Air-BOOT User Manual
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Backbox Penetration Testing Never Looked So Lovely
DISTROHOPPER DISTROHOPPER Our pick of the latest releases will whet your appetite for new Linux distributions. Picaros Diego Linux for children. here are a few distributions aimed at children: Doudou springs to mind, Tand there’s also Sugar on a Stick. Both of these are based on the idea that you need to protect children from the complexities of the computer (and protect the computer from the children). Picaros Diego is different. There’s nothing stripped- down or shielded from view. Instead, it’s a normal Linux distro with a brighter, more kid-friendly interface. The desktop wallpaper perhaps best We were too busy playing Secret Mario on Picaros Diego to write a witty or interesting caption. exemplifies this. On one hand, it’s a colourful cartoon image designed to interest young file manager. In the programming category, little young for a system like this, but the it children. Some of the images on the we were slightly disappointed to discover it may well work for children on the upper end landscape are icons for games, and this only had Gambas (a Visual Basic-like of that age range. should encourage children to investigate the language), and not more popular teaching Overall, we like the philosophy of wrapping system rather than just relying on menus. languages like Scratch or a Python IDE. Linux is a child-friendly package, but not On the other hand, it still displays technical However, it’s based on Debian, so you do dumbing it down. Picaros Diego won’t work details such as the CPU usage and the RAM have the full range of software available for every child, but if you have a budding and Swap availability. -
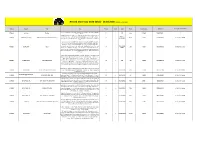
Record Store Day 2020 (GSA) - 18.04.2020 | (Stand: 05.03.2020)
Record Store Day 2020 (GSA) - 18.04.2020 | (Stand: 05.03.2020) Vertrieb Interpret Titel Info Format Inhalt Label Genre Artikelnummer UPC/EAN AT+CH (ja/nein/über wen?) Exclusive Record Store Day version pressed on 7" picture disc! Top song on Billboard's 375Media Ace Of Base The Sign 7" 1 !K7 Pop SI 174427 730003726071 D 1994 Year End Chart. [ENG]Pink heavyweight 180 gram audiophile double vinyl LP. Not previously released on vinyl. 'Nam Myo Ho Ren Ge Kyo' was first released on CD only in 2007 by Ace Fu SPACE AGE 375MEDIA ACID MOTHERS TEMPLE NAM MYO HO REN GE KYO (RSD PINK VINYL) LP 2 PSYDEL 139791 5023693106519 AT: 375 / CH: Irascible Records and now re-mastered by John Rivers at Woodbine Street Studio especially for RECORDINGS vinyl Out of print on vinyl since 1984, FIRST official vinyl reissue since 1984 -Chet Baker (1929 - 1988) was an American jazz trumpeter, actor and vocalist that needs little introduction. This reissue was remastered by Peter Brussee (Herman Brood) and is featuring the original album cover shot by Hans Harzheim (Pharoah Sanders, Coltrane & TIDAL WAVES 375MEDIA BAKER, CHET MR. B LP 1 JAZZ 139267 0752505992549 AT: 375 / CH: Irascible Sun Ra). Also included are the original liner notes from jazz writer Wim Van Eyle and MUSIC two bonus tracks that were not on the original vinyl release. This reissue comes as a deluxe 180g vinyl edition with obi strip_released exclusively for Record Store Day (UK & Europe) 2020. * Record Store Day 2020 Exclusive Release.* Features new artwork* LP pressed on pink vinyl & housed in a gatefold jacket Limited to 500 copies//Last Tango in Paris" is a 1972 film directed by Bernardo Bertolucci, saxplayer Gato Barbieri' did realize the soundtrack. -

