An Investigation Into Current Trends for Email Processing and Communication Research
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Implementation of Proactive Spam Fighting Te Niques
Implementation of Proactive Spam Fighting Teniques Masterarbeit von Martin Gräßlin Rupret-Karls-Universität Heidelberg Betreuer: Prof. Dr. Gerhard Reinelt Prof. Dr. Felix Freiling 03. März 2010 Ehrenwörtlie Erklärung I versiere, dass i diese Masterarbeit selbstständig verfasst, nur die angegebenen ellen und Hilfsmiel verwendet und die Grundsätze und Empfehlungen „Verantwortung in der Wissensa“ der Universität Heidelberg beatet habe. Ort, Datum Martin Gräßlin Abstract One of the biggest allenges in global communication is to overcome the problem of unwanted emails, commonly referred to as spam. In the last years many approaes to reduce the number of spam emails have been proposed. Most of them have in common that the end-user is still required to verify the filtering results. ese approaes are reactive: before mails can be classified as spam in a reliable way, a set of similar mails have to be received. Spam fighting has to become proactive. Unwanted mails have to be bloed before they are delivered to the end-user’s mailbox. In this thesis the implementation of two proactive spam fighting teniques is discussed. e first concept, called Mail-Shake, introduces an authentication step before a sender is allowed to send emails to a new contact. Computers are unable to authenticate themselves and so all spam messages are automatically bloed. e development of this concept is discussed in this thesis. e second concept, called Spam Templates, is motivated by the fact that spam messages are generated from a common template. If we gain access to the template we are able to identify spam messages by mating the message against the template. -
Metadata Track Akonadi the Independent Solution for PIM Data
Akonadi – The independent solution for PIM GCDS 2009 data Metadata track Akonadi the independent solution for PIM data Will Stephenson Will Stephenson Akonadi – The independent solution for PIM GCDS 2009 data Akonadi Topics Akona-what? Design Overview What we give you What you give us Will Stephenson Akonadi – The independent solution for PIM GCDS 2009 data Akonadi The story so far Monolithic apps Own data storage Limited if any external interfaces E-D-S Data storage service Limited range of types supported Will Stephenson Akonadi – The independent solution for PIM GCDS 2009 data Why? Limitations of KDE3 KResource framework limitations: Data is not shared Designed for synchronous access Hard to extend to other data types Basically no shared common code KMail limitations: Only limited backend abstraction Designed for small amounts of local data Will Stephenson Akonadi – The independent solution for PIM GCDS 2009 data Scalability with KDE 3 |Data| = small Contact applet KAddressBook l l KMail Kopete Will Stephenson Akonadi – The independent solution for PIM GCDS 2009 data Scalability in KDE 3 |Data| = large Contact applet KAddressBook l l KMail Kopete Will Stephenson Akonadi – The independent solution for PIM GCDS 2009 data Why? Goals As much as possible shared, type independent functionality Easy to extend to new data types Unified API to access PIM data, independent of the actual data source Scalability Will Stephenson Akonadi – The independent solution for PIM GCDS 2009 data Why? Goals One synchronization point for mobile devices Reliable, -

Functional HCL Notes Email Archiving Solution
AM ™ ArchiveMail DATASHEET Functional HCL Notes™ email archiving solution Key In Detail on Introducti Characteristics Benefits For the Users: Continuous growth in data volumes related to messaging and the practical limits imposed by Notes database architecture make email archiving systems essential. M Improved productivity due to automatic management of archive. COOPERTEAM’s Archive Mail™ is a functional archiving solution which responds to the M needs of administrators by allowing them to manage archiving policies efficiently and Access to archived documents from automatically, whilst still guaranteeing their users access to their documents and the Notes client, iNotes and mobile attached files. devices. Archive Mail™ automates the archiving of messages, calendar entries, tasks and contacts M Multi-criteria searching available for to one archive per year, hosted on either dedicated or shared function servers. Archiving both server & workstation. policies can be based on document ageing criteria. In addition, the archive process can be triggered when the mail database exceeds its For the Administrators: threshold (quota), or manually by users after selecting documents to be archived. M Optimization of the Domino Archive Mail™ allows administrators to manage multiple archive databases and easily infrastructure. implement ILM (Information Lifecycle Management) policies, and to correctly align the M Align messaging storage costs, value storage costs of the archived documents with their value to the business. for the business and quota policies. M Once Archive Mail™ is implemented, documents that meet the configured ageing Automated and centralised parameters for archiving are transferred to an archive database at a frequency predeter- management of archiving mined by their profile administrator. -

