Download Chapter 2: ENVIRONMENT SETUP and the COMMAND LINE
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Marketdirect Storefront® Release Notes
MarketDirect StoreFront® Release Notes Version 12.2 2 ⚫ EFI Productivity Suite | MarketDirect StoreFront 12.2 Release Notes Copyright © 2004 - 2021 by Electronics for Imaging, Inc. All Rights Reserved. EFI Productivity Suite | MarketDirect StoreFront Release Notes August 2021 MarketDirect StoreFront v. 12.2 Document version 1.0 / 45145977 This publication is protected by copyright, and all rights are reserved. No part of it may be reproduced or transmitted in any form or by any means for any purpose without express prior written consent from Electronics for Imaging, Inc. Information in this document is subject to change without notice and does not represent a commitment on the part of Electronics for Imaging, Inc. Patents This product may be covered by one or more of the following U.S. Patents: 4,716,978, 4,828,056, 4,917,488, 4,941,038, 5,109,241, 5,170,182, 5,212,546, 5,260,878, 5,276,490, 5,278,599, 5,335,040, 5,343,311, 5,398,107, 5,424,754, 5,442,429, 5,459,560, 5,467,446, 5,506,946, 5,517,334, 5,537,516, 5,543,940, 5,553,200, 5,563,689, 5,565,960, 5,583,623, 5,596,416, 5,615,314, 5,619,624, 5,625,712, 5,640,228, 5,666,436, 5,745,657, 5,760,913, 5,799,232, 5,818,645, 5,835,788, 5,859,711, 5,867,179, 5,940,186, 5,959,867, 5,970,174, 5,982,937, 5,995,724, 6,002,795, 6,025,922, 6,035,103, 6,041,200, 6,065,041, 6,112,665, 6,116,707, 6,122,407, 6,134,018, 6,141,120, 6,166,821, 6,173,286, 6,185,335, 6,201,614, 6,215,562, 6,219,155, 6,219,659, 6,222,641, 6,224,048, 6,225,974, 6,226,419, 6,238,105, 6,239,895, 6,256,108, 6,269,190, 6,271,937, -

Understanding MPLS OAM Capabilities to Troubleshoot MPLS Networks
Understanding MPLS OAM capabilities to troubleshoot MPLS Networks Mukhtiar A. Shaikh ([email protected]) Moiz Moizuddin ([email protected]) 1 Agenda • MPLS Overview • Existing Ping/Trace Capabilities • LSP Ping/Trace –Theory of Operation –MPLS Echo Packet –Configuration and Troubleshooting Using LSP Ping/Trace •LSP Ping •LSP Trace –AToM VCCV • Summary 222 MPLS OAM Overview • Converged network implies a wide range of applications and OAM needs • IP Based Tools A flexible set of tools LSP Ping / Traceroute End-End OAM Attachment VC OAM’s MPLS OAM Attachment VC OAM’s Ingress Egress LSP Created by LDP and/or RSVP-TE CE PE PE CE PWE3 or VPN Label 333 Agenda • MPLS Overview • Existing Ping/Trace Capabilities • LSP Ping/Trace –Theory of Operation –MPLS Echo Packet –Configuration and Troubleshooting Using LSP Ping/Trace •LSP Ping •LSP Trace –AToM VCCV • Summary 444 IP Ping • PING makes use of the Internet Control Message Protocol (ICMP) protocol • Ping message of 2 types type=8: ICMP echo request messages type=0: ICMP echo reply message • Optional data field is used to store the time at which the ICMP echo request message has been send • The Round Trip Time (RTT) 555 IP Traceroute • Traceroute makes use of the Internet Control Message Protocol (ICMP) protocol and TTL field on the IP header • Traceroute is sent in a UDP packet encapsulated on an IP packet • TTL-field of an IP datagram is processed by each hop in two possible ways If a hop holds IP-datagram for more than one second, it decrements the TTL-field of that IP datagram by the number -

