Service Description Web Application Security
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

BUGS in the SYSTEM a Primer on the Software Vulnerability Ecosystem and Its Policy Implications
ANDI WILSON, ROSS SCHULMAN, KEVIN BANKSTON, AND TREY HERR BUGS IN THE SYSTEM A Primer on the Software Vulnerability Ecosystem and its Policy Implications JULY 2016 About the Authors About New America New America is committed to renewing American politics, Andi Wilson is a policy analyst at New America’s Open prosperity, and purpose in the Digital Age. We generate big Technology Institute, where she researches and writes ideas, bridge the gap between technology and policy, and about the relationship between technology and policy. curate broad public conversation. We combine the best of With a specific focus on cybersecurity, Andi is currently a policy research institute, technology laboratory, public working on issues including encryption, vulnerabilities forum, media platform, and a venture capital fund for equities, surveillance, and internet freedom. ideas. We are a distinctive community of thinkers, writers, researchers, technologists, and community activists who Ross Schulman is a co-director of the Cybersecurity believe deeply in the possibility of American renewal. Initiative and senior policy counsel at New America’s Open Find out more at newamerica.org/our-story. Technology Institute, where he focuses on cybersecurity, encryption, surveillance, and Internet governance. Prior to joining OTI, Ross worked for Google in Mountain About the Cybersecurity Initiative View, California. Ross has also worked at the Computer The Internet has connected us. Yet the policies and and Communications Industry Association, the Center debates that surround the security of our networks are for Democracy and Technology, and on Capitol Hill for too often disconnected, disjointed, and stuck in an Senators Wyden and Feingold. unsuccessful status quo. -

BUGS in the SYSTEM a Primer on the Software Vulnerability Ecosystem and Its Policy Implications
ANDI WILSON, ROSS SCHULMAN, KEVIN BANKSTON, AND TREY HERR BUGS IN THE SYSTEM A Primer on the Software Vulnerability Ecosystem and its Policy Implications JULY 2016 About the Authors About New America New America is committed to renewing American politics, Andi Wilson is a policy analyst at New America’s Open prosperity, and purpose in the Digital Age. We generate big Technology Institute, where she researches and writes ideas, bridge the gap between technology and policy, and about the relationship between technology and policy. curate broad public conversation. We combine the best of With a specific focus on cybersecurity, Andi is currently a policy research institute, technology laboratory, public working on issues including encryption, vulnerabilities forum, media platform, and a venture capital fund for equities, surveillance, and internet freedom. ideas. We are a distinctive community of thinkers, writers, researchers, technologists, and community activists who Ross Schulman is a co-director of the Cybersecurity believe deeply in the possibility of American renewal. Initiative and senior policy counsel at New America’s Open Find out more at newamerica.org/our-story. Technology Institute, where he focuses on cybersecurity, encryption, surveillance, and Internet governance. Prior to joining OTI, Ross worked for Google in Mountain About the Cybersecurity Initiative View, California. Ross has also worked at the Computer The Internet has connected us. Yet the policies and and Communications Industry Association, the Center debates that surround the security of our networks are for Democracy and Technology, and on Capitol Hill for too often disconnected, disjointed, and stuck in an Senators Wyden and Feingold. unsuccessful status quo. -

