The Sensitivity of Coded Mask Telescopes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

AAS Worldwide Telescope: Seamless, Cross-Platform Data Visualization Engine for Astronomy Research, Education, and Democratizing Data
AAS WorldWide Telescope: Seamless, Cross-Platform Data Visualization Engine for Astronomy Research, Education, and Democratizing Data The Harvard community has made this article openly available. Please share how this access benefits you. Your story matters Citation Rosenfield, Philip, Jonathan Fay, Ronald K Gilchrist, Chenzhou Cui, A. David Weigel, Thomas Robitaille, Oderah Justin Otor, and Alyssa Goodman. 2018. AAS WorldWide Telescope: Seamless, Cross-Platform Data Visualization Engine for Astronomy Research, Education, and Democratizing Data. The Astrophysical Journal: Supplement Series 236, no. 1. Published Version https://iopscience-iop-org.ezp-prod1.hul.harvard.edu/ article/10.3847/1538-4365/aab776 Citable link http://nrs.harvard.edu/urn-3:HUL.InstRepos:41504669 Terms of Use This article was downloaded from Harvard University’s DASH repository, and is made available under the terms and conditions applicable to Open Access Policy Articles, as set forth at http:// nrs.harvard.edu/urn-3:HUL.InstRepos:dash.current.terms-of- use#OAP Draft version January 30, 2018 Typeset using LATEX twocolumn style in AASTeX62 AAS WorldWide Telescope: Seamless, Cross-Platform Data Visualization Engine for Astronomy Research, Education, and Democratizing Data Philip Rosenfield,1 Jonathan Fay,1 Ronald K Gilchrist,1 Chenzhou Cui,2 A. David Weigel,3 Thomas Robitaille,4 Oderah Justin Otor,1 and Alyssa Goodman5 1American Astronomical Society 1667 K St NW Suite 800 Washington, DC 20006, USA 2National Astronomical Observatories, Chinese Academy of Sciences 20A Datun Road, Chaoyang District Beijing, 100012, China 3Christenberry Planetarium, Samford University 800 Lakeshore Drive Birmingham, AL 35229, USA 4Aperio Software Ltd. Headingley Enterprise and Arts Centre, Bennett Road Leeds, LS6 3HN, United Kingdom 5Harvard Smithsonian Center for Astrophysics 60 Garden St. -

Space Astronomy in the 90S
Space Astronomy in the 90s Jonathan McDowell April 26, 1995 1 Why Space Astronomy? • SHARPER PICTURES (Spatial Resolution) The Earth’s atmosphere messes up the light coming in (stars twinkle, etc). • TECHNICOLOR (X-ray, infrared, etc) The atmosphere also absorbs light of different wavelengths (col- ors) outside the visible range. X-ray astronomy is impossible from the Earth’s surface. 2 What are the differences between satellite instruments? • Focussing optics or bare detectors • Wavelength or energy range - IR, UV, etc. Different technology used for different wavebands. • Spatial Resolution (how sharp a picture?) • Spatial Field of View (how large a piece of sky?) • Spectral Resolution (can it tell photons of different energies apart?) • Spectral Field of View (bandwidth) • Sensitivity • Pointing Accuracy • Lifetime • Orbit (hence operating efficiency, background, etc.) • Scan or Point What are the differences between satellites? • Spinning or 3-axis pointing (older satellites spun around a fixed axis, precession let them eventually see different parts of the sky) • Fixed or movable solar arrays (fixed arrays mean the spacecraft has to point near the plane perpendicular to the solar-satellite vector) 3 • Low or high orbit (low orbit has higher radiation, atmospheric drag, and more Earth occultation; high orbit has slower preces- sion and no refurbishment opportunity) • Propulsion to raise orbit? • Other consumables (proportional counter gas, attitude control gas, liquid helium coolant) 4 What are the differences in operation? • PI mission vs. GO mission PI = Principal Investigator. One of the people responsible for building the satellite. Nowadays often referred to as IPIs (In- strument PIs). GO = Guest Observer. Someone who just want to use the satel- lite. -