Zimbra Tips & Tricks
TOP ZIMBRA 15 TIPS & TRICKS This guide brings you the top 15 Zimbra Tips & Tricks to help you save time while working in Zimbra. If you find these Tips & Tricks helpful, you may also like our tutorial demos: The top 15 Zimbra Tips & Tricks (based on clicks on Zimbra’s “Did You Know?” blog) are: Throughout this guide, look for pop-up boxes highlighting quick tips Email Tips and Tricks and facts. 1 Searching in Zimbra TIP: Skip ahead to any 2 Importing Into and Exporting From Zimbra section of the 15 Tips & 3 Changing Your Zimbra Preferences Tricks by clicking on the 4 Changing Your Zimbra Theme titles to the right. 5 Setting Zimbra Email and SMS (text) Reminders 6 Enabling Zimbra’s Mandatory Spellcheck 7 Sorting Email 8 Creating an Appointment with the Mini Calendar 9 Creating an Email Distribution List or Contact Group 10 Opening an Email in a Separate Window 11 Turning on Zimbra’s Activity Stream 12 Switching from Conversation View to Message View 13 Sharing Your Zimbra Calendar Outside Your Organization 14 Sharing in Zimbra 15 Enabling Zimbra Two-Factor Authentication 1 Searching in Zimbra There are many great and easy ways to search in Zimbra: • Quick keyword search • Complex search • Right-click search Quick Keyword Search You can do a quick search using keywords like from, to, in, etc. Click here to see all search keywords. How much time do you spend searching To search by keyword: for a specific email? keyword: search word(s) Searches are easy and fast in Zimbra. Search Examples: your entire Zimbra • Find all email received from Mark (all email with “Mark” in the From account, including attachments, in seconds. -

The History of Spam Timeline of Events and Notable Occurrences in the Advance of Spam
The History of Spam Timeline of events and notable occurrences in the advance of spam July 2014 The History of Spam The growth of unsolicited e-mail imposes increasing costs on networks and causes considerable aggravation on the part of e-mail recipients. The history of spam is one that is closely tied to the history and evolution of the Internet itself. 1971 RFC 733: Mail Specifications 1978 First email spam was sent out to users of ARPANET – it was an ad for a presentation by Digital Equipment Corporation (DEC) 1984 Domain Name System (DNS) introduced 1986 Eric Thomas develops first commercial mailing list program called LISTSERV 1988 First know email Chain letter sent 1988 “Spamming” starts as prank by participants in multi-user dungeon games by MUDers (Multi User Dungeon) to fill rivals accounts with unwanted electronic junk mail. 1990 ARPANET terminates 1993 First use of the term spam was for a post from USENET by Richard Depew to news.admin.policy, which was the result of a bug in a software program that caused 200 messages to go out to the news group. The term “spam” itself was thought to have come from the spam skit by Monty Python's Flying Circus. In the sketch, a restaurant serves all its food with lots of spam, and the waitress repeats the word several times in describing how much spam is in the items. When she does this, a group of Vikings in the corner start a song: "Spam, spam, spam, spam, spam, spam, spam, spam, lovely spam! Wonderful spam!" Until told to shut up. -

Guest Artist Agreement
Artists Agreement Unitarian Universalist Congregation of Phoenix 4027 E. Lincoln Drive, Paradise Valley, AZ 85253 Phone: 602-840-8400 Email: [email protected] The Sanctuary Art Team of the Unitarian Universalist Congregation of Phoenix (UUCP) welcomes you. We are pleased that you are participating in our art exhibit. The following guidelines and liability agreement should be helpful to you in preparing for installation of your artwork. 1) All works selected for exhibit will be displayed in the Sanctuary or Hall in spaces reserved for that purpose. 2) An art inventory should be completed before arrival and sent to the email above or as directed. It MUST be completed when the art is delivered to UUCP. Artists must provide the following information: Artist's Name, Title of Work, Medium, Dimensions, and Sale Price or NFS (See inventory form). 3) All work must be ready for hanging. Any work over 600 square inches requiring protective covering must be covered in Plexiglas (NOT glass). 4) All works must remain on display until the termination of the show unless previously arranged with the Sanctuary Art Team. At the close of the show, the lender/artist agrees to remove the pieces on exhibit or arrange for their removal. Any object remaining in the Sanctuary for 30 days following the scheduled close of the show will be handled at the discretion of the Sanctuary Art Team. 5) Each object displayed will be exhibited in such manner as the Sanctuary Art Team decides. 6) The Sanctuary Art Team reserves the right to select and/or reject works, bearing in mind that the Sanctuary is not a conventional gallery and the selected works must be appropriate for all congregational activities. -

