Self-Test Linux/UNIX Fundamentals
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

UNIX Shell Programming (15CS35) Solution Internal Assessment
UNIX Shell Programming (15CS35) Solution Internal Assessment- II November - 2016 1. Explain significance of following commands (2x5=10 M) i. cp ?????? progs Wild card ? matches any single character, hence the above command (cp) copies files whose names are six in length to progs directory ii. ls *.[xyz]* Wild card * matches any number of characters, hence the above command (ls) lists all the files having extension as either x, or y or z. iii. ls jones[0-9][0- 9][0-9] In the above command the character class[0-9] matches any digit between 0 to 9. Hence the above command lists all the files beginning with jones and having last three characters as any digit between 0 to 9. iv. echo * The above command lists all the file in the current directory. v. cp foo foo* The above command copies the file foo to file called foo*. Here the wild card * loses its meaning. 1. Write UNIX commands for the following (2 X 5= 10 M) i. Find and replace all the occurrences of unix with UNIX in the file after confirming the user. : 1,$s/unix/UNIX/gc ii. List all the files in the current directory which names are having exactly 5 characters and any number of characters in their extension. ls ?????.* iii. Copy all files stored in /home/vtu with .c, .cpp and .java extensions to progs sub- directory in current directory cp /home/vtu/*.{c,cpp,java} ./progs iv. Delete all files containing agra or agar in their file names. rm *ag[ra][ar]* v. -
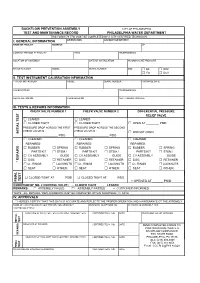
BFP Test Form
BACKFLOW PREVENTION ASSEMBLY CITY OF PHILADELPHIA TEST AND MAINTENANCE RECORD PHILADELPHIA WATER DEPARTMENT THIS FORM (79-770) MUST BE COMPLETED BY A CITY CERTIFIED TECHNICIAN I. GENERAL INFORMATION ORIENTATION ACCOUNT OR METER # NAME OF FACILITY ADDRESS ZIP CONTACT PERSON AT FACILITY TITLE TELEPHONE NO. LOCATION OF ASSEMBLY DATE OF INSTALLATION INCOMING LINE PRESSURE MANUFACTURER MODEL SERIAL NUMBER SIZE □ DS □ RPZ □ FS □ DCV II. TEST INSTRUMENT CALIBRATION INFORMATION TYPE OF INSTRUMENT MODEL SERIAL NUMBER PURCHASE DATE CALIBRATED BY TELEPHONE NO. REGISTRATION NO. CALIBRATED ON NEXT CALIBRATION DUE III. TESTS & REPAIRS INFORMATION CHECK VALVE NUMBER 1 CHECK VALVE NUMBER 2 DIFFERENTIAL PRESSURE RELIEF VALVE □ LEAKED □ LEAKED □ CLOSED TIGHT □ CLOSED TIGHT □ OPEN AT ________ PSID PRESSURE DROP ACROSS THE FIRST PRESSURE DROP ACROSS THE SECOND CHECK VALVE IS : CHECK VALVE IS : INITIAL TEST INITIAL □ DID NOT OPEN ______________________ PSID ______________________ PSID □ CLEANED □ CLEANED □ CLEANED REPAIRED: REPAIRED: REPAIRED: □ RUBBER □ SPRING □ RUBBER □ SPRING □ RUBBER □ SPRING PARTS KIT □ STEM / PARTS KIT □ STEM / PARTS KIT □ STEM / □ CV ASSEMBLY GUIDE □ CV ASSEMBLY GUIDE □ CV ASSEMBLY GUIDE □ DISC □ RETAINER □ DISC □ RETAINER □ DISC □ RETAINER * REPAIRS □ O - RINGS □ LOCKNUTS □ O - RINGS □ LOCKNUTS □ O - RINGS □ LOCKNUTS □ SEAT □ OTHER: □ SEAT □ OTHER: □ SEAT □ OTHER: □ CLOSED TIGHT AT ______ PSID □ CLOSED TIGHT AT ______ PSID TEST FINAL FINAL □ OPENED AT ______ PSID CONDITION OF NO. 2 CONTROL VALVE : □ CLOSED TIGHT □ LEAKED REMARKS : □ ASSEMBLY FAILED □ ASSEMBLY PASSED □ CUSTOMER INFORMED *NOTE : ALL REPAIRS / REPLACEMENTS MUST BE COMPLETED WITHIN FOURTEEN (14) DAYS IV. APPROVALS * I HEREBY CERTIFY THAT THIS DATA IS ACCURATE AND REFLECTS THE PROPER OPERATION AND MAINTENANCE OT THE ASSEMBLY NAME OF CERTIFIED BACKFLOW PREVENTION ASSEMBLY BUSINESS TELEPHONE NO. -