Particle Acceleration in Solar Flares What Is the Link Between Heating and Particle Acceleration?
Energetic Particles in the Solar Atmosphere (X- ray diagnostics) Nicole Vilmer LESIA, Observatoire de Paris, CNRS, UPMC, Université Paris-Diderot The Sun as a Particle Accelerator: First detection of energetic protons from the Sun(1942) (related to a solar flare) First X-ray observations of solar flares (1970) Chupp et al., 1974 First observations of -ray lines from solar flares (OSO7/Prognoz 1972) Since then many more observations With e.g. RHESSI (2002-2018) And also INTEGRAL, FERMI >120000 X-ray flares observed by RHESSI (NASA/SMEX; 2002-2018) But still a limited number of gamma- ray line flares ~30 Solar flare: Sudden release of magnetic energy Heating Particle acceleration X-rays 6-8 keV 25-80 keV 195 Å 304 Å 21 aug 2002 (extreme ultraviolet) 335 Å 15 fev 2011 HXR/GR diagnostics of energetic electrons and ions SXR emission Hot Plasma (7to 8 MK ) HXR emission Bremsstrahlung from non-thermal electrons Prompt -ray lines : Deexcitation lines(C and 0) (60%) Signature of energetic ions (>2 MeV/nuc) Neutron capture line: p –p ; p-α and p-ions interactions Production of neutrons Collisional slowing down of neutrons Radiative capture on ambient H deuterium + 2.2 MeV. line RHESSI Observations X/ spectrum Thermal components T= 2 10 7 K T= 4 10 7 K Electron bremsstrahlung Ultrarelativistic -ray lines Electron (ions > 3 MeV/nuc) Bremsstrahlung (INTEGRAL) SMM/GRS PHEBUS/GRANAT FERMI/LAT observations RHESSI Pion decay radiation(ions > ~300MeV/nuc) Particle acceleration in solar flares What is the link between heating and particle acceleration? Where are the acceleration sites? What is the transport of particles from acceleration sites to X/ γ ray emission sites? What are the characteristic acceleration times? RHESSI How many energetic particles? Energy spectra? Relative abundances of energetic ions? RHESSI Which acceleration mechanisms in solar flares? Shock acceleration? Stochastic acceleration? (wave-particle interaction) Direct Electric field acceleration. -
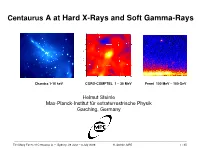
Centaurus a at Hard X-Rays and Gamma Rays
Centaurus A at Hard X-Rays and Soft Gamma-Rays Chandra 1-10 keV CGRO-COMPTEL 1 ± 30 MeV Fermi 100 MeV ± 100 GeV Helmut Steinle Max-Planck-Institut für extraterrestrische Physik Garching, Germany ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- The Many Faces of Centaurus A ± Sydney, 28 June ± 3 July 2009; H. Steinle, MPE 1 / 35 Centaurus A at Hard X-Rays and Soft Gamma-Rays Contents · Introduction · The Spectral Energy Distribution · Properties of the existing measurements in the hard X-ray / soft Gamma-ray regime · Important satellites for this energy / frequency range · Variability of the X-ray / Gamma-ray emission · Two examples of models for the Cen A Spectral Energy Distribution · Problems (features) to be considered when using the hard X-ray / soft Gamma-ray data ± the ªsoft X-ray transient problemº ± the ªSED problemº · Outlook ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- The Many Faces of Centaurus A ± Sydney, 28 June ± 3 July 2009; H. Steinle, MPE 2 / 35 Centaurus A at Hard X-Rays and Soft Gamma-Rays ------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- Introduction In the introductory (ªsetting the stageº) section of the -

The Sensitivity of Coded Mask Telescopes
https://ntrs.nasa.gov/search.jsp?R=20080030340 2019-08-30T05:03:31+00:00Z The sensitivity of coded mask telescopes Gerald K. Skinner Unzversity of Maryland, College Park, AlD 20742, USA &' CRESST &' NASA GSFC, Greenbelt, MD 20771, USA Corresponding author: [email protected] Compiled December 30, 2007 Simple formulae are often used to estimate the sensitivity of coded mask X-ray or gamma-ray telescopes, but t,hese are strictly only applicable if a number of basic assumptions are met. Complications arise, for example, if a grid structure is used to support the mask elements, if the detector spatial resolution is not good enough to completely resolve all the detail in the shadow of the mask or if any of a number of other simplifying conditions are not fulfilled. We derive more general expressions for the Poisson-noise-limited sensitivity of astronomical telescopes using the coded mask technique, noting explicitly in what circumstances they are applicable. The emphasis is on using nomenclature and techniques that result in simple and revealing results. Where no convenient expression is available a procedure is given which allows the calculation of the sensitivity. We consider certain aspects of the optimisation of the design of a coded mask telescope and show that when the detector spatial resolution and the mask to detector separation are fixed, the best source location accuracy is obtained when the mask elements are equal in size to the detector pixels. @ 2007 Optical Society of America OCIS codes: 340.7430, 100.1830, 110.4280. 1. Introduction construction by cross-correlation can be shown (again in specific circumstances, to be discussed below) also to Coded mask telescopes have been widely used in X-ray yield the best possible signal-to-noise ratio, such solu- and gamma-ray astronomy, particularly at those ener- tions have attracted widespread attention. -