Monthly Worship Themes What Does It Mean to Be a People Of
2 Begin Your Journey Here Sunday Worship Monthly Worship Themes What does it mean to be a people of... Welcome to UUCP! This is a religious community September Covenant Welcoming all as we Rev. Susan October Freedom Share our Journeys Frederick-Gray Grow in Spirit November Gratitude Together work to Advance Justice December Tradition The best way to see, feel and get to know this community January Truth is through Sunday morning services. Each month we February Love explore a theme in depth. Our themes challenge us to grow in meaning, build connections across diversities and March Hope make our world a better place. April Service May Peace Service times: May – September 13: 10:30 AM June Strength September 20 – April 17: 9:30 AM and 11:15 AM July/August Spirituality Starting Point Community Nights Are you new to UUCP? Do you have questions Break Bread and Make Friends at UUCP. Community about UUCP and Unitarian Universalism? Nights are a time of fellowship and community building Starting Point is an informal program for all ages. We provide the main dish with a vegetarian especially for you! Meet a representative from option and one side. Just bring your appetite, enthusi- the Membership Committee by the Starting asm, and a side dish or dessert to share if able. You are Point sign in the front lobby any second Sunday of the also welcome to bring a sack supper if you prefer. month. You don’t have to sign up. Just show up! Chalice Kids is a program for children that begins right In twenty to thirty minutes, we will answer questions and after the meal at 6:30 PM. -
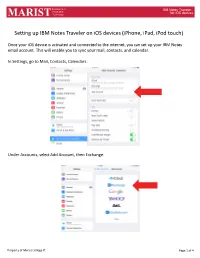
Setting up IBM Notes Traveler on Ios Devices (Iphone, Ipad, Ipod Touch)
Department of IBM Notes Traveler Information for iOS devices MARIST Technology Setting up IBM Notes Traveler on iOS devices (iPhone, iPad, iPod touch) Once your iOS device is activated and connected to the internet, you can set up your IBM Notes email account. This will enable you to sync your mail, contacts, and calendar. In Settings, go to Mail, Contacts, Calendars. Under Accounts, select Add Account, then Exchange. Property of Marist College IT Page 1 of 4 Department of IBM Notes Traveler Information for iOS devices MARIST Technology The Exchange window will display. In the Email field, enter your Marist email address. In the Password field, enter your IBM iNotes password (as you would log in to notes.marist.edu). In the Description field, type “Marist” (without quotation marks). Press “Next” in the upper right corner of the window. The window will expand. In the Server field type in “traveler.notes.marist.edu/traveler” (without quotation marks). In the Username field enter your iNotes username (firstname.lastname). Leave the Domain field blank. Press “Next” in the upper right corner of the window. Information Technology Property of Marist College IT Page 2 of 4 Department of IBM Notes Traveler MARIST Your account will be verified. The next screen displays the Notes data items that will Sync. Slide to the left any item you do not wish to sync, select Save. Information Technology for iOS devices Information Technology for iOS devices The Exchange Account will be created and you will be returned to Settings. Change the ‘Mail Days to Sync’ to your preference. -

