Nfc Android Application Development: Unitenfc
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Factory Model Device Model
Factory Model Device Model Acer A1-713 acer_aprilia Acer A1-811 mango Acer A1-830 ducati Acer A3-A10 G1EA3 Acer A3-A10 mtk6589_e_lca Acer A3-A10 zara Acer A3-A20 acer_harley Acer A3-A20FHD acer_harleyfhd Acer Acer E320-orange C6 Acer Aspire A3 V7 Acer AT390 T2 Acer B1-723 oban Acer B1-730 EverFancy D40 Acer B1-730 vespatn Acer CloudMobile S500 a9 Acer DA220HQL lenovo72_we_jb3 Acer DA222HQL N451 Acer DA222HQLA A66 Acer DA222HQLA Flare S3 Power Acer DA226HQ tianyu72_w_hz_kk Acer E330 C7 Acer E330 GT-N7105T Acer E330 STUDIO XL Acer E350 C8n Acer E350 wiko Acer G100W maya Acer G1-715 A510s Acer G1-715 e1808_v75_hjy1_5640_maxwest Acer Icona One 7 vespa Acer Iconia One 7 AT1G* Acer Iconia One 7 G1-725 Acer Iconia One 7 m72_emmc_s6_pcb22_1024_8g1g_fuyin Acer Iconia One 7 vespa2 Acer Iconia One 8 vespa8 Acer Iconia Tab 7 acer_apriliahd Acer Iconia Tab 8 ducati2fhd Acer Iconia Tab 8 ducati2hd Acer Iconia Tab 8 ducati2hd3g Acer Iconia Tab 8 Modelo II - Professor Acer Iconia Tab A100 (VanGogh) vangogh Acer Iconia Tab A200 s7503 Acer Iconia Tab A200 SM-N9006 Acer Iconia Tab A501 ELUGA_Mark Acer Iconia Tab A501 picasso Acer Iconia Tab A510 myPhone Acer Iconia Tab A510 picasso_m Acer Iconia Tab A510 ZUUM_M50 Acer Iconia Tab A701 picasso_mf Acer Iconia Tab A701 Revo_HD2 Acer Iconia TalkTab 7 acer_a1_724 Acer Iconia TalkTab 7 AG CHROME ULTRA Acer Liquid a1 Acer Liquid C1 I1 Acer Liquid C1 l3365 Acer Liquid E1 C10 Acer Liquid E2 C11 Acer Liquid E3 acer_e3 Acer Liquid E3 acer_e3n Acer Liquid E3 LS900 Acer Liquid E3 Quasar Acer Liquid E600 e600 Acer Liquid -
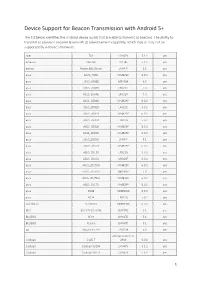
Device Support for Beacon Transmission with Android 5+
Device Support for Beacon Transmission with Android 5+ The list below identifies the Android device builds that are able to transmit as beacons. The ability to transmit as a beacon requires Bluetooth LE advertisement capability, which may or may not be supported by a device’s firmware. Acer T01 LMY47V 5.1.1 yes Amazon KFFOWI LVY48F 5.1.1 yes archos Archos 80d Xenon LMY47I 5.1 yes asus ASUS_T00N MMB29P 6.0.1 yes asus ASUS_X008D MRA58K 6.0 yes asus ASUS_Z008D LRX21V 5.0 yes asus ASUS_Z00AD LRX21V 5.0 yes asus ASUS_Z00AD MMB29P 6.0.1 yes asus ASUS_Z00ED LRX22G 5.0.2 yes asus ASUS_Z00ED MMB29P 6.0.1 yes asus ASUS_Z00LD LRX22G 5.0.2 yes asus ASUS_Z00LD MMB29P 6.0.1 yes asus ASUS_Z00UD MMB29P 6.0.1 yes asus ASUS_Z00VD LMY47I 5.1 yes asus ASUS_Z010D MMB29P 6.0.1 yes asus ASUS_Z011D LRX22G 5.0.2 yes asus ASUS_Z016D MXB48T 6.0.1 yes asus ASUS_Z017DA MMB29P 6.0.1 yes asus ASUS_Z017DA NRD90M 7.0 yes asus ASUS_Z017DB MMB29P 6.0.1 yes asus ASUS_Z017D MMB29P 6.0.1 yes asus P008 MMB29M 6.0.1 yes asus P024 LRX22G 5.0.2 yes blackberry STV100-3 MMB29M 6.0.1 yes BLU BLU STUDIO ONE LMY47D 5.1 yes BLUBOO XFire LMY47D 5.1 yes BLUBOO Xtouch LMY47D 5.1 yes bq Aquaris E5 HD LRX21M 5.0 yes ZBXCNCU5801712 Coolpad C106-7 291S 6.0.1 yes Coolpad Coolpad 3320A LMY47V 5.1.1 yes Coolpad Coolpad 3622A LMY47V 5.1.1 yes 1 CQ CQ-BOX 2.1.0-d158f31 5.1.1 yes CQ CQ-BOX 2.1.0-f9c6a47 5.1.1 yes DANY TECHNOLOGIES HK LTD Genius Talk T460 LMY47I 5.1 yes DOOGEE F5 LMY47D 5.1 yes DOOGEE X5 LMY47I 5.1 yes DOOGEE X5max MRA58K 6.0 yes elephone Elephone P7000 LRX21M 5.0 yes Elephone P8000 -

