Mobile Private Contact Discovery at Scale
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

RADA Sense Mobile Application End-User Licence Agreement
RADA Sense Mobile Application End-User Licence Agreement PLEASE READ THESE LICENCE TERMS CAREFULLY BY CONTINUING TO USE THIS APP YOU AGREE TO THESE TERMS WHICH WILL BIND YOU. IF YOU DO NOT AGREE TO THESE TERMS, PLEASE IMMEDIATELY DISCONTINUE USING THIS APP. WHO WE ARE AND WHAT THIS AGREEMENT DOES We Kohler Mira Limited of Cromwell Road, Cheltenham, GL52 5EP license you to use: • Rada Sense mobile application software, the data supplied with the software, (App) and any updates or supplements to it. • The service you connect to via the App and the content we provide to you through it (Service). as permitted in these terms. YOUR PRIVACY Under data protection legislation, we are required to provide you with certain information about who we are, how we process your personal data and for what purposes and your rights in relation to your personal data and how to exercise them. This information is provided in https://www.radacontrols.com/en/privacy/ and it is important that you read that information. Please be aware that internet transmissions are never completely private or secure and that any message or information you send using the App or any Service may be read or intercepted by others, even if there is a special notice that a particular transmission is encrypted. APPLE APP STORE’S TERMS ALSO APPLY The ways in which you can use the App and Documentation may also be controlled by the Apple App Store’s rules and policies https://www.apple.com/uk/legal/internet-services/itunes/uk/terms.html and Apple App Store’s rules and policies will apply instead of these terms where there are differences between the two. -

Appendix Contents
Appendix This appendix contains the textual transcripts of the fifty smartphone advertisements selected for the analysis. The smartphones are arranged in an alphabetical order and numbered in concord with the numbering of the advertisements used in the thesis. Contents Appendix .................................................................................................................................... 1 1 Acer Liquid Z220 commercial ......................................................................................... 4 2 Acer Liquid Z520 commercial ......................................................................................... 4 3 Alcatel Onetouch Idol 2 S commercial ............................................................................ 5 4 ALCATEL ONETOUCH PIXI 3 Family commercial ................................................... 6 5 ARCHOS Helium Plus commercial ................................................................................. 8 6 ASUS ZenFone 2 and ZenFone Zoom commercial ........................................................ 9 7 ASUS ZenFone Max commercial ................................................................................... 10 8 BlackBerry Classic commercial ..................................................................................... 12 9 BlackBerry PRIV commercial ....................................................................................... 13 10 BLU Life Pure Mini commercial ................................................................................ -
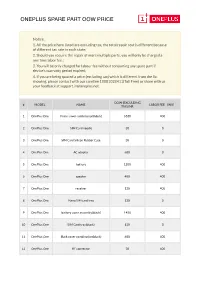
Oneplus-Spare-Part-OOW-Price V1
ONEPLUS SPARE PART OOW PRICE Notice: 1. All the price here listed are excluding tax, the total repair cost is different because of different tax rate in each state; 2. Should you require the repair of more multiple parts, you will only be charged a one time labor fee. ; 3. You will be only charged for labour fee without consuming any spare part if device's warranty period expired; 4. If you are being quoted a price (excluding tax) which is different from the list showing, please contact with our careline 18001028411(Toll Free) or share with us your feedback at [email protected]. OOW (EXCULDING # MODEL NAME LABOR FEE INR TAX) INR ҁ ҂ 1 OnePlus One Front-cover combination(black) 6530 400 2 OnePlus One SIM Card needle 30 0 3 OnePlus One SIM Card Silicon Rubber Case 30 0 4 OnePlus One AC adapter 600 0 5 OnePlus One battery 1200 400 6 OnePlus One speaker 400 400 7 OnePlus One receiver 130 400 8 OnePlus One Nano SIM card tray 130 0 9 OnePlus One battery cover assembly(black) 1450 400 10 OnePlus One SIM Card tray(black) 130 0 11 OnePlus One Back cover combination(black) 600 400 12 OnePlus One RF connector 70 400 OOW (EXCULDING # MODEL NAME LABOR FEE INR TAX) INR ҁ ҂ 13 OnePlus One USB FPC 260 400 14 OnePlus One Small PCBA 730 400 15 OnePlus One Front camera 860 400 16 OnePlus One main camera 2380 400 17 OnePlus One USB cable 600 0 18 OnePlus One Main Board(64G) 14450 400 19 OnePlus One SIM Socket 530 400 20 OnePlus One Front-cover combination(white) 7200 400 21 OnePlus One Nano SIM card trayҁwhite҂ 130 0 22 OnePlus One battery cover assembly(white) -
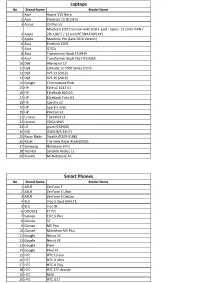
Type-C Compatible Device List 1.Xlsx
Laptops No Brand Name Model Name 1 Acer Aspire V15 Nitro 2 Acer Predator 15 (N15P3) 3 Aorus X3 Plus v5 MacBook (2015 version with USB-C port - Specs: 13.1mm THIN / 4 Apple 2lb. LIGHT / 12-inch RETINA DISPLAY) 5 Apple MacBook Pro (Late 2016 Version) 6 Asus EeeBook E202 7 Asus G752v 8 Asus Transformer Book T100HA 9 Asus Transformer Book Flip (TP200SA) 10 Dell Alienware 17 11 Dell Latitude 12 7000 Series (7275 12 Dell XPS 13 (2016) 13 Dell XPS 15 (2016) 14 Google Chromebook Pixel 15 HP Elite x2 1012 G1 16 HP EliteBook 840 G3 17 HP EliteBook Folio G1 18 HP Spectre x2 19 HP Spectre x360 20 HP Pavilion x2 21 Lenovo ThinkPad 13 22 Lenovo YOGA 900S 23 LG gram (15Z960) 24 MSI GS60 (MS-16H7) 25 Razer Blade Stealth (RZ09-0168) 26 Razer The New Razer Blade(2016) 27 Samsung Notebook 9 Pro 28 Toshiba Satellite Radius 12 29 Xiaomi Mi Notebook Air Smart Phones No Brand Name Model Name 1 ASUS ZenFone 3 2 ASUS ZenFone 3 Ultra 3 ASUS ZenFone 3 Deluxe 4 BLU Vivo 5 Dual SIM LTE 5 BLU Vivo XL 6 DOOGEE F7 Pro 7 Gionee Elife S Plus 8 Gionee S6 9 Gionee M5 Plus 10 Gionee Marathon M5 Plus 11 Google Nexus 5X 12 Google Nexus 6P 13 Google Pixel 14 Google Pixel XL 15 HTC HTC 10 evo 16 HTC HTC U Ultra 17 HTC HTC U Play 18 HTC HTC 10 Lifestyle 19 HTC M10 20 HTC HTC U11 21 Huawei Honor 22 Huawei Honor 8 23 Huawei Honor 9 24 Huawei Honor Magic 25 Huawei Hornor V9 26 Huawei Mate 9 27 Huawei Mate 9 Pro 28 Huawei Mate 9 Porsche Design 29 Huawei Nexus 6P 30 Huawei Nova2 31 Huawei P9 32 Huawei P10 33 Huawei P10 Plus 34 Huawei V8 35 Lenovo ZUK Z1(China) 36 Lenovo Zuk Z2 37 -

