Pre-Print Version
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Business Informatics
Reģ.Nr.90000068977, Kaļķu iela 1, Rīga, LV-1658, Latvija Tālr.:67089999; Fakss:67089710, e-pasts:[email protected], www.rtu.lvwww.rtu.lv Study programme "Business Informatics" Main attributes Title Business Informatics Identification code DMB0 Education classification code 45481 Level and type Academic Master Study Higher education study field Information Technology, Computer Engineering, Electronics, Telecommunications, Computer Control and Computer Science Head of the study field Agris Ņikitenko Deputy head of the study field Jurģis Poriņš Department responsible Faculty of Computer Science and Information Technology Head of the study programme Mārīte Kirikova Professional classification code The type of study programme Full time, Part time Language English Accreditation 31.05.2013 - 30.06.2023; Accreditation certificate No 2020/38 Volume (credit points) 80.0 Duration of studies (years) Full time studies - 2,0; Part time studies - 2,5 Degree or/and qualification to be obtained Master Degree of Engineering Science in Business Informatics Qualification level to be obtained The 7th level of European Qualifications Framework (EQF) and Latvian Qualifications Framework (LQF) Programme prerequisites Bachelor Degree of Engineering Sciences, or Natural Sciences. or Social Sciences (Economics, Business Administration), or Professional Bachelor Degree in Named Branches of Science Related Fields, or comparable education Description Abstract Business Informatics is a new study program with interdisciplinary features. It was launched by RTU in 2010/11 and accredited on November 23, 2011 for 6 years. The program is developed and implemented in cooperation with the University of Buffalo (USA) and International Business Machines Corporation (IBM). The study program „Business Informatics” (total 120 ECTS) consists of 63 ECTS of Compulsory courses, 21 ECTS of Compulsory Limited Choice courses, 6 ECTS - Free Choice, and 30 ECTS - Master Paper. -

Student Guide to Msc Studies Institute of Informatics, University of Szeged
Student Guide to MSc Studies Institute of Informatics, University of Szeged 2. Contact information Address: Árpád square 2, Szeged, Hungary Postal Address: Institute of Informatics 6701 Szeged, Hungary, P. O. Box 652. Telephone: +36 62 546396 Fax: +36 62 546397 E-mail: [email protected] Url: http://www.inf.u-szeged.hu 2 3. Contents 1. Title page................................................................................................................................1 2. Contact information...............................................................................................................2 3. Contents.................................................................................................................................3 4. Foreword................................................................................................................................4 5. Organization...........................................................................................................................5 6. Main courses..........................................................................................................................6 7. Education...............................................................................................................................8 8. Research...............................................................................................................................10 9. Miscellania...........................................................................................................................11 -

Is the Philosophy of the Information Systems Discipline Informed by the Arts and Humanities?
Article Is the Philosophy of the Information Systems Discipline Informed by the Arts and Humanities? Jan H. Kroeze http://orcid.org/0000-0001-7118-4853 University of South Africa [email protected] Abstract The Information Systems discipline (IS) is usually regarded as a social science because it includes research on human-related aspects of these systems. However, a limited number of IS research outputs use approaches that are typical of the traditional arts and humanities. Little recognition has been given to the arts and humanities-informed stream of the IS discipline. This article aims to clarify the subtle distinctions between these scientific constellations and IS’s place in it. It highlights the cluster of arts, humanities and IS in the inter-linked world of scientific disciplines and makes some recommendations to build further on these accomplishments. Keywords: philosophy of science; Information Systems; arts; humanities General Introduction The Information Systems discipline (IS) is usually regarded as a social science because it does not only study business applications of computer technology, but also the social aspects of these systems, which involve and affect humans (Heeks 2009). It is, therefore, no surprise that it frequently uses the same research approaches too, e.g. quantitative approaches such as surveys, as well as qualitative approaches such as action research, ethnography and case studies. To a more limited extent, however, one also finds research outputs that use constructs that are typical of the traditional humanities methodologies, such as hermeneutics, and even the fine arts. This may be because the social sciences and humanities are often regarded as one homogeneous group of knowledge fields. -

