Digital Technical Journal, Volume 5, Number 2: Multimedia; Application
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Parker Review
Ethnic Diversity Enriching Business Leadership An update report from The Parker Review Sir John Parker The Parker Review Committee 5 February 2020 Principal Sponsor Members of the Steering Committee Chair: Sir John Parker GBE, FREng Co-Chair: David Tyler Contents Members: Dr Doyin Atewologun Sanjay Bhandari Helen Mahy CBE Foreword by Sir John Parker 2 Sir Kenneth Olisa OBE Foreword by the Secretary of State 6 Trevor Phillips OBE Message from EY 8 Tom Shropshire Vision and Mission Statement 10 Yvonne Thompson CBE Professor Susan Vinnicombe CBE Current Profile of FTSE 350 Boards 14 Matthew Percival FRC/Cranfield Research on Ethnic Diversity Reporting 36 Arun Batra OBE Parker Review Recommendations 58 Bilal Raja Kirstie Wright Company Success Stories 62 Closing Word from Sir Jon Thompson 65 Observers Biographies 66 Sanu de Lima, Itiola Durojaiye, Katie Leinweber Appendix — The Directors’ Resource Toolkit 72 Department for Business, Energy & Industrial Strategy Thanks to our contributors during the year and to this report Oliver Cover Alex Diggins Neil Golborne Orla Pettigrew Sonam Patel Zaheer Ahmad MBE Rachel Sadka Simon Feeke Key advisors and contributors to this report: Simon Manterfield Dr Manjari Prashar Dr Fatima Tresh Latika Shah ® At the heart of our success lies the performance 2. Recognising the changes and growing talent of our many great companies, many of them listed pool of ethnically diverse candidates in our in the FTSE 100 and FTSE 250. There is no doubt home and overseas markets which will influence that one reason we have been able to punch recruitment patterns for years to come above our weight as a medium-sized country is the talent and inventiveness of our business leaders Whilst we have made great strides in bringing and our skilled people. -

Analysis of Cell-Based Rnai Screens Comment Michael Boutros*, Lígia P Brás†‡ and Wolfgang Huber†
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Springer - Publisher Connector Open Access Software2006BoutrosetVolume al. 7, Issue 7, Article R66 Analysis of cell-based RNAi screens comment Michael Boutros*, Lígia P Brás†‡ and Wolfgang Huber† Addresses: *Signaling and Functional Genomics, German Cancer Research Center, Im Neuenheimer Feld 580, 69120 Heidelberg, Germany. †EMBL - European Bioinformatics Institute, Cambridge CB10 1SD, UK. ‡Centre for Chemical and Biological Engineering, IST, Technical University of Lisbon, Av. Rovisco Pais, P-1049-001 Lisbon, Portugal. Correspondence: Michael Boutros. Email: [email protected]. Wolfgang Huber. Email: [email protected] reviews Published: 25 July 2006 Received: 27 March 2006 Revised: 7 June 2006 Genome Biology 2006, 7:R66 (doi:10.1186/gb-2006-7-7-r66) Accepted: 25 July 2006 The electronic version of this article is the complete one and can be found online at http://genomebiology.com/2006/7/7/R66 © 2006 Boutros et al.; licensee BioMed Central Ltd. This is an open access article distributed under the terms of the Creative Commons Attribution License (http://creativecommons.org/licenses/by/2.0), which permits unrestricted use, distribution, and reproduction in any medium, provided the original work is properly cited. reports Analysis<p>cellHTS of cell-based is a new method RNAi screens for the analysis and documentation of RNAi screens.</p> Abstract RNA interference (RNAi) screening is a powerful technology for functional characterization of deposited research biological pathways. Interpretation of RNAi screens requires computational and statistical analysis techniques. We describe a method that integrates all steps to generate a scored phenotype list from raw data. -
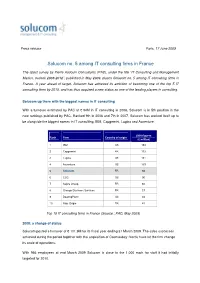
Solucom No. 5 Among IT Consulting Firms in France
Press release Paris, 17 June 2009 Solucom no. 5 among IT consulting firms in France The latest survey by Pierre Audouin Consultants (PAC), under the title “IT Consulting and Management Market, outlook 2008-2012”, published in May 2009, places Solucom no. 5 among IT consulting firms in France. A year ahead of target, Solucom has achieved its ambition of becoming one of the top 5 IT consulting firms by 2010, and has thus acquired a new status as one of the leading players in consulting. Solucom up there with the biggest names in IT consulting With a turnover estimated by PAC at € 94M in IT consulting in 2008, Solucom is in 5th position in the new rankings published by PAC. Ranked 9th in 2006 and 7th in 2007, Solucom has worked itself up to be alongside the biggest names in IT consulting, IBM, Capgemini, Logica and Accenture. 2008 figures Rank Firm Country of origin (€ million) 1 IBM US 194 2 Capgemini FR 173 3 Logica UK 151 4 Accenture US 139 5 Solucom FR 94 6 CSC US 90 7 Sopra Group FR 66 8 Orange Business Services FR 57 9 BearingPoint US 44 10 Atos Origin FR 41 Top 10 IT consulting firms in France (Source : PAC, May 2009) 2008: a change of status Solucom posted a turnover of € 101.9M for its fiscal year ending 31 March 2009. The sales successes achieved during the period together with the acquisition of Cosmosbay~Vectis have let the firm change its scale of operations. With 966 employees at end March 2009 Solucom is close to the 1,000 mark for staff it had initially targeted for 2010. -

