Apple Computer Mac OS X Version 10.3.6
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Version 7.8-Systemd
Linux From Scratch Version 7.8-systemd Created by Gerard Beekmans Edited by Douglas R. Reno Linux From Scratch: Version 7.8-systemd by Created by Gerard Beekmans and Edited by Douglas R. Reno Copyright © 1999-2015 Gerard Beekmans Copyright © 1999-2015, Gerard Beekmans All rights reserved. This book is licensed under a Creative Commons License. Computer instructions may be extracted from the book under the MIT License. Linux® is a registered trademark of Linus Torvalds. Linux From Scratch - Version 7.8-systemd Table of Contents Preface .......................................................................................................................................................................... vii i. Foreword ............................................................................................................................................................. vii ii. Audience ............................................................................................................................................................ vii iii. LFS Target Architectures ................................................................................................................................ viii iv. LFS and Standards ............................................................................................................................................ ix v. Rationale for Packages in the Book .................................................................................................................... x vi. Prerequisites -

Oracle Solaris Security for Developers Guide • September 2010 Contents
Oracle® Solaris Security for Developers Guide Part No: 816–4863–16 September 2010 Copyright © 2004, 2010, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related software documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, the following notice is applicable: U.S. GOVERNMENT RIGHTS Programs, software, databases, and related documentation and technical data delivered to U.S. Government customers are “commercial computer software” or “commercial technical data” pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, duplication, disclosure, modification, and adaptation shall be subject to the restrictions and license terms setforth in the applicable Government contract, and, to the extent applicable by the terms of the Government contract, the additional rights set forth in FAR 52.227-19, Commercial Computer Software License (December 2007). Oracle America, Inc., 500 Oracle Parkway, Redwood City, CA 94065. -

Open Directory Administration for Version 10.5 Leopard Second Edition
Mac OS X Server Open Directory Administration For Version 10.5 Leopard Second Edition Apple Inc. © 2008 Apple Inc. All rights reserved. The owner or authorized user of a valid copy of Mac OS X Server software may reproduce this publication for the purpose of learning to use such software. No part of this publication may be reproduced or transmitted for commercial purposes, such as selling copies of this publication or for providing paid-for support services. Every effort has been made to make sure that the information in this manual is correct. Apple Inc., is not responsible for printing or clerical errors. Apple 1 Infinite Loop Cupertino CA 95014-2084 www.apple.com The Apple logo is a trademark of Apple Inc., registered in the U.S. and other countries. Use of the “keyboard” Apple logo (Option-Shift-K) for commercial purposes without the prior written consent of Apple may constitute trademark infringement and unfair competition in violation of federal and state laws. Apple, the Apple logo, iCal, iChat, Leopard, Mac, Macintosh, QuickTime, Xgrid, and Xserve are trademarks of Apple Inc., registered in the U.S. and other countries. Finder is a trademark of Apple Inc. Adobe and PostScript are trademarks of Adobe Systems Incorporated. UNIX is a registered trademark of The Open Group. Other company and product names mentioned herein are trademarks of their respective companies. Mention of third-party products is for informational purposes only and constitutes neither an endorsement nor a recommendation. Apple assumes no responsibility with regard to the performance or use of these products. -

Deploying-Zones-11Gr2-Supercluster
An Oracle Technical White Paper November 2012 Best Practices for Deploying Oracle Solaris Zones with Oracle Database 11g on SPARC SuperCluster Best Practices for Deploying Oracle Solaris Zones with Oracle Database 11g on SPARC SuperCluster Introduction ....................................................................................... 1 SPARC SuperCluster Technologies for Database Consolidation ....... 2 SPARC T4-4 Domains in the SPARC SuperCluster ...................... 3 Database Services Within the SPARC SuperCluster ..................... 3 Database Consolidation on the SPARC SuperCluster ................... 4 Oracle Solaris Zones on the SPARC SuperCluster ........................ 4 Best Practices for Deploying Oracle Database 11g Using Oracle Solaris Zones .................................................................................... 6 Choosing the Number of Database Domains ................................. 6 Oracle Solaris Zones ..................................................................... 7 ZFS File System .......................................................................... 11 Zone Deployment Using the ssc_exavm Tool ............................ 11 Operating System Tunable Parameters ....................................... 12 Database Grid Configuration ....................................................... 14 Oracle RAC Configuration ........................................................... 19 Securing the Databases in SPARC SuperCluster ........................ 20 Example Database Consolidation Scenarios -