Dell EMC Powerstore CLI Guide
Dell EMC PowerStore CLI Guide May 2020 Rev. A01 Notes, cautions, and warnings NOTE: A NOTE indicates important information that helps you make better use of your product. CAUTION: A CAUTION indicates either potential damage to hardware or loss of data and tells you how to avoid the problem. WARNING: A WARNING indicates a potential for property damage, personal injury, or death. © 2020 Dell Inc. or its subsidiaries. All rights reserved. Dell, EMC, and other trademarks are trademarks of Dell Inc. or its subsidiaries. Other trademarks may be trademarks of their respective owners. Contents Additional Resources.......................................................................................................................4 Chapter 1: Introduction................................................................................................................... 5 Overview.................................................................................................................................................................................5 Use PowerStore CLI in scripts.......................................................................................................................................5 Set up the PowerStore CLI client........................................................................................................................................5 Install the PowerStore CLI client.................................................................................................................................. -

File Permissions Do Not Restrict Root
Filesystem Security 1 General Principles • Files and folders are managed • A file handle provides an by the operating system opaque identifier for a • Applications, including shells, file/folder access files through an API • File operations • Access control entry (ACE) – Open file: returns file handle – Allow/deny a certain type of – Read/write/execute file access to a file/folder by – Close file: invalidates file user/group handle • Access control list (ACL) • Hierarchical file organization – Collection of ACEs for a – Tree (Windows) file/folder – DAG (Linux) 2 Discretionary Access Control (DAC) • Users can protect what they own – The owner may grant access to others – The owner may define the type of access (read/write/execute) given to others • DAC is the standard model used in operating systems • Mandatory Access Control (MAC) – Alternative model not covered in this lecture – Multiple levels of security for users and documents – Read down and write up principles 3 Closed vs. Open Policy Closed policy Open Policy – Also called “default secure” • Deny Tom read access to “foo” • Give Tom read access to “foo” • Deny Bob r/w access to “bar” • Give Bob r/w access to “bar • Tom: I would like to read “foo” • Tom: I would like to read “foo” – Access denied – Access allowed • Tom: I would like to read “bar” • Tom: I would like to read “bar” – Access allowed – Access denied 4 Closed Policy with Negative Authorizations and Deny Priority • Give Tom r/w access to “bar” • Deny Tom write access to “bar” • Tom: I would like to read “bar” – Access -

Moxa Nport Real TTY Driver for Arm-Based Platform Porting Guide
Moxa NPort Real TTY Driver for Arm-based Platform Porting Guide Moxa Technical Support Team [email protected] Contents 1 Introduction ...................................................................................2 2 Porting to the Moxa UC-Series—Arm-based Computer ....................2 2.1 Build binaries on a general Arm platform ...................................................... 2 2.2 Cross-compiler and the Real TTY driver ........................................................ 3 2.3 Moxa cross-compiling interactive script......................................................... 4 2.4 Manually build the Real TTY driver with a cross-compiler ................................ 5 2.5 Deploy cross-compiled binary to target......................................................... 8 3 Porting to Raspberry Pi OS .............................................................9 4 Porting to the Yocto Project on Raspberry Pi ................................ 10 4.1 Prerequisite............................................................................................... 10 4.2 Create a Moxa layer for the Yocto Project..................................................... 11 4.3 Install a Moxa layer into the Yocto Project.................................................... 17 4.4 Deploy the Yocto image in Raspberry Pi ....................................................... 17 4.5 Start the Real TTY driver in Raspberry Pi ..................................................... 18 4.6 Set the default tty mapping to the Real TTY configuration ............................ -

LS JK BUILDER KIT 2007-2011 Jeep Wrangler JK Installation Guide
LS JK BUILDER KIT 2007-2011 Jeep Wrangler JK Installation Guide Install Guide © Table of contents: Preface………………………………………………………………… ………………….….….…3 Part 1 Power options…………………………………………………………………….….…..…4 Part 2 The LS JK…………………………………………………………………………….….….6 Part 3 LS engines…………………………………………………………………………….….…7 Part 4 Operating systems………………………………………………………………………..10 Part 5 Gen IV LS engine features……………………………………………………………….11 Part 6 Transmissions……………………………………………………………………………..12 Part 7 Transfer cases……………………………………………………………………………..13 Part 8 MoTech basic builder kit contents……………………………………………………….14 Part 9 MoTech basic builder kit photo ID table…………………………………………………18 Part 10 MoTech Basic Kit Installation Overview and Shop Tools Required………………...20 Part 11 Prepping the vehicle………………………………………………………………..……21 Part 12 Removing the body……………………………………………………………………....21 Part 13 Prepping the chassis…………………………………………………………………..…28 Part 14 Installing the powertrain………………………………………………………………….31 Part 15 Accessory drive………………………………………………… ………………………36 Part 16 Wiring the LS JK…………………………………………………………………………..39 Appendix ……………………………………………………………………………………………52 Pentstar fan installation……………………………………………………………………52 Wiring diagrams…………………………………………………………………………….53 241J Input gear installation………………………………………………………………..56 Manual to automatic conversion……………………………………………………….….81 Torque specification GM and Jeep……………………………………………………….83 Radiator hose guide…………………………………………………………………...…...86 LS JK master part list…………………………………………………………………........87 2 Install Guide © Preface: The Wrangler -