A Forensic Analysis of Security Events on System Z, Without the Use Of
16898: A Forensic Analysis of Security Events on System z, Without the Use of SMF Data Brian Marshall Vice President, Research and Development Vanguard Integrity Professionals Monday March 2, 2015 Insert Custom Session QR if Desired. Well, today it’s all about data! So, where is your data today? Wherever you are……. Your data on the move with tablets…. …and oh so many devices! Is your data in the cloud? In the hands of criminals? In the hands of other nations? In the hands of some government agency? We hear it every day! Because the truth is…. You are about to be compromised OR You have already been compromised Maybe you have better security…… The web became significantly more malicious, both as an attack vector and as the primary support element of other trajectories (i.e. social, mobile, e- mail, etc.). Attack Statistics Biggest IT Myths • Hey, it won’t happen to us! • Buy this tool <insert tool here> and it will solve all of your problems. • Let’s get the policy in place and we are good to go. • I passed my IT audit, I must be secure. Their M.O. The cyber spies typically enter targeted computer networks through “spearfishing” attaches, in which company official receives a creatively disguised email and it tricked into clicking on a link or attachment that then opens a secret door for hackers. They can’t get to me, I’m secure. • Hackers go after suppliers to get into larger companies. • Smaller companies tend not to have the funding, staff, or knowledge need to formalize – let alone maintain – more secure policies and procedures all combining to make them the path of least resistance….and the bad guys have discovered this. -

IDC Marketscape Names Accenture a Digital Strategy Leader | Accenture
IDC MarketScape IDC MarketScape: Worldwide Digital Strategy Consulting Services 2021 Vendor Assessment Douglas Hayward IDC MARKETSCAPE FIGURE FIGURE 1 IDC MarketScape Worldwide Digital Strategy Consulting Services Vendor Assessment Source: IDC, 2021 June 2021, IDC #US46766521 Please see the Appendix for detailed methodology, market definition, and scoring criteria. IDC OPINION This study represents the vendor assessment model called IDC MarketScape. This research is a quantitative and qualitative assessment of the characteristics that explain a vendor's current and future success in the digital strategy consulting services marketplace. This study assesses the capabilities and business strategies of 13 prominent digital strategy consulting services vendors. This evaluation is based on a comprehensive framework and a set of parameters expected to be most conducive to success in providing digital strategy consultancy. A significant component of this evaluation is the inclusion of digital strategy consulting buyers' perception of both the key characteristics and the capabilities of these providers. This client input was provided primarily from the vendors' clients, supplemented with a worldwide survey. Key findings include: . Consultancies are getting the basics right. Reference clients that IDC spoke with were impressed by the quality of the people from the leading digital strategy consultancies. On average, reference clients gave consultancies highest scores for people quality, action orientation, and client-specific insight. This indicates that digital strategy consultancies are getting the basics right — they are recruiting smart and empathetic people and are training and developing them well, they are getting to know their clients inside out, and they are producing very useful advice as a result. Clients want to be challenged more than ever by their digital strategy consultants. -

