General Information
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Security on the Mainframe Stay Connected to IBM Redbooks
Front cover Security on the IBM Mainframe Operating system and application security IBM Security Blueprint and Framework IBM mainframe security concepts Karan Singh Lennie Dymoke-Bradshaw Thomas Castiglion Pekka Hanninen Vincente Ranieri Junior Patrick Kappeler ibm.com/redbooks International Technical Support Organization Security on the IBM Mainframe April 2010 SG24-7803-00 Note: Before using this information and the product it supports, read the information in “Notices” on page ix. First Edition (April 2010) This edition applies to the IBM System z10 Enterprise Class server, the IBM System z10 Business Class server, and Version 1, Release 11, Modification 0 of z/OS (product number 5694-A01). © Copyright International Business Machines Corporation 2010. All rights reserved. Note to U.S. Government Users Restricted Rights -- Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Notices . ix Trademarks . .x Preface . xi The team who wrote this book . xi Now you can become a published author, too! . xii Comments welcome. xii Stay connected to IBM Redbooks . xiii Part 1. Introduction . 1 Chapter 1. Introduction. 3 1.1 IBM Security Framework. 4 1.1.1 People and identity . 5 1.1.2 Data and information. 5 1.1.3 Application and process . 5 1.1.4 Network, server, and endpoint . 5 1.1.5 Physical Infrastructure . 6 1.2 Framework and Blueprint . 7 1.3 IBM Security Blueprint. 7 Chapter 2. Security of the IBM Mainframe: yesterday and today . 13 2.1 Operating systems . 14 2.1.1 z/OS operating system family . 14 2.1.2 z/VM Hypervisor family . -
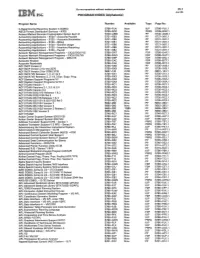
- -:§';'§: ISG PROGRAM INDEX (Alphabetic)
--- - Do not reproduce without written permission PI.1 ------ ---- Jan 84 :: - -:§';'§: ISG PROGRAM INDEX (Alphabetic) Program Name Number Available Type Page No. A Departmental Reporting System II (ADRS) 5796-PLN Now IUP 5796-PLK.1 A8CS Format Distribution Services - 4700 5799-8QZ Now PRPQ 5799-8QZ.1 Access Method Services Cryptographic Option Re1.1.0 5740-AM8 Now PP 5740-AM8.1 Accounting Applications - 5120 - Accounts Payable 5721-X83 Now PP 5721-X81.1 Accounting Applications - 5120 - Accounts Receivable 5721-X84 Now PP 5721-XB1.1 Accounting Applications - 5120 - Billing 5721-XB1 Now PP 5721-XB1.1 Accounting Applications - 5120 - General Ledger 5721-XB6 Now PP 5721-XB1.1 Accounting Applications - 5120 - Inventory Reporting 5721-XB5 Now PP 5721-XB1.1 Accounting Applications - 5120 - Payroll 5721-XB2 Now PP 5721-XB1.1 Account Network Management Programs - CICS/DOS/VS 5798-DAT Now FDP 5798-DAP.1 Account Network Management Programs - CICS/OS/VS 5798-DAQ Now FDP 5798-DAP.1 Account Network Management Program - IMS/VS 5798-DBP Now FDP 5798-DBJ.1 Accounts Payable 5798-CAC Now FDP 5798-BCT.1 Accounts Receivable 5798-CAE Now FDP 5798-BCT.1 ACF/NCP Version 2 5735-XX9 Now PP 5735-XX9.1 ACF/NCP Version 2 for the 3275 5735-XX9 Now PP 5735-XX9.1 ACF/NCP Version 3 for 3705/3725 5667-124 4/84 PP 5667-124.1 ACF/NCP/VS Releases 1, 2, 2.1 & 3 5735-XX1 Now PP 5735-XX1.1 ACF/NCP/VS Releases 2,2.1 & 3 Sys. Supp. Prog. 5735-XX3 Now PP 5735-XX3.1 ACF/System Support Programs V2 5735-XXA Now PP 5735-XXA.1 ACF /System Support Programs V2 R1.1 5735-XXA Now PP 5735-XXA.1 -