Oneplus 2 User Manual Index
OnePlus 2 User Manual Index 03 Welcome Page 10 USB Type-C Port & Charging 11 Power On 04 What’s in The Box? 12 OxygenOS 05 The Device 13 App Permissions 06 Alert Slider 14 Customization 07 Fingerprint Sensor 15 Messaging 08 Back Cover 16 Making a Call 09 Dual SIM Card Tray 17 Camera & Photos Thank you! The OnePlus 2 is the result of our hard work in trying to meet the steep expectations held by our users and community, of us. We promised to deliver an amazing amalgamation of mobile hardware, software and experience, and we want to thank all of you for pushing us to keep this promise. We truly couldn’t have offered the best mobile experience out there, without your help. What’s in The Box OnePlus 2 Charger USB Data & User Guide Charging Cable Quick Start Guide 4 | What’s in the box Device OxygenOS Camera Dual Nano SIM Slot Alert Slider Volume IR Laser Focus Power Sleep/Wake StyleSwap Cover Release Home/Fingerprint Sensor 5 | What’s in the box Device OxygenOS Alert Slider None Disable all notifications from all contacts The Alert Slider allows you to effortlessly switch between 3 (Alarm notifications will still be enabled). notification profiles without having to take the phone out of your pocket. Priority Receive notifications from only your priority contacts. All Receive notifications from all your contacts. 6 | What’s in the box Device OxygenOS Fingerprint Sensor Quickly and securely unlock your OnePlus 2 with a simple press. It can store up to 5 unique fingerprint profiles. -

