Lua Code: Security Overview and Practical Approaches to Static Analysis
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Oracle Communications Policy Management Licensing Information User Manual Release 12.5 Copyright © 2011, 2019, Oracle And/Or Its Affiliates
Oracle® Communications Policy Management Licensing Information User Manual Release 12.5.1 F16918-02 October 2019 Oracle Communications Policy Management Licensing Information User Manual Release 12.5 Copyright © 2011, 2019, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are “commercial computer software” pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. -

Avaliação Do Site Sitecheckdoctoronline.Net
Avaliação do site sitecheckdoctoronline.net Gerado a 02 de Setembro de 2020 05:08 AM O resultado é de 44/100 Conteúdo SEO Título Pro WebSite SEO Rank DocTor - Anlyze Tools Cumprimento : 43 Perfeito, o Título contém entre 10 e 70 caracteres. Descrição Site DocTor ProRank helps to check your web page online, anlyze contents for a better search engine ranking and boot your visitors. Cumprimento : 131 Perfeito, a Descrição META contém entre 70 e 160 caracteres. Palavras-chave Mau. Não detetámos palavras-chave META na sua página. Propriedades Og Boa! Esta página tira vantagens das propriedades Og. Meta Propriedade Conteúdo image http://sitecheckdoctoronline.net/assets/images/ facebook_banner.jpg Cabeçalhos H1 H2 H3 H4 H5 H6 1 5 6 0 0 0 [H1] ProRank Optimize Your Website [H2] 2,484 sites has been analyzed by ProRank [H2] Latest Updated Sites [H2] About Us [H2] Contact Info [H2] Follow Us [H3] In-Depth Reviews [H3] Recommendations Checklist [H3] SEO Analysis [H3] Top Technologies [H3] Top Web Servers [H3] Top Web Frameworks Conteúdo SEO Imagens Encontrámos 61 imagens nesta página. 41 atributos ALT estão vazios ou em falta. É recomendado adicionar texto alternativo de modo a que os motores de busca identifiquem melhor o conteúdo das suas imagens. Rácio Texto/HTML Rácio : 2% O rácio de texto para código HTML desta página é menor que 15 porcento, o que significa que provavelmente é necessário de adicionar mais conteúdos em forma de texto. Flash Perfeito, não foi encontrado conteúdo Flash nesta página. Iframe Excelente, não foram detetadas Iframes nesta página. Ligações SEO Reescrita de URL Perfeito. -

Towards Left Duff S Mdbg Holt Winters Gai Incl Tax Drupal Fapi Icici
jimportneoneo_clienterrorentitynotfoundrelatedtonoeneo_j_sdn neo_j_traversalcyperneo_jclientpy_neo_neo_jneo_jphpgraphesrelsjshelltraverserwritebatchtransactioneventhandlerbatchinsertereverymangraphenedbgraphdatabaseserviceneo_j_communityjconfigurationjserverstartnodenotintransactionexceptionrest_graphdbneographytransactionfailureexceptionrelationshipentityneo_j_ogmsdnwrappingneoserverbootstrappergraphrepositoryneo_j_graphdbnodeentityembeddedgraphdatabaseneo_jtemplate neo_j_spatialcypher_neo_jneo_j_cyphercypher_querynoe_jcypherneo_jrestclientpy_neoallshortestpathscypher_querieslinkuriousneoclipseexecutionresultbatch_importerwebadmingraphdatabasetimetreegraphawarerelatedtoviacypherqueryrecorelationshiptypespringrestgraphdatabaseflockdbneomodelneo_j_rbshortpathpersistable withindistancegraphdbneo_jneo_j_webadminmiddle_ground_betweenanormcypher materialised handaling hinted finds_nothingbulbsbulbflowrexprorexster cayleygremlintitandborient_dbaurelius tinkerpoptitan_cassandratitan_graph_dbtitan_graphorientdbtitan rexter enough_ram arangotinkerpop_gremlinpyorientlinkset arangodb_graphfoxxodocumentarangodborientjssails_orientdborientgraphexectedbaasbox spark_javarddrddsunpersist asigned aql fetchplanoriento bsonobjectpyspark_rddrddmatrixfactorizationmodelresultiterablemlibpushdownlineage transforamtionspark_rddpairrddreducebykeymappartitionstakeorderedrowmatrixpair_rddblockmanagerlinearregressionwithsgddstreamsencouter fieldtypes spark_dataframejavarddgroupbykeyorg_apache_spark_rddlabeledpointdatabricksaggregatebykeyjavasparkcontextsaveastextfilejavapairdstreamcombinebykeysparkcontext_textfilejavadstreammappartitionswithindexupdatestatebykeyreducebykeyandwindowrepartitioning -

Prologin System Administration Release 2020
Prologin System Administration Release 2020 Association Prologin Sep 28, 2020 CONTENTS 1 Infrastructure overview 3 1.1 Needs ................................................... 3 1.2 Network infrastructure .......................................... 4 1.3 Machine database ............................................. 4 1.4 User database ............................................... 4 1.5 File storage ................................................ 5 1.6 DHCP and DNS ............................................. 5 1.7 Matches cluster .............................................. 6 1.8 Other small services ........................................... 6 2 Setup instructions 7 2.1 Step 0: hardware and network setup ................................... 7 2.2 Step 1: setting up the core services: MDB, DNS, DHCP ......................... 8 2.3 Step 2: file storage ............................................ 19 2.4 Step 3: booting the user machines .................................... 20 2.5 Step 4: Concours ............................................. 22 2.6 Step 5: Setting up masternode and workernode .............................. 23 2.7 Step 6: Switching to contest mode .................................... 24 2.8 Common tasks .............................................. 24 3 Misc services 27 3.1 /sgoinfre ............................................... 27 3.2 doc .................................................... 28 3.3 paste ................................................... 28 3.4 Redmine ................................................ -