Active @ UNDELETE Users Guide | TOC | 2
Active @ UNDELETE Users Guide | TOC | 2 Contents Legal Statement..................................................................................................4 Active@ UNDELETE Overview............................................................................. 5 Getting Started with Active@ UNDELETE........................................................... 6 Active@ UNDELETE Views And Windows......................................................................................6 Recovery Explorer View.................................................................................................... 7 Logical Drive Scan Result View.......................................................................................... 7 Physical Device Scan View................................................................................................ 8 Search Results View........................................................................................................10 Application Log...............................................................................................................11 Welcome View................................................................................................................11 Using Active@ UNDELETE Overview................................................................. 13 Recover deleted Files and Folders.............................................................................................. 14 Scan a Volume (Logical Drive) for deleted files..................................................................15 -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

How to Create a Custom Live CD for Secure Remote Incident Handling in the Enterprise
How to Create a Custom Live CD for Secure Remote Incident Handling in the Enterprise Abstract This paper will document a process to create a custom Live CD for secure remote incident handling on Windows and Linux systems. The process will include how to configure SSH for remote access to the Live CD even when running behind a NAT device. The combination of customization and secure remote access will make this process valuable to incident handlers working in enterprise environments with limited remote IT support. Bert Hayes, [email protected] How to Create a Custom Live CD for Remote Incident Handling 2 Table of Contents Abstract ...........................................................................................................................................1 1. Introduction ............................................................................................................................5 2. Making Your Own Customized Debian GNU/Linux Based System........................................7 2.1. The Development Environment ......................................................................................7 2.2. Making Your Dream Incident Handling System...............................................................9 2.3. Hardening the Base Install.............................................................................................11 2.3.1. Managing Root Access with Sudo..........................................................................11 2.4. Randomizing the Handler Password at Boot Time ........................................................12 -

A Knoppix Based Live CD That Lets a Linux Cluster Ready for MPI and Other Parallel Computing in Less Than 15 Minutes!
A Knoppix based Live CD that lets a Linux Cluster ready for MPI and other Parallel Computing in less than 15 minutes! Abstract ParallelKnoppix is a live CD based on Knoppix, which is also a live CD, based on Debian Linux Distribution. ParallelKnoppix will let us create a linux cluster equipped with parallel programming tools/libraries such as MPI in a couple of minutes. It saves a lot of time that we spend in configuration of the computing environment. The existing environment is not disturbed using ParallelKnoppix, as it is a Live CD. Only on master node a directory is created that can be deleted after reboot if you want. Introduction “ParallelKnoppix is a re-master of Knoppix that allows setting up a cluster of machines for parallel processing using the LAM-MPI and/or MPICH implementations of MPI. Getting the cluster up and running takes less than 15 minutes, if the machines have PXE network cards.” >From http://pareto.uab.es/mcreel/ParallelKnoppix/ Background Clustering is one of the cheapest techniques to achieve Parallelism. Clustering by using linux is one of the linux powers. The universities and organization mimic super computing by connecting PCs through Ethernet Cards under Linux. Since linux is highly adopted by scientific community to do their research work as linux is loaded with a number of scientific tools such as LAM, PI, PVM and many more. So linux is best suited for parallel computing. But the problem is scientist and programmers have a lot to do with some pre-configuration of the linux environment. This makes there task slow and complex. -

Microsoft Windows Common Criteria Evaluation Security Target
Microsoft Common Criteria Security Target Microsoft Windows Common Criteria Evaluation Microsoft Windows 10 version 1809 (October 2018 Update) Microsoft Windows Server 2019 (October 2018 Update) Security Target Document Information Version Number 0.05 Updated On June 18, 2019 Microsoft © 2019 Page 1 of 126 Microsoft Common Criteria Security Target Version History Version Date Summary of changes 0.01 June 27, 2018 Initial draft 0.02 December 21, 2018 Updates from security target evaluation 0.03 February 21, 2019 Updates from evaluation 0.04 May 6, 2019 Updates from GPOS PP v4.2.1 0.05 June 18, 2019 Public version Microsoft © 2019 Page 2 of 126 Microsoft Common Criteria Security Target This is a preliminary document and may be changed substantially prior to final commercial release of the software described herein. The information contained in this document represents the current view of Microsoft Corporation on the issues discussed as of the date of publication. Because Microsoft must respond to changing market conditions, it should not be interpreted to be a commitment on the part of Microsoft, and Microsoft cannot guarantee the accuracy of any information presented after the date of publication. This document is for informational purposes only. MICROSOFT MAKES NO WARRANTIES, EXPRESS OR IMPLIED, AS TO THE INFORMATION IN THIS DOCUMENT. Complying with all applicable copyright laws is the responsibility of the user. This work is licensed under the Creative Commons Attribution-NoDerivs- NonCommercial License (which allows redistribution of the work). To view a copy of this license, visit http://creativecommons.org/licenses/by-nd-nc/1.0/ or send a letter to Creative Commons, 559 Nathan Abbott Way, Stanford, California 94305, USA. -