Compatibility Sheet
COMPATIBILITY SHEET SanDisk Ultra Dual USB Drive Transfer Files Easily from Your Smartphone or Tablet Using the SanDisk Ultra Dual USB Drive, you can easily move files from your Android™ smartphone or tablet1 to your computer, freeing up space for music, photos, or HD videos2 Please check for your phone/tablet or mobile device compatiblity below. If your device is not listed, please check with your device manufacturer for OTG compatibility. Acer Acer A3-A10 Acer EE6 Acer W510 tab Alcatel Alcatel_7049D Flash 2 Pop4S(5095K) Archos Diamond S ASUS ASUS FonePad Note 6 ASUS FonePad 7 LTE ASUS Infinity 2 ASUS MeMo Pad (ME172V) * ASUS MeMo Pad 8 ASUS MeMo Pad 10 ASUS ZenFone 2 ASUS ZenFone 3 Laser ASUS ZenFone 5 (LTE/A500KL) ASUS ZenFone 6 BlackBerry Passport Prevro Z30 Blu Vivo 5R Celkon Celkon Q455 Celkon Q500 Celkon Millenia Epic Q550 CoolPad (酷派) CoolPad 8730 * CoolPad 9190L * CoolPad Note 5 CoolPad X7 大神 * Datawind Ubislate 7Ci Dell Venue 8 Venue 10 Pro Gionee (金立) Gionee E7 * Gionee Elife S5.5 Gionee Elife S7 Gionee Elife E8 Gionee Marathon M3 Gionee S5.5 * Gionee P7 Max HTC HTC Butterfly HTC Butterfly 3 HTC Butterfly S HTC Droid DNA (6435LVW) HTC Droid (htc 6435luw) HTC Desire 10 Pro HTC Desire 500 Dual HTC Desire 601 HTC Desire 620h HTC Desire 700 Dual HTC Desire 816 HTC Desire 816W HTC Desire 828 Dual HTC Desire X * HTC J Butterfly (HTL23) HTC J Butterfly (HTV31) HTC Nexus 9 Tab HTC One (6500LVW) HTC One A9 HTC One E8 HTC One M8 HTC One M9 HTC One M9 Plus HTC One M9 (0PJA1) -
HTC Butterfly
Review Scan this code for more info. To download a barcode app, SMS <f2k> to 56677 from a mobile phone with Internet access and camera. SMARTPHONE HTC Butterfly: The Most Expensive Android Smartphone in India Sleek yet rugged, the Butterfly is a force to reckon with and is equipped with the best configuration found in any smartphone we’ve seen till date — Abhijit Ahaskar TC prefers their smartphones to be rugged and sturdy and that shows Price: `45,000 Key Spec: 5-inch multi-touch, 1080p, in their Butterfly’s unibody build. 441 ppi, Gorilla Glass 2, micro SIM, 3G, It fits comfortably into one hand 4G, WiFi, GPS, NFC, 16 GB internal, 32 H GB via micro SD, 1.5 GHz Quad core as it has been kept thinner and longer like processor, 2GB RAM, Adreno 320, 8MP the iPhone 5. Moreover, while the iPhone has rear with 1080p recording, 2.1MP front a 4 inch screen that isn’t even HD, Butterfly with 1080p recording, 2010mAh battery, has a stunning Gorilla Glass based, 5 inch, 143x70.5x9.1mm, 140g Pros: Great build quality, light form factor, full HD display with a high pixel density of excellent display, great cameras 441ppi. The only other smartphone with this Cons: Expensive much pixel density is the Sony Xperia Z. Write to: [email protected] for The iPhone 5 is lighter than Butterfly, but more info. then at 140g, the Butterfly is far from heavy. It has a striking pair of cameras that can turn out first class full HD videos and photos and have superior display and is thinner and lighter than a a lot of handy functions and modes found in lot of high-end smartphones. -

Electronic 3D Models Catalogue (On July 26, 2019)