Rocket Model 204 System Manager's Guide
Rocket Model 204 System Manager’s Guide Version 7 Release 4.0 May 2012 204-0704-SM-01 Notices Edition Publication date: May 2012 Book number: 204-0704-SM-01 Product version: Rocket Model 204 System Manager’s Guide Version 7 Release 4.0 Copyright © Computer Corporation of America 1989-2012. All Rights Reserved. Computer Corporation of America is a wholly-owned subsidiary of Rocket Software, Inc. Trademarks Rocket is a registered trademark of Rocket Software, Inc. For a list of Rocket registered trademarks go to: www.rocketsoftware.com/about/legal. All other products or services mentioned in this document may be covered by the trademarks, service marks, or product names of their respective owners. License agreement This software and the associated documentation are proprietary and confidential to Rocket Software, Inc., are furnished under license, and may be used and copied only in accordance with the terms of such license. Note This product may contain encryption technology. Many countries prohibit or restrict the use, import, or export of encryption technologies, and current use, import, and export regulation should be followed when exporting this product. Contact information Web Site: www.rocketsoftware.com Rocket Software, Inc. Headquarters 77 4th Avenue, Suite 100 Waltham, MA 02451–1468 USA Tel: +1.617.614.4321 Fax: +1.617.630.7100 ii Contacting Technical Support If you have current support and maintenance agreements with Rocket Software and CCA, contact Rocket Software Technical support by email or by telephone: Email: [email protected] Telephone : North America +1.800.755.4222 United Kingdom/Europe +44 (0) 20 8867 6153 Alternatively, you can access the Rocket Customer Portal and report a problem, download an update, or read answers to FAQs. -

VM for MVS Systems Programmers Part 2 Martha Mcconaghy, Marist College Mark Post, EDS Monday, August 14, 2006 Session 9128 Follow up Presentations
VM For MVS Systems Programmers Part 2 Martha McConaghy, Marist College Mark Post, EDS Monday, August 14, 2006 Session 9128 Follow Up Presentations • Other presentations this week which cover related subjects in more detail: • 9107 – 9109 Introduction to VM Hands-on Lab Tue 8am-noon • 9125 Virtual Networking with z/VM Guest LANS and Virtual Switch Tue 8am • 9115 VM Performance Introduction Tue 1:20pm • 9119 z/VM Installation - What are you afraid of? Tue 3pm • 9117 Introduction to VMSES/E for z/VM Wed 9:30am • 9118 Maintaining z/VM with VMSES/E lab Wed 11am • 9133 Configuring, Customizing and Modifying your VM System without an IPL Wed 3pm • 9123 TRACK for z/VM – What’s Happening in your Virtual Machine Thur 9:30am • 9116 z/VM Simplified Network Configuration Thur 3pm • 9136 Automated Linux Guest Monitoring on z/VM using PROP 35 Agenda • Part 1: • Introduction to and comparison of basic concepts • What is a hypervisor and what about all the “virtual” stuff? • Caring for a VM system (maintenance, system datasets, etc.) • System configuration concepts • Part 2: • Applications and guests • CMS vs. TSO • File Editors • Misc good stuff We will answer questions as time allows….. 36 Application Support • CP level of z/VM cannot execute applications. It’s only job is to emulate hardware and manage resources. • Does not provide file editing or writing capabilities. It can read CMS files for use with system configuration. • Cannot compile, assemble or execute programs. • CMS started out as an operating system during the early days of mainframes. • Became popular as a “guest” on CP to provide user/application functions. -