Guest OS Compatibility Guide
Guest OS Compatibility Guide Guest OS Compatibility Guide Last Updated: September 29, 2021 For more information go to vmware.com. Introduction VMware provides the widest virtualization support for guest operating systems in the industry to enable your environments and maximize your investments. The VMware Compatibility Guide shows the certification status of operating system releases for use as a Guest OS by the following VMware products: • VMware ESXi/ESX Server 3.0 and later • VMware Workstation 6.0 and later • VMware Fusion 2.0 and later • VMware ACE 2.0 and later • VMware Server 2.0 and later VMware Certification and Support Levels VMware product support for operating system releases can vary depending upon the specific VMware product release or update and can also be subject to: • Installation of specific patches to VMware products • Installation of specific operating system patches • Adherence to guidance and recommendations that are documented in knowledge base articles VMware attempts to provide timely support for new operating system update releases and where possible, certification of new update releases will be added to existing VMware product releases in the VMware Compatibility Guide based upon the results of compatibility testing. Tech Preview Operating system releases that are shown with the Tech Preview level of support are planned for future support by the VMware product but are not certified for use as a Guest OS for one or more of the of the following reasons: • The operating system vendor has not announced the general availability of the OS release. • Not all blocking issues have been resolved by the operating system vendor. -

OWASP Live CD: an Open Environment for Web Application Security
OWASP Live CD: An open environment for web application security. Matt Tesauro OWASP Live CD project lead OWASP Global Project Committee Texas Education Agency [email protected] Copyright 2007 © The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the OWASP License. The OWASP Foundation http://www.owasp.org Presentation Overview Who am I and what's this OWASP Live CD thing anyway? Where are we now? Where are we going? How can I get involved? What else is out there? OWASP 2 About me Varried IT Background Developer, DBA, Sys Admin, Pen Tester, Application Security, CISSP, CEH, RHCE, Linux+ Long history with Linux & Open Source First Linux install ~1998 DBA and Sys Admin was all open source Last full-time commercial OS = Windows 2000 Contributor to many projects, leader of one OWASP 3 Project History Started as a Summer of Code 2008 project SoC Project to update previous OWASP Live CD Autumn of Code 2006 & Spring of Code 2007 Lab Rat (v 2.1) Morphix (Debian derivative) Appeared dormant to me Applied and was sponsored March 25th, 2008 submitted my application Sept. 15th, 2008 completed the SoC project OWASP 4 Project Goals (post SoC) Make application security tools and documentation easily available and easy to use Compliment's OWASP goal to make application security visible Design goals Easy for users to keep updated Easy for project lead to keep updated Easy to produce releases (maybe quarterly) Focused on just application security – not general pen testing OWASP 5 Pseudocode != OWASP -

