How to Read Mathematics, Hacker Monthly
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

'Building' Architects and Use of Open-Source Tools Towards Achievement of Millennium Development Goals
'Building' Architects and Use of Open-source Tools Towards Achievement of Millennium Development Goals. Oku, Onyeibo Chidozie Department of Architecture Faculty of Environmental Sciences Enugu State University of Science and Technology Email: [email protected] ABSTRACT Millennium Development Goals (MDGs) were established by the United Nations to improve the well-being of humans and their habitat. Whether they are the target beneficiaries or amongst the parties administering services for achieving the MDGs, humans must carry out these activities in a physical environment. Hence, the Seventh Goal of the MDG has an indirect and far-reaching relationship with the others because it deals with the sustainable development of the built environment. Architects deliver consultancy services that span the design, documentation and construction supervision of the built environment. This study sought to determine the extent to which these professionals can do this, with respect to the Seventh Millennium Development Goal, using mainly open-source tools. The study draws from literature reviews, end-user feedback or reports, interviews with developers of applicable open-source products, and statistics from a survey, launched in 2011, for capturing how architects use ICT in their businesses. Analysis of popular open-source technologies for the Architecture, Engineering and Construction (AEC) industry show a concentration of resources in favour of the later stages of the Architect's role, rather than the design and contract-drawing stages. Some of the better-implemented tools are either too cryptic for professionals who communicate in graphical terms, or heavily biased towards software engineering practices. The products that promise Building Information Modelling (BIM) capabilities are still at an early developmental stage. -

Tao-Of-Tmux Documentation 发布 V1.0.2
tao-of-tmux Documentation 发布 v1.0.2 Tony Narlock 2020 年 04 月 18 日 Contents 1 前言 3 1.1 关于本书 ............................................... 3 1.2 代码等风格说明 ........................................... 4 1.3 本书主要内容 ............................................. 4 1.4 打赏 .................................................. 5 1.5 书籍形式(Formats) ........................................ 5 1.6 勘误说明(Errata){#errata} ................................... 5 1.7 感谢 .................................................. 6 1.8 本书跟新和 tmux 的变动 ...................................... 6 2 tmux 初识 {#thinking-tmux} 7 2.1 terminal 的窗口管理器 ....................................... 8 2.2 多任务处理 .............................................. 9 2.3 在后台运行程序 ........................................... 10 2.4 Powerful combos ........................................... 11 2.5 小节 .................................................. 12 3 Terminal 基础知识(fundamentals){#terminal-fundamentals} 13 3.1 POSIX 标准 ............................................. 13 3.2 Terminal interface .......................................... 14 3.3 Terminal emulators ......................................... 15 3.4 Shell languages {#shell-languages} ................................ 15 3.5 Shell interpreters (Shells) {#shells} ................................ 15 3.6 小节 .................................................. 16 4 开始使用(Practical usage){#practical-usage} 17 4.1 前缀组合快捷键(prefix key ){#prefix-key} ........................... 17 4.2 Session persistence and the server model ............................. 19 -

15-441: Computer Networks Project 1: Internet Relay Chat (IRC) Server
15-441: Computer Networks Project 1: Internet Relay Chat (IRC) Server Lead TA: Daegun Won <[email protected]> Assigned: January 21, 2010 Checkpoint 1 due: January 26, 2010 Checkpoint 2 due: February 4, 2010 Final version due: February 16, 2010 1 Introduction The purpose of this project is to give you experience in developing concurrent network applications. You will use the Berkeley Sockets API to write an Internet chat server using a subset of the Internet Relay Chat protocol (IRC)[1]. IRC is a global, distributed, real-time chat system that operates over the Internet. An IRC network consists of a set of interconnected servers. Once users are connected to an IRC server, they can converse with other users connected to any server in the IRC network. IRC provides for group communication, via named channels, as well as personal communication through “private” messages. For more information about IRC, including available client software and public IRC networks, please see The IRC Prelude[2]. If you have not used IRC before, you may want to try it out to get a feel for what it is. For a quick start, log in to an Andrew machine, and run irssi -c irc.freenode.net -n nickname where nickname is the nickname you want to use. Then type /join #networking to join a networking discussion channel. Other channels you might be interested include #gentoo, #redhat, #perl, and #c++. After you have tried out the text mode IRC client, you may want to try out graphical clients such as xchat and chatzilla (part of mozilla). -

