Titans and Trolls Enter the Open-Source Arena Debra Brubaker Burns
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Vulcano User Guide
MONSOON MULTIMEDIA User Guide © 2010 Monsoon Multimedia, Inc. All Rights Reserved. User Guide Contents INTRODUCTION ................................................................................................................................................ 2 HOOK UP THE CABLES ...................................................................................................................................... 4 CONFIGURE YOUR VULKANO ............................................................................................................................. 7 USING YOUR VULKANO FEATURES ................................................................................................................... 15 LIVE TV .......................................................................................................................................................... 15 GUIDE ........................................................................................................................................................... 16 MY RECORDINGS ............................................................................................................................................. 19 INTERNET APPS ............................................................................................................................................... 21 SETTINGS ....................................................................................................................................................... 22 SETUP .......................................................................................................................................................... -

Practice Tips for Open Source Licensing Adam Kubelka
Santa Clara High Technology Law Journal Volume 22 | Issue 4 Article 4 2006 No Free Beer - Practice Tips for Open Source Licensing Adam Kubelka Matthew aF wcett Follow this and additional works at: http://digitalcommons.law.scu.edu/chtlj Part of the Law Commons Recommended Citation Adam Kubelka and Matthew Fawcett, No Free Beer - Practice Tips for Open Source Licensing, 22 Santa Clara High Tech. L.J. 797 (2005). Available at: http://digitalcommons.law.scu.edu/chtlj/vol22/iss4/4 This Article is brought to you for free and open access by the Journals at Santa Clara Law Digital Commons. It has been accepted for inclusion in Santa Clara High Technology Law Journal by an authorized administrator of Santa Clara Law Digital Commons. For more information, please contact [email protected]. ARTICLE NO FREE BEER - PRACTICE TIPS FOR OPEN SOURCE LICENSING Adam Kubelkat Matthew Fawcetttt I. INTRODUCTION Open source software is big business. According to research conducted by Optaros, Inc., and InformationWeek magazine, 87 percent of the 512 companies surveyed use open source software, with companies earning over $1 billion in annual revenue saving an average of $3.3 million by using open source software in 2004.1 Open source is not just staying in computer rooms either-it is increasingly grabbing intellectual property headlines and entering mainstream news on issues like the following: i. A $5 billion dollar legal dispute between SCO Group Inc. (SCO) and International Business Machines Corp. t Adam Kubelka is Corporate Counsel at JDS Uniphase Corporation, where he advises the company on matters related to the commercialization of its products. -

Recent Developments in Cybersecurity Melanie J
American University Business Law Review Volume 2 | Issue 2 Article 1 2013 Fiddling on the Roof: Recent Developments in Cybersecurity Melanie J. Teplinsky Follow this and additional works at: http://digitalcommons.wcl.american.edu/aublr Part of the Law Commons Recommended Citation Teplinsky, Melanie J. "Fiddling on the Roof: Recent Developments in Cybersecurity." American University Business Law Review 2, no. 2 (2013): 225-322. This Article is brought to you for free and open access by the Washington College of Law Journals & Law Reviews at Digital Commons @ American University Washington College of Law. It has been accepted for inclusion in American University Business Law Review by an authorized administrator of Digital Commons @ American University Washington College of Law. For more information, please contact [email protected]. ARTICLES FIDDLING ON THE ROOF: RECENT DEVELOPMENTS IN CYBERSECURITY MELANIE J. TEPLINSKY* TABLE OF CONTENTS Introduction .......................................... ..... 227 I. The Promise and Peril of Cyberspace .............. ........ 227 II. Self-Regulation and the Challenge of Critical Infrastructure ......... 232 III. The Changing Face of Cybersecurity: Technology Trends ............ 233 A. Mobile Technology ......................... 233 B. Cloud Computing ........................... ...... 237 C. Social Networking ................................. 241 IV. The Changing Face of Cybersecurity: Cyberthreat Trends ............ 244 A. Cybercrime ................................. ..... 249 1. Costs of Cybercrime -