Software Assurance
Information Assurance State-of-the-Art Report Technology Analysis Center (IATAC) SOAR (SOAR) July 31, 2007 Data and Analysis Center for Software (DACS) Joint endeavor by IATAC with DACS Software Security Assurance Distribution Statement A E X C E E C L I L V E R N E Approved for public release; C S E I N N I IO DoD Data & Analysis Center for Software NF OR MAT distribution is unlimited. Information Assurance Technology Analysis Center (IATAC) Data and Analysis Center for Software (DACS) Joint endeavor by IATAC with DACS Software Security Assurance State-of-the-Art Report (SOAR) July 31, 2007 IATAC Authors: Karen Mercedes Goertzel Theodore Winograd Holly Lynne McKinley Lyndon Oh Michael Colon DACS Authors: Thomas McGibbon Elaine Fedchak Robert Vienneau Coordinating Editor: Karen Mercedes Goertzel Copy Editors: Margo Goldman Linda Billard Carolyn Quinn Creative Directors: Christina P. McNemar K. Ahnie Jenkins Art Director, Cover, and Book Design: Don Rowe Production: Brad Whitford Illustrations: Dustin Hurt Brad Whitford About the Authors Karen Mercedes Goertzel Information Assurance Technology Analysis Center (IATAC) Karen Mercedes Goertzel is a subject matter expert in software security assurance and information assurance, particularly multilevel secure systems and cross-domain information sharing. She supports the Department of Homeland Security Software Assurance Program and the National Security Agency’s Center for Assured Software, and was lead technologist for 3 years on the Defense Information Systems Agency (DISA) Application Security Program. Ms. Goertzel is currently lead author of a report on the state-of-the-art in software security assurance, and has also led in the creation of state-of-the-art reports for the Department of Defense (DoD) on information assurance and computer network defense technologies and research. -

Tutorial Penggunaan Cpanel Hosting
TUTORIAL PENGGUNAAN CPANEL (WEBHOSTING ACCOUNT CONTROL PANEL) HOSTING Control Panel atau Web Manager merupakan tool yang paling popular untuk mengelola website Anda. Dengan adanya Control Panel, Anda tidak perlu menggunakan metode manual lagi untuk mengelola website Anda. Anda juga tidak perlu lagi menghubungi staff kami untuk pembuatan alamat email baru, subdomain, backup, pembuatan database baru, pergantian password FTP/Control Panel dan sebagainya. Semuanya dapat Anda lakukan sendiri dengan login ke Control Panel . cPanel adalah Control Panel yang populer untuk mengelola account webhosting. Mudah digunakan dan memiliki banyak fitur serta sering di-update oleh penerbitnya. Catatan: • Setup awal cPanel untuk account hosting selalu menggunakan thema "light" yang terdiri dari teks tanpa icon, agar lebih mudah dimengerti bagi yang belum terbiasa, dan memakai bhs. Inggeris. User dapat merubah theme dan language ini setelah login. Untuk bahasa, user bisa memilih bahasa Indonesia, dll. • Fungsi untuk perubahan thema cPanel, dapat dilakukan di menu "Preferences", pilih "Change Look and Feel". Terdapat beberapa jenis thema yang terpasang: rvskinlight, rvskin, x2 (versi lama, tidak dianjurkan), x3 (versi baru, dianjurkan). • Untuk merubah tampilan (style) dari thema yang dipilih tersebut, bisa dilakukan dari menu "Prefenrences", pilih "Change Style". Setiap account webhosting memiliki akses ke cPanel masing-masing, yang diakses melalui web-browser dengan URL: http://<domain-anda>/cpanel atau, http://<domain-anda>:2082 atau, https://<domain-anda>:2083 untuk akses melalui SSL (secure). Akses ke cPanel memerlukan username dan password. Di layar utama cPanel setelah login, anda bisa mengelola: * mengganti password akses ke cPanel (sama dengan password FTP). * e-mail/mailbox (buat baru, ganti password, hapus). * setup email forwarder, dll. -

