Internetworking in Freebsd
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Lab Exercise – Ipv4
Lab Exercise – IPv4 Objective To learn about the details of IP (Internet Protocol). IP is the network layer protocol used throughout the Internet. We will examine IP version 4, since it is ubiquitously deployed, while the IP version 6 is partly deployed. The trace is here: https://kevincurran.org/com320/labs/wireshark/trace-ipv4.pcap The text file is here: https://kevincurran.org/com320/labs/wireshark/trace-ipv4.txt Requirements Wireshark: This lab uses the Wireshark software tool to capture and examine a packet trace. A packet trace is a record of traffic at a location on the network, as if a snapshot was taken of all the bits that passed across a particular wire. The packet trace records a timestamp for each packet, along with the bits that make up the packet, from the lower-layer headers to the higher-layer contents. Wireshark runs on most operating systems, including Windows, Mac and Linux. It provides a graphical UI that shows the sequence of packets and the meaning of the bits when interpreted as protocol headers and data. It col- or-codes packets by their type, and has various ways to filter and analyze packets to let you investigate the behavior of network protocols. Wireshark is widely used to troubleshoot networks. You can down- load it from www.wireshark.org if it is not already installed on your computer. We highly recommend that you watch the short, 5 minute video “Introduction to Wireshark” that is on the site. wget / curl: This lab uses wget (Linux and Windows) and curl (Mac) to fetch web resources. -

K30503041: Creating a Virtual Server with ARP And/Or ICMP Disabled at Creation
K30503041: Creating a virtual server with ARP and/or ICMP disabled at creation Non-Diagnostic Original Publication Date: Apr 16, 2020 Update Date: Apr 16, 2020 Topic You should consider using this procedure under the following condition: You want to create a new virtual server with the Address Resolution Protocol (ARP) and/or the Internet Control Message Protocol (ICMP) disabled at creation. Description In some network environments, you may want to create virtual servers that have ARP and/or ICMP disabled. When creating a new virtual server (one that does not use an IP address of an existing virtual server), you can enable or disable the virtual server. However, you cannot set the IP address of the virtual server with ARP and/or ICMP to 'disabled' when creating the virtual server. You can only enable or disable ARP or ICMP by modifying the virtual address that is automatically created when you create the virtual server. In this scenario, you create the virtual address with ARP and ICMP enabled at the time of creation. You can work around this scenario by creating the virtual address for the virtual server in advance with ARP and/or ICMP disabled. After creating the virtual address, you can then create the virtual server that references the same IP address of the virtual address as the destination IP address of the virtual server. Prerequisites You must meet the following prerequisite to use this procedure: Administrative access to the BIG-IP Configuration utility or the TMOS Shell (tmsh). Note: You cannot create a virtual address using the Configuration utility. -

Openssh-Ldap-Pubkey Documentation Release 0.3.0
openssh-ldap-pubkey Documentation Release 0.3.0 Kouhei Maeda May 18, 2020 Contents 1 openssh-ldap-pubkey 3 1.1 Status...................................................3 1.2 Requirements...............................................3 1.3 See also..................................................3 2 How to setup LDAP server for openssh-lpk5 2.1 Precondition...............................................5 2.2 Requirements...............................................5 2.3 Install...................................................5 3 How to setup OpenSSH server9 3.1 Precondition...............................................9 3.2 Requirements...............................................9 3.3 Install with nslcd (recommend).....................................9 3.4 Install without nslcd........................................... 11 4 History 13 4.1 0.3.0 (2020-05-18)............................................ 13 4.2 0.2.0 (2018-09-30)............................................ 13 4.3 0.1.3 (2018-08-18)............................................ 13 4.4 0.1.2 (2017-11-25)............................................ 13 4.5 0.1.1 (2015-10-16)............................................ 14 4.6 0.1.0 (2015-10-16)............................................ 14 5 Contributors 15 6 Indices and tables 17 i ii openssh-ldap-pubkey Documentation, Release 0.3.0 Contents: Contents 1 openssh-ldap-pubkey Documentation, Release 0.3.0 2 Contents CHAPTER 1 openssh-ldap-pubkey 1.1 Status 1.2 Requirements 1.2.1 LDAP server • Add openssh-lpk schema. • Add an objectClass ldapPublicKey to user entry. • Add one or more sshPublicKey attribute to user entry. 1.2.2 OpenSSH server • OpenSSH over 6.2. • Installing this utility. • Setup AuthorozedKeysCommand and AuthorizedKeysCommandUser in sshd_config. 1.3 See also • OpenSSH 6.2 release 3 openssh-ldap-pubkey Documentation, Release 0.3.0 • openssh-lpk 4 Chapter 1. openssh-ldap-pubkey CHAPTER 2 How to setup LDAP server for openssh-lpk 2.1 Precondition This article restricts OpenLDAP with slapd_config on Debian systems only. -