Digital Tomographic Imaging with Time-Modulated Pseudorandom Coded Aperture and Anger Camera
DIGITAL TOMOGRAPHIC IMAGING WITH TIME-MODULATED PSEUDORANDOM CODED APERTURE AND ANGER CAMERA Kenneth F. Koral, W. Leslie Rogers, and Glenn F. Knoll The University of Michigan, Ann Arbor, Michigan The properties of a time-modulated pseudo gamma-ray imaging in nuclear medicine. In common random coded aperture with digital reconstruc with the pinhole and converging-hole collimator tion are compared with those of conventional they permit magnification of the object so that de collimators used in gamma-ray imaging. The tector resolution need not limit object resolution. theory of this coded aperture is given and the Contrary to the pinhole and converging collimator, signal-to-noise ratio in an element of the recon however, the field of view is not reduced to a point structed image is shown to depend on the entire as magnification is increased but rather approaches source distribution. Experimental results with a the dimensions of the coded aperture as a limit. preliminary 4 X 4-cm pseudorandom coded Another property peculiar to images formed by aperture and an Anger camera are presented. coded apertures is their insensitivity to detector non These results include phantom and human thy uniformity and noise. The gains with respect to roid images and tomographic images of a rat detector noise or indeed any noise component not bone scan. The experimental realization of the modulated by the aperture may be realized because theoretical advantages of the time-modulated coded apertures can subtend open solid angles that coded aperture gives reason for continuing the are orders of magnitude greater than conventional clinical implementation and further develop apertures. -

Experiments on the Differential Vlbi Measurements with the Former Russian Deep Space Network
EXPERIMENTS ON THE DIFFERENTIAL VLBI MEASUREMENTS WITH THE FORMER RUSSIAN DEEP SPACE NETWORK Igor E. Molotov(1,2,3) (1)Bear Lakes Radio Astronomy Station of Central (Pulkovo) Astronomical Observatory, Pulkovskoye chosse 65/1, Saint-Petersburg, 196140, Russia , E-mail: [email protected] (2)Keldysh Institute of Applied Mathematics, Miusskaja sq. 4, 125047 Moscow, Russia (3)Central Research Institute for Machine Building, 4 Pionerskaya Street, Korolev, 141070, Russia ABSTRACT The differential VLBI technique (delta-VLBI) is applied transforms the signals into video frequencies, which for measuring spacecraft position with accuracy up to 1 then are sampled with 1- or 2-bit quantization, formatted in any standard VLBI format (Mk-4, S2, K-4, mas. This procedure allows to link the sky position of object with the position of close ICRF quasar on the Mk-2) and recorded on magnetic tapes or PC-disks celestial sphere. Few delta-VLBI measurements can together with precise clock using VLBI terminal. All frequency transformations are connected with atomic urgently improve the knowledge of object trajectory in the times of critical maneuvers. frequency standard. The tapes/disks from all radio telescopes of VLBI array are collected at data The Russian Deep Space Network that was based on processing center, where the data are cross-correlated. three large antennas: 70 m in Evpatoria (Ukraine) and The processing is aimed to measure the time delay of Ussuriysk (Far East), and 64 m in Bear Lakes (near emitted wavefront arrival to receiving antennas, and Moscow) arranged the trial delta-VLBI experiments frequency of interference (fringe rate), that contain the with help of four scientific institutions. -

GRANAT/WATCH Catalogue of Cosmic Gamma-Ray Bursts: December 1989 to September 1994? S.Y
ASTRONOMY & ASTROPHYSICS APRIL I 1998,PAGE1 SUPPLEMENT SERIES Astron. Astrophys. Suppl. Ser. 129, 1-8 (1998) GRANAT/WATCH catalogue of cosmic gamma-ray bursts: December 1989 to September 1994? S.Y. Sazonov1,2, R.A. Sunyaev1,2, O.V. Terekhov1,N.Lund3, S. Brandt4, and A.J. Castro-Tirado5 1 Space Research Institute, Russian Academy of Sciences, Profsoyuznaya 84/32, 117810 Moscow, Russia 2 Max-Planck-Institut f¨ur Astrophysik, Karl-Schwarzschildstr 1, 85740 Garching, Germany 3 Danish Space Research Institute, Juliane Maries Vej 30, DK 2100 Copenhagen Ø, Denmark 4 Los Alamos National Laboratory, MS D436, Los Alamos, NM 87545, U.S.A. 5 Laboratorio de astrof´ısica Espacial y F´ısica Fundamental (LAEFF), INTA, P.O. Box 50727, 28080 Madrid, Spain Received May 23; accepted August 8, 1997 Abstract. We present the catalogue of gamma-ray bursts celestial positions (the radius of the localization region is (GRB) observed with the WATCH all-sky monitor on generally smaller than 1 deg at the 3σ confidence level) board the GRANAT satellite during the period December of short-lived hard X-ray sources, which include GRBs. 1989 to September 1994. The cosmic origin of 95 bursts Another feature of the instrument relevant to observa- comprising the catalogue is confirmed either by their lo- tions of GRBs is that its detectors are sensitive over an calization with WATCH or by their detection with other X-ray energy range that reaches down to ∼ 8 keV, the do- GRB experiments. For each burst its time history and main where the properties of GRBs are known less than information on its intensity in the two energy ranges at higher energies. -