GNU M4, Version 1.4.7 a Powerful Macro Processor Edition 1.4.7, 23 September 2006
GNU M4, version 1.4.7 A powerful macro processor Edition 1.4.7, 23 September 2006 by Ren´eSeindal This manual is for GNU M4 (version 1.4.7, 23 September 2006), a package containing an implementation of the m4 macro language. Copyright c 1989, 1990, 1991, 1992, 1993, 1994, 2004, 2005, 2006 Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled “GNU Free Documentation License.” i Table of Contents 1 Introduction and preliminaries ................ 3 1.1 Introduction to m4 ............................................. 3 1.2 Historical references ............................................ 3 1.3 Invoking m4 .................................................... 4 1.4 Problems and bugs ............................................. 8 1.5 Using this manual .............................................. 8 2 Lexical and syntactic conventions ............ 11 2.1 Macro names ................................................. 11 2.2 Quoting input to m4........................................... 11 2.3 Comments in m4 input ........................................ 11 2.4 Other kinds of input tokens ................................... 12 2.5 How m4 copies input to output ................................ 12 3 How to invoke macros........................ -

Instructions for Pwd Candidates Regarding Typing Skill Test
INSTRUCTIONS FOR PWD CANDIDATES REGARDING TYPING SKILL TEST (ON COMPUTER) AND STENOGRAPHY SKILL TEST The following guidelines are applicable to PwD Candidates shortlisted for Typing test or stenography test. 1. Typing test will be conducted on computer. 2. Persons with benchmark disability in the category of Visually impaired, orthopedically handicapped (afflicted by cerebral palsy), orthopedically handicapped (both arm affected), orthopedically handicapped candidates who has a locomotor disability wherein the dominant writing extremity is affected to the extent of slowing down the performance of the candidate (such deficiency to be indicated in the certificate, issued by competent authority, submitted by the candidate) will be allowed compensatory time of 05 minutes. 3. VI Candidates are eligible for scribe/passage dictator. 4. The Scribe/ Passage dictator is identified by the candidate at own cost and as per own choice. 5. The scribe/Passage dictator will read out the passage to VI candidates only within the allotted time. 6. Passage will not be provided in Brail for the VI candidates. 7. A person acting as a Scribe/Passage dictator for one candidate cannot be a Scribe /Passage dictator for another candidate. 8. The scribe/Passage dictator arranged by the candidate should not be a candidate for the same examination. 9. The candidate shall be responsible for any misconduct on the part of the scribe/Passage dictator brought by him during typing test. 10.Persons with Disabilities candidates who claim to be permanently unfit to take the Typing test because of a physical disability may, with the prior approval of the CEPTAM, DRDO be exempted from the requirement of appearing and qualifying at such test, provided such a candidate submits in the attached format (Appendix-I) to the CEPTAM, DRDO from the competent Medical Authority, i.e. -

GNU M4, Version 1.4.19 a Powerful Macro Processor Edition 1.4.19, 28 May 2021
GNU M4, version 1.4.19 A powerful macro processor Edition 1.4.19, 28 May 2021 by Ren´eSeindal, Fran¸coisPinard, Gary V. Vaughan, and Eric Blake ([email protected]) This manual (28 May 2021) is for GNU M4 (version 1.4.19), a package containing an implementation of the m4 macro language. Copyright c 1989{1994, 2004{2014, 2016{2017, 2020{2021 Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.3 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled \GNU Free Documentation License." i Table of Contents 1 Introduction and preliminaries ::::::::::::::::: 3 1.1 Introduction to m4 :::::::::::::::::::::::::::::::::::::::::::::: 3 1.2 Historical references :::::::::::::::::::::::::::::::::::::::::::: 3 1.3 Problems and bugs ::::::::::::::::::::::::::::::::::::::::::::: 4 1.4 Using this manual :::::::::::::::::::::::::::::::::::::::::::::: 5 2 Invoking m4::::::::::::::::::::::::::::::::::::::: 7 2.1 Command line options for operation modes ::::::::::::::::::::: 7 2.2 Command line options for preprocessor features ::::::::::::::::: 8 2.3 Command line options for limits control ::::::::::::::::::::::: 10 2.4 Command line options for frozen state ::::::::::::::::::::::::: 11 2.5 Command line options for debugging :::::::::::::::::::::::::: 11 2.6 Specifying input files on the command line ::::::::::::::::::::: -