UNIX System Services Z/OS Version 1 Release 7 Implementation
Front cover UNIX System Services z/OS Version 1 Release 7 Implementation z/OS UNIX overview z/OS UNIX setup z/OS UNIX usage Paul Rogers Theodore Antoff Patrick Bruinsma Paul-Robert Hering Lutz Kühner Neil O’Connor Lívio Sousa ibm.com/redbooks International Technical Support Organization UNIX System Services z/OS Version 1 Release 7 Implementation March 2006 SG24-7035-01 Note: Before using this information and the product it supports, read the information in “Notices” on page xiii. Second Edition (March 2006) This edition applies to Version 1 Release 7 of z/OS (5637-A01), and Version 1, Release 7 of z/OS.e (5655-G52), and to all subsequent releases and modifications until otherwise indicated in new editions. © Copyright International Business Machines Corporation 2003, 2006. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . xiii Trademarks . xiv Preface . .xv The team that wrote this redbook. .xv Become a published author . xvi Comments welcome. xvii Chapter 1. UNIX overview. 1 1.1 UNIX fundamentals . 2 1.1.1 UNIX objectives . 2 1.1.2 What people like about UNIX . 2 1.1.3 What people don’t like about UNIX . 3 1.1.4 UNIX operating system . 3 1.1.5 UNIX file system . 4 1.1.6 Parameter files . 6 1.1.7 Daemons. 6 1.1.8 Accessing UNIX . 6 1.1.9 UNIX standards. 7 1.1.10 MVS and UNIX functional comparison . 8 1.2 z/OS UNIX System Services fundamentals . -

Version 20160304-Systemd
Linux From Scratch Version 20160304-systemd Created by Gerard Beekmans Edited by Douglas R. Reno Linux From Scratch: Version 20160304-systemd by Created by Gerard Beekmans and Edited by Douglas R. Reno Copyright © 1999-2016 Gerard Beekmans Copyright © 1999-2016, Gerard Beekmans All rights reserved. This book is licensed under a Creative Commons License. Computer instructions may be extracted from the book under the MIT License. Linux® is a registered trademark of Linus Torvalds. Linux From Scratch - Version 20160304-systemd Table of Contents Preface .......................................................................................................................................................................... vii i. Foreword ............................................................................................................................................................. vii ii. Audience ............................................................................................................................................................ vii iii. LFS Target Architectures ................................................................................................................................ viii iv. LFS and Standards ............................................................................................................................................ ix v. Rationale for Packages in the Book ................................................................................................................... -

Apple File System Reference
Apple File System Reference Developer Contents About Apple File System 7 General-Purpose Types 9 paddr_t .................................................. 9 prange_t ................................................. 9 uuid_t ................................................... 9 Objects 10 obj_phys_t ................................................ 10 Supporting Data Types ........................................... 11 Object Identifier Constants ......................................... 12 Object Type Masks ............................................. 13 Object Types ................................................ 14 Object Type Flags .............................................. 20 EFI Jumpstart 22 Booting from an Apple File System Partition ................................. 22 nx_efi_jumpstart_t ........................................... 24 Partition UUIDs ............................................... 25 Container 26 Mounting an Apple File System Partition ................................... 26 nx_superblock_t ............................................. 27 Container Flags ............................................... 36 Optional Container Feature Flags ...................................... 37 Read-Only Compatible Container Feature Flags ............................... 38 Incompatible Container Feature Flags .................................... 38 Block and Container Sizes .......................................... 39 nx_counter_id_t ............................................. 39 checkpoint_mapping_t ........................................ -