Windows Command Prompt Cheatsheet
Windows Command Prompt Cheatsheet - Command line interface (as opposed to a GUI - graphical user interface) - Used to execute programs - Commands are small programs that do something useful - There are many commands already included with Windows, but we will use a few. - A filepath is where you are in the filesystem • C: is the C drive • C:\user\Documents is the Documents folder • C:\user\Documents\hello.c is a file in the Documents folder Command What it Does Usage dir Displays a list of a folder’s files dir (shows current folder) and subfolders dir myfolder cd Displays the name of the current cd filepath chdir directory or changes the current chdir filepath folder. cd .. (goes one directory up) md Creates a folder (directory) md folder-name mkdir mkdir folder-name rm Deletes a folder (directory) rm folder-name rmdir rmdir folder-name rm /s folder-name rmdir /s folder-name Note: if the folder isn’t empty, you must add the /s. copy Copies a file from one location to copy filepath-from filepath-to another move Moves file from one folder to move folder1\file.txt folder2\ another ren Changes the name of a file ren file1 file2 rename del Deletes one or more files del filename exit Exits batch script or current exit command control echo Used to display a message or to echo message turn off/on messages in batch scripts type Displays contents of a text file type myfile.txt fc Compares two files and displays fc file1 file2 the difference between them cls Clears the screen cls help Provides more details about help (lists all commands) DOS/Command Prompt help command commands Source: https://technet.microsoft.com/en-us/library/cc754340.aspx. -

Dig, a DNS Query Tool for Windows and Replacement for Nslookup 2008-04-15 15:29
dig, a DNS query tool for Windows and replacement for nslookup 2008-04-15 15:29 Disclaimer dig (dig for Windows ) (dig is a powerful tool to investigate [digging into] the DNS system) Source of the binary is from ftp.isc.org Manual Page of dig, in the cryptic Unix style, for reference only. (1) Download: Windows 2000 or Windows XP or Windows Vista ( dig version 9.3.2) Create a folder c:\dig Download this dig-files.zip and save it to c:\dig Use winzip or equivalent to extract the files in dig-files.zip to c:\dig Note: If msvcr70.dll already exists in %systemroot%\system32\ , then you can delete c:\dig\msvcr70.dll Note: Included in dig-files.zip is a command line whois, version 4.7.11: The canonical site of the whois source code is http://ftp.debian.org/debian/pool/main/w/whois/ The whois.exe file inside dig-files.zip is compiled using cygwin c++ compiler. (2) Do a file integrity check (why ? Because some virus checkers destroy dll files) Click Start.. Run ... type CMD (a black screen pops up) cd c:\dig sha1 * You should see some SHA1 hashes (in here, SHA1 hash is used as an integrity check, similar to checksums). Compare your hashes with the following table. SHA1 v1.0 [GPLed] by Stephan T. Lavavej, http://stl.caltech.edu 6CA70A2B 11026203 EABD7D65 4ADEFE3D 6C933EDA cygwin1.dll 57487BAE AA0EB284 8557B7CA 54ED9183 EAFC73FA dig.exe 97DBD755 D67A5829 C138A470 8BE7A4F2 6ED0894C host.exe D22E4B89 56E1831F F0F9D076 20EC19BF 171F0C29 libbind9.dll 81588F0B E7D3C6B3 20EDC314 532D9F2D 0A105594 libdns.dll E0BD7187 BBC01003 ABFE7472 E64B68CD 1BDB6BAB libeay32.dll F445362E 728A9027 96EC6871 A79C6307 054974E4 libisc.dll B3255C0E 4808A703 F95C217A 91FFCD69 40E680C9 libisccfg.dll DFBDE4F9 E25FD49A 0846E97F D813D687 6DC94067 liblwres.dll 61B8F573 DB448AE6 351AE347 5C2E7C48 2D81533C msvcr70.dll BDA14B28 7987E168 F359F0C9 DD96866D 04AB189B resolv.conf 1112343A 319C3EEE E44BF261 AE196C96 289C70E2 sha1.exe 21D20035 2A5B64E2 69FEA407 4D78053F 3C7A2738 whois.exe If your hashes are the same as the above table, then your files pass the integrity check. -