Developer Survey
Developer Survey Questions requiring a response are in r ed . Questions in which a response is NOT required are in blue. This survey is a critical element of the developers workshop. We are using it to capture nuts and bolts information about codes within the community so that we can assess the landscape before the workshop and use this information to drive the discussions. Please collaborate to provide only one submission per code and submit your response using the online survey: h ttps://ucdavis.co1.qualtrics.com/jfe/form/SV_57wtv4gpuaowTsh Basic Information Code identification 1. What is the name of the code? [small text box] 2. Who are the primary authors/maintainers? [medium text box] 3. URL of webpage for the code (if different than the version control repository) [small text box] 4. URL of version control repository (if public) [small text box] Software 1. Which license(s) do you use? Select all that apply. a. Apache license b. BSD license c. GNU General Public License d. GNU Lesser General Public License e. MIT license f. Mozilla Public License g. Common Development and Distribution License h. Eclipse Public License i. Other. Please specify [small text box] j. No license 2. What programming language(s) is your code currently written in? Select all that apply a. Fortran 77 b. Fortran 90 or later c. C d. C++ e. Go f. Python g. Julia h. Matlab i. Other. Please specify. [small text box] 3. List the primary (high-level) code dependencies (e.g., PETSc, deal.ii, FEniCS) [medium text box] 4. List any additional (low-level) code dependencies (e.g., MPI, NetCDF, HDF5) [medium text box] 5. -
SFLC V Conservancy
Trademark Trial and Appeal Board Electronic Filing System. http://estta.uspto.gov ESTTA Tracking number: ESTTA863914 Filing date: 12/11/2017 IN THE UNITED STATES PATENT AND TRADEMARK OFFICE BEFORE THE TRADEMARK TRIAL AND APPEAL BOARD Proceeding 92066968 Party Defendant Software Freedom Conservancy Correspondence PAMELA S CHESTECK Address CHESTEK LEGAL P O BOX 2492 RALEIGH, NC 27602 UNITED STATES Email: [email protected] Submission Motion for Summary Judgment Yes, the Filer previously made its initial disclosures pursuant to Trademark Rule 2.120(a); OR the motion for summary judgment is based on claim or issue pre- clusion, or lack of jurisdiction. The deadline for pretrial disclosures for the first testimony period as originally set or reset: 07/20/2018 Filer's Name Pamela S Chestek Filer's email [email protected] Signature /Pamela S Chestek/ Date 12/11/2017 Attachments Motion for SJ on affirmative defenses-signed.pdf(756280 bytes ) Kuhn-Declara- tion_summary-judgment_as-submitted_reduced-size-signed.pdf(2181238 bytes ) Sandler-declara- tion_summary-judgment_as-submitted-reduced-size-signed.pdf(1777273 bytes ) Chestek declaration_summary-judgment-signed-with-exhibits.pdf(2003142 bytes ) IN THE UNITED STATES PATENT AND TRADEMARK OFFICE BEFORE THE TRADEMARK TRIAL AND APPEAL BOARD In the Mater of Registraion No. 4212971 Mark: SOFTWARE FREEDOM CONSERVANCY Registraion date: September 25, 2012 Sotware Freedom Law Center Peiioner, v. Cancellaion No. 92066968 Sotware Freedom Conservancy Registrant. RESPONDENT’S MOTION FOR SUMMARY JUDGMENT ON ITS AFFIRMATIVE DEFENSES Introducion The Peiioner, Sotware Freedom Law Center (“SFLC”), is a provider of legal services. It had the idea to create an independent enity that would ofer inancial and administraive services for free and open source sotware projects. -