Z/OS V2R2 Network File System Guide and Reference Contents
z/OS Network File System Guide and Reference Version 2 Release 2 SC23-6883-01 This edition applies to Version 2 Release 2 of z/OS® (5650-ZOS) and to all subsequent releases and modifications until otherwise indicated in new editions. This edition replaces SC23-6883-00. © Copyright IBM Corporation 1991, 2015. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. © Copyright IBM Corp. 1991, 2015 iii iv z/OS V2R2 Network File System Guide and Reference Contents Figures ...............xi Tested servers for the z/OS NFS client .....16 || z/OS NFS client restrictions ........17 Tables ...............xiii WebNFS support ............17 NFS versions with TCP/IP protocols ......18 Internet Protocol version 6 .........19 About this document ........xvii User-specified port range support .......20 Required product knowledge ........xvii Dynamic addressing ...........20 Where to find more information .......xvii 64-bit exploitation ............21 Access to documents ..........xvii Data transfer and conversion ........21 z/OS information ..........xviii Native ASCII support ..........21 Access to softcopy documents on CD-ROM and DVD collections and the Internet ......xix Chapter 2. Creating z/OS conventional How to look up message explanations with LookAt ..............xix MVS data sets ...........23 How to read syntax diagrams ........xx Overriding data set creation attributes .....23 Related protocol specifications .......xxii Preparing to create an MVS file........23 The z/OS -

Oracle Minicluster S7-2 Security Guide
Oracle MiniCluster S7-2 Security Guide Part No: E69475-12 March 2021 Oracle MiniCluster S7-2 Security Guide Part No: E69475-12 Copyright © 2018, 2021, Oracle and/or its affiliates. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error-free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs) and Oracle computer documentation or other Oracle data delivered to or accessed by U.S. Government end users are "commercial computer software" or "commercial computer software documentation" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, the use, reproduction, duplication, release, display, disclosure, modification, preparation of derivative works, and/or adaptation of i) Oracle programs (including any operating system, integrated software, any programs embedded, installed or activated on delivered hardware, and modifications of such programs), ii) Oracle computer documentation and/or iii) other Oracle data, is subject to the rights and limitations specified in the license contained in the applicable contract. -

Mac OS X Server User Management for Version 10.4 Or Later Second Edition
Mac OS X Server User Management For Version 10.4 or Later Second Edition K Apple Computer, Inc. Apple, the Apple logo, AirPort, AppleShare, AppleTalk, © 2006 Apple Computer, Inc. All rights reserved. FireWire, iBook, Keychain, LaserWriter, Mac, Mac OS, Macintosh, PowerBook, and QuickTime are trademarks The owner or authorized user of a valid copy of of Apple Computer, Inc., registered in the U.S. and other Mac OS X Server software may reproduce this countries. Extensions Manager, Finder, and SuperDrive publication for the purpose of learning to use such are trademarks of Apple Computer, Inc. software. No part of this publication may be reproduced or transmitted for commercial purposes, such as selling Adobe and PostScript are trademarks of Adobe Systems copies of this publication or for providing paid-for Incorporated. support services. Java and all Java-based trademarks and logos are Every effort has been made to ensure that the trademarks or registered trademarks of Sun information in this manual is accurate. Apple Computer, Microsystems, Inc. in the U.S. and other countries. Inc., is not responsible for printing or clerical errors. UNIX is a registered trademark in the United States and Apple other countries, licensed exclusively through X/Open 1 Infinite Loop Company, Ltd. Cupertino, CA 95014-2084 408-996-1010 Other company and product names mentioned herein www.apple.com are trademarks of their respective companies. Mention of third-party products is for informational purposes Use of the “keyboard” Apple logo (Option-Shift-K) for only and constitutes neither an endorsement nor a commercial purposes without the prior written consent recommendation. -