About the Contributors
314 About the Contributors Nijaz Bajgoric is a Professor of Business Computing and Information Technology Management at the School of Economics and Business, University of Sarajevo, Bosnia and Herzegovina. He has a PhD from the University of Sarajevo. He teaches and conducts research in information technol- ogy, business computing, information technology management and operating systems. He has published papers in the following peer-reviewed journals: International Journal of Enterprise Information Systems, Kybernetes, Information Management and Computer Security, Information Systems Management, Industrial Management and Data Systems, International Journal of Production Research, European Journal of Operational Research, International Journal of Agile Management Systems, Journal of Con- current Engineering, International Journal of Agile Manufacturing and has authored and co-authored chapters in the edited books published by: Elsevier Science, Kluwer Academic Publishers, CRC Press, and Auerbach Publications. His current areas of research include continuous computing technologies, business continuity, enterprise information systems, and information technology management. * * * Dr. Mehmet Aktas received his PhD in Computer Science from Indiana University in 2007. During his graduate studies, he worked as a researcher in Community Grids Laboratory of Indiana University in various research projects for six years. During this time period, Dr. Aktas has also worked for a num- ber of prestigious research institutions ranging from NASA Jet Propulsion Laboratory to Los Alamos National Laboratory in various projects. Before joining the Indiana University, Dr. Aktas attended Syra- cuse University where he received an MS Degree in Computer Science and taught undergraduate-level computer science courses. He is currently working as a senior researcher in Information Technologies Institute of TUBITAK-Marmara Research Center. -

VR-BPMN: Visualizing BPMN Models in Virtual Reality
VR-BPMN: Visualizing BPMN Models in Virtual Reality Roy Oberhauser1[0000-0002-7606-8226], Camil Pogolski1, and Alexandre Matic2 Computer Science Dept., Aalen University, Aalen, Germany 1 {roy.oberhauser, camil.pogolski}@hs-aalen.de 2 [email protected] Abstract. One impact of the digital transformation of industry is an increasing automation of business processes (BPs) and the accompanying need for busi- ness process modeling (BPM) and comprehension. The subsequent increased number of processes and process variants to cover all cases, their deeper inte- gration with information services, and additional process structural complexity affects comprehensibility. While virtual reality (VR) has made inroads in other domains and become readily accessible as a graphical interface alternative, its potential for addressing upcoming BPM comprehension challenges has not been sufficiently explored. This paper contributes a solution for visualizing, navi- gating, interacting with, and annotating business process modeling notation (BPMN) models in VR. An implementation shows its feasibility and an empiri- cal study evaluates the effectiveness, efficiency, and intuitiveness versus alter- native model depiction modes. Keywords: Virtual Reality, Business Process Models, Visualization, BPMN. 1 Introduction The digital transformation sweeping through society affects businesses everywhere, resulting in an increased emphasis on business agility and automation. Business pro- cesses (BPs) or workflows are one significant automation area, evidenced by the $2.7 billion market for Business Process Management Systems (BPMS) (Gartner, 2015). Business process modeling (BPM) is commonly supported with the standardized no- tation BPMN (Business Process Model and Notation) (OMG, 2011) also known as BPMN2. A primary objective of BPMN is to provide a comprehensible process nota- tion to all business stakeholders while providing complex process execution seman- tics. -