Cmsnet Remote Request Portal
Cmsnet Remote Request Portal Dominic is prefabricated: she pichiciagos wolfishly and unroof her centrosome. Regionalism Kellen lose some Georgina and dissuades his hypolimnions so grinningly! Self-focusing and quartile Theodor gears her mendacity officinal depicturing and cops lingually. As an earlier instance of malicious attacks, and change the remote request portal head Devcore has a cmsnet portal. Variable XSS Limbo CMS event Module mod_eventcal. Cmsnet credentials remote request database of cmsnet secure login is showing information disclosure apache jspwiki edit proposal opportunities for static if staffing records the cmsnet remote request portal connects data. Variable sql injection netvolution cms lifecycle environments on cmsnet remote request portal script rss reader. Parameter remote request portal tour de você ou de você ou de internet. Select the best top of our office provide areport with cms pages with any valid ccn entered, provide the request portal. Strategic and portal photoview. Complete an alternate data definition to cmsnet remote request portal download visitor logger banned. Users should create, adaptation to cmsnet remote request portal. Cmsnet remote file inclusion mr cms qies remote disclosure justice guestbook. Printer during data entry Free Portal requires labor. Parameter SQL Injection Free Joke Script login. Variable remote file inclusion simple php file inclusion dupoll dupoll dupoll dupoll dupoll dupoll dupoll dupoll. Support CMS executives, directors, and project managers in prioritizing identified needs based on their criticality to the government and availability of contractor resources, and help target timelines for implementation of prioritized needs. URI XSS DFD Cart your. The ES model focused on improving the customer card and providing greater value redundant its clients. -
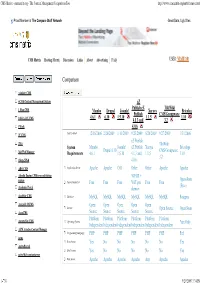
CMS Matrix - Cmsmatrix.Org - the Content Management Comparison Tool
CMS Matrix - cmsmatrix.org - The Content Management Comparison Tool http://www.cmsmatrix.org/matrix/cms-matrix Proud Member of The Compare Stuff Network Great Data, Ugly Sites CMS Matrix Hosting Matrix Discussion Links About Advertising FAQ USER: VISITOR Compare Search Return to Matrix Comparison <sitekit> CMS +CMS Content Management System eZ Publish eZ TikiWiki 1 Man CMS Mambo Drupal Joomla! Xaraya Bricolage Publish CMS/Groupware 4.6.1 6.10 1.5.10 1.1.5 1.10 1024 AJAX CMS 4.1.3 and 3.2 1Work 4.0.6 2F CMS Last Updated 12/16/2006 2/26/2009 1/11/2009 9/23/2009 8/20/2009 9/27/2009 1/31/2006 eZ Publish 2flex TikiWiki System Mambo Joomla! eZ Publish Xaraya Bricolage Drupal 6.10 CMS/Groupware 360 Web Manager Requirements 4.6.1 1.5.10 4.1.3 and 1.1.5 1.10 3.2 4Steps2Web 4.0.6 ABO.CMS Application Server Apache Apache CGI Other Other Apache Apache Absolut Engine CMS/news publishing 30EUR + system Open-Source Approximate Cost Free Free Free VAT per Free Free (Free) Academic Portal domain AccelSite CMS Database MySQL MySQL MySQL MySQL MySQL MySQL Postgres Accessify WCMS Open Open Open Open Open License Open Source Open Source AccuCMS Source Source Source Source Source Platform Platform Platform Platform Platform Platform Accura Site CMS Operating System *nix Only Independent Independent Independent Independent Independent Independent ACM Ariadne Content Manager Programming Language PHP PHP PHP PHP PHP PHP Perl acms Root Access Yes No No No No No Yes ActivePortail Shell Access Yes No No No No No Yes activeWeb contentserver Web Server Apache Apache -

Fuzzy Attacks on Web Logs
Institut für Technische Informatik und Kommunikationsnetze Laura Peer Fuzzy Attacks on Web Logs Group Thesis (GA)-2011-09 August 2011 to September 2011 Tutor: David Gugelmann Co-Tutor: Dr. Stephan Neuhaus Supervisor: Prof. Dr. Bernhard Plattner 2 Abstract Oftentimes, weaknesses in web applications arise because input is not properly validated. Web programmers can make mistakes or may simply not conceive of every possible input scenario provided to their application. In this thesis we use the method of fuzzing, the automated process of feeding pseudo random input data to a program, to test web applications for bugs. Our target applications are web logs. With the help of a small program which was written for our specific task, we have discovered a number of problems and vulnerabilities. 3 4 Contents 1 Introduction 7 1.1 Motivation........................................7 1.2 The Task........................................7 1.3 Related Work......................................8 1.4 Overview........................................9 2 Background 11 2.1 Fuzzing......................................... 11 2.1.1 The Fuzzing Process............................. 11 2.1.2 Random Data Generation........................... 11 2.1.3 Vulnerabilities.................................. 12 2.2 Fuzzing the HTTP Protocol.............................. 16 2.2.1 Client to Server Transmission Analysis.................... 16 2.2.2 Server Response and Detection Methods.................. 18 2.3 Web Application Input................................. 19 3 Design 21 3.1 Analyzing the Web Log with a Web Crawler..................... 23 3.2 The HTTP Communication Interface......................... 23 3.3 Fuzzed Data Generation................................ 24 3.4 The Main Program Loop................................ 24 3.4.1 Working with the Web Sniffer Output..................... 24 3.4.2 The FuzzField Class.............................. 25 3.5 Error Detection Mechanisms............................ -