How to Create a Personal Email Account/Address (Gmail, Yahoo & Outlook)
How to create a personal email account/address (Gmail, Yahoo & Outlook) Step 1 – select an email provider (Gmail, Yahoo, Outlook, etc.) There are many different email providers that will allow you to create an email account to send and receive emails. Some of the more common ones include Gmail, Yahoo and Outlook. Below are instructions for setting up an email account using these three providers. Gmail – 1) Go to www.gmail.com 2) Click create an account 3) You will get a small pop up box that asks you to select either: for myself or to manage my business. Select For myself 4) A form to create your account will appear. Complete the information in the form. a. First name, Last name b. Username – enter the first part of what you want your email address to be – for example, janedoe (@gmail.com will be added to the end of it.) For example: [email protected] c. Password – you will need to create a password. This is what will allow you to log into your account to send and receive emails 5) Next, you will see a form to enter some of your personal information, such as your phone number, birth date and gender – enter the requested information 6) You will receive Google’s Privacy and Terms. Read and click “I Agree” (you will need to agree to the privacy and terms in order to complete your email account sign up) 7) Once you agree to the terms and conditions, you will be taken to your new email account inbox 8) You can now start to send and receive emails 9) You can login to your new email account by going to www.gmail.com (and entering your email address and password) Yahoo – 1) Go to https://login.yahoo.com/account/create 2) Complete the information in the sign-up form that appears. -
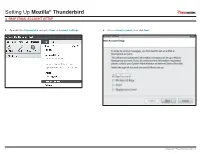
Setting up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP
Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP 1. Open Mozilla Thunderbird and go to Tools -> Account Settings. 2. Choose Email account; then click Next. 1 Copyright © EmailHosting.com LLC Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP (cont.) 3. In the Identity window type your name as you want it to appear on outgoing emails. 4. In the Server Information window select the radio button labeled IMAP. • Then, type your email address in the field labeled Email Address. • Enter imap.emailhosting.com in the field labeled Incoming Server. • Click Next to continue. • Enter smtp.emailhosting.com in the field labeled Outgoing Server. • Click Next to continue. John Smith imap.emailhosting.com [email protected] smtp.emailhosting.com Note: If you have already used Thunderbird in the past the Outgoing Server will not be listed. 2 Copyright © EmailHosting.com LLC Setting Up Mozilla® Thunderbird IMAP EMAIL ACCOUNT SETUP (cont.) 5. In the User Names window, the fields should already be filled out correctly. 6. Click Next on the Account Name page to accept the default Account Name. • Confirm that both fields match your EmailHosting username. • In the Congratulations window, verify that all information is correct. • Click Next to continue. • Then click Finish. [email protected] [email protected] [email protected] [email protected] 7. You will be prompted for your password. If you’d like to save your password, make sure Use Password Manager to remember this password is checked before clicking on OK to continue. Note: The field Outgoing Server is only visible during the setup of Mozilla Thunderbird’s first email account. -

Brave Gnu World
LINUXCOVERCOMMUNITY USERSTORY SchlagwortSchlagwortBrave GNU sollte Worldsollte hier hier stehen stehen Schlagwort sollte hier stehen COVER STORY The Monthly GNU Column BRAVE GNU WORLD This column looks into projects and current affairs in the world of free software from the perspective of the GNU Project and the FSF. In this issue, I’ll focus on Comspari and the EU decision on software patents. BY GEORG C.F. GREVE n the past, the German government the Kroupware project in 2002. The pub- principles back to front. For example, has often caused a (positive) stir due lic tender by the BSI was aimed to pro- many other solutions are based on the Ito its activities with free software. duce a groupware solution that would principle that the server is the king of The Federal Ministry of the Economy support strong cryptography and inte- the hill and the users have to bow down (BMWi) sponsored Gnupg [1], for exam- grate seamlessly into a heterogeneous and worship it. The Kolab server does ple. Add to this a number of accompany- environment. things differently. The program makes ing activities, such as a report by the The government office gave a consor- the user king, and gives the user power Bavarian Accounts Office, the KBST let- tium comprising Erfrakon, Klarälvdalens to do things. The software simply helps ter, and the highly acclaimed migration Datakonsult [2], and Intevation [3] the coordinate things as a central intermedi- guide by the Federal Ministry of the Inte- task of developing the software. Inter- ary. rior (BMI). nally, the design and the software was Kolab 1 combined so-called partial referred to as Kolab 1. -

Nextcloud User Manual Release Latest
Nextcloud User Manual Release latest The Nextcloud developers Oct 06, 2021 CONTENTS 1 Nextcloud latest user manual introduction1 2 What’s new for users in Nextcloud latest3 3 The Nextcloud Web interface7 3.1 Web browser requirements........................................7 3.2 Navigating the main user interface....................................8 4 Files & synchronization 11 4.1 Accessing your files using the Nextcloud Web interface......................... 11 4.2 Accessing Nextcloud files using WebDAV................................ 17 4.3 Managing deleted files.......................................... 28 4.4 Desktop and mobile synchronization.................................. 29 4.5 Encrypting your Nextcloud files on the server.............................. 30 4.6 File Sharing............................................... 33 4.7 Federated Shares............................................. 37 4.8 Making anonymous uploads....................................... 39 4.9 Large file uploads............................................ 41 4.10 Storage quota............................................... 42 4.11 Version control.............................................. 42 4.12 Projects.................................................. 43 4.13 Transfer Ownership........................................... 47 5 Groupware 49 5.1 Using the Contacts app.......................................... 49 5.2 Using the Calendar app......................................... 52 5.3 Synchronizing with Android....................................... 60 5.4