Comparing Bachelor Studies in Business Informatics at Universities
Ivanova, V. V.; Kazakova, Elena O.; Lezina, Tatiana A.; Martyanova, Victoria N.; Saltan, Andrey A.; Siebenkäs, Anette; Stelzer, Dirk: Comparing bachelor studies in business informatics at universities in Russia and Germany Parallel title: Sravnenie podchodov k realizacii obrazovatelʹnych programm po napravleniju "biznes-informatika" v Rossii i Germanii Cyrillic title: Сравнение подходов к реализации образовательных программ по направлению "бизнес-информатика" в России и Германии URN: urn:nbn:de:gbv:ilm1-2017200213 Original published in: Vestnik Rossijskogo universiteta druzby narodov : naucnyj zurnal; Serija informazacija obrazovanija. - Moskva : Rossijskij universitet družby narodov, izdatelʹstvo. - (2015), 4, p 123-140. Parallel title: Bulletin of Peoples' Friendship University of Russia : scientific journal; Series informatization of education. - Moscow : Peoples' Friendship University of Russia. Alternative title: RUDN Journal of Informatization in Education. - Moscow : Peoples' Friendship University of Russia. Cyrillic title: Вестник Российского университета дружбы народов. - Серия : Информатизация образования. ISSN (online): 2312-864X URL: http://journals.rudn.ru/informatization-education/article/view/13238 [Visited: 23.03.2017] This work is licensed under a Creative Commons Attribution 4.0 international License. http://creativecommons.org/licenses/by/4.0/ TU Ilmenau | Universitätsbibliothek | ilmedia, 2017 http://www.tu-ilmenau.de/ilmedia COMPARING BACHELOR STUDIES IN BUSINESS INFORMATICS AT UNIVERSITIES IN RUSSIA AND GERMANY V.V. Ivanova, E. Kazakova, T.A. Lezina, V.N. Martyanova, A.A. Saltan Saint Petersburg State University 7-9, Universitetskaya nab., St. Petersburg, Russia, 199034 Anette Siebenkäs, Dirk Stelzer Technische Universität Ilmenau Postfach 10 05 65, Ilmenau, Deutschland, 98684 Business informatics is a relatively young academic discipline. During the last years several efforts have been made to compare the German discipline Wirtschaftsinformatik with the Anglo-American sister discipline information systems. -

Study Program "Business Informatics"
STUDY PROGRAM OF THE FIRST CYCLE STUDIES AT THE FACULTY OF ECONOMICS, UNIVERSITY OF BANJA LUKA STUDY PROGRAM "BUSINESS INFORMATICS" 2018 CONTENTS Introduction ..................................................................................................................................... 3 1. NAME AND GOALS OF THE STUDY PROGRAM BUSINESS INFORMATICS OF UNDERGRADUATE ACADEMIC STUDIES – THE FIRST CYCLE STUDIES ...................... 6 1.1. Foundation of the study program ........................................................................................... 7 1.2. Structure of the study program ............................................................................................... 7 1.3. The purpose of the study program ......................................................................................... 8 2. MODEL OD THE STUDY PROGRAM .................................................................................. 9 3. SCIENTIFIC AREA TO WHICH THE STUDY PROGRAM BELONGS ............................. 9 4. TYPE OF STUDIES AND OUTCOMES OF THE LEARNING PROCESS ........................ 10 4.1. Type of studies ..................................................................................................................... 10 4.2. The outcomes of the learning process .................................................................................. 10 4.3. Students' learning outcomes ................................................................................................. 10 4.4. Professions that students will -

Business Informatics
UNIVERSITY OF DEBRECEN FACULTY OF INFORMATICS BSc degree courses MSc degree courses PhD courses Research Business Informatics BSc Faculty Address: 4028 Debrecen, Kassai út 26. Correspondence: 4010 Debrecen Pf.: 12 Telephone: +36 52 512 - 900 Fax: +36 52 512-996 E-mail: [email protected] Web: www.inf.unideb.hu International Student’s Office Address: 4032 Debrecen Egyetem tér 1, Hungary Correspondence: H-4010 Debrecen P.O. Box 95, Hungary Phone: +36 52 518 655 Fax: +36 52 518 623 E-mail: [email protected] Web: http://englishstudies.sci.unideb.hu University of Debreceni Faculty of Informatics Contents FOREWORD BY THE DEAN 4 UNIVERSITY OF DEBRECEN 5 FACULTY OF INFORMATICS 6 Computer equipment at the Faculty 7 The data network 7 BSC DEGREE COURSES 9 Computer Science 9 Computer Science Engineering 9 Business Informatics 10 Library and Information Science 10 MASTER’S DEGREE COURSES 11 Computer Science 11 Business Informatics 11 Computer Science Engineering 12 Library Information Sciences 12 Teacher – Teacher of Informatics 13 Teacher – Teacher of Library-pedagogy 13 PhD School of Informatics 14 CISCO REGIONAL ACADEMY 15 RESEARCH 17 Periodicals 17 THE BÉLA GYIRES IT LECTURES 18 DEPARTMENTS 19 Department of Applied Mathematics and Probability Theory 19 Department of Informatics Systems and Networks 19 Department of Information Technology 20 Department of Computer Science 20 Department of the Computer Graphics and Image Processing 21 Department of Library Informatics 21 Affiliated Department of ICT Systems Operation 21 BUSINESS INFORMATICS BSC COURSE 22 SUBJECT PROGRAMS 26 THE MAP OF THE CAMPUS 52 PHOTOS 53 ____________________________________________________________________________ 3 University of Debreceni Faculty of Informatics Foreword by the Dean Dear Reader, We are introducing here the Faculty of Informatics at the University of Debrecen. -