Display Sizes of Monitors, Pcs, Notebooks, Tablets, Phablets, Smartphones, Handhelds & HMD
Display sizes of Monitors, PCs, Notebooks, Tablets, Phablets, Smartphones, Handhelds & HMD Diago Devi Diago nal Widt Heig ce Aspe Operati nal Size h ht Widt ct ng Categor Model Brand Size (CM) (PX) (PX) h PPI Ratio System y Acer Chromeb 136 16:0 Comput ook Acer 11.6 29 6 768 1366 135 9 Chrome er Acer Iconia Tab 128 16:1 A Acer 10.1 26 0 800 1280 149 0 Android Tablet Acer 03:0 Picasso Acer 11.6 29 768 1280 768 190 5 Android Tablet Acer 384 Non 09:1 Window Comput S277HK Acer 27 68.6 0 2160 3840 e 6 s er Acer Switch 10 128 Non 05:0 E Acer 10.1 25.7 0 800 1280 e 8 Android Tablet Ainol Novo 10 128 08:0 Hero Ainol 10 25 0 800 1280 151 5 Android Tablet Ainol Novo 7 102 16:0 Crystal Ainol 7 18 4 600 1024 169 9 Android Tablet Ainol Novo 9 204 04:0 Spark Ainol 9.7 25 8 1536 1024 264 3 Android Tablet Alcatel One Touch 09:1 Idol Ultra Alcatel 4.7 11.9 720 1280 360 316 6 Android Mobile Alcatel One Touch 03:0 Ultra 995 Alcatel 4.3 10.9 480 800 320 217 5 Android Mobile Amazon 102 05:0 Fire Amazon 7 17.8 4 600 1024 171 8 Android Tablet Amazon Fire HD 128 05:0 10 Amazon 10 25.4 0 800 1280 149 8 Android Tablet Amazon 128 05:0 Fire HD 6 Amazon 6 15.2 0 800 1280 252 8 Android Tablet Amazon 128 05:0 Fire HD 8 Amazon 8 20.3 0 800 1280 189 8 Android Tablet WWW.MYMATHTABLES.COM 1 Amazon Kindle Fire 1st 75 : Gen Amazon 7 18 600 1024 600 169 128 Android Tablet Amazon Kindle 05:0 Fire HD 7" Amazon 7 18 800 1280 533 216 8 Android Tablet Amazon Kindle Fire HD 120 05:0 8.9" Amazon 8.9 23 0 1920 800 254 8 Android Tablet Apple Cinema Display 256 08:0 Comput 30" Apple -

Manual Root Galaxy S3 4.1.2.Pdf
Manual Root Galaxy S3 4.1.2 GT-I9300 is an International version of Samsung Galaxy S3 variants. With good knowledge of rooting and its risks in mind, click ROOT. 4.1.2 - JRO03C. In part 1 of our exclusive Android device rooting guide, I covered many frequently I have tried it to root Samsung Galaxy S3 and S4 mobile phones and it worked Which one can I use for a Samsung Galaxy S2 running jelly bean 4.1.2? VG. Here's an update tutorial on how to root Galaxy S3 on Android 4.3 or 4.4.2. (Also works. We have come up with an easy guide to help you will rooting your device in One go Xperia TX, Nexus 4, Galaxy Nexus, HTC Desire HD, One X, Nexus 4, Galaxy Mine is a miphone running jellybean 4.1.2, does everything even reboots. Here's an updated tutorial for rooting all Galaxy S3 models including AT&T, T-Mobile Android 4.3 Jelly Bean, Android 4.1.2/4.1.1, Android 4.0.3 ICS, etc…etc… I8190XXANI4: Android 4.1.2 XXANI4 Firmware for Galaxy S3 Mini GT-I8190 The firmware update recently out by Samsung and the users can manually However, flashing or installing official firmware restore device kernel, so root access. Manual Root Galaxy S3 4.1.2 Read/Download Root Galaxy S3 I9305 on Android 4.1.2 XXBMB2 Jelly Bean Official Firmware Gets Android 4.1.2 XXLQ4 Jelly Bean Official Firmware (Manually Install). However, my Straight Talk S3 is still running Android version 4.1.2 and my watch won't Is there any way I can either manually update my phone to 4.3, or can I You can try to root your device and install the 4.3, but many Straight Talk users. -

