Security and Privacy Settings of Your Web Browser Are As High As Possible for Your Style of Use
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mapping the Space of Location-Based Services 5
CHARLIEDETAR MAPPINGTHESPACEOFLOCATION- BASEDSERVICES 2 charlie detar Abstract This paper is an attempt to both summarize the current state of Lo- cation Based Services (LBS), and to unpack and problematize the underlying assumptions on which they operate. Location based ser- vices — including applications for mapping and navigation, social networking, gaming, and tourism and information services — are all based on the idea that information about a user’s location can be used to adapt the content and user interface of a service, improving it. However, the “location” used by these systems is usually restricted to data-poor representations such as geographic coordinates, and as such provides an insufficient cue for the rich and culturally contin- gent context embodied in the notion of a “place”. I will argue that developers should consider both the salience of the particular place- or space-based context to their application domain, and the potential impacts the application will have on a user’s sense of place when designing location based services. Contents 1 Introduction: Location, Location, Location 4 2 Space: the geometry of location 7 3 Place: the interpretation of location 12 4 Technology of space and place 17 5 Space, place, and location based services 22 6 Conclusion 45 7 Bibliography 46 1 Introduction: Location, Location, Location Location is a deep component of how we experience the world — it encapsulates not only a mathematical abstraction for our positions in space, but also a rich set of cultural meanings that we associate with particular places, which bound and contextualize our experience. The concept of “place” combines both geography and sociality — one has a “place” in relation to other people (and deviant behavior is “out of place”). -

Location-Aware Applications Considering the Impact of Privacy Legislation
Richard Ferraro Murat Aktihanoglu MANNING Location Aware Applications Richard Ferraro Murat Aktihanoglu Chapter 10 Copyright 2011 Manning Publications brief contents PART 1LBS, THE BIG PICTURE 1 ■ Location-based services: an overview 2 ■ Positioning technologies 3 ■ Mapping 4 ■ Content options PART 2TECHNOLOGY 5 ■ Consumer applications 6 ■ Mobile platforms 7 ■ Connectivity issues 8 ■ Server-side integration PART 3CREATING WINNING LBS BUSINESSES 9 ■ Monetization of location-based services 10 ■ The privacy debate 11 ■ Distributing your application 12 ■ Securing your business idea v The privacy debate This chapter covers Explaining what privacy really means Exploring the two sides of the privacy debate Understanding who manages privacy within location-aware applications Considering the impact of privacy legislation We started part 3, the final part of the book, by discussing in chapter 9 the different ways in which we can monetize location -aware applications and ser vices. Where these services are directed at the general public, extra care is required because of the ongoing debate over privacy of location data. If you were to survey an expert panel of mobile and web professionals about what they thought was the number-one hurdle to a wider and faster spread of LBS, we’d bet a large sum of money that their answer would be “privacy concerns.” More and more, the terms privacy and location are mentioned together (try Googling for the two terms together, and you’ll get over 1,980,000,000 entries), and the driver behind this is that people value their locational privacy above all 214 What do we mean by privacy? 215 other types of privacy (religious privacy, cultural privacy, behavioral privacy, and so on). -

Privacy Considerations for Secure Identification in Social Wireless
Privacy considerations for secure identification in social wireless networks Master’s degree thesis ELENA KOZHEMYAK Academic supervisor: Sonja Buchegger, KTH External supervisor: Christian Gehrmann, SICS Examiner: Johan Håstad, KTH September 2011 iii Abstract This thesis focuses on privacy aspects of identification and key exchange schemes for mobile social networks. In particular, we consider identification schemes that combine wide area mobile communication with short range com- munication such as Bluetooth, WiFi. The goal of the thesis is to identify possi- ble security threats to personal information of users and to define a framework of security and privacy requirements in the context of mobile social networking. The main focus of the work is on security in closed groups and the procedures of secure registration, identification and invitation of users in mobile social net- works. The thesis includes an evaluation of the proposed identification and key exchange schemes and a proposal for a series of modifications that augments its privacy-preserving capabilities. The ultimate design provides secure and ef- fective identity management in the context of, and in respect to, the protection of user identity privacy in mobile social networks. Keywords: mobile social networks, identity privacy, identity management, pseudonyms. iv Sammanfattning Det här examensarbetet handlar om personlig integritet, identifiering och nyckelutbyte i mobila sociala nätverk. Speciellt adresserar vi dessa aspekter för system som kombinerar mobil kommunikation med kort räckviddskommunika- tion som Bluetooth och WiFi. Målet med detta arbete är att identifiera möjliga säkerhetshot mot användarinformation och att ta fram ett ramverk för säkerhet och krav på personlig integritet i mobila sociala nätverk. Tyngdpunkten i ar- betet ligger på säkerhet i slutna grupper och förfaranden för säker registrering, identifiering och inbjudan av användare i mobila sociala nätverk. -