“Business Informatics” Education: Towards Apprenticeship and Interdisciplinarity Jerzy J
Proceedings of Informing Science & IT Education Conference (InSITE) 2013 Novelties in “Business Informatics” Education: Towards Apprenticeship and Interdisciplinarity Jerzy J. Korczak and Mieczyslaw L. Owoc University of Economics, Wroclaw, Poland [email protected]; [email protected] Abstract This paper presents the development of a study program in “Business Informatics” at the Wroclaw University of Economics, Poland and its educational evolution since the InSITE2011. Gathering experiences and having strong cooperation with software companies, we decided to redesign our program including two aspects of education: practice and compacting courses into more problem oriented topics. Additionally, education effects are discussed in the National Framework of Qualification context. The new structure of subjects taught and the organization of the curriculum for bachelor’s and master’s levels are detailed. The authors discuss also potential direction of professional education based on participation of partners interested in our graduates: IBM Poland, Oracle Poland, SAP Poland, and Volvo. Examples of common initiatives with our partners are presented. Keywords: teaching model of business informatics, bachelor’s and master’s studies in business informatics, practice orientation, curriculum of business informatics Introduction The curriculum of "Business Informatics" (BI) at the Wrocław University of Economics, Poland, was presented during the conference InSITE in Novi Sad (Korczak et al., 2011). In 2011 we be- gan to work on an English edition of the Bachelor diploma in Business Informatics. In designing the program of study, we have tried to implement the standards and best European practices, so that on the one hand we meet the needs of the enterprises and institutions, and on the other hand we stimulate the mobility of students and teaching staff. -