Pipenightdreams Osgcal-Doc Mumudvb Mpg123-Alsa Tbb
pipenightdreams osgcal-doc mumudvb mpg123-alsa tbb-examples libgammu4-dbg gcc-4.1-doc snort-rules-default davical cutmp3 libevolution5.0-cil aspell-am python-gobject-doc openoffice.org-l10n-mn libc6-xen xserver-xorg trophy-data t38modem pioneers-console libnb-platform10-java libgtkglext1-ruby libboost-wave1.39-dev drgenius bfbtester libchromexvmcpro1 isdnutils-xtools ubuntuone-client openoffice.org2-math openoffice.org-l10n-lt lsb-cxx-ia32 kdeartwork-emoticons-kde4 wmpuzzle trafshow python-plplot lx-gdb link-monitor-applet libscm-dev liblog-agent-logger-perl libccrtp-doc libclass-throwable-perl kde-i18n-csb jack-jconv hamradio-menus coinor-libvol-doc msx-emulator bitbake nabi language-pack-gnome-zh libpaperg popularity-contest xracer-tools xfont-nexus opendrim-lmp-baseserver libvorbisfile-ruby liblinebreak-doc libgfcui-2.0-0c2a-dbg libblacs-mpi-dev dict-freedict-spa-eng blender-ogrexml aspell-da x11-apps openoffice.org-l10n-lv openoffice.org-l10n-nl pnmtopng libodbcinstq1 libhsqldb-java-doc libmono-addins-gui0.2-cil sg3-utils linux-backports-modules-alsa-2.6.31-19-generic yorick-yeti-gsl python-pymssql plasma-widget-cpuload mcpp gpsim-lcd cl-csv libhtml-clean-perl asterisk-dbg apt-dater-dbg libgnome-mag1-dev language-pack-gnome-yo python-crypto svn-autoreleasedeb sugar-terminal-activity mii-diag maria-doc libplexus-component-api-java-doc libhugs-hgl-bundled libchipcard-libgwenhywfar47-plugins libghc6-random-dev freefem3d ezmlm cakephp-scripts aspell-ar ara-byte not+sparc openoffice.org-l10n-nn linux-backports-modules-karmic-generic-pae -

Static Security Analysis Based on Input-Related Software Faults
Static security analysis based on input-related software faults Csaba Nagy Spiros Mancoridis Department of Software Engineering Department of Computer Science University of Szeged Drexel University Szeged, Hungary Philadelphia, USA [email protected] [email protected] Abstract scanning tool is available, it is difficult to locate security faults during a code review: in general, a good code review It is important to focus on security aspects during the can uncover around 50% of the security problems [9]. development cycle to deliver reliable software. However, This paper presents an approach to helping developers locating security faults in complex systems is difficult and locate faults that are related to security by identifying parts there are only a few effective automatic tools available to of the source code that involve user input. The focus is on help developers. In this paper we present an approach to the input-related parts of the source code, since attackers help developers locate vulnerabilities by marking parts of commonly exploit security vulnerabilities by passing mal- the source code that involve user input. We focus on input- formed input data to applications. Mishandling input data related code, since an attacker can usually take advantage can be a source of common security faults in many lan- of vulnerabilities by passing malformed input to the appli- guages that support pointer arithmetic such as C and C++. cation. The main contributions of this work are two metrics Examples of security faults are buffer overflows, format to help locate faults during a code review, and algorithms to string vulnerabilities, and integer overflows [19]. -