Z/VM Version 7 Release 2
z/VM Version 7 Release 2 OpenExtensions User's Guide IBM SC24-6299-01 Note: Before you use this information and the product it supports, read the information in “Notices” on page 201. This edition applies to Version 7.2 of IBM z/VM (product number 5741-A09) and to all subsequent releases and modifications until otherwise indicated in new editions. Last updated: 2020-09-08 © Copyright International Business Machines Corporation 1993, 2020. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Figures................................................................................................................. xi Tables................................................................................................................ xiii About this Document........................................................................................... xv Intended Audience..................................................................................................................................... xv Conventions Used in This Document......................................................................................................... xv Escape Character Notation................................................................................................................... xv Case-Sensitivity.....................................................................................................................................xv Typography............................................................................................................................................xv -

Network Program Products General Information and Planning For
---- -------- - --- Network Program Products GC30-3463-0 -------_.---- - - --- General Information and Planning for NetView Release 2 MVS, VM and VSE ----- - --- Network Program Products GC30·3463·0 --_--------- - - ---.-. General Information and Planning for NetView Release 2 MVS, VM and VSE First Edition (June 1987) This book applies to the following IBM licensed program: NetView Release 2 for MVS/370 (program number 5665-361). MVS/XA (program number 5665-362). VM (program number 5664-204). and VSE (program number 5666-343). The licensed program described in this manual. and all licensed material avaiiable for it. are provided by IBM under terms of the Agreement for IBM Licensed Programs. Changes are made periodically to the information herein; before you use this publication in connection with the operation of IBM systems. consult the latest IBM Systeml370, 30xx, and 4300 Processors Bibliography, GC20-0001. for the editions that are applicable and current. Any reference to an IBM licensed program in this document is not intended to state or imply that only IBM's program may be used. Any functionally equivalent program may be used instead. It is possible that this material may contain reference to. or information about. IBM products (machines and programs). programming. or services that are not announced in your country. Such references or information must not be construed to mean that IBM intends to announce such products. programs. or services in your country. Publications are not stocked at the address given below. If you want more IBM publications. ask your IBM representative or write to the IBM branch office serving your locality. A form for your comments is provided at the back of this publication. -

Database Machines in Support of Very Large Databases
Rochester Institute of Technology RIT Scholar Works Theses 1-1-1988 Database machines in support of very large databases Mary Ann Kuntz Follow this and additional works at: https://scholarworks.rit.edu/theses Recommended Citation Kuntz, Mary Ann, "Database machines in support of very large databases" (1988). Thesis. Rochester Institute of Technology. Accessed from This Thesis is brought to you for free and open access by RIT Scholar Works. It has been accepted for inclusion in Theses by an authorized administrator of RIT Scholar Works. For more information, please contact [email protected]. Rochester Institute of Technology School of Computer Science Database Machines in Support of Very large Databases by Mary Ann Kuntz A thesis. submitted to The Faculty of the School of Computer Science. in partial fulfillment of the requirements for the degree of Master of Science in Computer Systems Management Approved by: Professor Henry A. Etlinger Professor Peter G. Anderson A thesis. submitted to The Faculty of the School of Computer Science. in partial fulfillment of the requirements for the degree of Master of Science in Computer Systems Management Approved by: Professor Henry A. Etlinger Professor Peter G. Anderson Professor Jeffrey Lasky Title of Thesis: Database Machines In Support of Very Large Databases I Mary Ann Kuntz hereby deny permission to reproduce my thesis in whole or in part. Date: October 14, 1988 Mary Ann Kuntz Abstract Software database management systems were developed in response to the needs of early data processing applications. Database machine research developed as a result of certain performance deficiencies of these software systems. -