Report on the 2020 FOSS Contributor Survey
Report on the 2020 FOSS Contributor Survey The Linux Foundation & The Laboratory for Innovation Science at Harvard Frank Nagle Harvard Business School David A. Wheeler The Linux Foundation Hila Lifshitz-Assaf New York University Haylee Ham Jennifer L. Hoffman Laboratory for Innovation Science at Harvard Acknowledgments This report and the research behind it would not have been possible without the leadership of the Core Infrastructure Initiative’s Advisory Committee, composed of Josh Corman, Steve Lipner, Audris Mockus, Henning Piezunka, and Sam Ransbotham. Frank Nagle would also like to thank his fellow co-directors of the Core Infrastructure Initiative, Jim Zemlin at the Linux Foundation and Karim Lakhani at the Laboratory for Innovation Science at Harvard, for their counsel and direction throughout this project. Gratitude and thanks to Michael Dolan and Kate Stewart at the Linux Foundation for their ongoing commitment to this undertaking. Thank you to James Dana for laying the initial groundwork for this survey. Finally — and perhaps, most importantly — thank you to all the individuals who contribute to FOSS projects. Without their tireless efforts, our core digital infrastructure and the feats enabled by it would not be sustainable. REVISED: This report has been updated since its original release on 8 December 2020. This second version, released on 10 December 2020, corrects errors found in the original text and graphics. Contents Executive Summary 4 Introduction 7 Methodology 9 Overview of Findings 10 Demographics 10 Figure 1: Gender -

PATENT PLEDGES Jorge L. Contreras*
PATENT PLEDGES Jorge L. Contreras* ABSTRACT An increasing number of firms are making public pledges to limit the enforcement of their patents. In doing so, they are entering a little- understood middle ground between the public domain and exclusive property rights. The best-known of these patent pledges are FRAND commitments, in which patent holders commit to license their patents to manufacturers of standardized products on terms that are “fair, reasonable and non-discriminatory.” But patent pledges have been appearing in settings well beyond standard-setting, including open source software, green technology and the life sciences. As a result, this increasingly prevalent private ordering mechanism is beginning to reshape the role and function of patents in the economy. Despite their proliferation, little scholarship has explored the phenomenon of patent pledges beyond FRAND commitments and standard- setting. This article fills this gap by providing the first comprehensive descriptive account of patent pledges across the board. It offers a four-part taxonomy of patent pledges based on the factors that motivate patent holders to make them and the effect they are intended to have on other market actors. Using this classification system, it argues that pledges likely to induce reliance in other market actors should be treated as “actionable” * Associate Professor, S.J. Quinney College of Law, University of Utah and Senior Policy Fellow, American University Washington College of Law. The author thanks Jonas Anderson, Clark Asay, Marc Sandy Block, Mark Bohannon, Matthew Bye, Michael Carrier, Michael Carroll, Colleen Chien, Thomas Cotter, Carter Eltzroth, Carissa Hessick, Meredith Jacob, Jay Kesan, Anne Layne-Farrar, Irina Manta, Sean Pager, Gideon Parchomovsky, Arti Rai, Amelia Rinehart, Cliff Rosky, Daniel Sokol and Duane Valz for their helpful comments, suggestions and discussion of this article and contributions of data to the Patent Pledge Database at American University. -
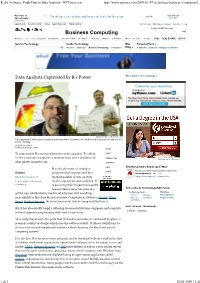
R, the Software, Finds Fans
R, the Software, Finds Fans in Data Analysts - NYTimes.com http://www.nytimes.com/2009/01/07/technology/business-computing/0... W elcom e to Get Started TimesPeople Lets You Share and Discover the Best of NYTimes.com 12:48 PM Tim esPeople No, thanks W hat‘s this? HOME PAGE TODAY'S PAPER VIDEO MOST POPULAR TIMES TOPICS My Account W elcome, corostat Log Out Help Search All NYTimes.com Business Com puting WORLD U.S. N.Y. / REGION BUSINESS TECHNOLOGY SCIENCE HEALTH SPORTS OPINION ARTS STYLE TRAVEL JOBS REAL ESTATE AUTOS Search Technology Inside Technology Bits Personal Tech » Internet Start-Ups Business Computing Companies Blog » Cellphones, Cameras, Computers and more Data Analysts Captivated by R‘s Power More Articles in Technology » Stuart Isett for The New York Times R first appeared in 1996, when the statistics professors Robert Gentleman, left, and Ross Ihaka released the code as a free software package. By ASHLEE VANCE Published: January 6, 2009 E-MAIL To some people R is just the 18th letter of the alphabet. To others, PRINT it‘s the rating on racy movies, a measure of an attic‘s insulation or SINGLE PAGE Advertise on NYTimes.com what pirates in movies say. REPRINTS SAVE Breaking News Alerts by E-Mail R is also the name of a popular SHARE Sign up to be notified when important news breaks. Related programming language used by a colombi@ unibg.it Bits: R You Ready for R? growing number of data analysts Change E-mail Address | Privacy Policy The R Project for Statistical inside corporations and academia. -