Spektr-RG All-Sky Survey Will Be a Major Step Forward for X-Ray Astronomy, Which Celebrated Its 50Th Anniversary a Few Years Ago
CONTEXT The Spektr-RG all-sky survey will be a major step forward for X-ray astronomy, which celebrated its 50th anniversary a few years ago. 1962. Professor Riccardo Giacconi and his team are the first to identify X-ray emission originating from outside the Solar system (a neutron star dubbed Sco X-1). In 2002, he is awarded the Nobel Prize in Physics for this feat and the following discoveries of distant X-ray sources. 1970–1973. The first X-ray all-sky survey in the 2–20 keV energy band is carried out by the Uhuru space observatory (NASA). It discovers more than 300 X-ray sources in our Milky Way and beyond. 1977–1979. An even more sensitive survey is carried out by the HEAO-1 (NASA) space observatory at energies from 0.25 to 180 keV. 1989-1998. Over the initial four years of directed observations, the Granat astrophysical observatory (USSR) observes many galactic and extra-galactic X-ray sources with emphasis on the deep imaging of the Center of our Galaxy in the hard (40-150 keV) and soft (4-20 keV) X-ray ranges. Unique maps of the Galactic Center in X- and gamma- rays are created; black holes, neutron stars and the first microquasar are discovered. Then Granat carries out a sensitive all-sky survey in the 40 to 200 keV energy band. 1990–1999. In its first six months of operation the ROSAT space observatory (DLR, NASA) performs a deep all-sky survey in the soft X-ray band (0.1–2.4 keV). -

Insight-HXMT) Satellite
SCIENCE CHINA Physics, Mechanics & Astronomy • Article • January 2016 Vol.59 No.1: 000000 doi: 10.1007/s11433-000-0000-0 Overview to the Hard X-ray Modulation Telescope (Insight-HXMT) Satellite ShuangNan Zhang1,2*,TiPei Li1,2,3, FangJun Lu1, LiMing Song1, YuPeng Xu1, CongZhan Liu1, Yong Chen1, XueLei Cao1, QingCui Bu1, Ce Cai1,2, Zhi Chang1, Gang Chen1, Li Chen4, TianXiang Chen1, Wei Chen1, YiBao Chen3, YuPeng Chen1, Wei Cui1,3, WeiWei Cui1, JingKang Deng3, YongWei Dong1, YuanYuan Du1, MinXue Fu3, GuanHua Gao1,2, He Gao1,2, Min Gao1, MingYu Ge1, YuDong Gu1, Ju Guan1, Can Gungor1, ChengCheng Guo1,2, DaWei Han1, Wei Hu1, Yan Huang1,Yue Huang1,2, Jia Huo1, ShuMei Jia1, LuHua Jiang1, WeiChun Jiang1, Jing Jin1, YongJie Jin5, Lingda Kong1,2, Bing Li1, ChengKui Li1, Gang Li1, MaoShun Li1, Wei Li1, Xian Li1, XiaoBo Li1, XuFang Li1, YanGuo Li1, ZiJian Li1,2, ZhengWei Li1, XiaoHua Liang1, JinYuan Liao1, Baisheng Liu1, GuoQing Liu3, HongWei Liu1, ShaoZhen Liu1, XiaoJing Liu1, Yuan Liu6, YiNong Liu5, Bo Lu1, XueFeng Lu1, Qi Luo1,2, Tao Luo1, Xiang Ma1, Bin Meng1, Yi Nang1,2, JianYin Nie1, Ge Ou1, JinLu Qu1, Na Sai1,2, RenCheng Shang3,, GuoHong Shen7, XinYing Song1, Liang Sun1, Ying Tan1, Lian Tao1, WenHui Tao1, YouLi Tuo1,2, Chun- Qin Wang7, GuoFeng Wang1, HuanYu Wang1, Juan Wang1, WenShuai Wang1, YuSa Wang1, XiangYang Wen1, BoBing Wu1, Mei Wu1, GuangCheng Xiao1,2, Shuo Xiao1,2, ShaoLin Xiong1, He Xu1, LinLi Yan1,2, JiaWei Yang1, Sheng Yang1, YanJi Yang1, Qibin Yi1, JiaXi Yu1, Bin Yuan7, AiMei Zhang1, ChunLei Zhang1, ChengMo Zhang1, Fan Zhang1, HongMei -