Brand Old Device
# New Device Old Device - Brand Old Device - Model Name 1 Galaxy A6+ Asus Asus Zenfone 2 Laser ZE500KL 2 Galaxy A6+ Asus Asus Zenfone 2 Laser ZE601KL 3 Galaxy A6+ Asus Asus ZenFone 2 ZE550ML 4 Galaxy A6+ Asus Asus Zenfone 2 ZE551ML 5 Galaxy A6+ Asus Asus Zenfone 3 Laser 6 Galaxy A6+ Asus Asus Zenfone 3 Max ZC520TL 7 Galaxy A6+ Asus Asus Zenfone 3 Max ZC553KL 8 Galaxy A6+ Asus Asus Zenfone 3 ZE520KL 9 Galaxy A6+ Asus Asus Zenfone 3 ZE552KL 10 Galaxy A6+ Asus Asus Zenfone 3s Max 11 Galaxy A6+ Asus Asus Zenfone Max 12 Galaxy A6+ Asus Asus Zenfone Selfie 13 Galaxy A6+ Asus Asus ZenFone Zoom ZX550 14 Galaxy A6+ Gionee Gionee A1 15 Galaxy A6+ Gionee Gionee A1 Lite 16 Galaxy A6+ Gionee Gionee A1 Plus 17 Galaxy A6+ Gionee Gionee Elife E8 18 Galaxy A6+ Gionee Gionee Elife S Plus 19 Galaxy A6+ Gionee Gionee Elife S7 20 Galaxy A6+ Gionee Gionee F103 21 Galaxy A6+ Gionee Gionee F103 Pro 22 Galaxy A6+ Gionee Gionee Marathon M4 23 Galaxy A6+ Gionee Gionee Marathon M5 24 Galaxy A6+ Gionee Gionee marathon M5 Lite 25 Galaxy A6+ Gionee Gionee Marathon M5 Plus 26 Galaxy A6+ Gionee Gionee P5L 27 Galaxy A6+ Gionee Gionee P7 Max 28 Galaxy A6+ Gionee Gionee S6 29 Galaxy A6+ Gionee Gionee S6 Pro 30 Galaxy A6+ Gionee Gionee S6s 31 Galaxy A6+ Gionee Gionee X1s 32 Galaxy A6+ Google Google Pixel 33 Galaxy A6+ Google Google Pixel XL LTE 34 Galaxy A6+ Google Nexus 5X 35 Galaxy A6+ Google Nexus 6 36 Galaxy A6+ Google Nexus 6P 37 Galaxy A6+ HTC Htc 10 38 Galaxy A6+ HTC Htc Desire 10 Pro 39 Galaxy A6+ HTC Htc Desire 628 40 Galaxy A6+ HTC HTC Desire 630 41 Galaxy A6+ -

What's Coming up in Smartphones in 2016S
coverstory What’s Coming Up in Smartphones in 2016 From foldable displays to battle of chips and power, here is what to expect from smartphones in 2016 - Anuj Sharma sers will witness many new devices with foldable displays, improved optics, more powerful processors, longer battery back- Uup and much more. India witnessed some real action in the smartphone category in 2015 and is considered as the fastest growing smartphone market in Asia Pacific. Battle of Chips: Apple A10, Snapdragon 820, Exynos 8, and Helio X20 To Bring More Power, Better Battery Life And VR To Smartphones In 2016 As the smartphone industry grows by leaps and 1. Forget the phone; in 2016 it’s all about the bounds, manufacturers are gearing up to entice users by processor giving them more processing power and speed. Exterior design will not be the center of attraction in 2016 as we 2. Samsung to Launch High-End Tizen-Powered have already seen slimmer, bigger screen size and even Smartphone curved display smartphones this year like LG G Flex. Next 3. Improvements in battery technology year major companies like Apple, HTC, Samsung and Xi- 4. Samsung to Release Foldable Smartphone in aomi are looking on the inside components to stay ahead of each other. January 2016, Will Feature MicroSD Slot and We have been witnessing more powerful chips with Non-Removable Battery. each passing year and 2016 won’t be any exception. Chips next year are expected to deliver better battery life, virtual reality and other features to offer seamless Like the 810 chip, the 820 will once again support 4K user experience. -