THE DEFENSIVE PATENT PLAYBOOK James M
THE DEFENSIVE PATENT PLAYBOOK James M. Rice† Billionaire entrepreneur Naveen Jain wrote that “[s]uccess doesn’t necessarily come from breakthrough innovation but from flawless execution. A great strategy alone won’t win a game or a battle; the win comes from basic blocking and tackling.”1 Companies with innovative ideas must execute patent strategies effectively to navigate the current patent landscape. But in order to develop a defensive strategy, practitioners must appreciate the development of the defensive patent playbook. Article 1, Section 8, Clause 8 of the U.S. Constitution grants Congress the power to “promote the Progress of Science and useful Arts, by securing for limited Times to Authors and Inventors the exclusive Right to their respective Writings and Discoveries.”2 Congress attempts to promote technological progress by granting patent rights to inventors. Under the utilitarian theory of patent law, patent rights create economic incentives for inventors by providing exclusivity in exchange for public disclosure of technology.3 The exclusive right to make, use, import, and sell a technology incentivizes innovation by enabling inventors to recoup the costs of development and secure profits in the market.4 Despite the conventional theory, in the 1980s and early 1990s, numerous technology companies viewed patents as unnecessary and chose not to file for patents.5 In 1990, Microsoft had seven utility patents.6 Cisco © 2015 James M. Rice. † J.D. Candidate, 2016, University of California, Berkeley, School of Law. 1. Naveen Jain, 10 Secrets of Becoming a Successful Entrepreneur, INC. (Aug. 13, 2012), http://www.inc.com/naveen-jain/10-secrets-of-becoming-a-successful- entrepreneur.html. -

Eclipse IP Management Modernization Sharon Corbett MODERNIZATION
Eclipse IP Management Modernization Sharon Corbett MODERNIZATION ● Eclipse IP - About ● Issue Statement WELCOME ● Objectives/Benefits ● License Compliance ● Self Service ● New Process Overview ● Futures ● Best Practices ● OSCM ● Wrap Up Eclipse Intellectual Property Management > Eclipse IP Policy (Board Approved) ○ Defines mechanism for accepting and licensing the intellectual property developed and leveraged by Eclipse projects > Legal Agreements ○ Formal - ECA, Committer Agreements, Working Group Participation Agreements > Due Diligence Review Process ○ Provenance, License Compatibility, Scanning for Anomalies ○ IP Ticket (CQ) > Commercial Adoption (Confidence/Safe) > High Bar, Rigorous, Well Respected COPYRIGHT (C) 2019, ECLIPSE FOUNDATION, INC. | MADE AVAILABLE UNDER THE ECLIPSE PUBLIC LICENSE 2.0 (EPL-2.0) What’s at Issue? > Eclipse IP Policy and Procedures (2004) > Significant changes over time > Cannot support agile development nor continuous delivery > Impossible to scale to modern day technology (Node.JS, Electron, NPM, etc.) > Burdensome - Lack of Automation COPYRIGHT (C) 2019, ECLIPSE FOUNDATION, INC. | MADE AVAILABLE UNDER THE ECLIPSE PUBLIC LICENSE 2.0 (EPL-2.0) The Time has Arrived ... > Bring Eclipse IP Policy and Process in line with contemporary expectations! COPYRIGHT (C) 2019, ECLIPSE FOUNDATION, INC. | MADE AVAILABLE UNDER THE ECLIPSE PUBLIC LICENSE 2.0 (EPL-2.0) Eclipse IP Governance Approach (Redefined) > Revise the IP Review requirements for third party content > Update IP Policy ○ Change due diligence approach for -