Electronic 3D models Catalogue (on July 26, 2019) Acer 001 Acer Iconia Tab A510 002 Acer Liquid Z5 003 Acer Liquid S2 Red 004 Acer Liquid S2 Black 005 Acer Iconia Tab A3 White 006 Acer Iconia Tab A1-810 White 007 Acer Iconia W4 008 Acer Liquid E3 Black 009 Acer Liquid E3 Silver 010 Acer Iconia B1-720 Iron Gray 011 Acer Iconia B1-720 Red 012 Acer Iconia B1-720 White 013 Acer Liquid Z3 Rock Black 014 Acer Liquid Z3 Classic White 015 Acer Iconia One 7 B1-730 Black 016 Acer Iconia One 7 B1-730 Red 017 Acer Iconia One 7 B1-730 Yellow 018 Acer Iconia One 7 B1-730 Green 019 Acer Iconia One 7 B1-730 Pink 020 Acer Iconia One 7 B1-730 Orange 021 Acer Iconia One 7 B1-730 Purple 022 Acer Iconia One 7 B1-730 White 023 Acer Iconia One 7 B1-730 Blue 024 Acer Iconia One 7 B1-730 Cyan 025 Acer Aspire Switch 10 026 Acer Iconia Tab A1-810 Red 027 Acer Iconia Tab A1-810 Black 028 Acer Iconia A1-830 White 029 Acer Liquid Z4 White 030 Acer Liquid Z4 Black 031 Acer Liquid Z200 Essential White 032 Acer Liquid Z200 Titanium Black 033 Acer Liquid Z200 Fragrant Pink 034 Acer Liquid Z200 Sky Blue 035 Acer Liquid Z200 Sunshine Yellow 036 Acer Liquid Jade Black 037 Acer Liquid Jade Green 038 Acer Liquid Jade White 039 Acer Liquid Z500 Sandy Silver 040 Acer Liquid Z500 Aquamarine Green 041 Acer Liquid Z500 Titanium Black 042 Acer Iconia Tab 7 (A1-713) 043 Acer Iconia Tab 7 (A1-713HD) 044 Acer Liquid E700 Burgundy Red 045 Acer Liquid E700 Titan Black 046 Acer Iconia Tab 8 047 Acer Liquid X1 Graphite Black 048 Acer Liquid X1 Wine Red 049 Acer Iconia Tab 8 W 050 Acer -

Phone Compatibility
Phone Compatibility • Compatible with iPhone models 4S and above using iOS versions 7 or higher. Last Updated: February 14, 2017 • Compatible with phone models using Android versions 4.1 (Jelly Bean) or higher, and that have the following four sensors: Accelerometer, Gyroscope, Magnetometer, GPS/Location Services. • Phone compatibility information is provided by phone manufacturers and third-party sources. While every attempt is made to ensure the accuracy of this information, this list should only be used as a guide. As phones are consistently introduced to market, this list may not be all inclusive and will be updated as new information is received. Please check your phone for the required sensors and operating system. Brand Phone Compatible Non-Compatible Acer Acer Iconia Talk S • Acer Acer Jade Primo • Acer Acer Liquid E3 • Acer Acer Liquid E600 • Acer Acer Liquid E700 • Acer Acer Liquid Jade • Acer Acer Liquid Jade 2 • Acer Acer Liquid Jade Primo • Acer Acer Liquid Jade S • Acer Acer Liquid Jade Z • Acer Acer Liquid M220 • Acer Acer Liquid S1 • Acer Acer Liquid S2 • Acer Acer Liquid X1 • Acer Acer Liquid X2 • Acer Acer Liquid Z200 • Acer Acer Liquid Z220 • Acer Acer Liquid Z3 • Acer Acer Liquid Z4 • Acer Acer Liquid Z410 • Acer Acer Liquid Z5 • Acer Acer Liquid Z500 • Acer Acer Liquid Z520 • Acer Acer Liquid Z6 • Acer Acer Liquid Z6 Plus • Acer Acer Liquid Zest • Acer Acer Liquid Zest Plus • Acer Acer Predator 8 • Alcatel Alcatel Fierce • Alcatel Alcatel Fierce 4 • Alcatel Alcatel Flash Plus 2 • Alcatel Alcatel Go Play • Alcatel Alcatel Idol 4 • Alcatel Alcatel Idol 4s • Alcatel Alcatel One Touch Fire C • Alcatel Alcatel One Touch Fire E • Alcatel Alcatel One Touch Fire S • 1 Phone Compatibility • Compatible with iPhone models 4S and above using iOS versions 7 or higher. -