3226701 Canada, Inc., Et Al. V. Qualcomm, Inc., Et Al. 15-CV-02678
Case 3:15-cv-02678-MMA-WVG Document 58 Filed 03/17/17 PageID.1170 Page 1 of 146 1 KESSLER TOPAZ LABATON SUCHAROW LLP MELTZER & CHECK, LLP James W. Johnson (Pro Hac Vice) 2 Eli R. Greenstein (Bar No. 217945) Michael H. Rogers (Pro Hac Vice) Jennifer L. Joost (Bar No. 296164) Matthew J. Hrutkay (Bar No. 297485) 3 Paul A. Breucop (Bar No. 278807) James T. Christie (Pro Hac Vice) Rupa Nath Cook (Bar No. 296130) [email protected] 4 [email protected] [email protected] [email protected] [email protected] 5 [email protected] [email protected] [email protected] 140 Broadway 6 One Sansome Street, Suite 1850 New York, New York 10005 San Francisco, CA 94104 Telephone: (212) 907-0700 7 Telephone: (415) 400-3000 Facsimile: (212) 818-0477 Facsimile: (415) 400-3001 8 -and- 9 Andrew L. Zivitz (Pro Hac Vice) 10 Jonathan F. Neumann (Pro Hac Vice) [email protected] 11 [email protected] 280 King of Prussia Road 12 Radnor, PA 19087 Telephone: (610) 667-7706 13 Facsimile: (610) 667-7056 14 Attorneys for the Public Employees Retirement System of Mississippi and 15 Co-Lead Counsel for the Proposed Class 16 UNITED STATES DISTRICT COURT 17 SOUTHERN DISTRICT OF CALIFORNIA 18 19 3226701 CANADA, INC., Case No. 15-CV-2678-MMA (WVG) Individually and on Behalf of All 20 Others Similarly Situated SECOND AMENDED CLASS 21 Plaintiffs, ACTION COMPLAINT FOR VIOLATIONS OF THE 22 v. FEDERAL SECURITIES LAWS 23 QUALCOMM, INC., STEVEN M. MOLLENKOPF, DEREK K. ABERLE, Judge: Hon. Michael M. Anello 24 GEORGE S. -

A Recent Study About One Plus 2 Mobile Computer and Its Specification with Features
A RECENT STUDY ABOUT ONE PLUS 2 MOBILE COMPUTER AND ITS SPECIFICATION WITH FEATURES Ganeshwara Shanmugam1, Mook Bin Hong2, Lai Yee Hern3 1,2,3Diploma in SE, Asia Pacific University, Kuala Lumpur, Malaysia ABSTRACT One Plus is a Chinese smartphone company, which found in late 2013. Its company in located in Shenzhen, Guangdong province, China. One Plus provided one of the most interesting phones in the year 2014. As Chinese phone turn out to be well-built and well-spec Android phone with one of the most beloved Android user interface customization feature, and around half the price of the normal smartphone, it gains the reputation in just a short period time. This investigation had to go through mostly about the OnePlus 2 specification and how the different electronic component works together to provide the user the best service ever. This study will also discuss the future and the limitation of mobile computing. Keywords: Architecture, Cache Memory, Features, Smart Phone I INTRODUCTION In this new era of globalisation, technology, and the electronic device had dominated our world. Technology had changed the way we live and the way we look at our surrounding world. Today, most of our friend and people surrounded us had at least one electronic device that can communicate and connect to the internet. This technology is called mobile computing. Mobile computing as become one of the most important and significant technology used by majorities of the population on this planet earth. It is a technology that allows an electronic device to communicate or share information with another device such as data, voice, and video. -

Announcement
Announcement Total 49 articles, created at 2016-04-18 18:01 1 Deep-dive review: For the iPad Pro, smaller is big Apple's latest iPad Pro, the new 9.7-in. model, not only gets many of the architecture advances from the larger version, but also a better camera and what may be Apple's (4.00/5) most advanced display yet. 2016-04-18 03:00 10KB www.itnews.com 2 Samsung Galaxy Note 6 UK release date, price, new features and specification rumours: Samsung Galaxy Note line (2.00/5) to return to the UK in 2016 The Samsung Galaxy Note series is returning to the UK this August with the new Note 6 (SM-N930F), expected to cost around £630 with a new waterproof design, iris scanner, huge 6GB of RAM and (allegedly) brand-new Android N. We... 2016-04-18 10:25 8KB www.pcadvisor.co.uk 3 Hadoop exemplifies the promises and the pitfalls of open source - here's why Fast moving and flexible, Hadoop has emerged to meet the data processing challenges of today, but it's not without challenges of its own,Big Data and Analytics ,Hadoop,Hortonworks,Internet of Things,Big Data,MapR,Cloudera,Doug Cutting,Apache Spark,Analytics 2016-04-18 14:32 1KB www.computing.co.uk 4 Brexit won't provide escape route from new EU data protection rules Lawyers warn that GDPR is coming regardless of what happens in June referendum vote,Security,Privacy ,GDPR,data protection,General Data Protection Regulation,European Union,EU Data Protection Regulation,EU referendum 2016-04-18 14:32 3KB www.computing.co.uk 5 CW@50: The changing face of the datacentre over the past 50 years As Computer