Privacy Leakage in Mobile Online Social Networks
Privacy Leakage in Mobile Online Social Networks Balachander Krishnamurthy, AT&T Labs – Research Craig E. Wills, Worcester Polytechnic Institute Workshop on Online Social Networks Boston, MA USA June 2010 1 Introduction Previously studied the leakage of personally identifiable information via Online Social Networks (OSNs) to third-party aggregators. Trend towards use of mobile devices to access OSNs (Facebook reports 25% of users access OSN via a mobile device every month). Also development of new OSNs—mobile OSNs (mOSNs)—that primarily cater to mobile users. Examples include Brightkite, Foursquare, Gowalla, Loopt, Urbanspoon, Whrrl. Mobile access to Web sites designed specifically for mobile devices and through the development of “apps” that are specific to a site and to a mobile platform. 2 New Privacy Concerns Mobile devices potentially introduce new privacy concerns for mOSNs. These include: • user presence and geographic location • information shared with a mOSN connected to a traditional OSN is also shared with that OSN • unique device identifiers Examine the degree to which leakage of private information is occurring via mOSNs. Related work by Chen&Rahman’08 on analyzing privacy designs of social networking apps focusing on location. 3 Interfaces and Interconnections for mOSNs Mobile Browser Mobile Browser 3rd−Party 3rd−Party 3rd−Party Server Server Server 1 2 3 Mobile Web Site Mobile Web Site Mobile API ConnectOSN API Connect Mobile OSN 1 Providing API Mobile OSN 2 Apps Connect Full Web Site Full Web Site 3rd−Party 3rd−Party Server Server 4 5 Traditional Browser Traditional Browser Interfaces include full Web site, mobile Web site and mobile app. -

Location-Sharing Technologies: Privacy Risks and Controls
Location-Sharing Technologies: Privacy Risks and Controls Janice Y. Tsai, Patrick Gage Kelley, Lorrie Faith Cranor, Norman Sadeh Carnegie Mellon University Pittsburgh, PA [email protected], [email protected], [email protected], [email protected] Updated February 2010 Abstract. Due to the ability of cell phone providers to use cell phone towers to pinpoint users’ locations, federal E911 requirements, the increasing popularity of GPS-capabilities in cellular phones, and the rise of cellular phones for Internet use, a plethora of new applications have been developed that share users’ real-time location information online [27]. This paper evaluates users’ risk and benefit perceptions related to the use of these technologies and the privacy controls of existing location-sharing applications. We conducted an online survey of American Internet users (n = 587) to evaluate users’ perceptions of the likelihood of several location-sharing use scenarios along with the magnitude of the benefit or harm of each scenario (e.g. being stalked or finding people in an emergency). We find that although the majority of our respondents had heard of location-sharing technologies (72.4%), they do not yet understand the potential value of these applications, and they have concerns about sharing their location information online. Most importantly, participants are extremely concerned about controlling who has access to their location. Generally, respondents feel the risks of using location-sharing technologies outweigh the benefits. Respondents felt that the most likely harms would stem from revealing the location of their home to others or being stalked. People felt the strongest benefit were being able to find people in an emergency and being able to track their children. -

Social Networking on Android
MeetYou – Social Networking on Android Alexandra-Mihaela Siriteanu Adrian Iftene Faculty of Computer Science Faculty of Computer Science “Al. I. Cuza” University “Al. I. Cuza” University Iasi, Romania Iasi, Romania [email protected] [email protected] Abstract – This paper aims to present a system that illustrates the According to Wikipedia, Android architecture consists in a social nature of a human being – the need to be always in touch “Linux kernel with middleware, libraries and APIs written in C with family and friends – taking into account facilities available and application software running on a platform which includes on Android platform. The role of this application is to create a Java-compatible libraries based on Apache”, a free type social network in which the users are being alerted when their software and open source license, aspect that makes it very friends are around. This gives them the possibility to set up a meeting or to avoid one. The users have the possibility to check in attracted among developers [3]. We will show in this paper some locations and allow their friends to follow their activity. how we used this architecture in order to build MeetYou Taking into account the security of the users, we included in the application. facilities of the application an option which allows close friends or family to check the user’s location based on a keyword text MeetYou application comes with two new facilities in message. For this purpose, available Android location and comparison with existing solutions. First one is related to the messages services are used for finding an approximate location of fact that users can place their contacts in groups (like family, a mobile phone running this program and then sharing it friends, colleagues, etc.) and they can set different parameters through MeetYou or via SMS. -