Integrated Virtual Ethernet Adapter Technical Overview and Introduction
Front cover Integrated Virtual Ethernet Adapter Technical Overview and Introduction Unique and flexible up to 10 Gbps Ethernet industry standard virtualizable network solution Hardware accelerated for improved throughput Configurable connections between LPARs and the physical network without the Virtual I/O Server Laurent Agarini Giuliano Anselmi ibm.com/redbooks Redpaper International Technical Support Organization Integrated Virtual Ethernet Adapter Technical Overview and Introduction October 2007 REDP-4340-00 Note: Before using this information and the product it supports, read the information in “Notices” on page v. First Edition (October 2007) This edition applies to IBM AIX Version 6, Release 1, the IBM System p 570, 560, 550, and 520, and the Hardware Management Console Version 7. © Copyright International Business Machines Corporation 2007. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . .v Trademarks . vi Preface . vii The team that wrote this paper . vii Become a published author . viii Comments welcome. viii Chapter 1. Integrated Virtual Ethernet adapter overview . 1 1.1 Introduction . 2 1.2 Advanced hardware features . 3 1.3 Virtualization features . 3 1.3.1 Virtualized logical ports . 3 1.3.2 Physical ports and system integration. 4 1.4 System p virtualization review. 7 1.4.1 Virtualization features and options . 7 1.5 IVE and Virtual I/O Server positioning. 9 Chapter 2. Integrated Virtual Ethernet architecture. 11 2.1 Architecture introduction . 12 2.2 Logical and physical components . 13 2.2.1 IVE logical component introduction. 13 2.2.2 IVE and physical, logical, and port groups . -

Capgemini U.S./ Worldwide | Systems Integrator
Launch Partner Solutions Atos Origin France/ Worldwide | Systems Integrator PARTNERS ARE TALKING Solution Summary ―Being an early adopter of Microsoft innovations will complement the company culture of Atos Origin. Wave • Based on the robust, scalable, and flexible platform that 2010 server-related technologies will improve the includes Microsoft® SharePoint® 2010, Office 2010, and Exchange Server 2010, Atos Origin will develop several productivity and collaboration efforts of our employees in solutions and standard services including Solvency II in their day-to-day work.‖ Motion, Procure to Pay in Motion, and AO Scientific - Francois Gruau, Senior Vice President, Community. Atos Origin's SharePoint portal development Business Development & Innovation, Atos Origin service enables companies to optimally access, manage, and utilize information whilst enabling new ways of communication, connection, and collaboration. • Solvency II in Motion is a project management infrastructure that helps insurance companies to better execute project coordination, document management, About the partner collaboration, and risk management. Procure to Pay in Motion assists purchasing departments through automation Atos Origin is a leading international information and collaborative functionality. The Scientific Community is technology (IT) services company, providing hi-tech the best 50 scientific people from within the organization. They are ―creators of change, making sure that whenever our transactional services, consulting, systems integration, clients choose us, they always get the best solution and managed operations to deliver business outcomes available.‖ globally. Atos Origin, Atos Worldline, and Atos Consulting employ 50,000 people. Atos Origin is the Worldwide Information Technology Partner for the Atos Origin Favorites Olympic Games and has a client base of international Business Connectivity Services | Visio® Services | Advanced companies across all sectors. -

GEO Awards 2009.Pdf
Chief Executive Founding Corporate Sponsors Michael Bendorf, GEO Charles Schwab Board of Directors Morgan Stanley CHAIR: Carine M. Schneider, Global Shares Smith Barney VICE-CHAIR: Janet Cooper, Linklaters Compensation Phil Ainsley, Equiniti Venture Group John Bagdonas, Independent Computershare Juan Bonilla, Cuatrecasas Deutsche Bank June Anne Burke, Baker & McKenzie Alex Brown Lindsey Doud, RBC cees E*TRADE FINANCIAL Jay Foley, Morgan Stanley Smith Barney Global Reward Judith Greaves, Pinsent Masons Plan Group Véronique Japp, BNP Paribas Securities Services HBOS Employee Desiree Klein-Wagner, Allianz Equity Solutions Nancy Mesereau, Fidelity Stock Plan Services Hewitt Bacon Steve Morey, Proctor & Gamble & Woodrow Brian Ruff, Eli Lilly & Company Linklaters Mary Samsa, Seyfarth Shaw LLP Merrill Lynch Barbara Seta, UBS AG Pinsent Masons Sean Trotman, Deloitte PricewaterhouseCoopers James Wulforst, E*TRADE Financial Prudential Financial Corporate Services, Incorporated UBS Financial Advisory Council Services, Inc. CHAIR: Steve Morey, Proctor & Gamble Watson Wyatt Worldwide Karen Beyer, General Electric Provider Council Kelley Garrett, Microsoft Corp. Wendy Jennings, Riverbed Technology, Inc. CHAIR: Jewon Wee, ISP Advisors Yvonne Prang, McDonald’s Deutschland Inc. CO-CHAIR: Paul Stoddart, Brian Ruff, Eli Lilly & Company HBOS Employee Equity Bernice Toy, Cisco Systems, Inc. Solutions Nigel Turner, BP Debbie Veys, Vodafone Group Plc Dominique Welcomme, Vivendi 1442 E. Lincoln Ave. #487 Orange, CA 92865 US TEL +1 714-630-2908 • FAX +1 253-423-8390 • WEB www.globalequity.org ost Innovative M &CreativeD esign TheGEO war AJ� udges The 00 2 9 war ACategories� The 2 009 A war� Categories A�out �he GEO A war�s Welcome �o �heGEO 2009 war s Dear GEO Members, A � The 2009 GEO Awards celebrate outstanding performance in the international employee share plan commu- nity by honoring the impressive achievements of ten companies from around the world. -