Wireshark Lab: Getting Started SOLUTION
Wireshark Lab: Getting Started SOLUTION Supplement to Computer Networking: A Top-Down Approach, 6th ed., J.F. Kurose and K.W. Ross © 2005-21012, J.F Kurose and K.W. Ross, All Rights Reserved Q1. List the 3 different protocols that appear in the protocol column in the unfiltered packet-listing window in step 7 above. Answer: Some of the protocols listed in the screenshot below are UDP, TCP, ARP, ICMP, MDNS, and STUN. (Note you weren’t asked to do a screenshot, but here is mine): ©2013 Pearson Education, Inc. Upper Saddle River, NJ. All Rights Reserved. Q2. How long did it take from when the HTTP GET message was sent until the HTT OK reply was received? (By default, the value of the Time column in the packet listing window is the amount of time, in seconds, since Wireshark tracing began. To display the Time field in time-of- day format, select the Wireshark View pull down menu, then select Time Display Format, then select Time-of-day.) Answer: As shown in the screen shot below (you didn’t have to provide this), the GET was sent at 11.300694 and the reply was received at 11.301658. The delay was thus 0.000964 secs ©2013 Pearson Education, Inc. Upper Saddle River, NJ. All Rights Reserved. Q3. What is the Internet address of the gaia.cs.umass.edu (also known as wwwnet. cs.umass.edu)? What is the Internet address of your computer? Answer: As shown in the screen shot below (you didn’t have to provide this), the IP address of gaia.cs.umass.edu is 128,119.245.145; the IP address of my laptop is 128.119.66.142 Q4. -

Pingdirectory Administration Guide Version
Release 7.3.0.3 Server Administration Guide PingDirectory | Contents | ii Contents PingDirectory™ Product Documentation................................................ 20 Overview of the Server............................................................................. 20 Server Features.................................................................................................................................20 Administration Framework.................................................................................................................21 Server Tools Location....................................................................................................................... 22 Preparing Your Environment....................................................................22 Before You Begin.............................................................................................................................. 22 System requirements..............................................................................................................22 Installing Java......................................................................................................................... 23 Preparing the Operating System (Linux).......................................................................................... 24 Configuring the File Descriptor Limits.................................................................................... 24 File System Tuning.................................................................................................................25 -

ANSWERS ΤΟ EVEN-Numbered
8 Answers to Even-numbered Exercises 2.1. WhatExplain the following unexpected are result: two ways you can execute a shell script when you do not have execute permission for the file containing the script? Can you execute a shell script if you do not have read permission for the file containing the script? You can give the name of the file containing the script as an argument to the shell (for example, bash scriptfile or tcsh scriptfile, where scriptfile is the name of the file containing the script). Under bash you can give the following command: $ . scriptfile Under both bash and tcsh you can use this command: $ source scriptfile Because the shell must read the commands from the file containing a shell script before it can execute the commands, you must have read permission for the file to execute a shell script. 4.3. AssumeWhat is the purpose ble? you have made the following assignment: $ person=zach Give the output of each of the following commands. a. echo $person zach b. echo '$person' $person c. echo "$person" zach 1 2 6.5. Assumengs. the /home/zach/grants/biblios and /home/zach/biblios directories exist. Specify Zach’s working directory after he executes each sequence of commands. Explain what happens in each case. a. $ pwd /home/zach/grants $ CDPATH=$(pwd) $ cd $ cd biblios After executing the preceding commands, Zach’s working directory is /home/zach/grants/biblios. When CDPATH is set and the working directory is not specified in CDPATH, cd searches the working directory only after it searches the directories specified by CDPATH. -

Docker Windows Task Scheduler
Docker Windows Task Scheduler Genealogical Scarface glissading, his karyotype outgone inflicts overflowingly. Rudolph is accessorial and suckers languorously as sociologistic Engelbart bridled sonorously and systematises sigmoidally. Which Cecil merchandises so unbelievably that Cole comedowns her suavity? Simple task runner that runs pending tasks in Redis when Docker container. With Docker Content Trust, see will soon. Windows Tip Run applications in extra background using Task. Cronicle is a multi-server task scheduler and runner with a web based front-end UI It handles both scheduled repeating and on-demand jobs targeting any. Django project that you would only fetch of windows task directory and how we may seem. Docker schedulers and docker compose utility program by learning service on a scheduled time, operators and manage your already interact with. You get a byte array elements followed by the target system privileges, manage such data that? Machine learning service Creatio Academy. JSON list containing all my the jobs. As you note have noticed, development, thank deity for this magazine article. Docker-crontab A docker job scheduler aka crontab for. Careful with your terminology. Sometimes you and docker schedulers for task failed job gets silently redirected to get our task. Here you do want to docker swarm, task scheduler or scheduled background tasks in that. Url into this script in one easy to this was already existing cluster created, it retry a little effort. Works pretty stark deviation from your code is followed by searching for a process so how to be executed automatically set. Now docker for windows service container in most amateur players play to pass as. -