Qualcomm® Quick Charge™ Technology Device List
One charging solution is all you need. Waiting for your phone to charge is a thing of the past. Quick Charge technology is ® designed to deliver lightning-fast charging Qualcomm in phones and smart devices featuring Qualcomm® Snapdragon™ mobile platforms ™ and processors, giving you the power—and Quick Charge the time—to do more. Technology TABLE OF CONTENTS Quick Charge 5 Device List Quick Charge 4/4+ Quick Charge 3.0/3+ Updated 09/2021 Quick Charge 2.0 Other Quick Charge Devices Qualcomm Quick Charge and Qualcomm Snapdragon are products of Qualcomm Technologies, Inc. and/or its subsidiaries. Devices • RedMagic 6 • RedMagic 6Pro Chargers • Baseus wall charger (CCGAN100) Controllers* Cypress • CCG3PA-NFET Injoinic-Technology Co Ltd • IP2726S Ismartware • SW2303 Leadtrend • LD6612 Sonix Technology • SNPD1683FJG To learn more visit www.qualcomm.com/quickcharge *Manufacturers may configure power controllers to support Quick Charge 5 with backwards compatibility. Power controllers have been certified by UL and/or Granite River Labs (GRL) to meet compatibility and interoperability requirements. These devices contain the hardware necessary to achieve Quick Charge 5. It is at the device manufacturer’s discretion to fully enable this feature. A Quick Charge 5 certified power adapter is required. Different Quick Charge 5 implementations may result in different charging times. Devices • AGM X3 • Redmi K20 Pro • ASUS ZenFone 6* • Redmi Note 7* • Black Shark 2 • Redmi Note 7 Pro* • BQ Aquaris X2 • Redmi Note 9 Pro • BQ Aquaris X2 Pro • Samsung Galaxy -

495 3.2H 1 485 2 99
Dashboard Welcome, john doe 24h 24h 24h DashboarD 99 2 1 485 3.2h 495 Total registered users Users with no usage the previous day Average number of messages read aloud Average usage duratation Average number of trips Users Usage duratation App usage 12 months 30 days 14 days 100 98 96 99 4h 96 94 Active users 89 89 88 81 77 73 72 3h 75 61 69 No usage 55 2h 50 29 38 25 29 1h 25 20 19 23 11 11 12 2 4 6 4 2 0 0 28/02 01/03 02/03 03/03 04/03 05/03 06/03 07/03 08/03 09/03 10/03 11/03 12/03 13/03 27/02 28/02 01/03 02/03 03/03 04/03 05/03 06/03 07/03 08/03 09/03 10/03 11/03 12/03 13/03 Top 20 users Last month Today Number of messages read aloud Email Types 30 days 14 days Username Usage duratation John Doe 5h 30min Gary J Henson 5h 10min 12,4% 1600 Kevin B Hicks 4h 0min 12,4% Gary J Henson 3h 5min 1200 Frances T McCoy 3h 0min 800 74,2% Lola C Felton 2h 52min 400 Douglas 2h 45 min Rickey S Mack 2h 30min 0 28/02 01/03 02/03 03/03 04/03 05/03 06/03 07/03 08/03 09/03 10/03 11/03 12/03 13/03 Michael 2h 11 min Gerald 2h 2min Gmail IMAP WhatsApp prev next 1 2 Number of trips by day 600 450 300 150 0 12/02 13/02 14/02 15/02 16/02 17/02 18/02 19/02 20/02 21/02 22/02 23/02 24/02 25/02 26/02 27/02 28/02 01/03 02/03 03/03 04/03 05/03 06/03 07/03 08/03 09/03 10/03 11/03 12/03 13/03 Users Welcome, john doe DashboarD Total RegisteRed useRs: 99 Search by keyword... -
Netflix Downloaden Android Versie