CDP Supply Chain 2011
CARBON DISCLOSURE PROJECT CDP Supply Chain 2011 Frances Way Head of Supply Chain [email protected] UK Office +44 (0)20 7415 7095 US Office +1 212 378 2085 2010 CDP SuPPly Chain MeMberS CDP Supply Chain 2011 Accenture Hynix Semiconductor CDP Supply Chain enables businesses to successfully implement supplier engagement strategies around greenhouse gas emissions and risk management in a Acer Inc. IBM changing climate. ASUSTeK Computer Imperial Tobacco Group Banco Bradesco Johnson & Johnson The Carbon Disclosure Project (CDP) is the recognized leader in carbon reporting Bank of America Johnson Controls and has assembled the largest global database of corporate emissions and climate Barclays Juniper Networks change information. Using the same standardized reporting platform, CDP Supply Chain provides world-class data collection so that members can calculate their Baxter International KAO Corporation supply chain emissions and better manage risk. Other benefits include best practice Kellogg Company Becker Underwood sharing and unique cross-sector networking opportunities. Biogen Idec Kimberly-Clark Corporation BT Group L’O r e a l Cadbury Logica Chicony Power Technology Merck & Co. Colgate-Palmolive Company Millipore Coloplast Molson Coors “Logica has been reporting via the CDP since 2006 and ConAgra Foods National Australia Bank in 2009 achieved a leading position in our sector in CO2 Danone National Grid emission reduction and strategy. We use it to drive Dell* Nestle reporting across our organization and as a result have Diebold PepsiCo* saved £10M in our UK organization alone. By supporting EADS* Philips Electronics our suppliers to report via the CDP we want to help them Elopak Reckitt Benckiser to make similar energy, carbon and cost savings. -

Istorie Unix/Linux
1. Introducere & Instalare 1.1 Istorie Unix/Linux Istorie Unix/Linux Anii 60 Bell Laboratories (divizie de cercetare a AT&T) formeaza un consortiu impreuna cu MIT (Massachusetts Institute of Technology) si General Electric pentru a dezvolta un sistem de operare interactiv, multiuser si multi-tasking numit Multics (Multiplexed Information and Computing Service) care sa ruleze pe Mainframe-uri GE-645. Proiectul nu a avut succesul scontat, iar Bell Labs se retrage. Un programator pe nume Ken Thompson nu renunta si continua dezvoltarea proiectului impreuna cu un alt programator pe nume Dennies Ritchie. 1970 Noul proiect este numit Unics (Uniplexed Information and Computing Service). Numele este atribuit de Brian Kernighan, iar mai tarziu este schimbat in UNIX. Sistemul de operare este scris in limbaj de asamblare. 1973 Unix este rescris in C pentru a putea fi portabil (sa ruleze si pe alte masini). Acest lucru a dus la o dezvoltare accelerata. AT&T distribuie noul sistem universitatilor, marilor firme dar si guvernului USA. 1973-1979 Unix-ul este in continuare dezvoltat in cadrul Universitatii Berkeley din California. Printre imbunatatiri sunt shell-ul C, editorul VI precum si alte utilitare necesare. Tot aici este adaugat suportul pentru lucrul in retea. 1980-1983 AT&T lanseaza prima versiune comerciala de UNIX fara a introduce modificarile aduse de Berkeley. 1982 Un programator din cadrul proiectului BSD (Berkeley Software Distribution - Berkeley Unix) impreuna cu cativa colegi de la Stanford University creaza firma SUN - Stanford University Network. Prima lansare de Unix are loc in 1983 si se numeste SunOS. Printre altele sunt introduse NFS (Network File System) care devine un standard. -