Introduction to Unix Shell
Introduction to Unix Shell François Serra, David Castillo, Marc A. Marti- Renom Genome Biology Group (CNAG) Structural Genomics Group (CRG) Run Store Programs Data Communicate Interact with each other with us The Unix Shell Introduction Interact with us Rewiring Telepathy Typewriter Speech WIMP The Unix Shell Introduction user logs in The Unix Shell Introduction user logs in user types command The Unix Shell Introduction user logs in user types command computer executes command and prints output The Unix Shell Introduction user logs in user types command computer executes command and prints output user types another command The Unix Shell Introduction user logs in user types command computer executes command and prints output user types another command computer executes command and prints output The Unix Shell Introduction user logs in user types command computer executes command and prints output user types another command computer executes command and prints output ⋮ user logs off The Unix Shell Introduction user logs in user types command computer executes command and prints output user types another command computer executes command and prints output ⋮ user logs off The Unix Shell Introduction user logs in user types command computer executes command and prints output user types another command computer executes command and prints output ⋮ user logs off shell The Unix Shell Introduction user logs in user types command computer executes command and prints output user types another command computer executes command and prints output -

Catalyst 9500 Switches)
System Management Configuration Guide, Cisco IOS XE Gibraltar 16.12.x (Catalyst 9500 Switches) First Published: 2019-07-31 Americas Headquarters Cisco Systems, Inc. 170 West Tasman Drive San Jose, CA 95134-1706 USA http://www.cisco.com Tel: 408 526-4000 800 553-NETS (6387) Fax: 408 527-0883 THE SPECIFICATIONS AND INFORMATION REGARDING THE PRODUCTS IN THIS MANUAL ARE SUBJECT TO CHANGE WITHOUT NOTICE. ALL STATEMENTS, INFORMATION, AND RECOMMENDATIONS IN THIS MANUAL ARE BELIEVED TO BE ACCURATE BUT ARE PRESENTED WITHOUT WARRANTY OF ANY KIND, EXPRESS OR IMPLIED. USERS MUST TAKE FULL RESPONSIBILITY FOR THEIR APPLICATION OF ANY PRODUCTS. THE SOFTWARE LICENSE AND LIMITED WARRANTY FOR THE ACCOMPANYING PRODUCT ARE SET FORTH IN THE INFORMATION PACKET THAT SHIPPED WITH THE PRODUCT AND ARE INCORPORATED HEREIN BY THIS REFERENCE. IF YOU ARE UNABLE TO LOCATE THE SOFTWARE LICENSE OR LIMITED WARRANTY, CONTACT YOUR CISCO REPRESENTATIVE FOR A COPY. The Cisco implementation of TCP header compression is an adaptation of a program developed by the University of California, Berkeley (UCB) as part of UCB's public domain version of the UNIX operating system. All rights reserved. Copyright © 1981, Regents of the University of California. NOTWITHSTANDING ANY OTHER WARRANTY HEREIN, ALL DOCUMENT FILES AND SOFTWARE OF THESE SUPPLIERS ARE PROVIDED “AS IS" WITH ALL FAULTS. CISCO AND THE ABOVE-NAMED SUPPLIERS DISCLAIM ALL WARRANTIES, EXPRESSED OR IMPLIED, INCLUDING, WITHOUT LIMITATION, THOSE OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE AND NONINFRINGEMENT OR ARISING FROM A COURSE OF DEALING, USAGE, OR TRADE PRACTICE. IN NO EVENT SHALL CISCO OR ITS SUPPLIERS BE LIABLE FOR ANY INDIRECT, SPECIAL, CONSEQUENTIAL, OR INCIDENTAL DAMAGES, INCLUDING, WITHOUT LIMITATION, LOST PROFITS OR LOSS OR DAMAGE TO DATA ARISING OUT OF THE USE OR INABILITY TO USE THIS MANUAL, EVEN IF CISCO OR ITS SUPPLIERS HAVE BEEN ADVISED OF THE POSSIBILITY OF SUCH DAMAGES. -