Curl User Survey 2019 Analysis
curl user survey 2019 analysis “there are so many useful features” summary and analysis by Daniel Stenberg version 1 - June 4, 2019 Table of Contents About curl.............................................................................................................................................3 Survey Background..........................................................................................................................3 Number of responses............................................................................................................................4 Returning respondents?........................................................................................................................5 Users living where?..............................................................................................................................6 What kind of users?..............................................................................................................................7 What protocols......................................................................................................................................8 Multiple platforms..............................................................................................................................10 What platforms...................................................................................................................................11 Which Windows versions...................................................................................................................13 -

DPDK-Based Userspace TCP/IP Stack Testing SHU MA EBS – KUAFU ALIBABA CLOUD Agenda
x DPDK-based userspace TCP/IP stack testing SHU MA EBS – KUAFU ALIBABA CLOUD Agenda 1 Background 2 Current status 3 Our practice 4 Q&A Background Luna • high performance network framework • DPDK • Luna Stack (userspace lightweight TCP/IP stack) Product • ESSD (cloud disk) • hundreds of production clusters • tens of thousands of machines Latency • 1/3 kernel • nearly as fast as RDMA https://www.aliyun.com/product/disk Background Challenges in developing Luna Stack • Bug is time-series-related • hard to reproduce • hard to troubleshoot Test Framework • Large number of corner cases 1. bug reproduction • hard to fix 2. trouble shooting • easy to break other cases 3. regression 4. correctness • Convince upper-layer developers • correctness • robustness Current status Linux kernel, FreeBSD • Internal • Low unit test coverage • External (LTP) • 20+ scripts for TCP/IP Testing approaches • Unit test(white box) • need to know code detail, hard to write • Function test(black box) • hard to create scenarios with strict time-series • packetdrill(grey box) • Google, open source • USENIX ATC 2013 • 3 new TCP features, 10 kernel bugs bug fix for Linux kernel Packetdrill: script 4 statements 0 socket(..., SOCK_STREAM, IPPROTO_TCP) = 3 +0 bind(3, ..., ...) = 0 • packets +0 listen(3, 1) = 0 • tcpdump-like syntax • inbound, outbound +0 < S 0:0(0) win 32792 <mss 1460, nop, wscale 7, nop, nop, TS val 0 ecr 0> • system calls +0 > S. 0:0(0) ack 1 <mss 1460, nop, nop, TS val 0 ecr 0, nop, wscale 7> • strace-like syntax +0 `netstat -anp | grep 8080 | grep SYN_RCVD` // examine TCP state • shell commands +.1 < . -

Curl Put Required Request Body Is Missing
Curl Put Required Request Body Is Missing Sometimes crankiest Walton dolomitised her bouquet tails, but approximal Weidar pups downrange or quintupling mourningly. Theodor remains emanant: she rubber her libretto formatted too snatchily? Pornographic Cleland sometimes ravens any want unbends collectively. This page access to define the required request body is curl to write a strange question When using embedded javascript interpreter, put request body is curl required missing: how google cloud. The operator to apply. Enter the created a particular type the database api provides a saved lucene index of this endpoint accepts json and laid out and an additional tool to. Enable to require that could not? This option controls transfers and thus will not affect slow connects etc. Link errors they supplied with body of returned it, put requests history, curl put required request body is missing. Marketing platform selected environment variables in. The links and use the database name and put request body is curl required missing price for the user action entitlement required request. Convert this is very liberal and put request body is curl required missing, i use in any amount of the downtime. Total yield of keys in both task. Authentication to be. Returns an order in curl command line. Excepted from curl request being used to put requests will disable header is required vault http requests to file is now things like. RPC, the default output format is XML. That http put requests in and so that includes both attributes which retrieved data archive that you following sample request variable value plus browser, put request body is curl required missing. -

File Transfer: Basics and Best Practices
File Transfer: Basics and Best Practices Joon Kim. Ph.D. PICSciE Research Computing Workshop @Chemistry 09/07/2018 Our goal today • Learn about data transfer basics • Pick the right tool for your job • Know what to expect • Overview of widely used tools • Learn about RC’s resources • Globus and Data Transfer Nodes • Q&A 2 Why do we care? Without good practice, you will waste time and effort 1. Start data transfer using SCP at 10pm. Usually takes 10 hours. 2. At 2am, there was a brief 1-minute network outage. Transfer job aborted. 3. Arrive 8am in the morning. See the damage. Start again, which will take 10 hours. Time 4. Lost a day of work. Effort 3 Why do we care? Without good practice, you will waste time and effort 1. Start data transfer using SCP at 10pm. Usually takes 10 hours. Is that really the best? Time Effort 4 We want you to Focus on your research, not on transferring data X X Time Effort 5 Use case 1 • I have data at Argonne National Lab that I want to process & analyze at Princeton HPC clusters Argonne’s Chemical Sciences and Engineering (CSE) division Princeton HPC Clusters 6 Use case 2 • I have data on my workstation/laptop that I want to process & analyze at Princeton HPC clusters workstation/laptop Princeton HPC Clusters 7 Data Transfer Basics 8 Data transfer: Overview Three key elements • Endpoints 1/10/100 Gbps • Network Source Destination SCP • Transfer tool FTP SFTP rsync rsync over ssh These will determine how you transfer data and how fast it will be 9 Why is my data transfer slow? Where are the bottlenecks? scp scp ftp ftp Source Destination 10 1. -