Linux at 25 PETERHISTORY H
Linux at 25 PETERHISTORY H. SALUS Peter H. Salus is the author of A n June 1991, at the USENIX conference in Nashville, BSD NET-2 was Quarter Century of UNIX (1994), announced. Two months later, on August 25, Linus Torvalds announced Casting the Net (1995), and The his new operating system on comp.os.minix. Today, Android, Google’s Daemon, the Gnu and the Penguin I (2008). [email protected] version of Linux, is used on over two billion smartphones and other appli- ances. In this article, I provide some history about the early years of Linux. Linus was born into the Swedish minority of Finland (about 5% of the five million Finns). He was a “math guy” throughout his schooling. Early on, he “inherited” a Commodore VIC- 20 (released in June 1980) from his grandfather; in 1987 he spent his savings on a Sinclair QL (released in January 1984, the “Quantum Leap,” with a Motorola 68008 running at 7.5 MHz and 128 kB of RAM, was intended for small businesses and the serious hobbyist). It ran Q-DOS, and it was what got Linus involved: One of the things I hated about the QL was that it had a read-only operating system. You couldn’t change things ... I bought a new assembler ... and an editor.... Both ... worked fine, but they were on the microdrives and couldn’t be put on the EEPROM. So I wrote my own editor and assembler and used them for all my programming. Both were written in assembly language, which is incredibly stupid by today’s standards. -

Apache Tomcat 9
Apache Tomcat 9 Preview Mark Thomas, September 2015 © 2015 Pivotal Software, Inc. All rights reserved. 2 Introduction Apache Tomcat committer since December 2003 – [email protected] Tomcat 8 release manager Member of the Servlet, WebSocket and EL expert groups Consultant Software Engineer @ Pivotal Currently focused on Apache Tomcat 9 © 2015 Pivotal Software, Inc. All rights reserved. 3 Agenda Specification mandated new features Tomcat specific new features Tomcat features removed Internal changes © 2015 Pivotal Software, Inc. All rights reserved. 4 Tomcat versions Minimum 1st Stable Tomcat JavaEE Servlet JSP EL WebSocket JASPIC EOL Java SE Release 5.x 4 1.4 2.4 2.0 N/A N/A N/A 08 2004 09 2012 6.x 5 5 2.5 2.1 2.1 N/A N/A 02 2007 12 2016 7.x 6 6 3.0 2.2 2.2 1.1 N/A 01 2011 TBD 8.x 7 7 3.1 2.3 3.0 1.1 N/A 02 2014 TBD 9.x 8 8 4.0 2.4? 3.1? 2.0? 1.1? Q4 2016? TBD © 2015 Pivotal Software, Inc. All rights reserved. 5 Specification changes © 2015 Pivotal Software, Inc. All rights reserved. 6 Specifications JavaEE 8 Key elements – HTML 5.0 – HTTP/2 – Simplification – Better integration for managed beans – Better infrastructure for the cloud © 2015 Pivotal Software, Inc. All rights reserved. 7 Specifications Servlet 4.0 Work started, stalled and is now starting again – Driven by JavaOne HTTP/2 Ease of use improvements – HttpFilter, default methods Clarifications – Starting to make progress © 2015 Pivotal Software, Inc.