CA XCOM Data Transport for UNIX and Linux Overview Guide
CA XCOM™ Data Transport® for UNIX and Linux Overview Guide r11.5 Second Edition This documentation and any related computer software help programs (hereinafter referred to as the “Documentation”) is for the end user’s informational purposes only and is subject to change or withdrawal by CA at any time. This Documentation may not be copied, transferred, reproduced, disclosed, modified or duplicated, in whole or in part, without the prior written consent of CA. This Documentation is confidential and proprietary information of CA and protected by the copyright laws of the United States and international treaties. Notwithstanding the foregoing, licensed users may print a reasonable number of copies of the documentation for their own internal use, and may make one copy of the related software as reasonably required for back-up and disaster recovery purposes, provided that all CA copyright notices and legends are affixed to each reproduced copy. Only authorized employees, consultants, or agents of the user who are bound by the provisions of the license for the product are permitted to have access to such copies. The right to print copies of the documentation and to make a copy of the related software is limited to the period during which the applicable license for the Product remains in full force and effect. Should the license terminate for any reason, it shall be the user’s responsibility to certify in writing to CA that all copies and partial copies of the Documentation have been returned to CA or destroyed. EXCEPT AS OTHERWISE STATED IN THE APPLICABLE LICENSE AGREEMENT, TO THE EXTENT PERMITTED BY APPLICABLE LAW, CA PROVIDES THIS DOCUMENTATION “AS IS” WITHOUT WARRANTY OF ANY KIND, INCLUDING WITHOUT LIMITATION, ANY IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NONINFRINGEMENT. -

Washington Systems Center Technical Bulletin: "SNA Networking Products Overview and SNA Release/Function Guide" (GG22-9256-00)
Washington Technical Systems Bulletin Center A. H. Shrader GG22-9386-00 December 1984 Washington Systems Center Gaithersburg, Maryland Technical Bulletin SNA NETWORKING PRODUCT OVERVIEW Hank Shrader GG22-9386-00 December 1984 The information contained in this document has not been submitted to any formal IBM test and is distributed on an "as is" basis WITHOUT ANY WARRANTY EITHER EXPRESSED OR IMPLIED. The use of this information or the implementation of any of these techniques is a customer responsibility and depends on the customer's ability to evaluate and integrate them into the customer's operational environment. While each item may have been reviewed by IBM for accuracy in a specific situation, there is no guarantee that the same or similar results will be obtained elsewhere. Customers attempting to adapt these techniques to their own environments do so at their own risk. In this document, any references made to an IBM program product are not intended to state or imply that only IBM's program product may be used; \ any functionally equivalent program may be used instead. It is possible that this material may contain reference to, or information about, IBM products (machines and programs), programming, or services that are not announced in your country. Such references or information must not be construed to mean that IBM intends to announce such IBM products, programming, or services in your country. Publications are not stocked at the address given below; requests for IBM publications should be made to your IBM representative or to the IBM office serving your locality. A form for reader's comments is provided at the back of this publication. -

