to minimize the vulnerability of United States communications networks to a crippling nuclear first strike by the Soviet Union, the Internet that was originally envisioned to enhance U.S. security is turning into a battlefield 1 for nations or sub-national groups to launch virally spreading attacks 2 and induce network failures potentially involving critical infrastructure systems.3 Cyber warfare and cyberoffense 4 have been a part of U.S. military operations for decades.5 Treaties and rules of engagement define what is off-limits during a cyberwar.6 The more vulnerable the system is, the more policy is necessary to deter adversarial nations from launching attacks, and vice-versa. Some cyberattacks are analogous to air forces probing one anotherʼs defenses or perhaps to espionage during the Cold War, which occurred though there was no official war and no physical harm. Cyberespionage largest recent cyberattacks in their book, but due to a gap in theory and practice. operations of China, for example, against the United States and its allies Cyber War: The Next Threat to National Organizations are vulnerable to the extent have been going on for years and will Security and What to Do About It. Once a they want to be and to how much they want never really end.7 virus or malware is inadvertently to spend to address vulnerabilities. 14 And downloaded onto a networked personal cyber vulnerabilities can be completely U.S. Air Force General Kevin Chilton, computer (PC) by a user9, the PC can be eliminated -- unlike conventional, nuclear, former Commander-in-Chief of commandeered to perform cyberattacks chemical, or biological which are permanent Strategic Command, has stated that ranging from electronic banking crimes, vulnerabilities due to laws of nature. -

Study on Computer Trojan Horse Virus and Its Prevention ZHU Zhenfang
International Journal of Engineering and Applied Sciences (IJEAS) ISSN: 2394-3661, Volume-2, Issue-8, August 2015 Study on Computer Trojan Horse Virus and Its Prevention ZHU Zhenfang to steal or viciously revise files, spy system information, steal various commands and passwords, and even format users’ Abstract— In recent years, the fast development of computer hardware. In addition, Trojan horse virus usually records network technology, has become an integral part of human’s life, keyboard operation by means of keyboard record, and then work and study. But with the popularity of the Internet, obtains the account and password of E-bank. Attackers can computer viruses, Trojans and other new terms have become some well-known network vocabularies. Studies have shown directly steal users’ wealth by obtaining accounts and that most users of computer are more or less suffered from passwords. On the other hand, Trojan horse can also cause the computer virus. So people must attach great importance to the native machine be affected by other vicious virus. network security problem. The paper studied Trojan virus. Paper first introduced the concept, characteristics and PREVENTION OF HORSE VIRUS categories of the Trojan virus and its harm, and then focused on the way and means of the Trojan’s spread. It introduced the According to the above introduction, we know that Trojan virus loading and hiding technology, too. Its last part Trojan horse virus is very dangerous. If we neglect the focused on the prevention measures, it put forward reasonable prevention, our computer may be easily attacked. For the suggestions to users, and paper also put forward prevention prevention of Trojan intrusion, Trojan intrusion should be advice to improve network security. -

Antivirus Downloads Free the Best Antivirus Software 2021: Free and Paid Options Compared
antivirus downloads free The best antivirus software 2021: free and paid options compared. Having one of the best antivirus software packages in your device is as important as it has ever been. Yup, it's an incredibly boring and dry thing to think about - particularly as many of us won't have been affected by a virus for years and years, if ever - but that's not meant to say you shouldn't have one of the best antivirus packs anyway. It's definitely still a case of 'rather have it and not need than need it and not have it', for sure. We can guarantee that there are baddies still out there and want to get your personal details, even if it might not be in the traditional sense of a virus anymore. So, whether you have a premium machine like one of the best gaming PCs or one of the best gaming laptops, or just a cheap one for work, having one of the best antivirus will protect you while you work or play. If you're looking to beef up security on an Apple Mac or MacBook though, you might want to consider checking out our antivirus for Macs guide. However, in the year 2021, it is a very saturated market. There are free versions that we remember from years ago still around - though now refined - and also some newer or much-revamped paid-for programs that are more comprehensive than ever. As a result, it can be a confusing market to work your way through. But fear not, we’ve looked at a range of options available, from premium to free, from some of the biggest players in online security, to help you make a safe and informed decision on the best antivirus software for you.