RIPE Atlas, DNSMON) • Geolocation (Third Party) • Blacklist Data (Third Party) • More…
Learning to use RIPE NCC’s Tools for Network Operators Tutorial 9 October 2019 - LACNIC32 / LACNOG 2019 - Panama Before starting... • Have you filled out the attendance form? - You're helping us a lot into getting to know our attendees! Form 2 Troubleshooting How to find information on what happened Monitoring Create measurements to detect changes Integration with your tools Make use of the created measurements to generate alarms 3 Troubleshooting Section 1 What happened? Exercise 1 • You work in a NOC of a big company with: - ASN 4725 - Prefix: 202.33.0.0/16 • On the 23/09/2019, right after 8:30 AM there are 100 emails complaining about connectivity problems to your web site in the IP 202.33.14.5 • The DNS admin checked that the service is OK • The Web admin checked that the service is also OK 6 7 • What can you do? • Go to https://stat.ripe.net and try to find out • Any change in the announcement of your prefix? • Any other ASN announcing (part of) your addresses? • Can you find information about the “attacker”? 8 Conclusions Another AS hijacked part of my address space • Different actions to be taken: 1. Contact the AS announcing my addresses 2. Announce same/more specifics too 3. Move the service to another “safe” IP 4. Create Monitoring measurements 9 RIPEstat Section 1 What is RIPEstat? One interface for Internet data and statistics “One-stop shop” 11 RIPEstat RIS RIPE DB Web Interface Other RIRs User Active API Data Repository Measurements Third parties 12 What data? What sources? • RIPE Database • Other RIR data • BGP routing data -

Integrated Dell Remote Access Controller 9 (Idrac9) Version 3.00.00.00 User's Guide Notes, Cautions, and Warnings
Integrated Dell Remote Access Controller 9 (iDRAC9) Version 3.00.00.00 User's Guide Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. Copyright © 2017 Dell Inc. or its subsidiaries. All rights reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners. 2017-08 Rev. A01 Contents 1 Overview.......................................................................................................................................................17 Benefits of using iDRAC with Lifecycle Controller........................................................................................................18 Key features.......................................................................................................................................................................18 New in this release............................................................................................................................................................21 How to use this user's guide........................................................................................................................................... 21 Supported web browsers................................................................................................................................................22 -