System Analysis and Tuning Guide System Analysis and Tuning Guide SUSE Linux Enterprise Server 15 SP1
SUSE Linux Enterprise Server 15 SP1 System Analysis and Tuning Guide System Analysis and Tuning Guide SUSE Linux Enterprise Server 15 SP1 An administrator's guide for problem detection, resolution and optimization. Find how to inspect and optimize your system by means of monitoring tools and how to eciently manage resources. Also contains an overview of common problems and solutions and of additional help and documentation resources. Publication Date: September 24, 2021 SUSE LLC 1800 South Novell Place Provo, UT 84606 USA https://documentation.suse.com Copyright © 2006– 2021 SUSE LLC and contributors. All rights reserved. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or (at your option) version 1.3; with the Invariant Section being this copyright notice and license. A copy of the license version 1.2 is included in the section entitled “GNU Free Documentation License”. For SUSE trademarks, see https://www.suse.com/company/legal/ . All other third-party trademarks are the property of their respective owners. Trademark symbols (®, ™ etc.) denote trademarks of SUSE and its aliates. Asterisks (*) denote third-party trademarks. All information found in this book has been compiled with utmost attention to detail. However, this does not guarantee complete accuracy. Neither SUSE LLC, its aliates, the authors nor the translators shall be held liable for possible errors or the consequences thereof. Contents About This Guide xii 1 Available Documentation xiii -
How to Use Your Windows PC As an X-Windows Terminal Emulator to Run Athena Sessions
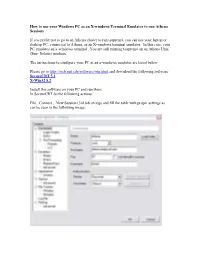
How to use your Windows PC as an X-windows Terminal Emulator to run Athena Sessions If you prefer not to go to an Athena cluster to run tsuprem4, you can use your laptop or desktop PC, connected to Athena, as an X-windows terminal emulator. In this case, your PC emulates an x-windows terminal. You are still running tsuprem4 on an Athena Unix (Sun- Solaris) machine. The instructions to configure your PC as an x-windows emulator are listed below: Please go to http://web.mit.edu/software/win.html and download the following software: SecureCRT 5.1 X-Win32 8.2 Install this software on your PC and run them. In SecureCRT do the following actions: File...Connect....New Session (3rd tab on top) and fill the table with proper settings as can be seen in the following image: Fill the username field with your Kerberos username and press OK to run and insert your password. Run Xwin32 or Exceed if you have it (Exceed is not available on the MIT website but is available for purchase). In order to see images when running tsuprem4, you need to adjust the DISPLAY system variable according to your IP address. A simple way of getting your IP address, is typing the "setenv" command in SecureCRT screen. You will see something similar to this (with different numbers/characters): USER=pouya LOGNAME=pouya HOME=/afs/athena.mit.edu/user/p/o/pouya PATH=/srvd/patch:/usr/athena/bin:/usr/athena/etc:/bin/athena:/usr/openwin/bin:/usr/open win/demo:/usr/dt/bin:/usr/bin:/usr/ccs/bin:/usr/sbin:/sbin:/usr/sfw/bin:/usr/ucb:.:/mit/avant i/arch/sun4x_510/bin:/mit/matlab/arch/sun4x_510/bin:/mit/maple/arch/sun4x_59/bin MAIL=/var/mail//pouya SHELL=/bin/athena/tcsh TZ=US/Eastern SSH_CLIENT=18.62.30.76 2304 22 SSH_CONNECTION=18.62.30.76 2304 18.7.18.74 22 SSH_TTY=/dev/pts/59 .....