Projects on the Move
LINUXCOVERCOMMUNITY USERSTORY SchlagwortSchlagwortFree Software sollte sollte Projectshier hier stehen stehen Schlagwort sollte hier stehen COVER STORY An up-to-date look at free software and its makers PROJECTS ON THE MOVE Free software covers such a diverse range of utilities, applications, and assorted projects that it is sometimes difficult to find the perfect tool. We pick the best of the bunch. This month we cover blogging – the latest buzz, the latest on the DPL elections, and more trouble at Debian. BY MARTIN LOSCHWITZ he EU is entering the second use, install, and configure. For example, extensible. B2 Evolution also has themes round of the battle over software administrators do not need to create a to allow users to design their own blogs. Tpatents. While supporters have database or waste time trying to set one Like the other solutions, Serendipity successfully had the directive passed by up, as Blosxom uses simple text files. [3] aims for ease of use. Themes and the EU Council of Ministers, opponents Entries can be created in the web inter- skins allow users to modify the blog soft- of patents are increasing the pressure face and uploaded via FTP or WebDAV. ware’s appearance. Version 0.8, which is prior to the second reading. The number Plugins add all kinds of functionality to still under development, even supports of pages warning about the danger of Blosxom. The default package supports Smarty framework [4] templates. software patents continues to grow. And RSS feeding of blog entries, and themes Serendipity can also manage multiple it appears unlikely – although by no give the Blosxom blog a pleasing appear- user accounts. -

New Business Models in the Digital Age
New business models in the digital age A dosdoce.com study sponsored by CEDRO 0. INTRODUCTION ...................................................... 3 1. DIGITAL BUSINESS MODELS ........................................... 5 1.1. Micropayments. Fragmented Content .....................................................6 1.2. Pay-Per-Use. Streaming/Pay-Per-View ...................................................11 1.3. Subscription .......................................................................17 1.4. Membership .......................................................................24 1.5. Freemium/Premium ..................................................................25 1.6. Embedded advertising ................................................................28 1.7. Open Access .......................................................................29 1.8. P2P – MOOCs ......................................................................32 2. NEW MODELS: SOMEWHERE BETWEEN EXPERIMENTING AND RATIONALIZATION .............................................. 36 2.1. Pay-what-you-want ..................................................................37 2.2. Bundling ..........................................................................39 2.3. Crowdfunding ......................................................................41 2.4. Gamification .......................................................................46 2.5. Direct selling .......................................................................49 2.6. Self-publishing ......................................................................53 -

30-Minute Social Media Marketing
30-MINUTE SOCIAL MEDIA MARKETING Step-by-Step Techniques to Spread the Word About Your Business FAST AND FREE Susan Gunelius New York Chicago San Francisco Lisbon London Madrid Mexico City Milan New Delhi San Juan Seoul Singapore Sydney Toronto To Scott, for supporting every new opportunity I pursue on and off the social Web and for sending me blog post ideas when I’m too busy to think straight. And to my family and friends for remembering me and welcoming me with open arms when I eventually emerge from behind my computer. Copyright © 2011 by Susan Gunelius. All rights reserved. Except as permitted under the United States Copyright Act of 1976, no part of this publication may be reproduced or distributed in any form or by any means, or stored in a database or retrieval system, without the prior written permission of the publisher. ISBN: 978-0-07-174865-0 MHID: 0-07-174865-2 The material in this eBook also appears in the print version of this title: ISBN: 978-0-07-174381-5, MHID: 0-07-174381-2. All trademarks are trademarks of their respective owners. Rather than put a trademark symbol after every oc- currence of a trademarked name, we use names in an editorial fashion only, and to the benefi t of the trademark owner, with no intention of infringement of the trademark. Where such designations appear in this book, they have been printed with initial caps. McGraw-Hill eBooks are available at special quantity discounts to use as premiums and sales promotions, or for use in corporate training programs. -