DAA Protocol
Analysis of Direct Anonymous Attestation using Murphi Ilya Pirkin, Sudip Regmi CS 259 Project Report. March 14, 2008 1. Introduction In this project, we modeled and analyzed the security properties of the Direct Anonymous Protocol [1] using Murphi. We simplified the protocol model using security primitives which we considered unbreakable and modeled our abstractions in Murphi. Running simulations in Murphi, we were able to confirm several known attacks in the protocol explained in [2] and [3]. In addition, the model uncovered an issue with cross-site verifications that we will discuss below. 2. Protocol Overview and Murphi model Diagram 1 below shows a simple outline of the DAA protocol. As shown, there are three major agents: the Issuer, Platforms (each consists of the Host and TPM), and Verifiers. The final goal of the DAA protocol is to provide a way for the verifiers to ensure the authenticity of the platforms without revealing their identity. A platform is considered authentic if it contains an authentic TPM inside and has been correctly authenticated and authorized by the Issuer. The protocol has two phases: join and sign/verify. The goal of the join protocol is to set up the platform so it can prove its authenticity to verifiers. The join protocol is initiated by the platform. During the join protocol, platforms choose and commit to a secret value f, authenticate themselves to the Issuer (using its Endorsement Key EK ). The Issuer then generates a DAA Certificate from the platforms commitment to f and Issuer’s short-term key PKI. The platform stores its DAA Certificate internally. -

An Overview of the Scala Programming Language
An Overview of the Scala Programming Language Second Edition Martin Odersky, Philippe Altherr, Vincent Cremet, Iulian Dragos Gilles Dubochet, Burak Emir, Sean McDirmid, Stéphane Micheloud, Nikolay Mihaylov, Michel Schinz, Erik Stenman, Lex Spoon, Matthias Zenger École Polytechnique Fédérale de Lausanne (EPFL) 1015 Lausanne, Switzerland Technical Report LAMP-REPORT-2006-001 Abstract guage for component software needs to be scalable in the sense that the same concepts can describe small as well as Scala fuses object-oriented and functional programming in large parts. Therefore, we concentrate on mechanisms for a statically typed programming language. It is aimed at the abstraction, composition, and decomposition rather than construction of components and component systems. This adding a large set of primitives which might be useful for paper gives an overview of the Scala language for readers components at some level of scale, but not at other lev- who are familar with programming methods and program- els. Second, we postulate that scalable support for compo- ming language design. nents can be provided by a programming language which unies and generalizes object-oriented and functional pro- gramming. For statically typed languages, of which Scala 1 Introduction is an instance, these two paradigms were up to now largely separate. True component systems have been an elusive goal of the To validate our hypotheses, Scala needs to be applied software industry. Ideally, software should be assembled in the design of components and component systems. Only from libraries of pre-written components, just as hardware is serious application by a user community can tell whether the assembled from pre-fabricated chips. -

Printing Printf: Formatted Printing
Printing printf: formatted printing So far we have just been copying stuff from standard-in, files, pipes, etc to the screen or another file. Say I have a file with names and phone numbers. I would like to print it out with vertically aligned columns. (so my printout is not in the same format as the input file) File contents: Desired display: Bob 4929 Bob 4929 Chuck 4882 Chuck 4882 printf is a command from the C programming language to control printing. Shell script #!/bin/bash printf "Hello world.\n" a=`echo Hello world. | wc | nawk '{print $2}' ` printf "This phrase contains %d words\n" $a Run it alpaca.ceri.memphis.edu512:> printex.sh Hello world. This phrase contains 2 words alpaca.ceri.memphis.edu513:> #!/bin/bash printf "Hello world.\n" a=`echo Hello world. | wc | nawk '{print $2}' ` printf "This phrase contains %d words\n" $a We need the double quotes “ . “ to define an argument (the stuff inside the quotes) for printf. #!/bin/bash printf "Hello world.\n" a=`echo Hello world. | wc | nawk '{print $2}' ` printf "This phrase contains %d words\n" $a The argument in double quotes has - Regular text (“Hello world”, “This text contains “) - Some funny new thing - %d – a format specifier. - The already known specification for a new line - \n #!/bin/bash printf "Hello world.\n" a=`echo Hello world. | wc | nawk '{print $2}' ` printf "This phrase contains %d words\n" $a We also have another argument, the $a, which is a shell variable, at the end. Note that the items are delimited with spaces, not commas.