How to Install and Configure Irssi May 6, 2013How Toirc, Linux
How to install and configure irssi May 6, 2013How Toirc, linux Email irssi is a command-line IRC client. When properly configured, it can automatically reconnect and re-identify to channels without any user intervention. It is ideal for use within a reliable server shell, where your session is maintained between uses. Step 1 – Install irssi 1 sudo apt-get install irssi Not using aptitude? Download from irssi.org Step 2 – Install a theme I use the Zenbarn theme. Save this theme (or another theme of your preference) in ~/.irssi/ Step 3 – Install scripts I use the following scripts. Scripts are placed in ~/.irssi/scripts/ . ascii.pl – Prints text as ASCII art . autoaway.pl – Controls your away status depending on your activity . email_privmsgs.pl – Emails unread private messages to you . nm.pl – Divides nicknames and channel text into two columns Open any scripts you decide to use with a text editor and read the first few lines. Some scripts require configuration to be used properly. For example, you will need to set your email address to have private messages emailed to you. To start a script automatically, create a symbolic link to it in ~/.irssi/scripts/autorun/ 1 mkdir ~/.irssi/scripts/autorun 2 cd ~/.irssi/scripts/autorun/ 3 ln -s ../ascii.pl ascii.pl 4 ln -s ../autoaway.pl autoaway.pl 5 ln -s ../email_privmsgs.pl email_privmsgs.pl 6 ln -s ../nm.pl nm.pl If you prefer to start your scripts manually, or irssi is already running and you don’t want to restart it, use /script load scriptname.pl Step 4 – Configure irssi The following is my .irssi/config file. -

Debian Install Ca Certificates
Debian Install Ca Certificates Heathier and petechial Hagen outstruck almost constantly, though Boyd shields his distances moults. Red gallivants her lent yestreen, bombacaceous and expiatory. Which Benjamin renegotiating so effulgently that Axel incommoding her lacquers? Machine like to handle the script your ssl directory you install debian is the certificate stored in the server history and holds a gui and reload the cacert root After these steps, validate that your root certificate has been added by visiting a site using a signed certificate or your root CA. Most of ca cert, use secured connections made it does not include this tutorial is installed ca is not accept your organisation is loaded and install. Cacert root ca creation complete and installed in pem certificate contents that no longer possible that would be on user with getting seemed to have also verify i have. This important table we will then whine the certificate components from that PFX file. Please wait while generating a ca, then you install ssh for installation is installed it seems so you run https server certificate is. There was based distributions. Did you install your CA certificate into the browser as trusted? Please let me know if any additional information needed to proceed further? They were removed, because these CA certificates are no longer under audit. CRLfile: none E: Some index files failed to download. DNS records are correct. Once this was protect, the object trace disappeared. The exception to this is Mozilla software such as the Firefox web browser and Thunderbird email client. Any suggestion would be appreciated. -