Annexes : Installation Du Logiciel R Et Des Packages R
Annexes : Installation du logiciel R et des packages R Pr´e-requis et objectif • Aucun pr´e-requis n’est n´ecessaire.La lecture du chapitre 1 pourrait tou- tefois se r´ev´eler int´eressante. • Ce chapitre d´ecritcomment installer le logiciel R, dans sa version x (rem- placer partout dans le reste de ce document x par le num´ero de la derni`ere version disponible), sous le syst`emed’exploitation Microsoft Windows et aussi comment ajouter des packages suppl´ementaires sous Windows ou sous Linux. SECTION C.1 Installation de R sous Microsoft Windows Commencez par t´el´echarger le logiciel R (fichier R-x-win.exe o`u x est le nu- m´ero de la derni`ereversion disponible) `a l’aide de votre navigateur web usuel `a l’adresse suivante : http://cran.r-project.org/bin/windows/base/ Enregistrez ensuite ce fichier ex´ecutable sur le bureau de Windows puis double- cliquez sur le fichier R-x-win.exe dont voici l’icˆone : . Le logiciel s’installe alors et vous n’avez plus qu’`a suivre les instructions qui s’affichent et `a conserver les options propos´ees par d´efaut. Lorsque l’icˆone est ajout´ee sur le bureau, l’installation peut ˆetre consi- d´er´ee comme termin´ee. 574 Le logiciel R SECTION C.2 Installation de packages suppl´ementaires De nombreux modules (packages ou librairies) suppl´ementaires sont dispo- nibles sur le site internet : http://cran.r-project.org/web/packages/available_packages_by_name. html, ou bien encore ici : http://cran.r-project.org/bin/windows/contrib/, dans le dossier corres- pondant au num´ero x de votre version de R. -

December 2016, Volume 34 No.2
ISSN 0735-1348 Department of Physics, East Carolina University, 1000 East 5th Street, Greenville, NC 27858, USA http://www.ecu.edu/cs-cas/physics/ancient-timeline/ December 2016, Volume 34 No.2 IRSL dating of fast-fading sanidine feldspars from Sulawesi, Indonesia 1 Bo Li, Richard G. Roberts, Adam Brumm, Yu-Jie Guo, Budianto Hakim, Muhammad Ramli, Maxime Aubert, Rainer Grün, Jian-xin Zhao, E. Wahyu Saptomo Bayesian statistics in luminescence dating: The ‘baSAR’-model and its 14 implementation in the R package ‘Luminescence’ Norbert Mercier, Sebastian Kreutzer, Claire Christophe, Guillaume Guérin, Pierre Guibert, Christelle Lahaye, Philippe Lanos, Anne Philippe, and Chantal Tribolo RLumShiny - A graphical user interface for the R Package ‘Luminescence’ 22 Christoph Burow, Sebastian Kreutzer, Michael Dietze, Margret C. Fuchs, Manfred Fischer, Christoph Schmidt, Helmut Brückner Thesis abstracts 33 Bibliography 36 Ancient TL Started by the late David Zimmerman in 1977 EDITOR Regina DeWitt, Department of Physics, East Carolina University, Howell Science Complex, 1000 E. 5th Street Greenville, NC 27858, USA; Tel: +252-328-4980; Fax: +252-328-0753 ([email protected]) EDITORIAL BOARD Ian K. Bailiff, Luminescence Dating Laboratory, Univ. of Durham, Durham, UK ([email protected]) Geoff A.T. Duller, Institute of Geography and Earth Sciences, Aberystwyth University, Ceredigion, Wales, UK ([email protected]) Sheng-Hua Li, Department of Earth Sciences, The University of Hong Kong, Hong Kong, China ([email protected]) Shannon Mahan, U.S. Geological Survey, Denver Federal Center, Denver, CO, USA ([email protected]) Richard G. Roberts, School of Earth and Environmental Sciences, University of Wollongong, Australia ([email protected]) REVIEWERS PANEL Richard M.