Automatic Fingerprinting of Websites Automatisk Fingeravtryckning Av
DEGREE PROJECT IN COMPUTER ENGINEERING, FIRST CYCLE, 15 CREDITS STOCKHOLM, SWEDEN 2020 Automatic fingerprinting of websites Using clustering and multiple bag-of-words models Automatisk fingeravtryckning av hemsidor Med användning av klustring och flera ordvektormodeller ALFRED BERG NORTON LAMBERG KTH ROYAL INSTITUTE OF TECHNOLOGY SCHOOL OF ENGINEERING SCIENCES IN CHEMISTRY, BIOTECHNOLOGY AND HEALTH Automatic fingerprinting of websites Using clustering and multiple bag-of-words models Automatisk fingeravtryckning av hemsidor Med användning av klustring och flera ordvektormodeller Alfred Berg Norton Lamberg Examensarbete inom Datateknik, Grundnivå, 15 hp Handledare: Shahid Raza Examinator: Ibrahim Orhan TRITA-CBH-GRU-2020:060 KTH Skolan för kemi, bioteknologi och hälsa 141 52 Huddinge, Sverige Abstract Fingerprinting a website is the process of identifying what technologies a website uses, such as their used web applications and JavaScript frameworks. Current fingerprinting methods use manually created fingerprints for each technology it looks for. These fingerprints consist of multiple text strings that are matched against an HTTP response from a website. Creating these fingerprints for each technology can be time-consuming, which limits what technologies fingerprints can be built for. This thesis presents a potential solution by utilizing unsupervised machine learning techniques to cluster websites by their used web application and JavaScript frameworks, without requiring manually created fingerprints. Our solution uses multiple bag-of-words models combined with the dimensionality reduction technique t-SNE and clustering algorithm OPTICS. Results show that some technologies, for example, Drupal, achieve a precision of 0.731 and recall of 0.485 without any training data. These results lead to the conclusion that the proposed solution could plausibly be used to cluster websites by their web application and JavaScript frameworks in use. -

Omid Raha Mystack Documentation Release 0.1
Omid Raha MyStack Documentation Release 0.1 Omid Raha Oct 28, 2019 Contents 1 Aircrack-ng 3 1.1 Install...................................................3 1.1.1 Install aircrack-ng 1.2-beta1 from source............................3 2 APPLE 5 2.1 Tips....................................................5 2.1.1 Apple ID............................................5 2.1.2 Hackintosh...........................................5 3 Astronomy 7 3.1 astronomical unit (AU, or au)......................................7 3.2 What Is the Distance Between Earth and Mars?.............................7 3.3 What is the Distance to the Moon?....................................7 3.4 What Is the Distance Between Earth and sun?..............................7 3.5 Software.................................................8 3.6 Galaxy..................................................8 4 Atlassian 9 4.1 Tips....................................................9 4.1.1 Atlassian installation approach.................................9 4.1.2 Atlassian license Prices..................................... 10 4.1.3 Run Jira with docker...................................... 11 4.1.4 Run Confluence with docker.................................. 12 4.1.5 Run Bitbucket Server with docker............................... 12 4.1.6 JIRA is Unable to Start due to Could not create necessary subdirectory............ 12 4.1.7 Atlassian Docker compose file................................. 13 4.1.8 Backup atlassian product.................................... 15 4.1.9 Bamboo............................................ -
Open Source Disclosure
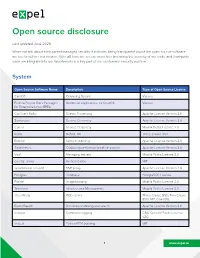
Open source disclosure Last updated June 2020 When we talk about transparent managed security it includes being transparent about the open source software we use to deliver our service. After all, how we secure ourselves (including the security of our code and third-party code we integrate into our Workbench) is a key part of our customers’ security posture. System Open Source Software Name Description Type of Open Source License CentOS Operating System Various Fedora Project Extra Packages Additional applications for CentOS Various for Enterprise Linux (EPEL) Confluent Kafka Stream Processing Apache License Version 2.0 Zookeeper Service Discovery Apache License Version 2.0 Consul Service Discovery Mozilla Public License 2.0 Redis NoSQL DB Three Clause BSD Burrow Kafka monitoring Apache License Version 2.0 Timesketch Collaborative forensic timeline analysis Apache License Version 2.0 Vault Managing secrets Mozilla Public License 2.0 oauth2_proxy Authentication MIT Gravitational Teleport SSH proxy Apache License Version 2.0 Postgres Database PostgreSQL License Packer Image building Mozilla Public License 2.0 Terraform Infrastructure Management Mozilla Public License 2.0 OpenResty Web server Three Clause BSD, Two Clause BSD, MIT, OpenSSL ElasticSearch Document indexing and search Apache License Version 2.0 snoopy Command logging GNU General Public License v2.0 ship_it Python RPM building MIT 1 www.expel.io Python Open Source Software Name Description Type of Open Source License simplejson Simple, fast, extensible JSON encoder/decoder for Academic Free License, MIT Python aiohttp Async http client/server framework (asyncio) Apache License Version 2.0 ansible-tower-cli A CLI tool for Ansible Tower and AWX. -

Cloud Native Core Licensing Information User Manual
Oracle® Communications Cloud Native Core Licensing Information User Manual Release 2.1.0 F22873-02 January 2020 Oracle Communications Cloud Native Core Licensing Information User Manual, Release 2.1.0 F22873-02 Copyright © 2019, 2020, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs.