Crack the Code!
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

CS 105 Review Questions #2 in Addition to These Questions
1 CS 105 Review Questions #2 In addition to these questions, remember to look over your labs, homework assignments, readings in the book and your notes. 1. Explain how writing functions inside a Python program can potentially make the program more concise (i.e. take up fewer total lines of code). 2. The following Python statement may cause a ZeroDivisionError. Rewrite the code so that the program will not automatically halt if this error occurs. c = a / b 3. Indicate whether each statement is true or false. a. In ASCII code, the values corresponding to letters in the alphabet are consecutive. b. ASCII code uses the same values for lowercase letters as it does for capital letters. c. In ASCII code, non-printing, invisible characters all have value 0 4. Properties of ASCII representation: a. Each character is stored as how much information? b. If the ASCII code for ‘A’ is 65, then the ASCII code for ‘M’ should be ______. c. Suppose that the hexadecimal ASCII code for the lowercase letter ‘a’ is 0x61. Which lowercase letter would have the hexadecimal ASCII code 0x71 ? d. If we represent the sentence “The cat slept.” in ASCII code (not including the quotation marks), how many bytes does this require? e. How does Unicode differ from ASCII? 5. Estimate the size of the following file. It contains a 500-page book, where a typical page has 2000 characters of ASCII text and one indexed-color image measuring 200x300 pixels. “Indexed color” means that each pixel of an image takes up one byte. -

COS433/Math 473: Cryptography Mark Zhandry Princeton University Spring 2017 Cryptography Is Everywhere a Long & Rich History
COS433/Math 473: Cryptography Mark Zhandry Princeton University Spring 2017 Cryptography Is Everywhere A Long & Rich History Examples: • ~50 B.C. – Caesar Cipher • 1587 – Babington Plot • WWI – Zimmermann Telegram • WWII – Enigma • 1976/77 – Public Key Cryptography • 1990’s – Widespread adoption on the Internet Increasingly Important COS 433 Practice Theory Inherent to the study of crypto • Working knowledge of fundamentals is crucial • Cannot discern security by experimentation • Proofs, reductions, probability are necessary COS 433 What you should expect to learn: • Foundations and principles of modern cryptography • Core building blocks • Applications Bonus: • Debunking some Hollywood crypto • Better understanding of crypto news COS 433 What you will not learn: • Hacking • Crypto implementations • How to design secure systems • Viruses, worms, buffer overflows, etc Administrivia Course Information Instructor: Mark Zhandry (mzhandry@p) TA: Fermi Ma (fermima1@g) Lectures: MW 1:30-2:50pm Webpage: cs.princeton.edu/~mzhandry/2017-Spring-COS433/ Office Hours: please fill out Doodle poll Piazza piaZZa.com/princeton/spring2017/cos433mat473_s2017 Main channel of communication • Course announcements • Discuss homework problems with other students • Find study groups • Ask content questions to instructors, other students Prerequisites • Ability to read and write mathematical proofs • Familiarity with algorithms, analyZing running time, proving correctness, O notation • Basic probability (random variables, expectation) Helpful: • Familiarity with NP-Completeness, reductions • Basic number theory (modular arithmetic, etc) Reading No required text Computer Science/Mathematics Chapman & Hall/CRC If you want a text to follow along with: Second CRYPTOGRAPHY AND NETWORK SECURITY Cryptography is ubiquitous and plays a key role in ensuring data secrecy and Edition integrity as well as in securing computer systems more broadly. -

Simple Substitution and Caesar Ciphers
Spring 2015 Chris Christensen MAT/CSC 483 Simple Substitution Ciphers The art of writing secret messages – intelligible to those who are in possession of the key and unintelligible to all others – has been studied for centuries. The usefulness of such messages, especially in time of war, is obvious; on the other hand, their solution may be a matter of great importance to those from whom the key is concealed. But the romance connected with the subject, the not uncommon desire to discover a secret, and the implied challenge to the ingenuity of all from who it is hidden have attracted to the subject the attention of many to whom its utility is a matter of indifference. Abraham Sinkov In Mathematical Recreations & Essays By W.W. Rouse Ball and H.S.M. Coxeter, c. 1938 We begin our study of cryptology from the romantic point of view – the point of view of someone who has the “not uncommon desire to discover a secret” and someone who takes up the “implied challenged to the ingenuity” that is tossed down by secret writing. We begin with one of the most common classical ciphers: simple substitution. A simple substitution cipher is a method of concealment that replaces each letter of a plaintext message with another letter. Here is the key to a simple substitution cipher: Plaintext letters: abcdefghijklmnopqrstuvwxyz Ciphertext letters: EKMFLGDQVZNTOWYHXUSPAIBRCJ The key gives the correspondence between a plaintext letter and its replacement ciphertext letter. (It is traditional to use small letters for plaintext and capital letters, or small capital letters, for ciphertext. We will not use small capital letters for ciphertext so that plaintext and ciphertext letters will line up vertically.) Using this key, every plaintext letter a would be replaced by ciphertext E, every plaintext letter e by L, etc. -

Battle Management Language: History, Employment and NATO Technical Activities
Battle Management Language: History, Employment and NATO Technical Activities Mr. Kevin Galvin Quintec Mountbatten House, Basing View, Basingstoke Hampshire, RG21 4HJ UNITED KINGDOM [email protected] ABSTRACT This paper is one of a coordinated set prepared for a NATO Modelling and Simulation Group Lecture Series in Command and Control – Simulation Interoperability (C2SIM). This paper provides an introduction to the concept and historical use and employment of Battle Management Language as they have developed, and the technical activities that were started to achieve interoperability between digitised command and control and simulation systems. 1.0 INTRODUCTION This paper provides a background to the historical employment and implementation of Battle Management Languages (BML) and the challenges that face the military forces today as they deploy digitised C2 systems and have increasingly used simulation tools to both stimulate the training of commanders and their staffs at all echelons of command. The specific areas covered within this section include the following: • The current problem space. • Historical background to the development and employment of Battle Management Languages (BML) as technology evolved to communicate within military organisations. • The challenges that NATO and nations face in C2SIM interoperation. • Strategy and Policy Statements on interoperability between C2 and simulation systems. • NATO technical activities that have been instigated to examine C2Sim interoperation. 2.0 CURRENT PROBLEM SPACE “Linking sensors, decision makers and weapon systems so that information can be translated into synchronised and overwhelming military effect at optimum tempo” (Lt Gen Sir Robert Fulton, Deputy Chief of Defence Staff, 29th May 2002) Although General Fulton made that statement in 2002 at a time when the concept of network enabled operations was being formulated by the UK and within other nations, the requirement remains extant. -

IMPLEMENTASI ALGORITMA CAESAR, CIPHER DISK, DAN SCYTALE PADA APLIKASI ENKRIPSI DAN DEKRIPSI PESAN SINGKAT, Lumasms
Prosiding Seminar Ilmiah Nasional Komputer dan Sistem Intelijen (KOMMIT 2014) Vol. 8 Oktober 2014 Universitas Gunadarma – Depok – 14 – 15 Oktober 2014 ISSN : 2302-3740 IMPLEMENTASI ALGORITMA CAESAR, CIPHER DISK, DAN SCYTALE PADA APLIKASI ENKRIPSI DAN DEKRIPSI PESAN SINGKAT, LumaSMS Yusuf Triyuswoyo ST. 1 Ferina Ferdianti ST. 2 Donny Ajie Baskoro ST. 3 Lia Ambarwati ST. 4 Septiawan ST. 5 1,2,3,4,5Jurusan Manajemen Sistem Informasi, Universitas Gunadarma [email protected] Abstrak Short Message Service (SMS) merupakan salah satu cara berkomunikasi yang banyak digunakan oleh pengguna telepon seluler. Namun banyaknya pengguna telepon seluler yang menggunakan layanan SMS, tidak diimbangi dengan faktor keamanan yang ada pada layanan tersebut. Banyak pengguna telepon seluler yang belum menyadari bahwa SMS tidak menjamin integritas dan keamanan pesan yang disampaikan. Ada beberapa risiko yang dapat mengancam keamanan pesan pada layanan SMS, diantaranya: SMS spoofing, SMS snooping, dan SMS interception. Untuk mengurangi risiko tersebut, maka dibutuhkan sebuah sistem keamanan pada layanan SMS yang mampu menjaga integritas dan keamanan isi pesan. Dimana tujuannya ialah untuk menutupi celah pada tingkat keamanan SMS. Salah satu penanggulangannya ialah dengan menerapkan algoritma kriptografi, yaitu kombinasi atas algoritma Cipher Disk, Caesar, dan Scytale pada pesan yang akan dikirim. Tujuan dari penulisan ini adalah membangun aplikasi LumaSMS, dengan menggunakan kombinasi ketiga algoritma kriptografi tersebut. Dengan adanya aplikasi ini diharapkan mampu mengurangi masalah keamanan dan integritas SMS. Kata Kunci: caesar, cipher disk, kriptografi, scytale, SMS. PENDAHULUAN dibutuhkan dikarenakan SMS mudah digunakan dan biaya yang dikeluarkan Telepon seluler merupakan salah untuk mengirim SMS relatif murah. satu hasil dari perkembangan teknologi Namun banyaknya pengguna komunikasi. -

Cryptography: Decoding Student Learning
ABSTRACT PATTERSON, BLAIN ANTHONY. Cryptography: Decoding Student Learning. (Under the direction of Karen Keene.) Cryptography is a content field of mathematics and computer science, developed to keep information safe both when being sent between parties and stored. In addition to this, cryptography can also be used as a powerful teaching tool, as it puts mathematics in a dramatic and realistic setting. It also allows for a natural way to introduce topics such as modular arithmetic, matrix operations, and elementary group theory. This thesis reports the results of an analysis of students' thinking and understanding of cryptog- raphy using both the SOLO taxonomy and open coding as they participated in task based interviews. Students interviewed were assessed on how they made connections to various areas of mathematics through solving cryptography problems. Analyzing these interviews showed that students have a strong foundation in number theoretic concepts such as divisibility and modular arithmetic. Also, students were able to use probabil- ity intuitively to make sense of and solve problems. Finally, participants' SOLO levels ranged from Uni-structural to Extended Abstract, with Multi-Structural level being the most common (three participants). This gives evidence to suggest that students should be given the opportunity to make mathematical connections early and often in their academic careers. Results indicate that although cryptography should not be a required course by mathematics majors, concepts from this field could be introduced -

9 Purple 18/2
THE CONCORD REVIEW 223 A VERY PURPLE-XING CODE Michael Cohen Groups cannot work together without communication between them. In wartime, it is critical that correspondence between the groups, or nations in the case of World War II, be concealed from the eyes of the enemy. This necessity leads nations to develop codes to hide their messages’ meanings from unwanted recipients. Among the many codes used in World War II, none has achieved a higher level of fame than Japan’s Purple code, or rather the code that Japan’s Purple machine produced. The breaking of this code helped the Allied forces to defeat their enemies in World War II in the Pacific by providing them with critical information. The code was more intricate than any other coding system invented before modern computers. Using codebreaking strategy from previous war codes, the U.S. was able to crack the Purple code. Unfortunately, the U.S. could not use its newfound knowl- edge to prevent the attack at Pearl Harbor. It took a Herculean feat of American intellect to break Purple. It was dramatically intro- duced to Congress in the Congressional hearing into the Pearl Harbor disaster.1 In the ensuing years, it was discovered that the deciphering of the Purple Code affected the course of the Pacific war in more ways than one. For instance, it turned out that before the Americans had dropped nuclear bombs on Japan, Purple Michael Cohen is a Senior at the Commonwealth School in Boston, Massachusetts, where he wrote this paper for Tom Harsanyi’s United States History course in the 2006/2007 academic year. -

Cryptanalysis of Mono-Alphabetic Substitution Ciphers Using Genetic Algorithms and Simulated Annealing Shalini Jain Marathwada Institute of Technology, Dr
Vol. 08 No. 01 2018 p-ISSN 2202-2821 e-ISSN 1839-6518 (Australian ISSN Agency) 82800801201801 Cryptanalysis of Mono-Alphabetic Substitution Ciphers using Genetic Algorithms and Simulated Annealing Shalini Jain Marathwada Institute of Technology, Dr. Babasaheb Ambedkar Marathwada University, India Nalin Chhibber University of Waterloo, Ontario, Canada Sweta Kandi Marathwada Institute of Technology, Dr. Babasaheb Ambedkar Marathwada University, India ABSTRACT – In this paper, we intend to apply the principles of genetic algorithms along with simulated annealing to cryptanalyze a mono-alphabetic substitution cipher. The type of attack used for cryptanalysis is a ciphertext-only attack in which we don’t know any plaintext. In genetic algorithms and simulated annealing, for ciphertext-only attack, we need to have the solution space or any method to match the decrypted text to the language text. However, the challenge is to implement the project while maintaining computational efficiency and a high degree of security. We carry out three attacks, the first of which uses genetic algorithms alone, the second which uses simulated annealing alone and the third which uses a combination of genetic algorithms and simulated annealing. Key words: Cryptanalysis, mono-alphabetic substitution cipher, genetic algorithms, simulated annealing, fitness I. Introduction II. Mono-alphabetic substitution cipher Cryptanalysis involves the dissection of computer systems by A mono-alphabetic substitution cipher is a class of substitution unauthorized persons in order to gain knowledge about the ciphers in which the same letters of the plaintext are replaced unknown aspects of the system. It can be used to gain control by the same letters of the ciphertext. -

Block Ciphers
BLOCK CIPHERS MTH 440 Block ciphers • Plaintext is divided into blocks of a given length and turned into output ciphertext blocks of the same length • Suppose you had a block cipher, E(x,k) where the input plaintext blocks,x, were of size 5-bits and a 4-bit key, k. • PT = 10100010101100101 (17 bits), “Pad” the PT so that its length is a multiple of 5 (we will just pad with 0’s – it doesn’t really matter) • PT = 10100010101100101000 • Break the PT into blocks of 5-bits each (x=x1x2x3x4) where each xi is 5 bits) • x1=10100, x2= 01010, x3=11001, x4=01000 • Ciphertext: c1c2c3c4 where • c1=E(x1,k1), c2=E(x2,k2), c3=E(x3,k3), c4=E(x4,k4) • (when I write the blocks next to each other I just mean concatentate them (not multiply) – we’ll do this instead of using the || notation when it is not confusing) • Note the keys might all be the same or all different What do the E’s look like? • If y = E(x,k) then we’ll assume that we can decipher to a unique output so there is some function, we’ll call it D, so that x = D(y,k) • We might define our cipher to be repeated applications of some function E either with the same or different keys, we call each of these applications “round” • For example we might have a “3 round” cipher: y Fk x E((() E E x, k1 , k 2)), k 3 • We would then decipher via 1 x Fk (,, y) D((() D D y, k3 k 2) k 1) S-boxes (Substitution boxes) • Sometimes the “functions” used in the ciphers are just defined by a look up table that are often referred to “S- boxes” •x1 x 2 x 3 S(x 1 x 2 x 3 ) Define a 4-bit function with a 3-bit key 000 -