The IBM System/38
8 The IBM System/38 8.1 Introduction IBM’s capability-based System38 [Berstis 80a, Houdek 81, IBM Sa, IBM 82b], announced in 1978 and delivered in 1980, is an outgrowth of work that began in the late sixties and early seventies on IBM’s future system (FS) project. Designers at the IBM Development Laboratory in Rochester, Minnesota incorporated ideas from FS, modified by their needs, to pro- duce a system for the commercial marketplace. It is interesting that such an advanced, object-based architecture has been ap- plied to a very traditional product space. Initially, only the COBOL and RPG III languages were provided. The system, which includes the CPF (Control Program Facility) operating system, is intended to support transaction processing and data- base applications constructed in commercial languages. A major goal of the System38 design is to maintain pro- grammer independence from the system implementation [Dahlby SO]; IBM wished to retain maximum flexibility to modify System38’s implementation for future technologies while supporting previously written System38 programs. The designers also wished to support a high level of integrity and security at the machine interface and to support commonly executed user and system functions efficiently, such as data- base searches and memory management [Hoffman 801. To meet these goals, IBM chose a layered machine structure with a high-level programming interface. The layers of this design are shown in Figure 8-l. At the lowest level is a hardware machine that directly exe- 137 The IBM System/38 User Applications Verticai Microcode Horizon&/ Microcode Hardware Machine Figure 8-1: System/38 Implementation Layers cutes 32-bit horizontal microcode. -
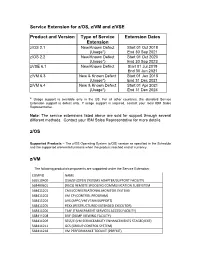
Service Extension for Z/OS, Z/VM and Z/VSE
Service Extension for z/OS, z/VM and z/VSE Product and Version Type of Service Extension Dates Extension z/OS 2.1 New/Known Defect Start 01 Oct 2018 (Usage*) End 30 Sep 2021 z/OS 2.2 New/Known Defect Start 01 Oct 2020 (Usage*) End 30 Sep 2023 zVSE 6.1 New/Known Defect Start 01 Jul 2019 End 30 Jun 2021 z/VM 6.3 New & Known Defect Start 01 Jan 2018 (Usage*) End 31 Dec 2021 z/VM 6.4 New & Known Defect Start 01 Apr 2021 (Usage*) End 31 Dec 2024 * Usage support is available only in the US. For all other countries, the standard Service Extension support is defect only. If usage support is required, contact your local IBM Sales Representative. Note: The service extensions listed above are sold for support through several different methods. Contact your IBM Sales Representative for more details. z/OS Supported Products – The z/OS Operating System (z/OS) version as specified in the Schedule and the supported elements/functions when the product reached end of currency. z/VM The following products/components are supported under the Service Extension: COMPID NAME 565510400 OSA/SF (OPEN SYSTEMS ADAPTER/SUPPORT FACILITY) 568409601 (RSCS) REMOTE SPOOLING COMMUNICATION SUBSYSTEM 568411201 CMS (CONVERSATIONAL MONITOR SYSTEM) 568411202 VM CP (CONTROL PROGRAM) 568411204 AVS (APPC/VM VTAM SUPPORT) 568411205 REXX (RESTRUCTURED EXTENDED EXECUTOR) 568411206 TSAF (TRANSPARENT SERVICES ACCESS FACILITY) 568411208 DVF (DUMP VIEWING FACILITY) 568411209 SESS/E (VM SERVICEABILITY ENHANCEMENTS STAGED/EXT) 568411211 GCS (GROUP CONTROL SYSTEM) 568411218 VM PERFORMANCE -

IBM Z/VM Version 6 Release 4 Security Target
IBM z/VM Version 6 Release 4 Security Target Version: 1.2 Status: Released Last Update: 2017-11-29 Classification: Public IBM Corporation IBM z/VM Version 6 Release 4 Security Target Trademarks The following terms are trademarks or registered trademarks of International Business Machines Corporation in the United States, other countries, or both: ● Enterprise Systems Architecture/390 ● ESA/390 ● IBM ● IBM logo ● HiperSockets ● PR/SM ● Processor Resource/Systems Manager ● RACF ● S/390 ● z System ● VM/ESA ● z/Architecture ● z/VM Other company, product, and service names may be trademarks or service marks of others. Legal Notice This document contains information of a confidential nature. Review and Approval Process: Refer to the inspection process in the z System Software Programming Process. Required Reviewers ● Brian Hugenbruch Document Distribution and Change Notification: The document is distributed to the reviewers of this line item. When reissued with changes, the document owner sends a note to the reviewers notifying them of the availability of a new document version. Revision History Revision Date Author(s) Changes to Previous Revision 1.2 2017-11-29 Brian W. Released public version Hugenbruch Version: 1.2 Classification: Public Page 2 of 125 Last update: 2017-11-29 Copyright © 2017 by atsec information security and IBM IBM Corporation IBM z/VM Version 6 Release 4 Security Target Table of Contents 1 Introduction ................................................................................................... 10 1.1 Security Target