China's Shiyan Weixing Satellite Programme, 2014-2017
SPACE CHRONICLE A BRITISH INTERPLANETARY SOCIETY PUBLICATION Vol. 71 No.1 2018 MONUMENTAL STATUES TO LOCAL LIVING COSMONAUTS CHINA’S SHIYAN WEIXING SPEKTR AND RUSSIAN SPACE SCIENCE SATELLITE PROGRAMME FIRST PICTURES OF EARTH FROM A SOVIET SPACECRAFT REPORTING THE RIGHT STUFF? Press in Moscow During the Space Race SINO-RUSSIAN ISSUE ISBN 978-0-9567382-2-6 JANUARY 20181 Submitting papers to From the editor SPACE CHRONICLE DURING THE WEEKEND of June 3rd and 4th 2017, the 37th annual Sino- Chinese Technical Forum was held at the Society’s Headquarters in London. Space Chronicle welcomes the submission Since 1980 this gathering has grown to be one of the most popular events in the for publication of technical articles of general BIS calendar and this year was no exception. The 2017 programme included no interest, historical contributions and reviews less than 17 papers covering a wide variety of topics, including the first Rex Hall in space science and technology, astronautics Memorial Lecture given by SpaceFlight Editor David Baker and the inaugural Oleg and related fields. Sokolov Memorial Paper presented by cosmonaut Anatoli Artsebarsky. GUIDELINES FOR AUTHORS Following each year’s Forum, a number of papers are selected for inclusion in a special edition of Space Chronicle. In this issue, four such papers are presented ■ As concise as the content allows – together with an associated paper that was not part the original agenda. typically 5,000 to 6,000 words. Shorter papers will also be considered. Longer The first paper, Spektr and Russian Space Science by Brian Harvey, describes the papers will only be considered in Spektr R Radio Astron radio observatory – Russia’s flagship space science project. -

ART-P/Granat Observations of the X-Ray Pulsar 4U0115+634 During the Outburst in February 1990 A
Astronomy Letters, Vol. 26, No. 1, 2000, pp. 1–8. Translated from Pis’ma v Astronomicheskiœ Zhurnal, Vol. 26, No. 1, 2000, pp. 3–12. Original Russian Text Copyright © 2000 by Lutovinov, Grebenev, Sunyaev. ART-P/Granat Observations of the X-ray Pulsar 4U0115+634 during the Outburst in February 1990 A. A. Lutovinov1, S. A. Grebenev1*, and R. A. Sunyaev1, 2 1 Space Research Institute, Russian Academy of Sciences, ul. Profsoyuznaya 84/32, Moscow, 117810 Russia 2 Max-Planck Institut für Astrophysik, Garching, Germany Received April 6, 1999 Abstract—Observations of the transient X-ray pulsar 4U0115+634 with the ART-P telescope aboard the Granat Observatory during the outburst in February 1990 are presented. The source exhibited a strong, regular and irregular variability, including X-ray bursts of duration 300–500 s. Two absorption features were detected in the source’s photon spectrum at ~12 and ~22 keV, which were interpreted as the lines of resonance scattering of its emission at the first and second cyclotron harmonics. The magnetic-field strength B on the neutron-star surface that corresponds to these lines is ~1.3 × 1012 G. The ratio of the line energies slightly differs from the harmonic ratio 1 : 2. Moreover, this ratio and the line energies themselves vary appreciably with phase on a time scale of one pulsation period. The dependence of other spectral parameters for 4U0115+634 on pulse phase is investigated. © 2000 MAIK “Nauka/Interperiodica”. INTRODUCTION erties, they differ markedly from “soft” transients, X-ray novae. In general, its spectrum is well described by a The transient X-ray source 4U0115+634 was dis- power law with a photon index α ~ 0.5 and with an covered by the Uhuru satellite during its outburst in exponential cutoff at energies above 10–15 keV.