Imac G4 17 800 Mhz EMC 1936 Battery Replacement
iMac G4 17 800 MHz EMC 1936 Battery … Guide ID: 5160 - Draft: 2013-09-04 iMac G4 17 800 MHz EMC 1936 Battery Replacement iMac G4/800 17-Inch (Flat Panel) Specs iMac 17" Flat Panel - M8812LL/A - PowerMac4,5 - M6498 - EMC 1936 Written By: mayer This document was generated on 2020-12-01 03:28:38 PM (MST). © iFixit — CC BY-NC-SA www.iFixit.com Page 1 of 5 iMac G4 17 800 MHz EMC 1936 Battery … Guide ID: 5160 - Draft: 2013-09-04 INTRODUCTION Pre-Installed MacOS 9.2.2 & X 10.1.2 Maximum MacOS X 10.4.11 This model is capable of booting in MacOS 9 and using MacOS 9 applications within the MacOS X "Classic" environment. Standard RAM 256 MB Maximum RAM: 1.0 GB RAM Type PC133 SDRAM Min. RAM Speed 10 ns Details: Although Apple's original specifications stated that it shipped with PC100 RAM, Apple later warned that "PC100 RAM is not to be used with iMac (Flat Panel) computers and may create performance and reliability issues". *There is one factory installed memory module in a 168-pin DIMM slot and one 144-pin user- accessible SO-DIMM slot. Standard Hard Drive 60 GB (5400 RPM) Int. HD Interface Ultra ATA/66 Standard Optical 2X "SuperDrive" Standard Disk: None Details: Apple reports that the tray-loading DVD-R/CD-RW SuperDrive "writes DVD-R discs at 2x speed, reads DVDs at 6x speed, writes CD-R discs at 8x speed, writes CD-RW discs at 4x speed, and reads CDs at 24x speed." Also see: What are the capabilities of the optical drive provided by the iMac G4 models? How do you replace or upgrade the optical drive? Standard Modem 56k v.90 Standard Ethernet 10/100Base-T Standard AirPort 802.11b (Optional) Standard Bluetooth None USB Ports 3 (1.1) Firewire Ports: 2 (400) Standard AirPort: 802.11b (Optional) Standard Bluetooth: None PRAM battery 3.6V half-AA TOOLS: T15 Torx Screwdriver (1) This document was generated on 2020-12-01 03:28:38 PM (MST). -
Intrinsic Value AAPL.Numbers
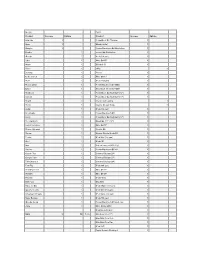
Google Apple Product Success Failure Product Success Failure Adwords 1 PowerBook G4 Titanium 1 Apps 1 iBook (white) 1 Google+ 1 Power Macintosh G4 Quicksilver 1 Reader 1 Server G4 Quicksilver 1 iGoogle 1 iPod (1st gen) 1 Labs 1 iMac G4 15" 1 Wave 1 iBook (14") 1 Video 1 eMac 1 Desktop 1 Xserve 1 Code Search 1 iMac G4 17" 1 Buzz 1 iPod (2nd gen) 1 Picasa Linux 1 Power Macintosh G4 MDD 1 Gears 1 Macintosh Server G4 MDD 1 Notebook 1 PowerBook G4 Aluminum (12") 1 Aarvark 1 PowerBook G4 Aluminum (17") 1 Health 1 Xserve slot loading 1 Picnik 1 Xserve Cluster Node 1 Listen 1 iPod (3rd gen) 1 Bookmarks 1 Power Macintosh G5 1 Lively 1 PowerBook G4 Aluminum (15") 1 Docs Gadgets 1 iBook G4 (12" / 14") 1 Search Timeline 1 iMac G4 20" 1 Picasa Uploader 1 Xserve G5 1 Places 1 Xserve Cluster Node G5 1 Postini 1 iPod Mini (1st gen) 1 Knol 1 iPod+HP 1 Mini 1 AirPort Express (802.11g) 1 Vaccine 1 Power Macintosh G5 FX 1 Classic Plus 1 Cinema Display (20") 1 Google Pack 1 Cinema Display (23") 1 Talk Chatback 1 Cinema Display (30") 1 Fast Flip 1 iPod (4th gen) 1 Friend Connect 1 iMac G5 17" 1 Sidewiki 1 iMac G5 20" 1 Related 1 iPod Photo 1 One Pass 1 Mac Mini 1 Video for Biz 1 iPod Shuffle (1st gen) 1 Apps for Teams 1 iPod Mini (2nd gen) 1 Adsense for Feeds 1 iPod Nano (1st gen) 1 News Badges 1 iPod (5th gen) 1 iGoogle Social 1 Power Macintosh G5 dual core 1 Jaiku 1 iMac (Early 2006) 1 iPod Radio Remote 1 Total 3 39 7.1% MacBook Pro (15") 1 Mac Mini Core Solo 1 Mac Mini Core Duo 1 iPod Hi-Fi 1 Apple Remote Desktop 3 1 MacBook Pro (17") 1 MacBook 1 Shake 4