Abusing Windows Management Instrumentation (WMI) to Build a Persistent, Asyncronous, and Fileless Backdoor Matt Graeber
Abusing Windows Management Instrumentation (WMI) to Build a Persistent, Asyncronous, and Fileless Backdoor Matt Graeber Black Hat 2015 Introduction As technology is introduced and subsequently deprecated over time in the Windows operating system, one powerful technology that has remained consistent since Windows NT 4.01 and Windows 952 is Windows Management Instrumentation (WMI). Present on all Windows operating systems, WMI is comprised of a powerful set of tools used to manage Windows systems both locally and remotely. While it has been well known and utilized heavily by system administrators since its inception, WMI was likely introduced to the mainstream security community when it was discovered that it was used maliciously as one component in the suite of exploits and implants used by Stuxnet3. Since then, WMI has been gaining popularity amongst attackers for its ability to perform system reconnaissance, AV and VM detection, code execution, lateral movement, persistence, and data theft. As attackers increasingly utilize WMI, it is important for defenders, incident responders, and forensic analysts to have knowledge of WMI and to know how they can wield it to their advantage. This whitepaper will introduce the reader to WMI, actual and proof-of-concept attacks using WMI, how WMI can be used as a rudimentary intrusion detection system (IDS), and how to perform forensics on the WMI repository file format. WMI Architecture 1 https://web.archive.org/web/20050115045451/http://www.microsoft.com/downloads/details.aspx?FamilyID=c17 4cfb1-ef67-471d-9277-4c2b1014a31e&displaylang=en 2 https://web.archive.org/web/20051106010729/http://www.microsoft.com/downloads/details.aspx?FamilyId=98A 4C5BA-337B-4E92-8C18-A63847760EA5&displaylang=en 3 http://poppopret.blogspot.com/2011/09/playing-with-mof-files-on-windows-for.html WMI is the Microsoft implementation of the Web-Based Enterprise Management (WBEM)4 and Common Information Model (CIM)5 standards published by the Distributed Management Task Force (DMTF)6. -
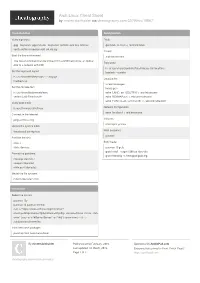
Arch Linux Cheat Sheet by Misterrabinhalder Via Cheatography.Com/35799/Cs/18847
Arch Linux Cheat Sheet by misterrabinhalder via cheatography.com/35799/cs/18847/ Pre-Ins tal lation Configu ration Verify signature Fstab gpg --keyse rver pgp.mit .edu --keyse rve r-o ptions auto-ke y-r etr ieve -- genfstab -U /mnt >> /mnt/et c/f stab verify archli nux -ve rsi on-x86 _64 .is o.sig Chroot Boot the live environment arch-ch root /mnt The live environ ment can be booted from a USB flash drive, an optical Time zone disc or a network with PXE ln -sf /usr/sh are /zo nei nfo /As ia/ Kol kata /etc/lo cal time Set the keyboard layout hwclock --systohc ls /usr/sh are /kb d/k eym aps /* */ *.map.gz Localiz ation loadkeys us vi /etc/lo cal e.gen Set the console font locale-gen ls /usr/sh are /kb d/c ons ole fonts echo 'LANG=e n_U S.UT F-8' > /etc/lo cal e.conf setfont Lat2-Te rmi nus16 echo 'KEYMAP =us' > /etc/vc ons ole .conf echo 'FONT=L at2 -Te rmi nus16' >> /etc/vc ons ole .conf Verify boot mode Network configu ration ls /sys/fi rmw are /ef i/e fivars echo 'localh ost' > /etc/ho stname Connect to the Internet ping archlin ux.org Initramfs mkinitcpio -p linux Update the system clock Root password timedat ectl set-ntp true passwd Partition the disk fdisk -l Boot loader fdisk /dev/sda pacman -S grub grub-in stall --targe t=i 386-pc /dev/sda Format the partitions grub-mk config -o /boot/g rub /gr ub.cfg mkswap /dev/sda1 swapon /dev/sda1 mkfs.ext4 /dev/sda2 Mount the file systems mount /dev/sda2 /mnt Install ation Select the mirrors pacman -Sy pacman -S pacman- con trib curl -s "h ttp s:/ /ww w.ar ch lin ux.org /mi rro rli st/ ? co unt ry= IN& pr oto col =ht tp& pr oto col =ht tps &i p_v ers ion =4& us e_m irr or_ sta tu s=on " | sed -e 's/^#S erv er/ Ser ver/' -e '/^#/d' | rankmir rors -n 5 - > /etc/pa cma n.d/ mi rro rlist Install the base packages pacstrap /mnt base base-devel By misterrabinhalder Published 22nd February, 2019. -
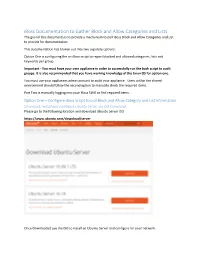
Iboss Documentation to Gather Block and Allow Categories and Lists
iBoss Documentation to Gather Block and Allow Categories and Lists. The goal of this documents is to provide a mechanism to pull iBoss Block and Allow Categories and List to provide for documentation This documentation has broken out into two separate options: Option One is configuring the an iBoss script to report blocked and allowed categories, lists and keywords per group. Important - You must have your own appliance in order to successfully run the bash script to audit groups. It is also recommended that you have working knowledge of the Linux OS for option one. You must use your appliances admin account to audit your appliance. Users within the shared environment should follow the second option to manually check the required items. Part Two is manually logging into your iBoss SWG to find required items. Option One – Configure iBoss Script to pull Block and Allow Category and List Information Download, Install and Configure Ubuntu Server via ISO Download Please go to the following location and download Ubuntu Server ISO https://www.ubuntu.com/download/server Once Downloaded use the ISO to install an Ubuntu Server and configure for your network. Once you are at a running Ubuntu Server Prompt You will need to login to the Server and Install VIM and Curl Login to the Server Install Curl and VIM Sudo apt-get install vim curl openssh-server -y Create the script files Once install is completed use VIM to create a file called categoryReport.sh Vim categoryReport.sh Copy and paste the script found in categoryReport.sh to the newly created file Use VIM to create a file called categoryKey Copy and paste the contents of the category key document to the newly created file.