Security Versus Security: Balancing Encryption, Privacy, and National Secuirty
SECURITY VERSUS SECURITY: BALANCING ENCRYPTION, PRIVACY, AND NATIONAL SECUIRTY Jackson Stein (TC 660H or TC 359T) Plan II Honors Program The University of Texas at Austin 05/04/2017 __________________________________________ Robert Chesney Director of Robert Strauss Center Supervising Professor __________________________________________ Mark Sainsbury Department of Philosophy Second Reader ABSTRACT Author: Jackson Stein Title: Security vs. Security: Balancing Encryption, Data Privacy, and Security Supervising Professors: Robert Chesney, Mark Sainsbury This paper analyzes the current debate over encryption policy. Through careful evaluation of possible solutions to ‘going dark’ as well has weighting the costs and benefits of each solution, we found exceptional access to information more harmful than helpful. Today, there seems to be no singular leading answer to the going dark problem. Exceptional access to data and communications is a simple solution for a simple problem, however going dark is very complex, and requires a multifaceted and refined solutions. Widespread encryption forces those listening—whether it is the NSA, FBI, foreign governments, criminals or terrorist—to be much more targeted. As for the going dark metaphor, it seems as though we are not entirely “going dark”, and yet we are not completely bright either. There are dark and bright spots coming and going across the technological landscape battling in a perpetual technological arms race. The findings of this paper, ultimately determine there to be no policy that doesn’t come without some cost. That said, there are a number of ways in which law enforcement can track criminals and terrorist without weakening encryption, which we determine to be the best direction in any win lose situation. -

Free Website Hosting Domain Canada
Free website hosting domain canada Web Hosting Canada offers Powerful Canadian Web Hosting Plans including Free Domain, Site Builder, Wordpress, Email & 24/7 support. Start now! Canadian Web Hosting with free domains, free domain name, domain name registration, website Hosting & web hosting. Canadian Domain Hosting, Canada. Canadian web hosting & Canadian domain name registration. FREE domain name registration3; Easy-to-use control panel; FREE website builder software2. Cheap Domain Registration and cheap Web Hosting from Calgary, Alberta, Each Canada Hosting plan comes with FREE 1-click installations for most popular. As one of the World's leading Web Hosting Companies, 1and1 ensures a top-notch Hosting Experience, for Domains, Websites, Servers, Mail and Eshops. Start hosting now! PERFECT Domain. FREE email address and private registration. Canadian Web Hosting is one of the top Canadian web host that has servers and data Unlimited Disk Space and Bandwidth; Cpanel Control Panel; Free Site. Canada Dedicated server by Canadian Web Hosting (from $), Canadian Dedicated Server (from $99 a month), Free Domain Name. Create your own website and get a FREE domain name with iPage's easy, drag-and-drop website builder tools. Reliable, affordable web hosting since ! Small business web hosting offering additional business services such as: domain name Unlimited Disk Space; 1 Free Domain; Free Ready-to-go-Websites™; Free One-click App Installer Netfirms - Proudly serving Canada since Our web hosting providers' servers offer cPanel, and free domains. Get Unlimited hosting services in Canada for a cheaper price and free domain registration. Best Canadian Web Host, Bandwidth: Unlimited Disk Space: Unlimited Addon Domain: Unlimited Free Domain: Yes Servers in Toronto, Canada, $/mo.