ACPI Project for Ecomstation
The ACPI Project for eComStation David Azarewicz www.88watts.net [email protected] Warpstock USA 2012 About Me • I am primarily a hardware developer. I started my career designing hardware for IBM 360 mainframe clones. • I then joined a small company building Cray compatible computers where I did a little of everything including microcode and embedded systems hardware and software. • Since then I have worked on projects from auto industry process controllers, to home automation, to radiation effects testing for satellite electronics. • I have been using OS/2 and developing software for OS/2 since the beginning. • Being an experienced hardware developer gives me an advantage in writing device drivers. Warpstock USA 2012 - The ACPI Project - David Azarewicz - Page 2 of 20 This Presentation • What is ACPI? • What is the ACPI Project? • What does the ACPI Project software do? • The Big Picture • The benefits and limitations of the ACPI Project software • How to work around problems • Using ACPI in your applications • Questions Warpstock USA 2012 - The ACPI Project - David Azarewicz - Page 3 of 20 What is ACPI? • ACPI stands for Advanced Configuration and Power Interface • ACPI is supplied by your computer vendor and is part of your computer’s BIOS. • ACPI provides a standard interface to your computer’s hardware through a list of objects and methods called the ACPI tables. • Software can use the ACPI tables to learn about what hardware is available • Software can use the ACPI tables to do things in the system. • ACPI is an extremely large and complex topic and is not really the subject of this presentation. -

Evolutionary Sprint 2009/11
Evolutionary Sprint Evolutionary Sprint 2009/11 Speaker: Eugene Gorbunoff software http://ecomstation.ru Perspectives of eComStation 2008/11 “Build non-sinking constructions” 2007/11 “Change your mind” 2006/11 “OS/2 Village” software http://ecomstation.ru Perspectives of eComStation What is Evolutionary Sprint? ● Evolutionary = don't migrate to other platform ● Sprint = 2-3 years to improve situation (starting from fall 2006) software http://ecomstation.ru Perspectives of eComStation Contents of the presentation: (A) (B) (C) What's new? What is successful eCS? PC in 2010 Roles Make quick changes FAQ eComStation 3.0 We need new software software http://ecomstation.ru Perspectives of eComStation Key slide: #04-00 Sci-tech labs.. development of technologies.. software http://ecomstation.ru Perspectives of eComStation software http://ecomstation.ru Perspectives of eComStation Keep in mind.. eComStation 2.0 was started in 2002!! software http://ecomstation.ru Perspectives of eComStation What's new in 2009? # 05-00 eComStation 2.0 RC7, eComStation 2.0 GA Applications: * OpenOffice.org 3.1 GA * PMView (2009/05) improved for SMP/Panorama VESA * always the latest Thunderbird, Firefox * DFSee 10.0 New technologies: * Flash-player software http://ecomstation.ru Perspectives of eComStation What's new in 2009? # 05-02 ACPI * Poor support of users during 2009 * Intel ACPI source code 2008/12 * ACPI is patching the kernel on-the-fly (suspend/resume) * support of Embedded controller is implemented Hardware support: * CUPS (USB, debugging) software http://ecomstation.ru -

SEFS: Security Module for Extensible File System Architectures
SEFS: Security Module for Extensible File System Architectures Þ Þ Lu´ıs FerreiraÝ , Andr´eZ´uquete and Paulo Ferreira Ý ISEL/INESC, Þ IST/INESC g fluis.ferreira, andre.zuquete, paulo.ferreira @inesc.pt Abstract ethical access by file server’s administrators; or (iv) unauthorized accesses to users’ files by an attacker Data security is a fundamental issue in modern com- capable of impersonating them. Whence, access con- puter systems. In particular, data storage systems are trol mechanisms, either physical or logical, aren’t bul- frequently subject to attacks and so need protection. letproof, and that may be a major concern for people Typical storage systems rely on access control mecha- dealing with sensitive data. nisms, either physical or logical, to prevent unautho- To make it even worse, current distributed file sys- rized users from accessing stored data. However, such tems exacerbate some of the previous problems and mechanisms are useless against non-ethical attitudes introduce new ones. On distributed file systems peo- taken by privileged users, like system administrators. ple have to trust on: (i) the physical security of remote Thus, the ultimate solution for ensuring the privacy of file servers, (ii) administration teams (that may blur sensitive data is to use cryptographic techniques. individual non-ethical attitudes), (iii) the capability This article describes the design and implemen- of remote authentication mechanisms to prevent per- tation of a security module, for extensible file sys- sonification, and, finally, (iv) they have to trust that tem architectures (SEFS), that enforces file security attackers cannot understand or modify data flows using cryptographic techniques.