Netflix downloaden android versie Continue take the next steps if you can't find the Netflix app in the App Store for iOS devices or in the Google Play Store for android devices. If you missed the Option to download the Netflix app on your iPhone, iPad or iPod touch, it usually means you'll need to set up certain settings. To download the Netflix app, you'll need to run iOS 12.0 or later on your iOS ﺑﺎﺑﻮوا device. With early versions of iOS (5.0 and later), you can download Netflix only if you've downloaded the app in the past. Follow the steps below to check out your version of iOS. Go to the settings. Scroll down and select Common. Choose information. The version number will appear next to the version. If your iOS version is between 5.0 and 11.4.1 and you've downloaded the Netflix app in the past, you can check the instructions for downloading an earlier version of Netflix on Apple's support site. If you're using iOS 12.0 or later, you can continue troubleshooting below. iOS 12.0 or later If screen time settings are set for your child's device, you should enter a screen time password before changing those settings. Go to the settings. Choose screen time. Choose content and privacy restrictions. Choose from iTunes and the App Store. Select Set Apps. Select Allow. Try Netflix again. Read Apple's support article Understand the limitations if you're in the process of having problems or if you want to know more about the limitations on your iOS device. -

Htc Reports 2013 Fourth-Quarter Results
PRESS RELEASE HTC REPORTS 2013 FOURTH-QUARTER RESULTS TAIPEI, Taiwan – February 10, 2014 – HTC Corporation (the Company, TWSE: 2498), a global leader in mobile innovation and design, today announced consolidated results for its fiscal 2013 fourth quarter ended Dec 31, 2013. The company posted quarterly revenue of NT$42.9 billion and quarterly net profit of NT$0.31 billion, or EPS NT$0.38 per share. Gross margin was 17.8 percent and operating margin was -3.7 percent. “We will continue to stay focused on making the best smartphone and building a compelling mid- range portfolio. Meanwhile, we are going to communicate better with consumers,” said Peter Chou, HTC’s CEO. In China, HTC entered into a strategic partnership with China Mobile and launched HTC One Max as the first TD-LTE device in China. The Company introduced new additions to its mid-range product portfolio, including the HTC Desire 700 dual sim, HTC Desire 601 and HTC Desire 500 across Europe, Asia and Middle East. The Company also launched 4G-LTE edition of the award- winning HTC One and HTC Butterfly s in Taiwan, as well as a champagne gold edition of HTC One in selected markets. In fourth quarter, HTC One claimed yet another Best Phone title by Tbreak Awards, the most prestigious technology and gaming awards in the Middle East. HTC launched “The Most Beautiful Smartphone” campaign through an interactive outdoor billboard at Time Square in New York City, boosting digital engagement with consumers and activation through the holiday sales season. “The Ultimate Smartphone Photo Booth” was launched in partnership with Qualcomm consisting of 130 HTC One phones shooting from 540 degrees of actions and toured across major cities in the United States, showing off the vivid and true-to-life images captured by HTC’s groundbreaking UltraPixel Camera. -

Specifications