Secure Communications One Time Pad Cipher
Cipher Machines & Cryptology © 2010 – D. Rijmenants http://users.telenet.be/d.rijmenants THE COMPLETE GUIDE TO SECURE COMMUNICATIONS WITH THE ONE TIME PAD CIPHER DIRK RIJMENANTS Abstract : This paper provides standard instructions on how to protect short text messages with one-time pad encryption. The encryption is performed with nothing more than a pencil and paper, but provides absolute message security. If properly applied, it is mathematically impossible for any eavesdropper to decrypt or break the message without the proper key. Keywords : cryptography, one-time pad, encryption, message security, conversion table, steganography, codebook, message verification code, covert communications, Jargon code, Morse cut numbers. version 012-2011 1 Contents Section Page I. Introduction 2 II. The One-time Pad 3 III. Message Preparation 4 IV. Encryption 5 V. Decryption 6 VI. The Optional Codebook 7 VII. Security Rules and Advice 8 VIII. Appendices 17 I. Introduction One-time pad encryption is a basic yet solid method to protect short text messages. This paper explains how to use one-time pads, how to set up secure one-time pad communications and how to deal with its various security issues. It is easy to learn to work with one-time pads, the system is transparent, and you do not need special equipment or any knowledge about cryptographic techniques or math. If properly used, the system provides truly unbreakable encryption and it will be impossible for any eavesdropper to decrypt or break one-time pad encrypted message by any type of cryptanalytic attack without the proper key, even with infinite computational power (see section VII.b) However, to ensure the security of the message, it is of paramount importance to carefully read and strictly follow the security rules and advice (see section VII). -
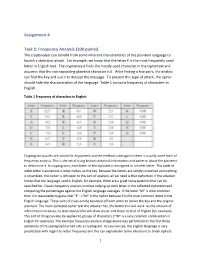
Assignment 4 Task 1: Frequency Analysis (100 Points)
Assignment 4 Task 1: Frequency Analysis (100 points) The cryptanalyst can benefit from some inherent characteristics of the plaintext language to launch a statistical attack. For example, we know that the letter E is the most frequently used letter in English text. The cryptanalyst finds the mostly-used character in the ciphertext and assumes that the corresponding plaintext character is E. After finding a few pairs, the analyst can find the key and use it to decrypt the message. To prevent this type of attack, the cipher should hide the characteristics of the language. Table 1 contains frequency of characters in English. Table 1 Frequency of characters in English Cryptogram puzzles are solved for enjoyment and the method used against them is usually some form of frequency analysis. This is the act of using known statistical information and patterns about the plaintext to determine it. In cryptograms, each letter of the alphabet is encrypted to another letter. This table of letter-letter translations is what makes up the key. Because the letters are simply converted and nothing is scrambled, the cipher is left open to this sort of analysis; all we need is that ciphertext. If the attacker knows that the language used is English, for example, there are a great many patterns that can be searched for. Classic frequency analysis involves tallying up each letter in the collected ciphertext and comparing the percentages against the English language averages. If the letter "M" is most common then it is reasonable to guess that "E"-->"M" in the cipher because E is the most common letter in the English language. -

John F. Byrne's Chaocipher Revealed
John F. Byrne’s Chaocipher Revealed John F. Byrne’s Chaocipher Revealed: An Historical and Technical Appraisal MOSHE RUBIN1 Abstract Chaocipher is a method of encryption invented by John F. Byrne in 1918, who tried unsuccessfully to interest the US Signal Corp and Navy in his system. In 1953, Byrne presented Chaocipher-encrypted messages as a challenge in his autobiography Silent Years. Although numerous students of cryptanalysis attempted to solve the challenge messages over the years, none succeeded. For ninety years the Chaocipher algorithm was a closely guarded secret known only to a handful of persons. Following fruitful negotiations with the Byrne family during the period 2009-2010, the Chaocipher papers and materials have been donated to the National Cryptologic Museum in Ft. Meade, MD. This paper presents a comprehensive historical and technical evaluation of John F. Byrne and his Chaocipher system. Keywords ACA, American Cryptogram Association, block cipher encryption modes, Chaocipher, dynamic substitution, Greg Mellen, Herbert O. Yardley, John F. Byrne, National Cryptologic Museum, Parker Hitt, Silent Years, William F. Friedman 1 Introduction John Francis Byrne was born on 11 February 1880 in Dublin, Ireland. He was an intimate friend of James Joyce, the famous Irish writer and poet, studying together in Belvedere College and University College in Dublin. Joyce based the character named Cranly in Joyce’s A Portrait of the Artist as a Young Man on Byrne, used Byrne’s Dublin residence of 7 Eccles Street as the home of Leopold and Molly Bloom, the main characters in Joyce’s Ulysses, and made use of real-life anecdotes of himself and Byrne as the basis of stories in Ulysses.