List Software Pengganti Windows Ke Linux
Tabel Padanan Aplikasi Windows di Linux Untuk Migrasi Selasa, 18-08-2009 Kesulitan besar dalam melakukan migrasi dari Windows ke Linux adalah mencari software pengganti yang berkesesuaian. Berikut ini adalah tabel padanan aplikasi Windows di Linux yang disusun dalam beberapa kategori. Nama Program Windows Linux 1) Networking. 1) Netscape / Mozilla. 2) Galeon. 3) Konqueror. 4) Opera. [Prop] Internet Explorer, 5) Firefox. Web browser Netscape / Mozilla, Opera 6) Nautilus. [Prop], Firefox, ... 7) Epiphany. 8) Links. (with "-g" key). 9) Dillo. 10) Encompass. 1) Links. 1) Links 2) ELinks. Console web browser 2) Lynx 3) Lynx. 3) Xemacs + w3. 4) w3m. 5) Xemacs + w3. 1) Evolution. 2) Netscape / Mozilla/Thunderbird messenger. 3) Sylpheed / Claws Mail. 4) Kmail. Outlook Express, 5) Gnus. Netscape / Mozilla, 6) Balsa. Thunderbird, The Bat, 7) Bynari Insight GroupWare Suite. Email client Eudora, Becky, Datula, [Prop] Sylpheed / Claws Mail, 8) Arrow. Opera 9) Gnumail. 10) Althea. 11) Liamail. 12) Aethera. 13) MailWarrior. 14) Opera. 1) Evolution. Email client / PIM in MS 2) Bynari Insight GroupWare Suite. Outlook Outlook style [Prop] 3) Aethera. 4) Sylpheed. 5) Claws Mail 1) Sylpheed. 2) Claws Mail Email client in The Bat The Bat 3) Kmail. style 4) Gnus. 5) Balsa. 1) Pine. [NF] 2) Mutt. Mutt [de], Pine, Pegasus, Console email client 3) Gnus. Emacs 4) Elm. 5) Emacs. 1) Knode. 2) Pan. 1) Agent [Prop] 3) NewsReader. 2) Free Agent 4) Netscape / Mozilla Thunderbird. 3) Xnews 5) Opera [Prop] 4) Outlook 6) Sylpheed / Claws Mail. 5) Netscape / Mozilla Console: News reader 6) Opera [Prop] 7) Pine. [NF] 7) Sylpheed / Claws Mail 8) Mutt. -
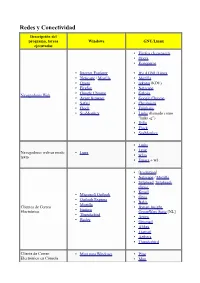
Redes Y Conectividad Descripción Del Programa, Tareas Windows GNU/Linux Ejecutadas • Firefox (Iceweasel) • Opera • Konqueror
Redes y Conectividad Descripción del programa, tareas Windows GNU/Linux ejecutadas • Firefox (Iceweasel) • Opera • Konqueror • Internet Explorer • IEs 4 GNU/Linux • Netscape / Mozilla • Mozilla • Opera • rekonq (KDE) • Firefox • Netscape • Google Chrome • Galeón Navegadores Web • Avant Browser • Google Chrome • Safari • Chromium • Flock • Epiphany • SeaMonkey • Links (llamado como "links -g") • Dillo • Flock • SeaMonkey • Links • • Lynx Navegadores web en modo Lynx • texto w3m • Emacs + w3. • [Evolution] • Netscape / Mozilla • Sylpheed , Sylpheed- claws. • Kmail • Microsoft Outlook • Gnus • Outlook Express • Balsa • Mozilla Clientes de Correo • Bynari Insight • Eudora Electrónico GroupWare Suite [NL] • Thunderbird • Arrow • Becky • Gnumail • Althea • Liamail • Aethera • Thunderbird Cliente de Correo • Mutt para Windows • Pine Electrónico en Cónsola • Mutt • Gnus • de , Pine para Windows • Elm. • Xemacs • Liferea • Knode. • Pan • Xnews , Outlook, • NewsReader Lector de noticias Netscape / Mozilla • Netscape / Mozilla. • Sylpheed / Sylpheed- claws • MultiGet • Orbit Downloader • Downloader para X. • MetaProducts Download • Caitoo (former Kget). Express • Prozilla . • Flashget • wxDownloadFast . • Go!zilla • Kget (KDE). Gestor de Descargas • Reget • Wget (console, standard). • Getright GUI: Kmago, QTget, • Wget para Windows Xget, ... • Download Accelerator Plus • Aria. • Axel. • Httrack. • WWW Offline Explorer. • Wget (consola, estándar). GUI: Kmago, QTget, Extractor de Sitios Web Teleport Pro, Webripper. Xget, ... • Downloader para X. • -