Marketing in the Round
ptg7913109 Praise for Marketing in the Round “Dietrich and Livingston have given us a practical guide and checklist for organiza- tions to tear down the organizational silos that stand in the way of getting success- ful marketing results in a networked media age.” —Beth Kanter, coauthor of Networked Nonprofit “Dietrich and Livingston’s latest book, Marketing in the Round, provides readers with an inspiring view into the pragmatic science of seventeenth-century Japanese martial combat and its keen relevance to the reinvigorated practice of ‘Integrated Marketing Communications’ (IMC). The authors teach new empathetic and ubiquitous campaign strategies that bring IMC well into the twenty-first century. Comprehensive social and traditional media strategies are delivered ‘in the round,’ providing practitioners with credible and meaningful tactics, unrestricted by con- ventional limits of reach and frequency.” —Mark Meudt, vice president of communications and marketing for General Dynamics; author of “Supporting Uncle Sam: Ideas for a Unique Integrated Communications Strategy,” Northwestern University, Medill School, Journal of Integrated Marketing Communications, 2011 ptg7913109 “I’ve been following Gini and Geoff for years, and they are the real deal! In this book, the authors offer an actionable, no-nonsense approach to what it will take on every level to actually communicate and connect with your stakeholders. If you have the stomach for breaking down budget silos, holding yourself accountable to measurable objectives, and embracing a commonsense -

The Big Analytics Book Project Is an Aggregation of Articles That Best Represent Thoughts by Some of the Leading Minds in the Data Analytics Industry
The Big Analytics Leaders Collaborative Book Project For, Of, and By the Data Analytics Leaders and Influencers Compiled by Deeksha Joshi & Vishal Kumar Contents SECTION A: STRATEGY FOR THE DATA ANALYTICS LEADERS ................................................... 8 1. Rise of Data Capital by Paul Sonderegger ........................................................................................ 9 2. Investing in Big Data by Bill Pieroni .............................................................................................. 13 3. From Data to Insight: Seven Tips for a Great Data Strategy by Anne Russell ........................ 16 4. Data is Not Always a Substitute for Strategy by Steven Sinofsky ............................................. 20 5. Understand How Your Company Creates Value by Cary Burch ............................................... 26 6. Act Like an Analyst, Think Like a Strategist by Dr. Justin Barclay .......................................... 28 7. The Last Mile of Intuitive Decision Making by Vishal Kumar ................................................. 31 8. Three BIG Reasons Companies are Failing with Big Data Analytics by Ian St. Maurice ..... 36 9. How to Leverage Power of Big Data Analytics in Making Strategic Decisions by Ankush Chopra ........................................................................................................................................................... 40 10. How to Hire the Best Analytics Leaders: And it’s not the way you think! by Tony Branda 43 11. Big Decisions -

Typografisk Mall C/B-Uppsats
On The Market For Successful Uptake of Mobile Social Software by Karina Moreno Torres Department of Mathematics, Natural and Computer Science University of Gävle S-801 76 Gävle, Sweden Email: [email protected] Abstract For the past recent years mobile developers and content providers have been aware of consumers‟ engagement in online social networking. New opportunities are presented when using a mobile device as a medium for social interaction, also referred to as mobile social software. An ever growing effort aimed at various mobile design processes and applications have taken place. To achieve a widespread adoption of mobile social software amongst the main stream mobile consumer, several problem areas have to be taken into consideration, such as the technological possibilities and limitations of mobile phones, security issues regarding user privacy and the different aspects of consumers appeal for social media. This research looks into the overall situation of the current field of research and focuses on the interests in mobile social software amongst users. The study was geographically limited to Malmö, Sweden and focused on a population at the ages of 13-18. Keywords: Location based services, LBS, social media, social network, mobile social software, location awareness, position technology. Preface This research is a senior undergraduate thesis of 10 points and a final work for my Bachelor‟s degree in Computer Science at Gävle University (HiG). I was granted permission by Redikod AB to conduct this study during the summer of 2008. My interest for this thesis originates from the first European Location Based Entertainment Summit which was held in Malmö, Sweden on May 13, 2008. -