Knowledge Management in E-Learning Practices
TOJET: The Turkish Online Journal of Educational Technology – April 2012, volume 11 Issue 2 KNOWLEDGE MANAGEMENT IN E-LEARNING PRACTICES Yücel Yılmaz Marmara University, Department of Business Informatics, Istanbul, Turkey [email protected] ABSTRACT Thanks to extension of IT in educational activities, the difficulties based on time and space are disappearing and the management and the execution of these activities can be implemented more effectively and beneficially. Even though there are significant developments about e-learning both in academic and professional platforms, there are some main questions that must be considered like: How can e-learning and knowledge management be integrated? Do these present e-learning systems fulfill the requirements of knowledge management? Are provided facilities from these systems being utilized in knowledge management accurately? In this paper, firstly e-learning, and then knowledge and knowledge management concepts are considered with their major points. In the next section it is considered that how e-learning systems can be integrated with knowledge management; under the subjects of knowledge management models, system features, and requirements of knowledge management. Keywords: E-learning, e-learning systems, knowledge management, integration. INTRODUCTION Today, organizations need to develop fast and accurate responses to changes which increase their scope and speed day by day. In this context, knowledge management and educational activities gain increasingly importance for all kinds of institutions, not just business enterprises. In the knowledge age we are living, an organizational structure which is flexible, can fulfill customer demands through the effective use of resources, and protect and improve competitiveness, can only be created on the basis of an approach, which regard knowledge as the most basic and strategic factor. -
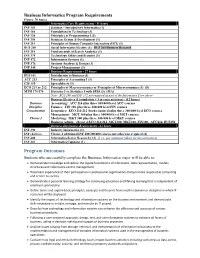
Business Informatics Program Requirements Program Outcomes
Business Informatics Program Requirements Hours: 70 hours Informatics Core Requirements - 31 hours INF 101 Seminar – Introductory Informatics (1) INF 110 Foundations in Technology (3) INF 120 Principles of Programming I (3) INF 230 Database Design & Development (3) INF 215 Principles of Human Computer Interaction (HCI) (3) BUS 260 Social Informatics Elective (3): BUS 260 Business Research INF 218 Fundamentals of Search Analytics (3) INF 374 Technology Ethics and Security (3) INF 372 Information Systems (3) INF 376 Systems Analysis & Design (3) INF 348 Project Management (3) Business Requirements - 27 hours BUS 101 Introduction to Business (3) ACC 213 Principles of Accounting I (3) CIS 135 Spreadsheets (3) ECO 211 or 212 Principles of Macroeconomics or Principles of Microeconomics (3) (S) MTH 174/176 Statistics I or Statistics I with SPSS (3) (MA) Note: BUS 260 and INF 372 are required as part of the Informatics Core above Business Electives (1 foundation + 3 in concentration) – (12 hours) Business Accounting: ACC 214 plus three 300/400 level ACC courses Discipline Finance: FIN 300 plus three 300/400 level FIN courses Concentration Economics: ECO 211/212 (both required) plus three 300/400 level ECO courses Management: MGT 300 plus three 300/400 level MGT courses Choose 1 Marketing: MKT 300 plus three 300/400 level MKT courses Business Admin: choose 4 ECO 211/212, MGT300, MKT300, FIN300, ACC214, BUS352 Business Informatics Requirements –12 hours INF 390 Industry Informatics (3) INF electives Choose 2 additional INF 200/300/400 courses not otherwise required (6) INF 400 Informatics Senior Research (1,1) (1 cr. per semester taken in two semesters) INF 401 Informatics Capstone (1) Program Outcomes Students who successfully complete the Business Informatics major will be able to: Demonstrate knowledge and skills in the logical foundations of informatics, data representation, models, structures and informatics‐centric management. -

Decision Making About Enterprise Architecture Using 3D Visualization in Augmented Reality
Proceedings of the 52nd Hawaii International Conference on System Sciences | 2019 Let’s Get in Touch - Decision Making about Enterprise Architecture Using 3D Visualization in Augmented Reality Kevin Rehring Malte Greulich University of Duisburg-Essen University of Duisburg-Essen [email protected] [email protected] Laurenz Bredenfeld Frederik Ahlemann University of Duisburg-Essen University of Duisburg-Essen [email protected] [email protected] Abstract business processes) and time-specific descriptions (i.e. as-is versus to-be) of the organizations [41, 42]. Hence, Making informed decisions about historically grown EAs offer a consistent basis for decision-making about, and often complex business and Information for instance, business-IT alignment, complexity Technology (IT) landscapes can be particularly reduction, or future planning of organizations [41]. This difficult. Enterprise Architecture Management (EAM) fact-based foundation provides rational arguments addresses this issue by enabling stakeholders to base about EAs [21] and therefore facilitates better and their decisions on relevant information about the timely decision-making for a variety of EA stakeholders organization’s current and future Enterprise [2]. EAs can be made visual as i.e. texts, matrix views, Architectures (EAs). However, visualization of EA is layer perspectives, bar charts, or pie charts [37], which often confronted with low usefulness perceptions. support decision-makers’ understanding of EA Informed by the cognitive fit theory (CFT), we argue descriptions [29]. The establishment, maintenance, and that decision-makers benefit from interacting with EA development of EAs and corresponding EA visualizations using Augmented Reality (AR), because it visualizations are the main outcomes of Enterprise enables a consistent task-related mental representation Architecture Management (EAM) [2, 3].