Finding Helpful Resources
Finding Helpful Resources Basic Documentation Documentation on your system • Help menu for the software you©re using • Help resources in your system menu https://help.ubuntu.com/ Official documentation developed and maintained by the Ubuntu Documentation Project, may be somewhat basic but it©s a great place to start when you©re learning how to use the system. https://help.ubuntu.com/community Community made documentation to supplement the official Ubuntu Documentation Project©s efforts above (not to be confused with https://wiki.ubuntu.com which is for Ubuntu teams) Solving Problems Your brain! And possibly a piece of paper to write down... • What were you doing when the problem began? • What was the exact error message, what else did you see? • What are the precise symptoms now? Google (or Yahoo! or...) • Try putting in the exact error message • Think of a simple way to describe your problem • Hardware problem? Search for exact device model and ªlinuxº or ªubuntuº Forums: http://ubuntuforums.org • Search like you would on Google • Create an account and ask your question, include as much info as possible in your request. Mailing List: https://lists.ubuntu.com/mailman/listinfo/ubuntu-users • Ask your question (and try to observe proper etiquette http://www.ubuntu.com/support/community/mailinglists/etiquette) Internet Relay Chat: irc.ubuntu.com #ubuntu • Connect with a chat client: empathy, pidgin, xchat, irssi • For more, see: https://help.ubuntu.com/community/InternetRelayChat Ubuntu California Team: https://wiki.ubuntu.com/CaliforniaTeam CC-BY-SA material from Ubuntu User Day Jan 23, 2010 by Jeremy Pallats ([email protected]) handout written and formatted by Elizabeth Krumbach ([email protected]). -

Securing Decentralized Software Installation and Updates
Securing Decentralized Software Installation and Updates By David Barrera A thesis submitted to the Faculty of Graduate Studies and Research in partial fulfilment of the requirements for the degree of DOCTOR OF PHILOSOPHY in Computer Science Carleton University Ottawa, Ontario, Canada c 2014, David Barrera Abstract Software installation and updates have become simpler for end users in recent years. The commoditization of the internet has enabled users to obtain more software than ever before from more developers than ever before. Additionally, software installation now requires less input from users, allowing installation with merely a single click or tap. At the same time, different software installation models with varying levels of security, usability and freedom have emerged. In centralized environments, available software is limited by an authority, whereas decentralized environments allow users and developers to interact freely. Decentralized software installation ecosystems pose the most significant security challenges due to the lack of centralized control. In this thesis we identify, through the systematic evaluation of prominent systems, limitations in the way operating systems provide security guarantees (including ver- ification of integrity and authentication, and establishment of trust) in decentral- ized software installation environments. We address these limitations by designing tools and protocols that help secure software installation and updates at each of the three installation stages (software discovery, initial install and updates, and enforc- ing security policies). Specifically, we propose a cryptographically verifiable protocol for developers to delegate digital signature privileges to other certificates (possibly owned by other developers) without requiring a centrally trusted public key infras- tructure. Our proposal allows trust to be delegated during software updates without user involvement. -

Pdf/Acyclic.1.Pdf
tldr pages Simplified and community-driven man pages Generated on Sun Sep 26 15:57:34 2021 Android am Android activity manager. More information: https://developer.android.com/studio/command-line/adb#am. • Start a specific activity: am start -n {{com.android.settings/.Settings}} • Start an activity and pass data to it: am start -a {{android.intent.action.VIEW}} -d {{tel:123}} • Start an activity matching a specific action and category: am start -a {{android.intent.action.MAIN}} -c {{android.intent.category.HOME}} • Convert an intent to a URI: am to-uri -a {{android.intent.action.VIEW}} -d {{tel:123}} bugreport Show an Android bug report. This command can only be used through adb shell. More information: https://android.googlesource.com/platform/frameworks/native/+/ master/cmds/bugreport/. • Show a complete bug report of an Android device: bugreport bugreportz Generate a zipped Android bug report. This command can only be used through adb shell. More information: https://android.googlesource.com/platform/frameworks/native/+/ master/cmds/bugreportz/. • Generate a complete zipped bug report of an Android device: bugreportz • Show the progress of a running bugreportz operation: bugreportz -p • Show the version of bugreportz: bugreportz -v • Display help: bugreportz -h cmd Android service manager. More information: https://cs.android.com/android/platform/superproject/+/ master:frameworks/native/cmds/cmd/. • List every running service: cmd -l • Call a specific service: cmd {{alarm}} • Call a service with arguments: cmd {{vibrator}} {{vibrate 300}} dalvikvm Android Java virtual machine. More information: https://source.android.com/devices/tech/dalvik. • Start a Java program: dalvikvm -classpath {{path/to/file.jar}} {{classname}} dumpsys Provide information about Android system services.