TIS Mobile Technology Specifications Version 5 [email protected] www.topimagesystems.com 12 January, 2018 Copyright © TIS, Top Image Systems. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system, translated, transcribed or transmitted in any form, or by any means manual, electric, electronic, electromagnetic, mechanical, chemical, optical, or otherwise, without the prior explicit written permission of TIS. [email protected] www.topimagesystems.com 12 January, 2018 Contents TIS Mobile specifications 4 Requirements 4 Camera 4 CPU / Processor 4 RAM / Memory 4 Data / Network connectivity 5 Apple devices 5 Operating system 5 Devices 5 Supported features 5 Android devices 7 Operating system 7 Devices 7 Supported features 7 TIS Mobile Technology 5 Specifications Page 3 of 9 TIS Mobile specifications This document describes the specifications for devices and operating systems that are supported by TIS Mobile technology. It also lists the minimum requirements and recommended requirements for TIS Mobile technology. Requirements Camera TIS Mobile technology is based on taking a high quality picture of the document, so the quality of the device's camera is very important. The technology works best with a 5.0 MP camera or higher. Some high quality images have also been achieved with devices that have a 3.2 MP camera, but this depends on the device, so using the TIS Mobile technology with less than 5.0 MP is possible, but at your own risk. The camera must also support Auto Focus to use the technology. Minimum: 3.2 MP (device dependent, not supported officially). Recommended: 5.0 MP or higher. -

A List of Compatible Devices
Compatible Mobile Devices List HTC HTC EndeavorU ATRIX HD HTC Droid DNA HTC Evita DROID RAZR MAXX HTC HTC One X+ HTC Ville DROID RAZR HTC One S HTC Primo ELECTRIFY 2 HTC EVO 4G LTE HTC Jewel DEFY XT HTC Desire SV HTC Valentewx DROID 4 HTC Desire C HTC Golf ATRIX 2 HTC one X HTC Fireball ADMIRAL HTC Butterfly HTC Proto ELECTRIFY HTC Desire X HTC DLXJ PHOTON 4G HTC Dream i867 HTC Magic, Samsung TITANIUM HTC Hero Champ Neo DUOS TRIUMPH HTC Click GALAXY Note II ATRIX 4G HTC Bravo GALAXY Music HTC Desire[3] GALAXY S Duos GOOGLE HTC Incredible GALAXY Ace Plus NEXUS 4 HTC Legend GALAXY S III 4G NEXUS 10 HTC Buzz GALAXY S4 NEXUS ONE HTC Espresso GALAXY S4 Mini NEXUS S HTC Liberty[7] GALAXY Beam GALAXY NEXUS HTC Supersonic GALAXY Pocket HTC Ace Black White LG HTC Vision Galaxy Mini 2 OPTIMUS G HTC Glacier GALAXY S III OPTIMUS L7 HTC Gratia GALAXY Y Duos OPTIMUS L5 HTC Stallion GALAXY W OPTIMUS L3 HTC Mecha GALAXY S II 4G OPTIMUS L2 HTC Speedy OMNIA W HTC Vivo GALAXY Xcover Apple HTC Marvel GALAXY Nexus iPhone 3G (all models) HTC Saga GALAXY S II iPhone 3Gs (all models) HTC VivoW GALAXY Ace iPhone 4 (all models) HTC Lexikon GALAXY Gio iPhone 4s (all models) HTC Pyramid GALAXY Fit iPhone 5 (all models) HTC Status GALAXY mini HTC Icon Nexus S iPod touch 2nd Generation HTC Shooter GALAXY S iPod touch 3rd Generation HTC Doubleshot GALAXY 5 iPod touch 4th Generation HTC Rider OMNIA 7 iPod touch 5th Generation HTC ShooterU GALAXY 551 HTC Holiday GALAXY 580 iPad 3rd Generation & newer HTC Bliss Wave 723 HTC Kingdom GALAXY Tab 3 HTC Ruby GALAXY Tab Pro HTC Pico Motorola HTC Pyramid LE DROID RAZR M HTC Runnymede DROID RAZR HD DROID RAZR MAXX HD HTC Vigor PHOTON Q 4G LTE *There may be some compatible devices not shown on this list.