Location Cheating: a Security Challenge to Location-Based Social Network Services
CORE Metadata, citation and similar papers at core.ac.uk Provided by UNL | Libraries University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln Faculty Publications from the Department of Electrical & Computer Engineering, Department Electrical and Computer Engineering of 2011 Location Cheating: A Security Challenge to Location-based Social Network Services Wenbo He University of Nebraska-Lincoln, [email protected] Xue Liu McGill University, [email protected] Mai Ren University of Nebraska-Lincoln, [email protected] Follow this and additional works at: https://digitalcommons.unl.edu/electricalengineeringfacpub Part of the Electrical and Computer Engineering Commons He, Wenbo; Liu, Xue; and Ren, Mai, "Location Cheating: A Security Challenge to Location-based Social Network Services" (2011). Faculty Publications from the Department of Electrical and Computer Engineering. 205. https://digitalcommons.unl.edu/electricalengineeringfacpub/205 This Article is brought to you for free and open access by the Electrical & Computer Engineering, Department of at DigitalCommons@University of Nebraska - Lincoln. It has been accepted for inclusion in Faculty Publications from the Department of Electrical and Computer Engineering by an authorized administrator of DigitalCommons@University of Nebraska - Lincoln. 2011 31st International Conference on Distributed Computing Systems Location Cheating: A Security Challenge to Location-based Social Network Services Wenbo He Xue Liu Mai Ren Electrical Engineering Department School of Computer Science Computer Science and Engineering University of Nebraska-Lincoln McGill University University of Nebraska-Lincoln Email: [email protected] Email: [email protected] Email: [email protected] Abstract—Location-based mobile social network services such In this paper, we use foursquare as an example to investigate as foursquare and Gowalla have grown exponentially over the the vulnerability in location-based social network services. -
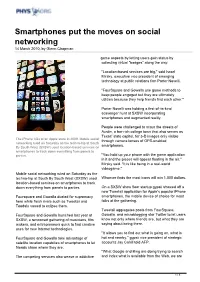
Smartphones Put the Moves on Social Networking 14 March 2010, by Glenn Chapman
Smartphones put the moves on social networking 14 March 2010, by Glenn Chapman game aspects by letting users gain status by collecting virtual "badges" along the way. "Location-based services are big," said Israel Mirsky, executive vice president of emerging technology at public relations firm Porter Novelli. "FourSquare and Gowalla use game methods to keep people engaged but they are ultimately utilities because they help friends find each other." Porter Novelli was holding a first-of-its-kind scavenger hunt at SXSW incorporating smartphones and augmented reality. People were challenged to scour the streets of Austin, a bar-rich college town that also serves as Texas' state capitol, for 3-D images only visible The iPhone 3Gs at an Apple store in 2009. Mobile social through camera lenses of GPS-enabled networking ruled on Saturday as the techno-hip at South By South West (SXSW) used location-based services on smartphones. smartphones to track down everything from panels to parties. "You hold up your phone with the game application in it and the pieces will appear floating in the air," Mirsky said. "It is like being in a real-world videogame." Mobile social networking ruled on Saturday as the techno-hip at South By South West (SXSW) used Whoever finds the most icons will win 1,000 dollars. location-based services on smartphones to track down everything from panels to parties. On a SXSW show floor startup gypsii showed off a new Tweetsii application for Apple's popular iPhone Foursquare and Gowalla dueled for supremacy smartphones, the mobile device of choice for most here while fresh rivals such as Tweetsii and folks at the gathering. -

Geosentric Oyj Stock Exchange Release April 29, 2011 at 17:10
GeoSentric Oyj Stock Exchange Release April 29, 2011 at 17:10 FINANCIAL STATEMENTS RELEASE FOR FINANCIAL YEAR 2010 The Annual Report 2010 of GeoSentric Oyj has been published on the Company’s web site. The Annual Report is available at www.geosentric.com. Summary of key figures Review of October – December 2010 Operational overview Material events in the year 2010 Material events after the end of the financial year Review of the financial position and the financial results Sufficient Liquidity Outlook Assessment of significant operational risks Review of R&D-activities Change in Accounting Practices Investments and financing Personnel and organization Environmental issues Board of Directors and auditors Group Structure Board authorization Structural arrangements and changes in amounts of shares Company shares and shareholders Board proposal for distribution of profit SUMMARY OF KEY FIGURES Key figures summarizing the Group’s financial position and financial results from continuing operations (teuros if not indicated otherwise): In period 4Q/2010 2010 4Q/2009 2009 Net sales 39 54 0 4 Operating result -1752 -9536 -3358 -13916 Basic earnings per share -0.00 -0.01 -0.00 -0.02 (eur) At the end of period Total assets 1420 8893 Shareholders´ equity -15024 -2236 Total liabilities 16444 11129 REVIEW OF OCTOBER – DECEMBER 2010 The Company has also continued implementing its business plan and the required cost reductions to meet the conditions of the additional financing approved by the Annual General Meeting on June 30, 2010. Cost reductions were implemented as headcount reductions in all areas of the business as well as consolidation of engineering resources from higher cost regions of the world into China.